SUSE Linux Enterprise Desktop Administration Chapter 5 Manage















- Slides: 67

SUSE Linux Enterprise Desktop Administration Chapter 5 Manage the Network Configuration

Objectives • Objective 1—Manage the Network Configuration Information from Ya. ST • Objective 2—Test the Network Connection with Command-Line Tools • Objective 3—Use Su. SEfirewall 2 • Objective 4—Use Network Manager to Configure the Network • Objective 5—Provide Remote Access SUSE Linux Enterprise Desktop Administration 2

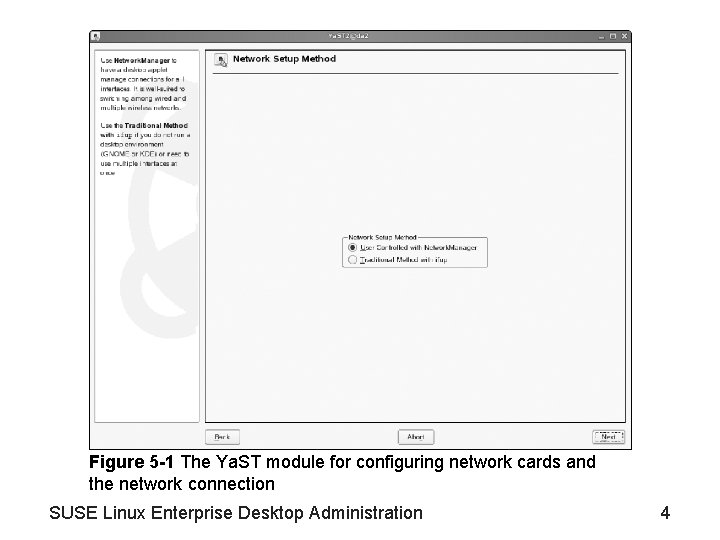
Objective 1—Manage the Network Configuration Information from Ya. ST • The Ya. ST module for configuring network cards and the network connection – Can be accessed from the Ya. ST Control Center – See Figure 5 -1 • To activate the network configuration module, select Network Devices > Network Card • Network setup methods: – User Controlled with Network Manager – Traditional Method with ifup SUSE Linux Enterprise Desktop Administration 3

Figure 5 -1 The Ya. ST module for configuring network cards and the network connection SUSE Linux Enterprise Desktop Administration 4

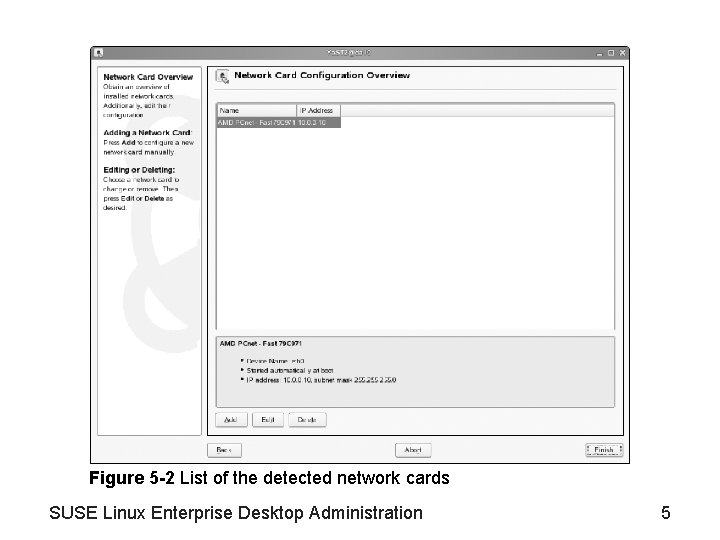
Figure 5 -2 List of the detected network cards SUSE Linux Enterprise Desktop Administration 5

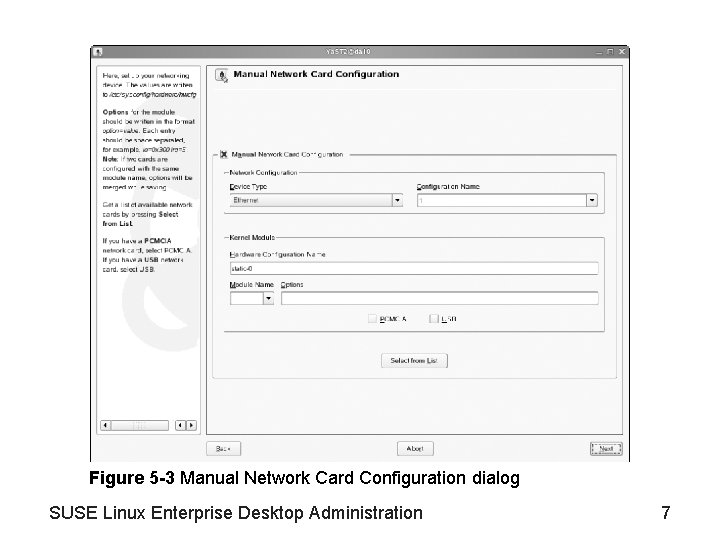
Objective 1—Manage the Network Configuration Information from Ya. ST (continued) • Cards are usually autodetected by Ya. ST – And the correct kernel module is used • Select the card you want to configure – Then select Edit (see Figure 5 -4) • If the card is not recognized by Ya. ST, the required module must be entered manually • Use the Manual Network Card Configuration dialog to configure: (see Figure 5 -3) – Network Configuration – Kernel Module SUSE Linux Enterprise Desktop Administration 6

Figure 5 -3 Manual Network Card Configuration dialog SUSE Linux Enterprise Desktop Administration 7

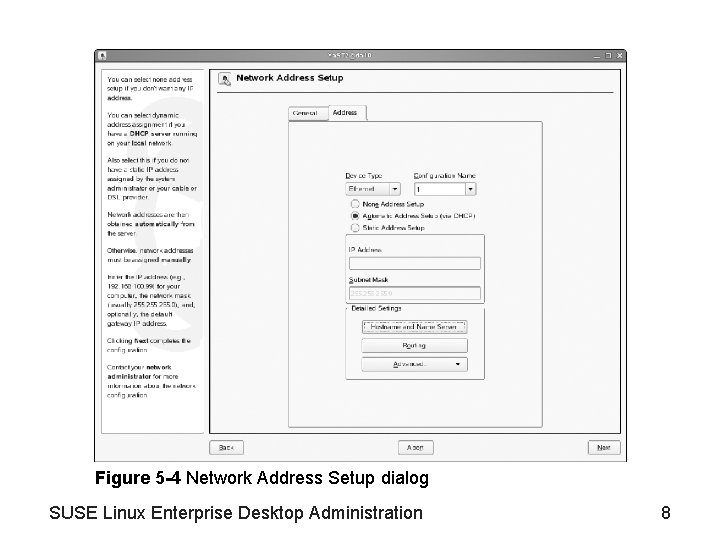
Figure 5 -4 Network Address Setup dialog SUSE Linux Enterprise Desktop Administration 8

