COMP 2113 Introduction to Electronic Commerce Richard Henson



















- Slides: 42

COMP 2113 Introduction to Electronic Commerce Richard Henson University of Worcester February 2008

Week 2: IT infrastructure for e-commerce n Objectives: Ø identify basic IT components required for a business e-commerce solution Ø classify computer networks according to size, topology, and administration Ø describe what a communications protocol is and explain why “open source” has become an issue Ø choose an appropriate method of access to the Internet for a single computer and a network

Required Technologies for E-Commerce Networks & network security n Communication software n The Internet & the World Wide Web n Email clients and servers n Web Servers n Web Browsers n Web Pages n

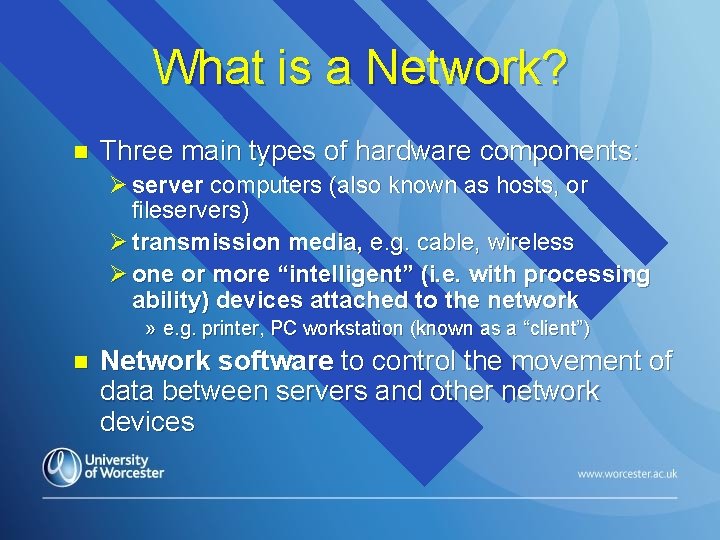
What is a Network? n Three main types of hardware components: Ø server computers (also known as hosts, or fileservers) Ø transmission media, e. g. cable, wireless Ø one or more “intelligent” (i. e. with processing ability) devices attached to the network » e. g. printer, PC workstation (known as a “client”) n Network software to control the movement of data between servers and other network devices

Classification of Networks n Most commonly used criteria: ØSize » how far the cables have to travel ØAdministration » Peer-peer » Client-server ØTopology » how the computers are connected together

Classifying networks by size n Local Area Network (LAN) ØRarely larger than about 2 km n Metropolitan Area Network (MAN) ØUp to 50 km n Wide Area Network (WAN) ØCould cover whole planet!

Local Area Network (LAN) n n n Most organisational networks are LANs Could have anything between one and many thousands of users Controlled within a single organisation All cabling digital, fast, and internally owned An organisation may have two or more LANs, which may be interconnected for the interchange of data

Wide Area Network (WAN) Connections between organisations n Can use: n Øanalogue telephone link ØDigital telephone link » ISDN » ADSL ØDedicated digital line » leased » privately owned n The Internet is a worldwide WAN using high bandwidth digital dedicated lines

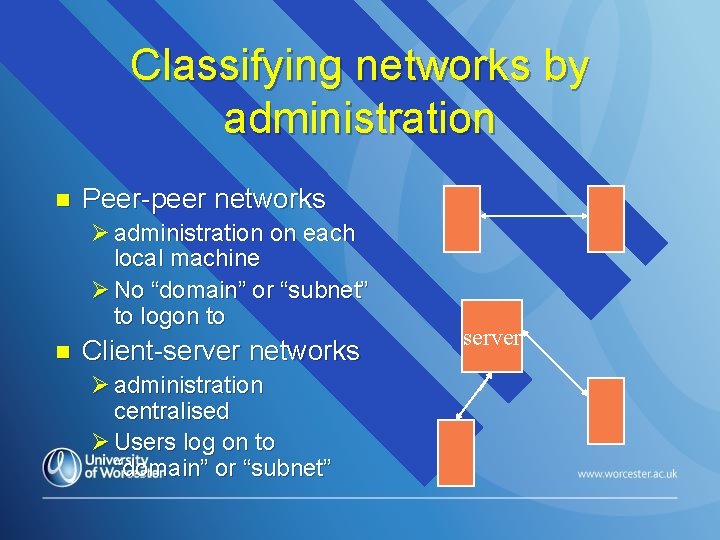
Classifying networks by administration n Peer-peer networks Ø administration on each local machine Ø No “domain” or “subnet” to logon to n Client-server networks Ø administration centralised Ø Users log on to “domain” or “subnet” server

