Electronic Commerce Richard Henson University of Worcester April



































- Slides: 38

Electronic Commerce Richard Henson University of Worcester April 2008

Week 9: On-line Payment Systems and Secure Networks n Objectives: Ø explain how an on-line buyer can be authenticated Ø describe how the buyer can be reassured during the fulfilment process Ø explain the acronym VPN and how part of the Internet can become a VPN Ø apply principles of “after sales service” to on-line trading Ø exercise greater control over web page data extracted from databases

Authenticating the Buyer n E-commerce systems provide a range of options for rapid on-line payment: Ø by credit card Ø by debit card Ø by agreed credit terms with the vendor n The following methods are also included, but are non-digital and slow the process down Ø by cheque Ø by bankers draft

Authenticating the Buyer n Whichever of the rapid payment methods is used… Øbuyer needs to be authenticated by the ecommerce site n This requires on-line communication with a financial institution » must be via Internet » fixed IP address needed n site must be secure – therefore must use a secure protocol

Authenticating the Buyer n Financial institutions only tend to communicate via Internet with trusted sites Øvendor would need to go through rigorous procedures to become such a site Øeasier to outsource and hire a Merchant Services Company to act as the trusted site » e. g. World. Pay, Netbanx, Pay. Pal

Authenticating the Buyer n The merchant service does the following: Ø connects the e-commerce site via secure link to their secure server Ø captures buyer details on their secure server Ø connects via secure link to an on-line financial institution Ø passes buyer details to on-line financial institution n It is then up to the financial institution to deal with the prospective sale…

Authenticating the Buyer The financial system uses the personal details supplied to authenticate the buyer and authorise payment n Three outcomes are possible: n Øauthenticated and authorised Øauthenticated but not authorised » e. g. over credit limit Ønot authenticated » buyer details incorrect i. e. not matching records or inconsistent

Arranging for Payment n Once the buyer has been authenticated and authorised Øpayment can be taken from the account The merchant services company will be charged for accessing the secure financial network n It therefore makes sense for authentication and payment to both occur during the same “session” on the secure financial network n

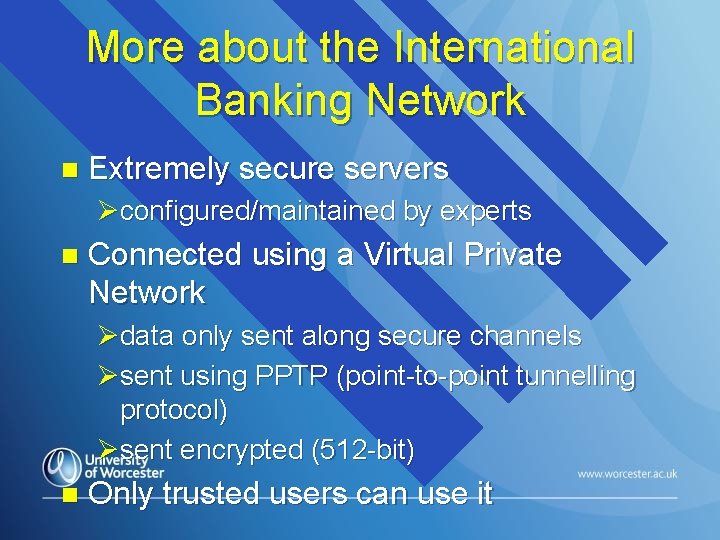
More about the International Banking Network n Extremely secure servers Øconfigured/maintained by experts n Connected using a Virtual Private Network Ødata only sent along secure channels Øsent using PPTP (point-to-point tunnelling protocol) Øsent encrypted (512 -bit) n Only trusted users can use it

Virtual Private Networks n Can be completely private Øa mesh of dedicated private lines n Can use the Internet. . . Øobvious security implications…

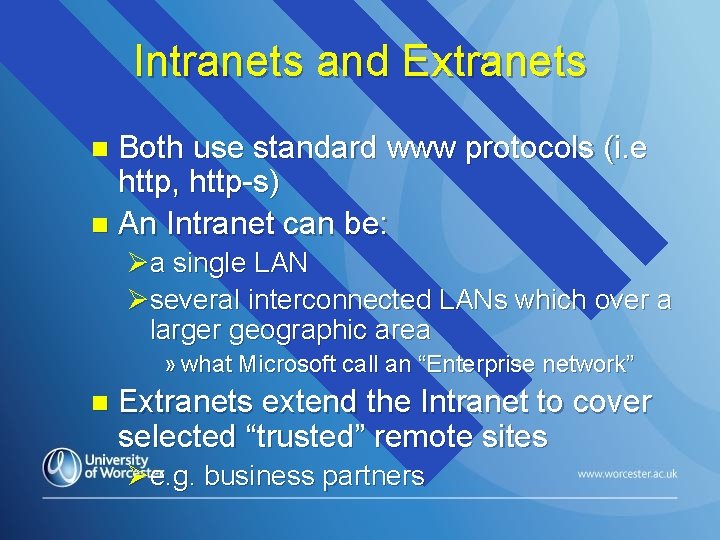
Intranets and Extranets Both use standard www protocols (i. e http, http-s) n An Intranet can be: n Øa single LAN Øseveral interconnected LANs which over a larger geographic area » what Microsoft call an “Enterprise network” n Extranets extend the Intranet to cover selected “trusted” remote sites Øe. g. business partners

