Electronic Commerce q Electronic commerce o Growing popularity






















































- Slides: 67

Electronic Commerce q Electronic commerce: o Growing popularity o Billions of dollars at stake o A major proving ground for computer, network, and Internet security mechanisms q Challenges that electronic commerce must deal with: o Protecting intellectual property on the Internet o Guarding users’ online privacy o Establishing acceptable electronic payment systems Chapter 14 Electronic Commerce 1

What is Electronic Commerce? q q Electronic commerce (or e-commerce) encompasses all business activities that are conducted using computer-mediated networks Subcategories: o Business-to-consumer (a. k. a B 2 C or e-retail) consumers purchasing goods and services (mostly over the Internet) § According to the Census Bureau, there was $8. 7 billion in eretail sales in the last quarter of 2000 (~1% of the $856 billion in retail sales) o Business-to-business (a. k. a. B 2 B) - transactions between businesses over computer networks o Support transactions (e. g. recruiting employees, holding virtual meetings, managing inventory, etc. ) Chapter 14 Electronic Commerce 2

E-Commerce – Benefits and Challenges q Benefits: o For businesses: § Increased sales § Decreased costs o For consumers: § Increased choice § Increased convenience § Decreased prices q Challenges: o Protecting intellectual property o Guarding online privacy o Establishing acceptable electronic payment systems Chapter 14 Electronic Commerce 3

Copyright q q Copyright - the notion that the creator of an original work has certain rights to restrict the work’s duplication or distribution Copyright protects: o o o o q Literary works Musical works Dramatic works Sculptures Photographs Movies Any other form expression conveyed using a tangible medium Copyright does not protect: o Ideas, processes, concepts, principles, or other non-tangible articles Chapter 14 Electronic Commerce 4

Copyright (cont) q Rational for copyright: o In order to encourage people to create new and useful works, creators must be granted protections that enable them to control their work and profit from it q Legal status of copyright (in the U. S. ): o Article I, Section 8 of the U. S. Constitution grants Congress the power to “promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries. ” o The Digital Millennium Copyright Act (DMCA) of 1998 § Circumvention of technological measures employed by owners to protect (restrict access and copying) their works § Tampering with copyright management information Chapter 14 Electronic Commerce 5

DMCA Controversy q q q July, 2001, Dmitry Sklyarov, a Russian Ph. D. student visiting Las Vegas for a computer conference Arrested by U. S. authorities and charged with violating the DMCA’s provision on circumventing copyright protection mechanisms Sklyarov had developed Advanced e. Book Processor software for a Russian company, Elcomsoft o Enabled users to convert digital files from Adobe Systems’ protected “e. Book” format to the unprotected PDF o Product was intended to allow blind people to access e. Books using a text-to-speech program (which cannot read e. Book files but can read PDF files) Chapter 14 Electronic Commerce 6

DMCA Controversy (cont) q q q April 2001, a team of researchers led by Princeton professor Edward Felten sought to publish their findings on the weakness of the proposed SDMI digital music access-control technologies The paper was withdrawn when the recording industry threatened to pursue legal action under the DMCA if the group published its methods for circumventing the SDMI protections Sklyarov’s case and a challenge by Felten to the DMCA on the grounds that it violates his First Amendment rights to freedom of speech are still pending Chapter 14 Electronic Commerce 7

Intellectual Property q q Intellectual Property - the notion that creation of the mind (whether tangible or intangible) also deserve protection Issues: o Value of intellectual property § Some companies now sell ideas or other intangible products § Depend on intellectual property rights to protect them from unfair practices by their competitors o Most countries have laws relating to copyright and intellectual property, but there are substantial variations from country to country § The Internet makes protected works available everywhere Ø Ø Unfair use in countries with weaker protection Abuse in countries with strong protections Chapter 14 Electronic Commerce 8

Intellectual Property (cont) q Issues (cont): o The ability of the Internet to widely distribute digital works quickly and cheaply § Consider analog music albums: Ø Ø Easy to copy • Duplication process resulted in degradation of the recording Hard to distributing copies widely § Consider digital music files: Easy to copy • An exact digital copy can be made which is indistinguishable from the original Ø Easy to distribute widely • The Internet is well suited for wide distribution of files Chapter 14 Electronic digital Commerce 9 Ø