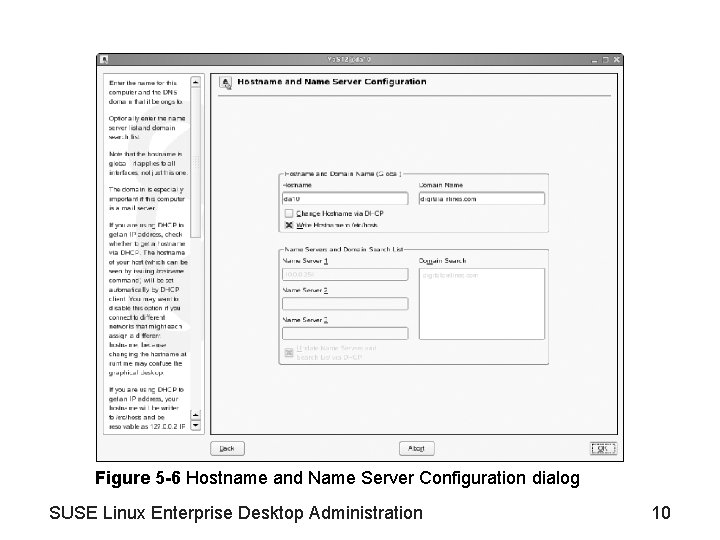
Objective 1—Manage the Network Configuration Information from Ya. ST (continued) • Network address options – – – None Address Setup Automatic Address Setup (via DHCP) Static Address Setup Hostname and Name Server Routing Advanced • Hostname and Name Server configuration – See Figure 5 -6 SUSE Linux Enterprise Desktop Administration 9

Figure 5 -6 Hostname and Name Server Configuration dialog SUSE Linux Enterprise Desktop Administration 10

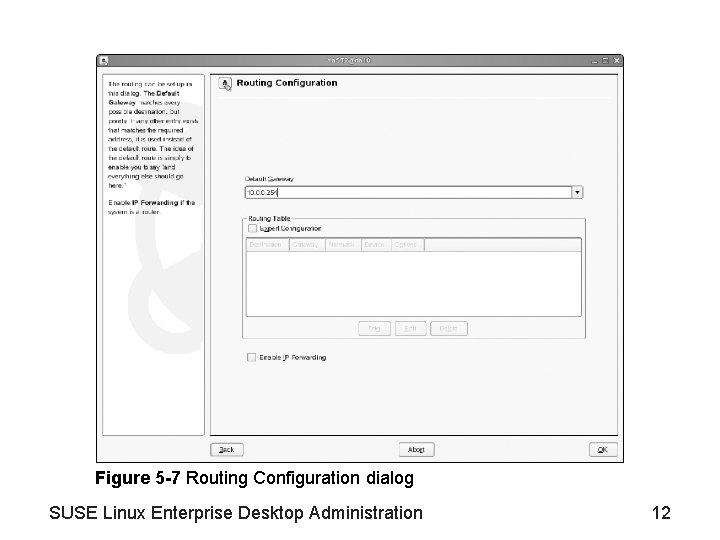
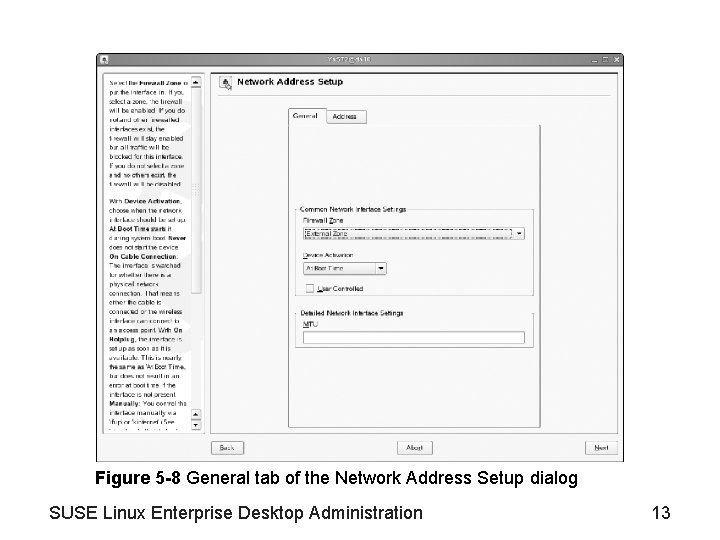
Objective 1—Manage the Network Configuration Information from Ya. ST (continued) • Routing configuration – See Figure 5 -7 • General configuration options (see Figure 5 -8) – Firewall Zone • • No Zone, All Traffic Blocked Internal Zone (Unprotected) Demilitarized Zone External Zone – Device Activation – MTU (Maximum Transfer Unit) SUSE Linux Enterprise Desktop Administration 11

Figure 5 -7 Routing Configuration dialog SUSE Linux Enterprise Desktop Administration 12

Figure 5 -8 General tab of the Network Address Setup dialog SUSE Linux Enterprise Desktop Administration 13

Objective 1—Manage the Network Configuration Information from Ya. ST (continued) • If you selected Wireless as a Device Type for a WLAN card – A dialog appears where you can enter WLAN-specific configuration parameters – WEP keys are entered in a separate dialog after selecting WEP Keys • Verify that the Ethernet card is available in the computer using the ip command SUSE Linux Enterprise Desktop Administration 14

Exercise 5 -1: Manage the Network Configuration Information from Ya. ST • In this exercise, change all important configuration information into static values • Use the ip command to find out which IP address you are currently using – Note your current hostname – Then change the network configuration to a static IP address, using the values you found – Use 10. 0. 0. 254 as the default gateway and also as the address of the name server SUSE Linux Enterprise Desktop Administration 15

Objective 2—Test the Network Connection with Command-Line Tools • This objective will cover the following: – View and Change the Network Configuration with ip – Test Network Connections – Trace Network Packets SUSE Linux Enterprise Desktop Administration 16

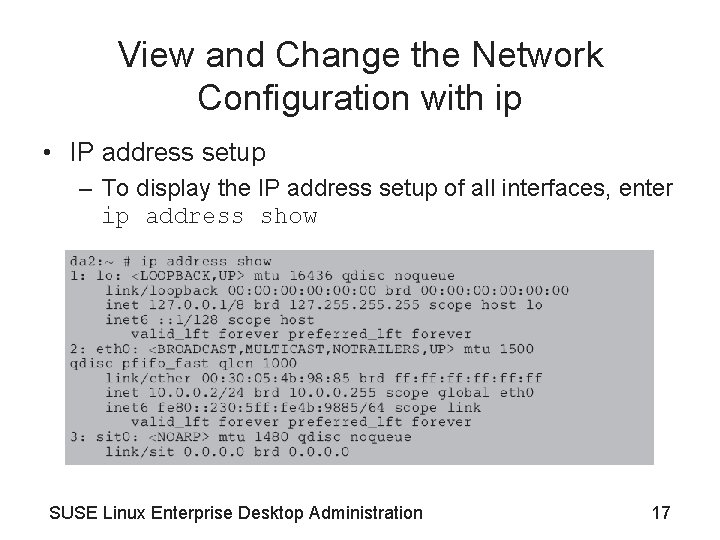
View and Change the Network Configuration with ip • IP address setup – To display the IP address setup of all interfaces, enter ip address show SUSE Linux Enterprise Desktop Administration 17