Creating an Extranet n Can use private leased lines to link sites Øsecure, but expensive Ødo not need to use http, etc. n Can also use the Internet: Øsecurity issues need resolving Øvery little cost Øuse client-server web applications across different sites

Extranets and Virtual Private Networks An Extranet is not necessarily a secure means of transmitting data n Data should be secure on the servers (if set up properly) n Data sent using HTTP on top of TCP/IP can easily be intercepted n A VPN carries sensitive data, which must not be intercepted. . . n

VPNs on the Internet n Four techniques can be used to enhance security: Øuse of secure channels, rather than packet switching Øsecure encryption techniques Øsecure protocol such as http-s for sending/receiving data Ø“tunnelling” protocol such as PPTP » hides the data within other data

More about PPTP n Sponsored by MS and CISCO ØProposal for consideration by IETF n Extension of PPP ØAllow organisations to extend their own corporate network by using private “tunnels” over public Internet ØSecure connection over public networks ØEffectively using WAN as a single large LAN

Secure Data Transfer Standards n Four technologies that have been developed especially to enable secure transactions over the Internet: Ø HTTP-S : secure http Ø SSL : Secure Sockets Layer (most used : Netscape) Ø SET : Secure Electronic Transaction (Mastercard/Visa) Ø Digital signature technology

SSL Secure Sockets Layer n Developed by Netscape for browser participation in Internet security n Provides encryption of http packets on TCP/IP routes between Internet hosts n Not been accessed by hackers so far n Most commonly used protocol for ecommerce transactions, despite the emergence of SET (next slide…) n

SET n n n Secure Electronic Transactions Developed by credit card companies Based on the idea of a digital certificate Ø customer and the merchant identity both validated or “certified” n A need for “trusted” agencies Ø who decides who is trustworthy? Ø banks & financial institutions?

Issues surrounding on-line payment n Potential shoppers suspicious about security Ødoubts heightened by reporting of the media n In time. . . ØInternet will become a more common place to do business ØShoppers will gain experience of the advantages of buying on-line

Current Best Practice Take payments by credit card through a secure server n Creators of shop@ssistant recommend the use of a secure transaction service n Ø“major contribution to the potential viability of any e-commerce site on the Internet”

Reassuring the Shopper n Use of a secure transaction service makes sure that: Øcredit card details are being transmitted securely Øcredit card details are not being held on any computer system where they could be compromised.

Reassuring the Shopper n When the shopper is transparently transferred to the secure server Øthe secure server icon is displayed in his browser Ødesigned to promote a feeling of confidence in the mind of the shopper when using this service

Reassuring the Shopper n Shopper Dealing with a nationallyknown, branded supplier of credit card services Øauthorised to carry the logos of the card issuers on their site Øactive participation of the credit card issuers ’and merchant services ’ organisations.

Reassuring the merchant! n The existence of a secure network for credit card transactions helps the merchant too: Øcard details are never passed to the merchant ’s site Ønot involved at all in the secure data transmission Øhas no possibility to take, see or store the card details Øeffectively removed from the possibility of collusion in any card malpractice

Reassuring the merchant! n Flexibility in taking payments is assured since all of the world ’s major credit and debit cards are accepted by the transaction services

Reassuring the merchant! the merchant will know whether the shopper has good credit to cover the value of the goods before completing processing of the order n When the merchant receives an e-mail from the transaction service provider confirming payment, the money is almost as good as in the bank! n

Fulfilment - getting the goods to the customer n Includes: Øcustomer service Øcommunications (e. g. by email) Øwarehousing Øshipping Østorage Øinsurance

Payment and Fulfillment n Agreed convention of on-line trading that payment is not taken until the goods have been “picked” Øtaken out of the warehouse in preparation for delivery Whole process of authentication and payment is therefore delayed until the product is about to be picked n Errors in customer details not discovered until picking takes place! n

Payment and Fulfillment n If an authentication error does occur Øthe potential buyer is emailed, explaining the problem Øthe picking process is suspended n If authentication is successful Øbuyer is emailed » informed that product has been picked Øpicked product goes to delivery stage

Issues concerning Fulfillment n If: Øeither goods do not arrive Øor buyer is not satisfied with the goods The buyer has a right to a refund n Under recent EU law the refund must occur before goods are returned n

Issues concerning Fulfillment n Fraud could occur: Øsite itself could be fraudulent » buyers should look out for a secure connection window » if no window, don’t supply card details ØIf fraud has occurred, and e-commerce site is: » not to blame… » unable to pay Øcredit card company will usually pay the refund

Issues concerning Fulfillment also includes after-sales service n Example: if a computer has been purchased, and the buyer has a problem, there need to be good communication channels available: n Øtelephone - call centre if high call volumes can reasonably be expected Øemail - quick response required!