Peer-Peer (P 2 P) networks n All users have the following responsibilities: ØSecurity & network administration Øaccess to services and resources n Generally OK if: Øvery network is very small ØUsers are trustworthy and know what they are doing! n Complexity grows very rapidly with increasing numbers of workstations

Client/Server Networks n Distributed computer systems that enable many users to access information n Machine that contains the information being accessed is called the server n User's computer is called the client n Network connection only made when information needs to be accessed by a user Ø therefore very efficient

Communications between Client and Server n Communication Ø across the network Ø Client runs “client software” Ø Server runs “server software” Ø all computers use a common protocol n Internet managed as peer-peer, but most Internet transactions based client-server Ø Internet host computers can play either role… » client or server

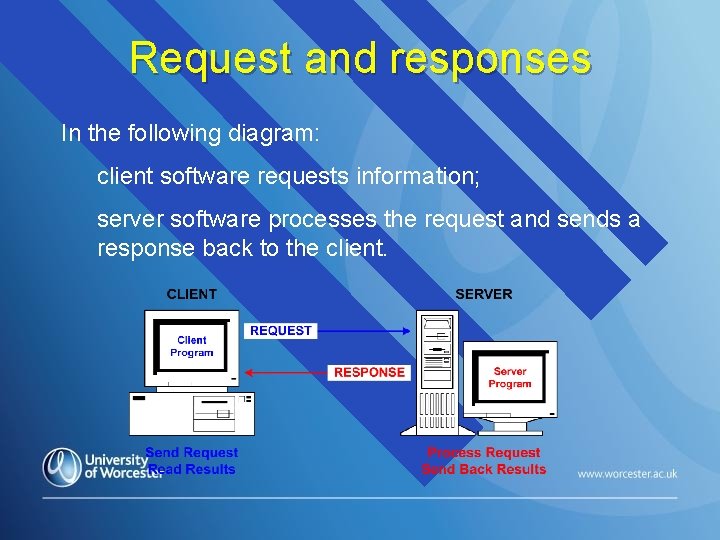
Request and responses In the following diagram: client software requests information; server software processes the request and sends a response back to the client.

Network characteristics n n Electrical connections between computers ESSENTIAL for the client-server interactions to occur Either use a physical conductor e. g. Ø optical fibre Ø coaxial copper Ø copper (twisted pair) n Or using electromagnetic waves Ø infra-red Ø radio waves Ø microwaves

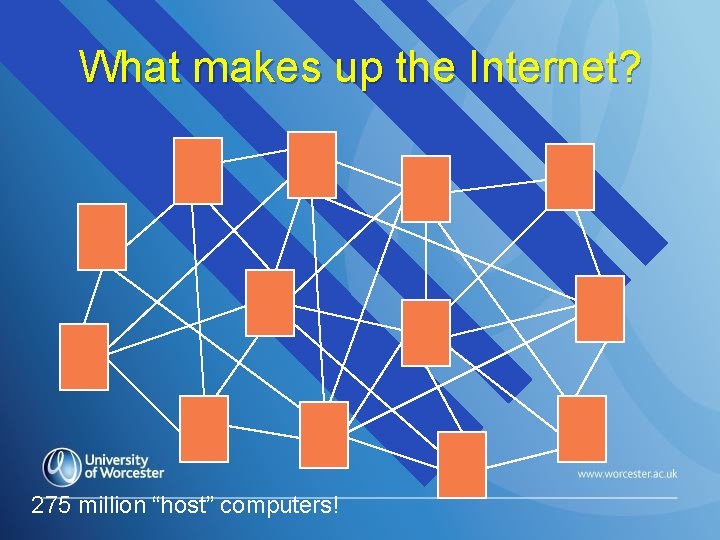
What makes up the Internet? 275 million “host” computers!