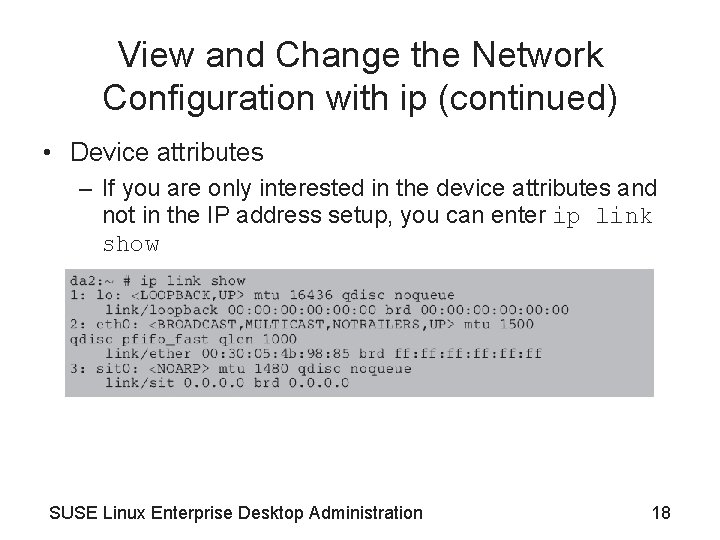
View and Change the Network Configuration with ip (continued) • Device attributes – If you are only interested in the device attributes and not in the IP address setup, you can enter ip link show SUSE Linux Enterprise Desktop Administration 18

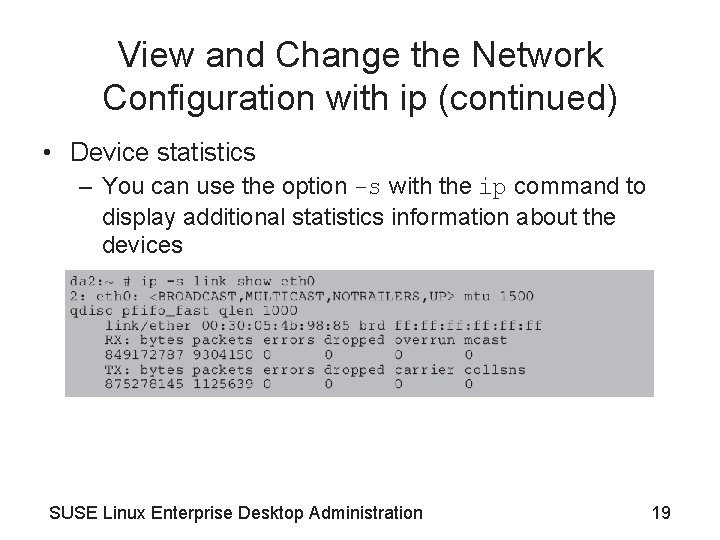
View and Change the Network Configuration with ip (continued) • Device statistics – You can use the option -s with the ip command to display additional statistics information about the devices SUSE Linux Enterprise Desktop Administration 19

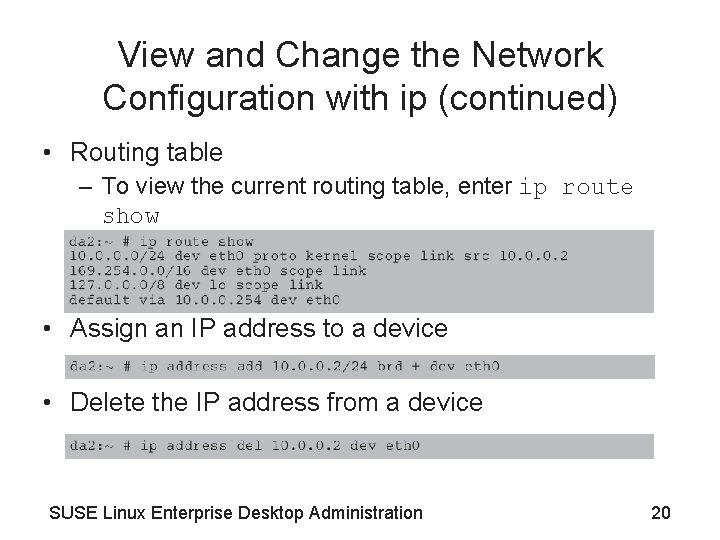
View and Change the Network Configuration with ip (continued) • Routing table – To view the current routing table, enter ip route show • Assign an IP address to a device • Delete the IP address from a device SUSE Linux Enterprise Desktop Administration 20

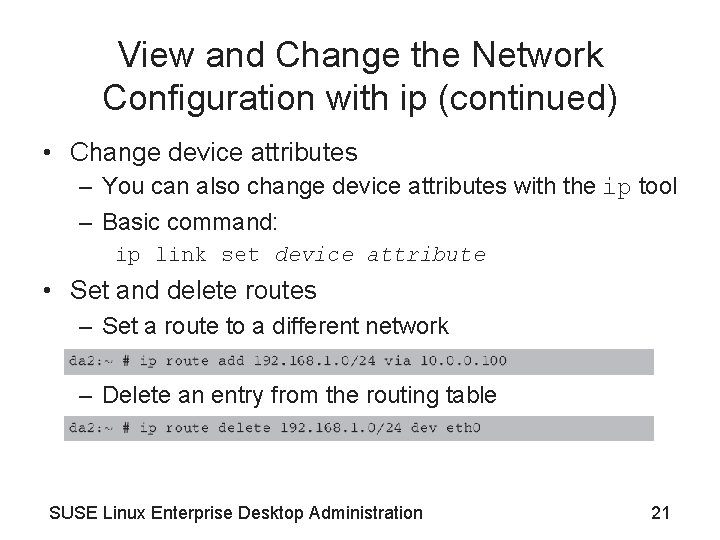
View and Change the Network Configuration with ip (continued) • Change device attributes – You can also change device attributes with the ip tool – Basic command: ip link set device attribute • Set and delete routes – Set a route to a different network – Delete an entry from the routing table SUSE Linux Enterprise Desktop Administration 21

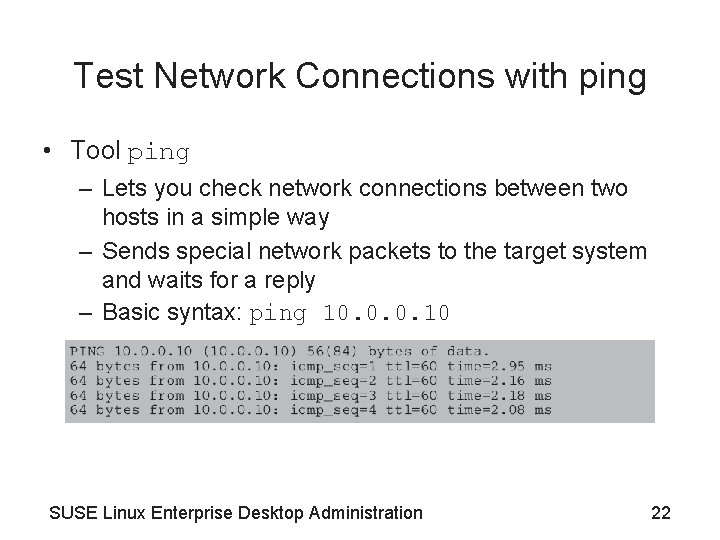
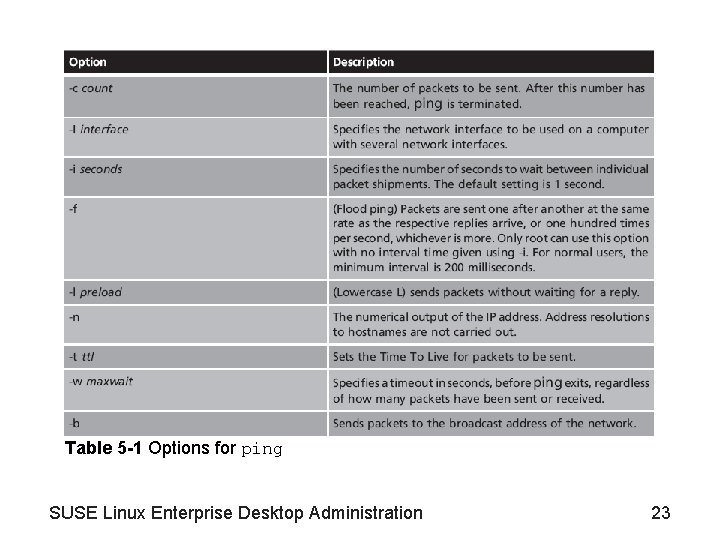
Test Network Connections with ping • Tool ping – Lets you check network connections between two hosts in a simple way – Sends special network packets to the target system and waits for a reply – Basic syntax: ping 10. 0. 0. 10 SUSE Linux Enterprise Desktop Administration 22