Product Pages – a final word… n n n As you only have a small number of products, a product summary for each can be included on a single page However, that summary page should also include a link to a unique page for each product Thanks to parameter passing between pages, this can be achieved with just a single “master” page, and a single “detail” page

Dreamweaver and passing parameters – 1 n n n The master page must include a column for each record with a hyperlink to the detail page The hyperlink must be appended by a get (? ) construct, which passes a field that has a unique value for that record The link then becomes long and potentially “scary”, but this is essential for passing data to another web page

Dreamweaver and passing parameters - 2 n When navigating from “master” to “detail”, there is a need to make sure that… Ø the correct fieldname is selected when the link is created using “make link” option Ø the correct parameter is chosen for passing the appropriate value for that field to the detail page n This parameter needs to be picked up by the detail page and an SQL statement used to filter the data in the relevant product dataset

Passing Parameters & “Scary Strings” n Dreamweaver shields the non-mathematician from coding as much as possible… Ø but sometimes the variables used for passing data within or between pages just have to be “scary strings” Ø if you don’t want to engage with programming logic that’s understandable » Just remember when typing such strings that: n n every “begin”({) has an “end” (}) every “start quotes” has an “end quotes” » also, remember that Dreamweaver does colour coding for its programming code, and this could be a useful way to detect typing errors (we all make them!)

Dreamweaver and passing parameters - 3 n The detail page needs to know about the parameter fieldname in order to correctly make use of the parameter value passed from the master page in its SQL query Ø both can be achieved when the dataset wizard is used to filter the data to be displayed Ø just use the “advanced” option » parameter section just needs a fieldname that corresponds to the SQL query n a wizard will create the “scary string” so no worries » main SQL statement needs “where fieldname=? ” to put the parameter value in the right place

Products: Control over asp. net product pages n n In a real e-commerce site, it is unlikely that all on-line products can be displayed on a single page In such cases, a “category” field is included in the products table, and product pages are accessed via “category” pages Ø category number can then be passed as a parameter from a master page to select products of a particular category for the “detail page”
 Henson trust manitoba
Henson trust manitoba Phoebe henson
Phoebe henson Kentucky state university mascot
Kentucky state university mascot Location-based commerce (l-commerce)
Location-based commerce (l-commerce) The legal environment of electronic commerce
The legal environment of electronic commerce Enterprise-class electronic commerce software:
Enterprise-class electronic commerce software: The internet the web and electronic commerce
The internet the web and electronic commerce Proses bisnis dalam kerangka electronic commerce
Proses bisnis dalam kerangka electronic commerce Electronic payment systems for e-commerce
Electronic payment systems for e-commerce Enterprise-class electronic commerce software:
Enterprise-class electronic commerce software: Retailing in electronic commerce products and services
Retailing in electronic commerce products and services Web based tools for electronic commerce
Web based tools for electronic commerce Edi e-commerce
Edi e-commerce Integrity in e commerce
Integrity in e commerce Electronic commerce payments inc
Electronic commerce payments inc Electronic contract law
Electronic contract law Secure electronic commerce
Secure electronic commerce Define edi in e commerce
Define edi in e commerce Pure electronic commerce
Pure electronic commerce Remedi electronic commerce group
Remedi electronic commerce group Electric commerce
Electric commerce Chapter 2 the internet the web and electronic commerce
Chapter 2 the internet the web and electronic commerce Payment systems for electronic commerce
Payment systems for electronic commerce An electronic is the electronic exchange of money or scrip
An electronic is the electronic exchange of money or scrip Electronic field production
Electronic field production Looking for richard
Looking for richard Hidden rules among classes
Hidden rules among classes Worcester county asylum
Worcester county asylum Hells angels worcester
Hells angels worcester Worcester polytechnic institute chemical engineering
Worcester polytechnic institute chemical engineering Inspectors in worcester
Inspectors in worcester How does this political cartoon depict president jackson
How does this political cartoon depict president jackson Worcester v georgia
Worcester v georgia Sequoyah cherokee leader
Sequoyah cherokee leader Worcester v georgia
Worcester v georgia Worcester v georgia
Worcester v georgia Exzellent worcester sauce
Exzellent worcester sauce North high school worcester
North high school worcester Worcester v. georgia
Worcester v. georgia