Internet Server Computers n n n Very powerful Managed 24 hours a day Use a secure operating system Ø UNIX (e. g. LINUX) Ø Windows 2000, XP or 2003 n n n If properly configured, very secure against access by unauthorised users It should therefore be impossible for such persons to access private data But… are there enough trustworthy UNIX and WINDOWS SERVER experts to manage 275 million computers properly?

Communications Protocols n n n The sets of rules and procedures used by computers when they communicate with one another Many protocols produced over the years by manufacturers HOWEVER… the most popular set of protocols (TCP/IP) was produced by academics Ø used in conjunction with packet-switching Ø developed for the military » Perhaps surprisingly… inherently not secure!

Internet Protocols n A simplified model of network protocols regards communication as taking place through 4 software layers: Ø Application layer – FTP, HTTP and SMTP » concerned with what actually appears on the screen display Ø Transport or Host-Host - TCP protocol Ø Internet layer - IP protocol Ø Physical Network access layer – software held on network card

Why choose TCP/IP? n Reasons partly historical: Ø evolved as an Internet protocol & got influential Internet community seal of approval) n Partly academic: Ø fitted well with the OSI “open source” software model n Partly technical: Ø highly robust, and reliable Ø designed to get messages through even in the event of a nuclear attack

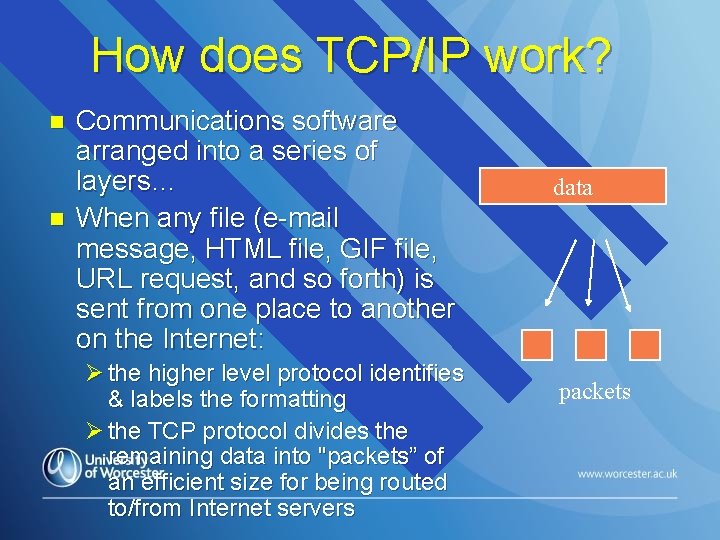
How does TCP/IP work? n n Communications software arranged into a series of layers… When any file (e-mail message, HTML file, GIF file, URL request, and so forth) is sent from one place to another on the Internet: Ø the higher level protocol identifies & labels the formatting Ø the TCP protocol divides the remaining data into "packets” of an efficient size for being routed to/from Internet servers data packets

How does data get sent across a network? n Each communications protocol uses a defined packet size ØTCP/IP size typically 768 bytes n Packets: Øconverted into binary (0/1) Øbinary becomes high/low electrical signals Øsignals sent across the network…

Data transmission Rates n n n Amount of data that can be simultaneously sent/received along communications channels is known as bandwidth low bandwidth channels - transfer rate measured in Kilobits/sec medium/high bandwidth - measured in Megabits/sec