Table 5 -1 Options for ping SUSE Linux Enterprise Desktop Administration 23

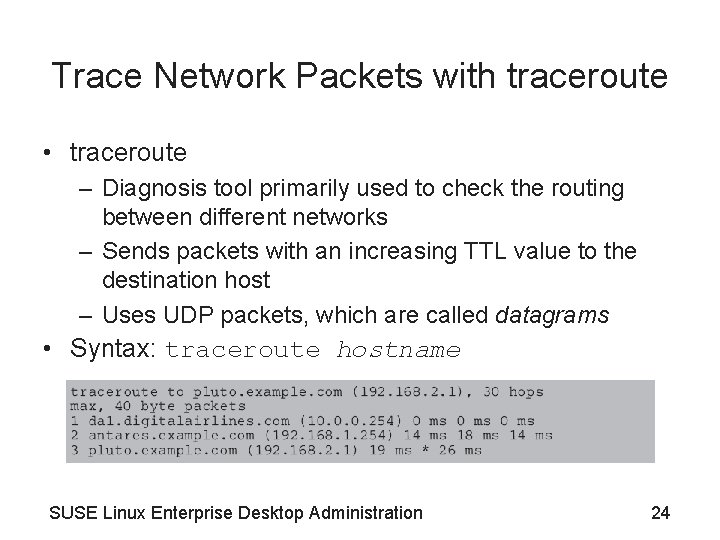
Trace Network Packets with traceroute • traceroute – Diagnosis tool primarily used to check the routing between different networks – Sends packets with an increasing TTL value to the destination host – Uses UDP packets, which are called datagrams • Syntax: traceroute hostname SUSE Linux Enterprise Desktop Administration 24

Exercise 5 -2: Test the Network Configuration • In this exercise, you view the current network configuration with the ip command test it using ping and traceroute • Use ip to view the current IP address and current route – Use ping to access your own IP address, that of the gateway, and that of www. novell. com • Use traceroute to view the hops an IP packet takes to access www. novell. com SUSE Linux Enterprise Desktop Administration 25

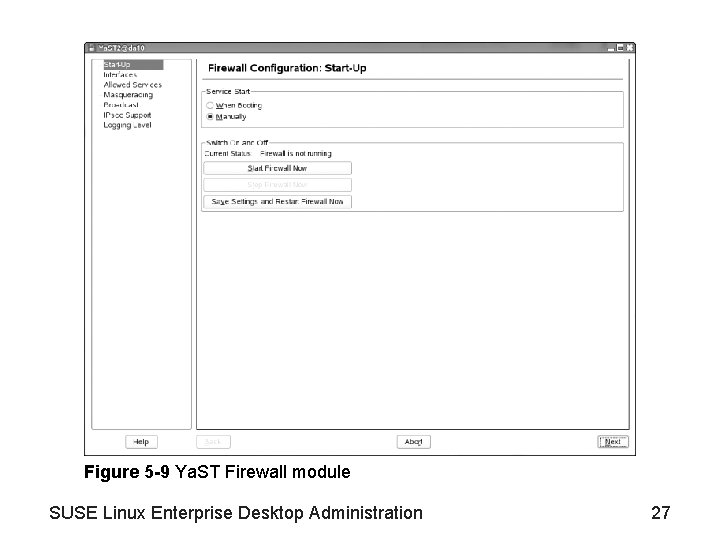
Objective 3—Use Su. SEfirewall 2 • Packet filtering in Linux is done by the kernel and its netfilter framework • Su. SEfirewall 2 – Consists of a number of scripts that set rules to filter IP packets using the program iptables – Can be configured using the Ya. ST Firewall module • An alternative would be to edit the file /etc/sysconfig/Su. SEfirewall 2 with a text editor – See Figure 5 -9 SUSE Linux Enterprise Desktop Administration 26

Figure 5 -9 Ya. ST Firewall module SUSE Linux Enterprise Desktop Administration 27

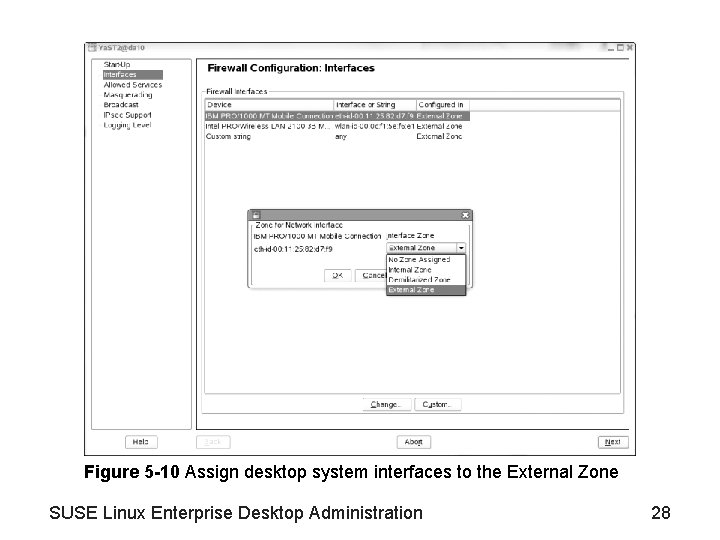
Figure 5 -10 Assign desktop system interfaces to the External Zone SUSE Linux Enterprise Desktop Administration 28

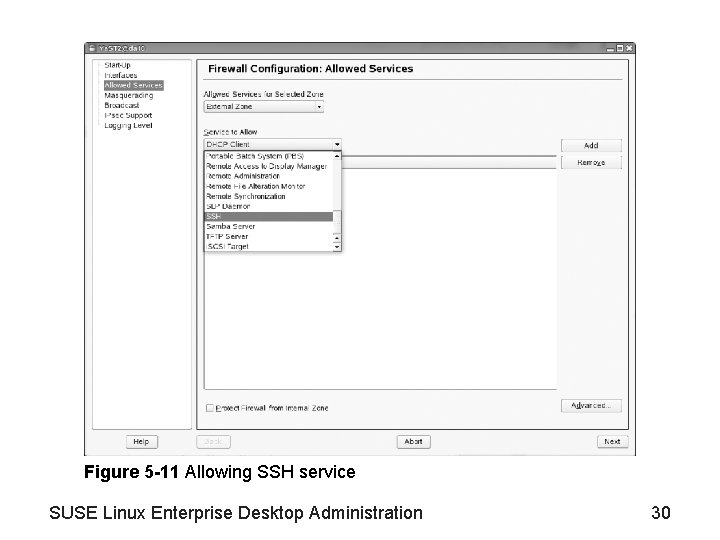
Objective 3—Use Su. SEfirewall 2 (continued) • Allowing SSH services – See Figure 5 -11 • Changes are stored in the file /etc/sysconfig/Su. SEfirewall 2 SUSE Linux Enterprise Desktop Administration 29

Figure 5 -11 Allowing SSH service SUSE Linux Enterprise Desktop Administration 30

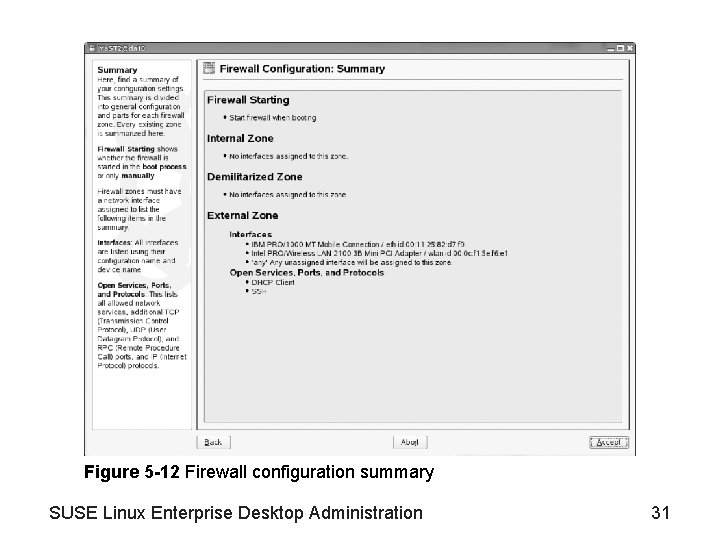
Figure 5 -12 Firewall configuration summary SUSE Linux Enterprise Desktop Administration 31

Objective 4—Use Network. Manager to Configure the Network • Network. Manager – Allows you to change the network configuration according to your needs • Without switching to the root account – Runs as a root-user system level daemon • Programs used – /usr/sbin/Network. Manager. Dispatcher • Network. Manager will first try a wired and then a wireless adapter SUSE Linux Enterprise Desktop Administration 32

Objective 4—Use Network. Manager to Configure the Network (continued) • Network. Manager keeps two lists of wireless networks: – A trusted list and a preferred list • Network. Manager applet – Shows the current network configuration – Also allows you to change the configuration • To connect to a wireless network, select a wireless network entry – Your computer will be disconnected from the wired network and connected to the wireless network SUSE Linux Enterprise Desktop Administration 33

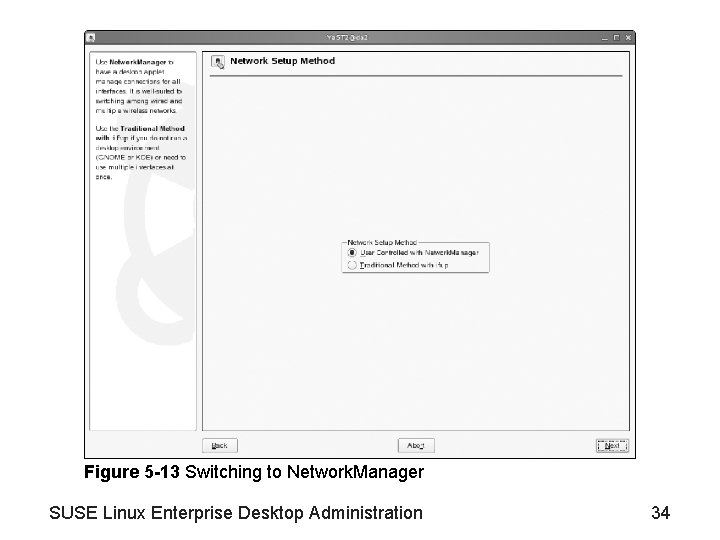
Figure 5 -13 Switching to Network. Manager SUSE Linux Enterprise Desktop Administration 34

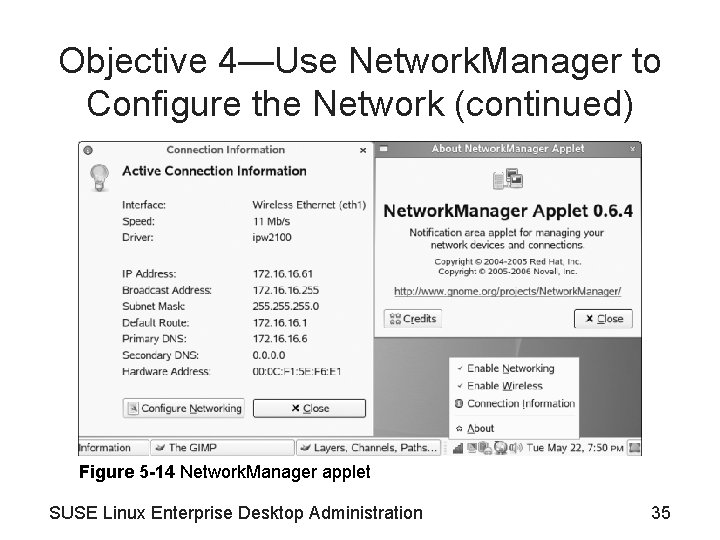
Objective 4—Use Network. Manager to Configure the Network (continued) Figure 5 -14 Network. Manager applet SUSE Linux Enterprise Desktop Administration 35

Objective 5—Provide Remote Access • This objective explains how to: – Use Open. SSH – Configure VPN Connections – Use VNC SUSE Linux Enterprise Desktop Administration 36

Use Open. SSH • SSH suite – Developed to provide secure transmission by encrypting the authentication strings • And all the other data exchanged between the hosts • SUSE Linux Enterprise Desktop 10 installs the package Open. SSH by default – Includes programs such as ssh, scp, and sftp as alternatives to Telnet, rlogin, rsh, rcp, and FTP SUSE Linux Enterprise Desktop Administration 37

Use Open. SSH (continued) • Cryptography basics – Cryptography deals with procedures and techniques used to encrypt data • And prove the authenticity of data – Symmetric encryption • • • DES (Data Encryption Standard) Triple DES IDEA Blowfish AES (Advanced Encryption Standard) SUSE Linux Enterprise Desktop Administration 38

Use Open. SSH (continued) • Cryptography basics (continued) – Asymmetric encryption • RSA • Diffie Hellman • SSH features and architecture – SSH features • Login from a remote host • Interactive or noninteractive command execution on remote hosts SUSE Linux Enterprise Desktop Administration 39