Data transmission Rates Fastest on LANs - up to 1000 Mbits/sec n Bandwidth between Internet computers is usually high - 2 Mbits/sec upwards n Because the Internet is so popular even high bandwidth channels become congested n Pressure to keep increasing bandwidth between Internet computers n

Connecting to the Internet n From a single computer: Ø Analogue dial-up to an ISP via modem (max 50 Kbits/sec) Ø ISDN line to an ISP (128 Kb/sec or more) Ø ADSL line to an ISP (2 -8 Mb/sec or more) n Through a network Ø may need to connect a number of computers to the Internet Ø more bandwidth required Ø further options available…

Alternatives for linking the local network with the Internet n Use a standard telephone link (not digital) Ø cost (minimal) – usually a local call plus rental Ø speed – always relatively slow, because data has to be converted from/to digital during sending. Even slower on a network! n Use a digital (ISDN) telephone link Ø cost – VERY expensive Ø speed – faster than analogue line n n Use ADSL, ADSL business (fixed IP address) Use a dedicated digital link Ø Cost – expensive, but usually a fixed fee Ø Speed – can be very fast, but at considerable extra cost…

IT infrastructure required to put a company network “on-line” n n A secure internal “client-server” computer network Typical networking server software Ø Windows NT/2000 Ø Unix (most likely Linux) n A Firewall to separate the internal network from the External (i. e. Internet) network

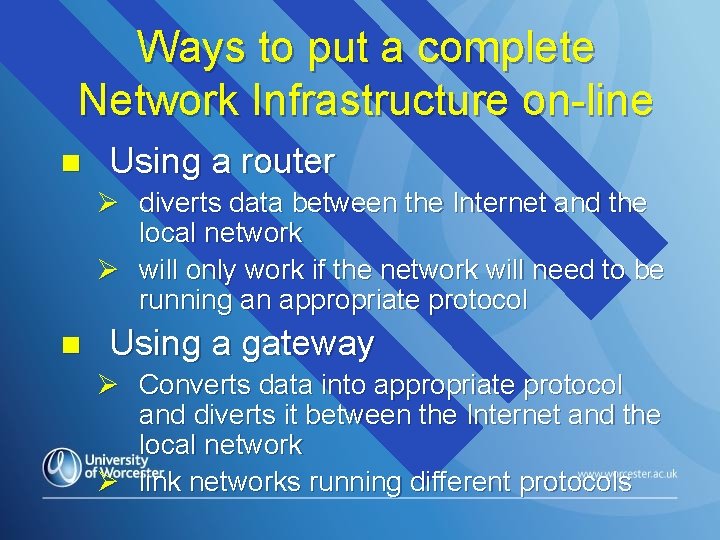
Ways to put a complete Network Infrastructure on-line n Using a router Ø diverts data between the Internet and the local network Ø will only work if the network will need to be running an appropriate protocol n Using a gateway Ø Converts data into appropriate protocol and diverts it between the Internet and the local network Ø link networks running different protocols

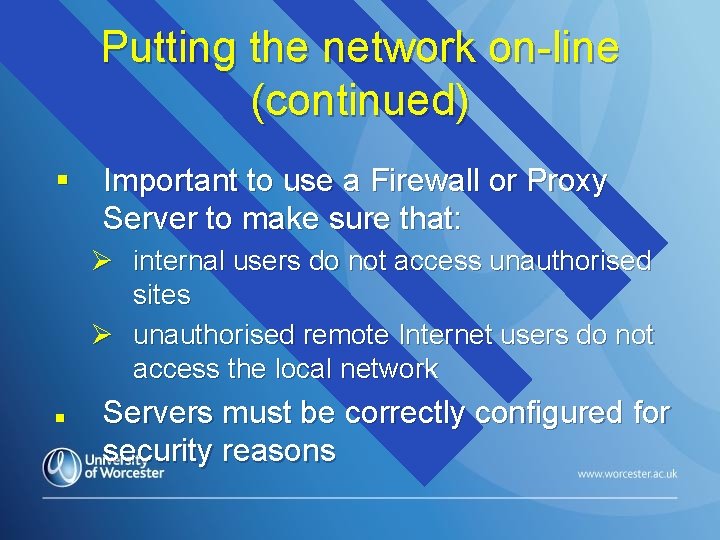
Putting the network on-line (continued) § Important to use a Firewall or Proxy Server to make sure that: Ø internal users do not access unauthorised sites Ø unauthorised remote Internet users do not access the local network n Servers must be correctly configured for security reasons

Putting the network on-line (continued) n n n Secure connections can be made with credit card authorisation and payment sites using “Merchant Server” software Regular monitoring of the network is essential to ensure that unauthorised users are not trying to gain access A digital connection of some kind is needed between the router/gateway and a computer connected to the Internet

Choosing a partner – an ISP (Internet Service Provider) n n Only the largest corporate enterprises are likely to be part of the Internet Most businesses need to find a partner who will provide the link between the connection medium and the Internet Many possibilities – pays to shop around Important criteria: Ø Average rate of transfer of data between ISP system and the main Internet backbone Ø ISP availability record (ideally 24 hours/day, 365 days/year)

Internet Communication Types relevant to E-commerce n Data: Ø as/with web pages Ø as with data files n Messages Ø electronic equivalent of P 2 P letters » Email… » SMS… » “Instant” messaging

Communicating Messages Electronically via E-mail

E-mail: a brief overview n Allows you to send the electronic equivalent of a letter to other people Ø anywhere in the world Ø very quickly Ø with very little expense n n n Can also be the most convenient way to leave someone nearby a message Can also send/receive messages in particular formats (e. g. EDI format) Also, text/graphics/sound/video attachments can be included

LAN E-mail & Internet E-mail n Both use mailboxes for storing mail on servers n LAN e-mail: Ø all mailboxes on one server Ø e-mail is simply uploaded to and downloaded from the server n Internet e-mail Ø requires the transmission of messages between mailboxes on servers in different networks Ø mechanism therefore much more complicated

Features of a Client-Server E-mail system n Email client software required: Ø downloads mail from mailbox on the server: Ø connects to a LAN server or Internet Server Ø provides an environment for reading and managing e-mail Ø allows sending of e-mail to a server

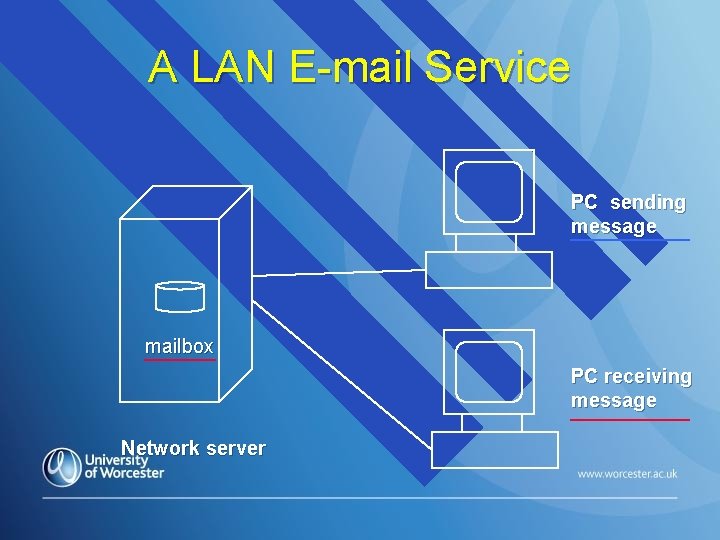
A LAN E-mail Service PC sending message mailbox PC receiving message Network server

A LAN E-mail Service Requires a client-server network n Good example of a client-server application: n ØThe email client software (e. g. Pegasus) runs on a client computer, and accessed by the user ØThe email server software (e. g. Mercury) provides user mailboxes, and controls access to them ØThe server computer that holds the mailboxes is known as a mail server