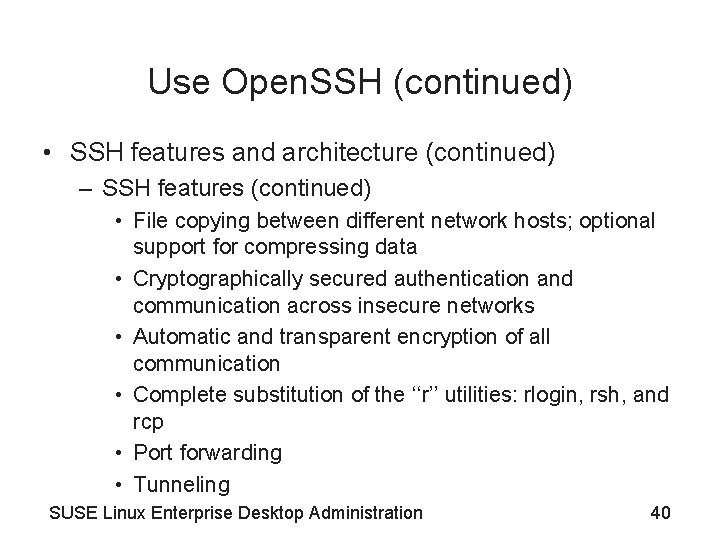
Use Open. SSH (continued) • SSH features and architecture (continued) – SSH features (continued) • File copying between different network hosts; optional support for compressing data • Cryptographically secured authentication and communication across insecure networks • Automatic and transparent encryption of all communication • Complete substitution of the ‘‘r’’ utilities: rlogin, rsh, and rcp • Port forwarding • Tunneling SUSE Linux Enterprise Desktop Administration 40

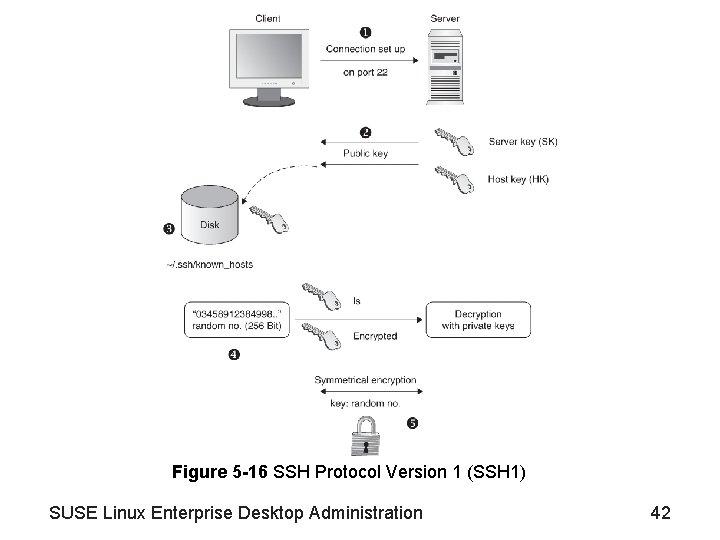
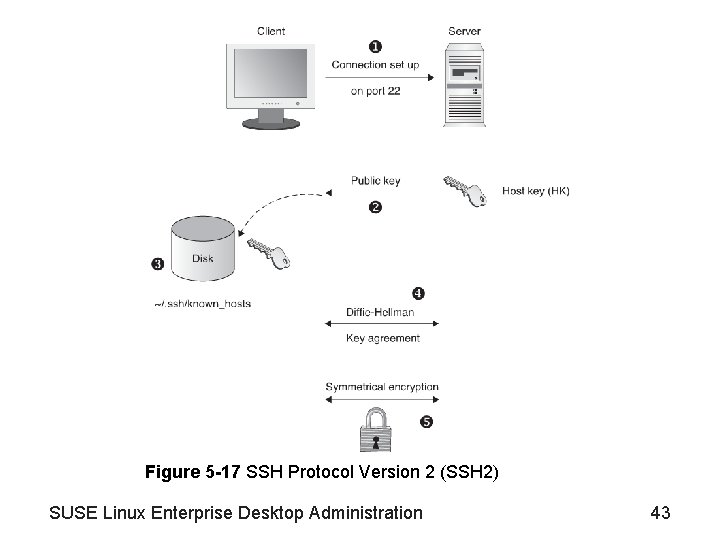
Use Open. SSH (continued) • SSH features and architecture (continued) – SSH protocol versions • Protocol Version 1 (SSH 1) (see Figure 5 -16) • Protocol Version 2 (SSH 2) (see Figure 5 -17) – SSH authentication mechanism configuration • SSH server can decrypt the session key generated and encrypted by the client only if it also has the private key • Client can check if the public host key of the server really belongs to the server • SSH currently does not use any directory services or any certificates for public key management SUSE Linux Enterprise Desktop Administration 41

Figure 5 -16 SSH Protocol Version 1 (SSH 1) SUSE Linux Enterprise Desktop Administration 42

Figure 5 -17 SSH Protocol Version 2 (SSH 2) SUSE Linux Enterprise Desktop Administration 43

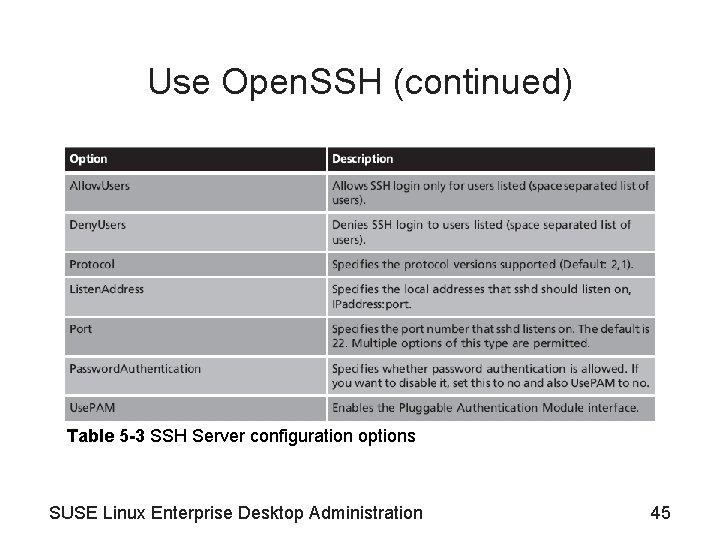
Use Open. SSH (continued) • SSH features and architecture (continued) – SSH authentication mechanism configuration (continued) • The two most important mechanisms – Public key (RSA/DSA) authentication – Password authentication • Configure the SSH server – See Table 5 -3 – Configuration file for the server is /etc/sshd_config SUSE Linux Enterprise Desktop Administration 44

Use Open. SSH (continued) Table 5 -3 SSH Server configuration options SUSE Linux Enterprise Desktop Administration 45

Use Open. SSH (continued) • Configure the SSH client – Edit the file /etc/ssh_config – Users can edit their individual settings in the file /. ssh/config – Ensure that only servers are accepted whose keys have been previously added to /. ssh/known_hosts or /etc/ssh_known_hosts • Set the option Strict. Host. Key. Checking in the client configuration file (/. ssh/config) to yes SUSE Linux Enterprise Desktop Administration 46