An Internet E-mail Service n n To send and receive email, the mail server needs to be connected to the Internet Compared to LAN mail, and Internet server will also therefore ADDITIONALLY need to control: Ø the sending of email to remote servers Ø receipt of email from remote servers Ø putting received email messages into the right mailbox

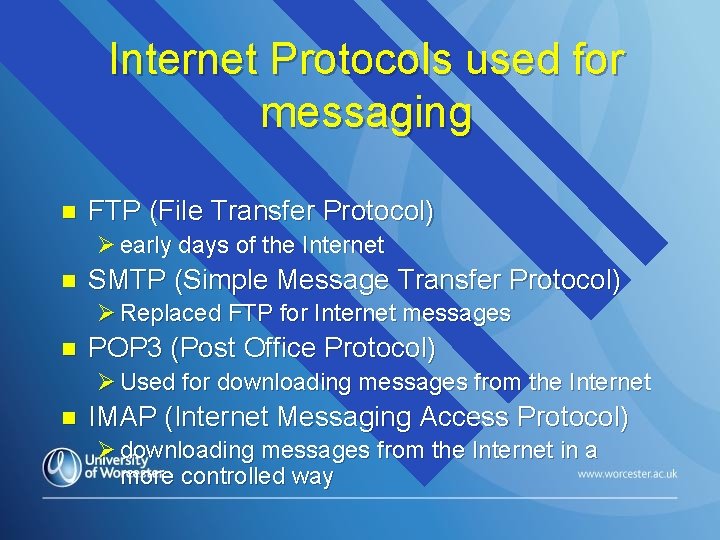
Internet Protocols used for messaging n FTP (File Transfer Protocol) Ø early days of the Internet n SMTP (Simple Message Transfer Protocol) Ø Replaced FTP for Internet messages n POP 3 (Post Office Protocol) Ø Used for downloading messages from the Internet n IMAP (Internet Messaging Access Protocol) Ø downloading messages from the Internet in a more controlled way

Encryption/Decryption of E-mail n n n Text messages contain a stream of ASCII codes Easy for anyone intercepting the message to read One easy form of encryption is to use a mathematical operation to create an encrypted code before sending Operation can be reversed on arrival (decryption) to reproduce the original ASCII codes However, anyone who knows how the data was encrypted can easily decrypt it… More sophisticated systems available e. g. public/private key encryption

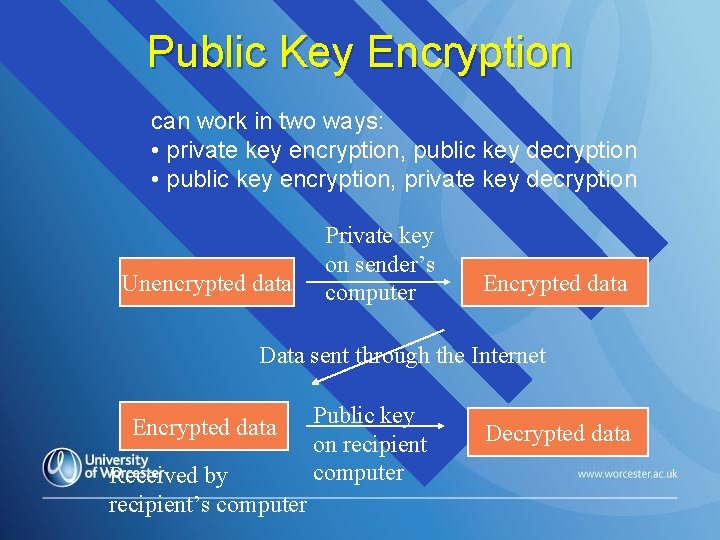
Public Key Encryption can work in two ways: • private key encryption, public key decryption • public key encryption, private key decryption Unencrypted data Private key on sender’s computer Encrypted data Data sent through the Internet Encrypted data Received by recipient’s computer Public key on recipient computer Decrypted data

That’s all Folks!