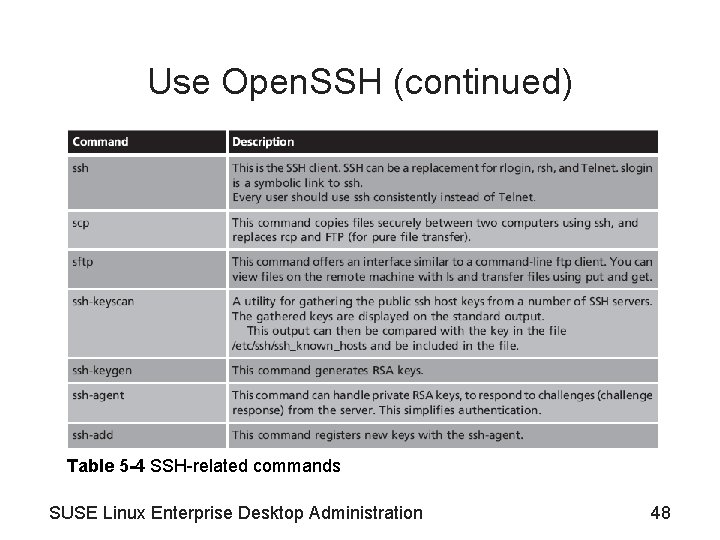
Use Open. SSH (continued) • SSH-related commands – See Table 5 -4 – Basic syntax for ssh: • ssh options host command – Basic syntax for scp is: • scp options sourcefile destinationfile – SSH can also be used to protect unencrypted traffic, like POP 3, by tunneling it through an SSH connection SUSE Linux Enterprise Desktop Administration 47

Use Open. SSH (continued) Table 5 -4 SSH-related commands SUSE Linux Enterprise Desktop Administration 48

Exercise 5 -3: Practice Using Open. SSH • Perform the following tasks: – Log in to your partner’s computer as root – Execute the ps aux command on your partner’s computer without logging in to his or her computer – Copy the /etc/hosts file from your partner’s computer to your /tmp directory – Copy the /etc/hosts file from your computer to the home directory of geeko on your partner’s computer – Using sftp, copy the /bin/date file from your partner’s computer to /home/geeko/ on your computer SUSE Linux Enterprise Desktop Administration 49

Use Open. SSH (continued) • Public key authentication management – Public key authentication process • Public key of the user has to be stored on the server in the home directory of the user account being accessed • Public keys are stored on the server in the file/. ssh/authorized_keys • The corresponding private key must be stored on the client computer • The secret key should be protected by a passphrase SUSE Linux Enterprise Desktop Administration 50

Use Open. SSH (continued) • Public key authentication management (continued) – Create a key pair • Create a key pair with the ssh-keygen command • A different key is required for SSH 1 than for SSH 2 • The keys are stored in the directory /. ssh – Configure and use public key authentication • For authentication using RSA or DSA keys, you need to copy the public key to the server – And then append the public key to the file /. ssh/authorized_keys SUSE Linux Enterprise Desktop Administration 51

Use Open. SSH (continued) • Public key authentication management (continued) – Configure and use public key authentication (continued) • When authentication is done with keys, the passphrase is required when logging in to the server – Or when copying with scp • The ssh-agent can be used to avoid typing this passphrase upon each connection • The ssh-agent serves as a wrapper for any other process • You can also use the ssh-agent with a graphical login SUSE Linux Enterprise Desktop Administration 52

Exercise 5 -4: Perform Public Key Authentication • Create an ssh-key pair, add the public key to the file ~geeko/. ssh/authorized_keys on your partner’s computer, and note the difference between logging in with and without a public key • Then, use the ssh-agent to cache the private key and log in again to your partner’s machine as geeko • As root, change the SSH server configuration to allow only public key authentication • Restart sshd and, as root, try ssh geeko@localhost SUSE Linux Enterprise Desktop Administration 53

Configure VPN Connections • VPN and IPSec basics – VPN (Virtual Private Network) • Technology that uses one network infrastructure to carry the packets of another network – A VPN does not necessarily have to encrypt the traffic, but encryption is used on most VPNs – Technologies used to implement VPNs • IPSec, Open. VPN, L 2 TP, HTTPS, and SSH SUSE Linux Enterprise Desktop Administration 54

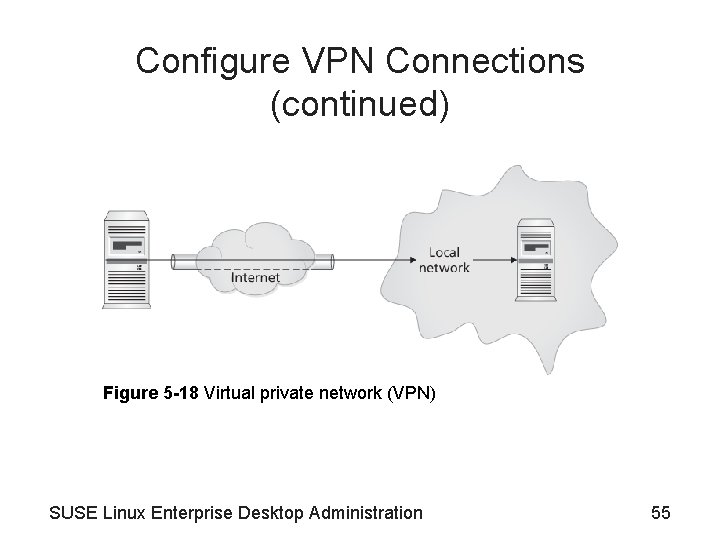
Configure VPN Connections (continued) Figure 5 -18 Virtual private network (VPN) SUSE Linux Enterprise Desktop Administration 55

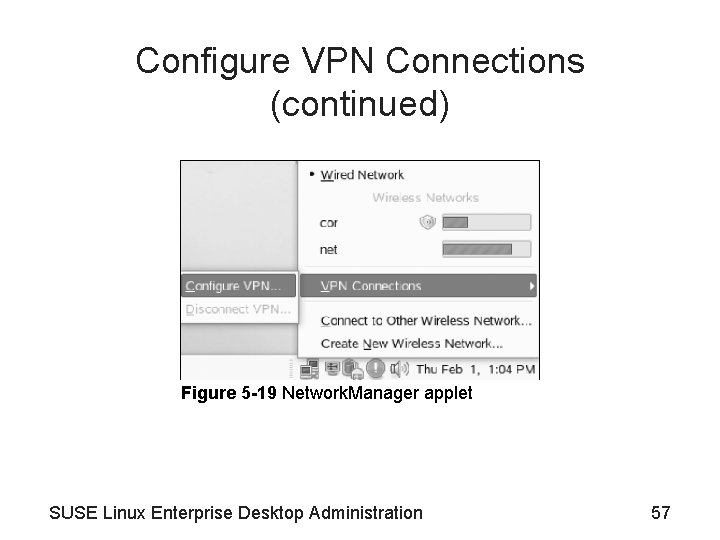
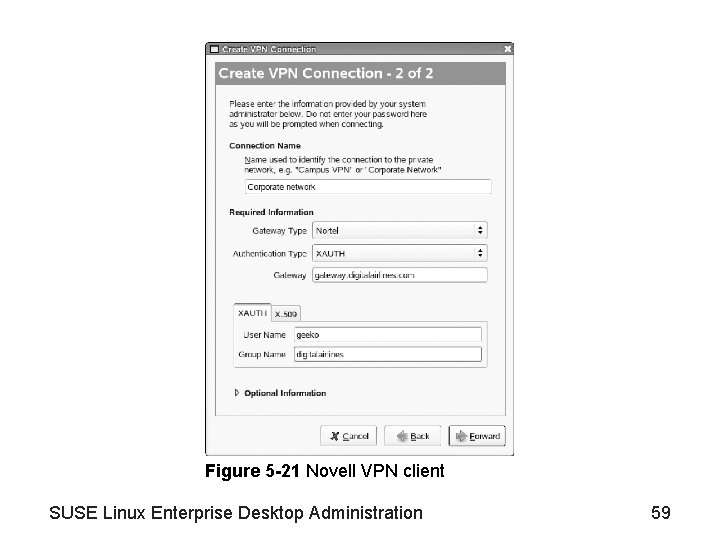
Configure VPN Connections (continued) • Configure VPN connections with Network. Manager – The Network. Manager applet makes it easy to connect to a VPN gateway • See Figure 5 -19 – An assistant guides you through the VPN configuration • See Figure 5 -20 – Types of VPN clients • Novell VPN client, Open. VPN client, and Compatible Cisco VPN client (vpnc) • See Figure 5 -21 SUSE Linux Enterprise Desktop Administration 56

Configure VPN Connections (continued) Figure 5 -19 Network. Manager applet SUSE Linux Enterprise Desktop Administration 57

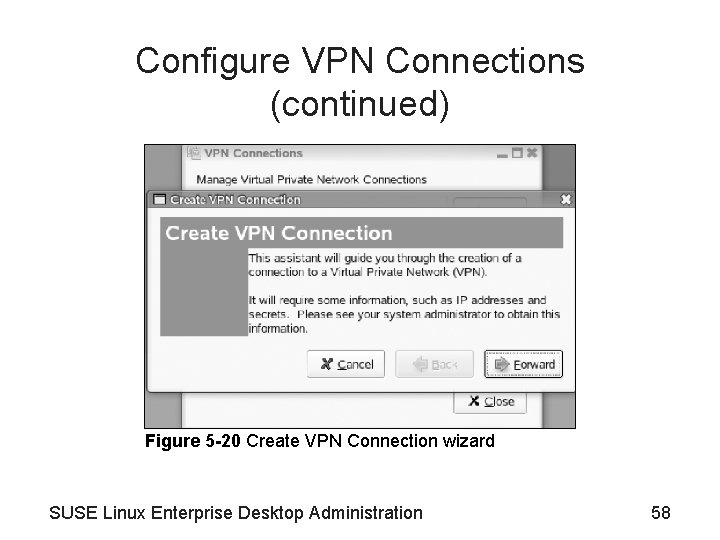
Configure VPN Connections (continued) Figure 5 -20 Create VPN Connection wizard SUSE Linux Enterprise Desktop Administration 58

Figure 5 -21 Novell VPN client SUSE Linux Enterprise Desktop Administration 59

Configure VPN Connections (continued) • Configure VPN connections with Network. Manager (continued) – GNOME keyring • Application that allows you to store various credentials and protect them with a password – Advantage of using the GNOME keyring • You only have to remember one password to unlock the encrypted keyring – Contains various usernames and corresponding passwords for different applications SUSE Linux Enterprise Desktop Administration 60

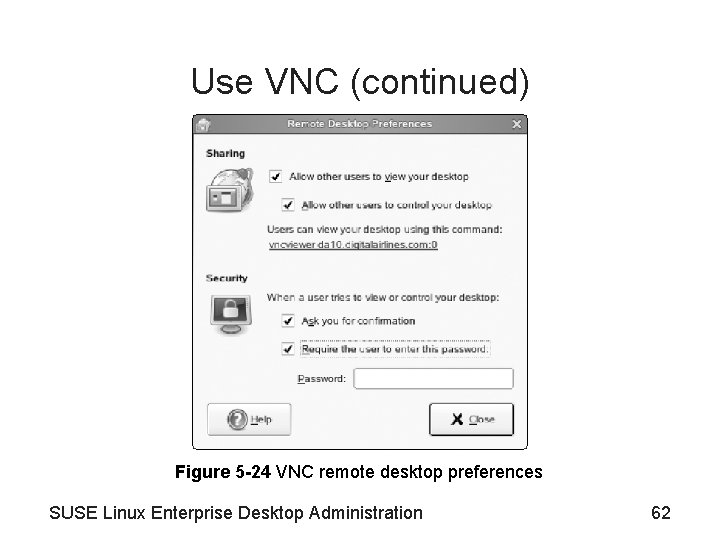
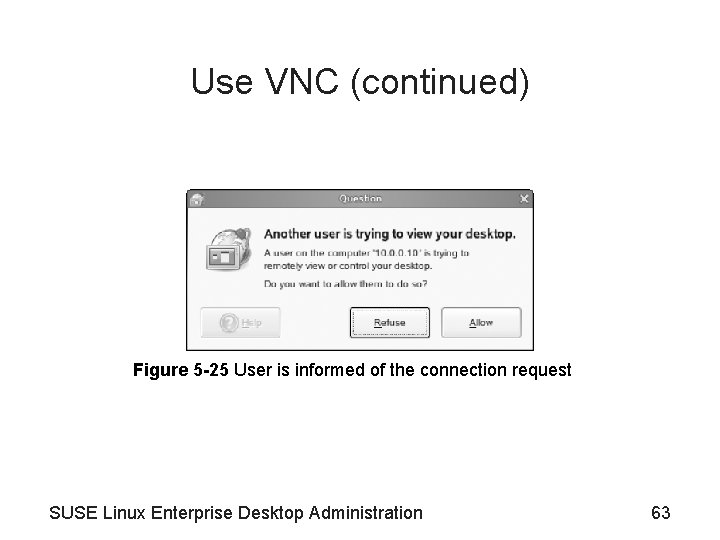
Use VNC • VNC (Virtual Network Computing) – VNC server software component transmits the content of the screen to a remote computer • Running the VNC viewer software – Allows someone else to view your desktop – Allows another user to interact with the mouse and keyboard – Implementations used on SUSE Linux Enterprise Desktop 10 are Tight. VNC and vino – See Figures 5 -24 and 5 -25 SUSE Linux Enterprise Desktop Administration 61

Use VNC (continued) Figure 5 -24 VNC remote desktop preferences SUSE Linux Enterprise Desktop Administration 62

Use VNC (continued) Figure 5 -25 User is informed of the connection request SUSE Linux Enterprise Desktop Administration 63

Exercise 5 -5: Use VNC • In this exercise, you will work with a partner • You start the VNC server using vino-preferences and allow your partner to connect to your desktop with vncviewer SUSE Linux Enterprise Desktop Administration 64

Summary • The Network Card module of Ya. ST can be used to easily manage your network interface configuration • Common IP configuration parameters include an IP address, subnet mask, hostname, name server (DNS), and WLAN settings for wireless network interfaces • Network interface and IP information is stored in the /etc/sysconfig/network directory • Different IP networks are connected to one another via routers SUSE Linux Enterprise Desktop Administration 65

Summary (continued) • After system initialization, you can use the ip command to view, configure, and manage your network interfaces, IP configuration, and routing table • You can use the Firewall module of Ya. ST to configure packet filtering on your network interfaces • Network. Manager can be used to keep track of several wired and wireless networks on portable or laptop computers • The SSH daemon (sshd) provides a secure alternative to telnet, rlogin, rsh, rcp, and FTP by encrypting traffic SUSE Linux Enterprise Desktop Administration 66

Summary (continued) • SSH uses a combination of asymmetric and symmetric encryption and supports several standard encryption algorithms • You can configure the SSH type, authentication, and encryption types in the SSH server configuration file /etc/sshd_config • You can generate asymmetric SSH encryption keys using the ssh-keygen command view them using the ssh-keyscan command • You can use the vino-preferences command to configure a VNC server SUSE Linux Enterprise Desktop Administration 67