Intellectual Property Protection q q q The Paris Convention (1883) o Protected only patents, trademarks, and industrial designs o 14 member states The Berne Convention (1886) o Extended protection to various literary, musical, and artistic works The World Intellectual Property Organization (1970) o A special agency of the United Nations o Includes nearly ninety percent of the world’s nations as members states o Oversees the development and application of international standards for the protection of intellectual Chapter 14 Electronic Commerce 10 property

Cybersquatting q Cybersquatting - register an Internet domain name that is a trademark of other people or companies in hopes of profiting: o Attracting a large number of Internet users o Selling the domain name to the rightful owner q Rulings (by WIPO) o October, 2000: evicted a cybersquatter from the domain name madonna. com in response to a complain filed by pop singer Madonna § Other celebrities have won similar cases: Julia Roberts, Nicole Kidman, and Jimi Hendrix’ estate o February, 2001, rocker Bruce Springsteen failed in his attempt to wrest the domain name brucespringsteen. com from a fan Chapter 14 Electronic Commerce 11

Case Study of Intellectual Property on the Internet Napster is music-file sharing software q Created in 1999 by Shawn Fanning q More than 60 million users at it peak in popularity q Functionality: q o Locate songs o Download and store a digital (MP 3) copy for free o Listen to the song as often as desired Chapter 14 Electronic Commerce 12

Case Study: Napster (cont) q Ripping o Using software known as a ripper, individuals can: § Extract (or rip) tracks from commercial, copyrighted compact discs § Store them in the MP 3 file format § “Share” them with other Napster users Ø q Results: Copyright violation o Artists and record companies do not realize a sale each time one of their songs is transferred from one Napster user to another o Fewer people may buy CDs when they can obtain copies of any song on them for free Chapter 14 Electronic Commerce 13

File Sharers vs. RIAA q July, 2000 o Recording Industry Association of America (RIAA), a trade group representing most of the record companies seeks an injunction against Napster in Federal court o The injunction was granted with the judge ordering Napster to eliminate all copyrighted material from its service (Napster appeals) q March, 2001 o Injuction takes effect – Napster ordered to block trading of copyrighted songs o Napster vows to comply with the judge’s order and to continue serving uncopyrighted work while seeking a settlement with the music industry Chapter 14 Electronic Commerce 14

File Sharers vs. RIAA (cont) q March, 2001 – June, 2001 o Filtering techniques become more effictive o Napster usage declines markedly o Napster announces plans to transform into a paid-subscription service q July, 2001 - present o Napster song-swapping service defunct o Other song-swapping services gain popularity o RIAA sues song swappers Chapter 14 Electronic Commerce 15

The Secure Digital Music Initiative (SDMI) q SDMI is a consortium of about 200 companies representing: o The recording industry o Consumer electronics o Technology firms q Goal: to develop a voluntary, open framework for playing, storing, and distributing digital music in a protected form Chapter 14 Electronic Commerce 16

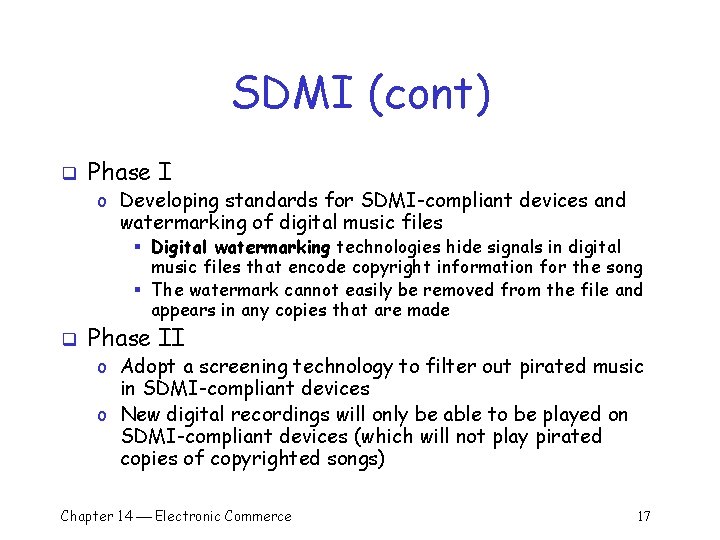
SDMI (cont) q Phase I o Developing standards for SDMI-compliant devices and watermarking of digital music files § Digital watermarking technologies hide signals in digital music files that encode copyright information for the song § The watermark cannot easily be removed from the file and appears in any copies that are made q Phase II o Adopt a screening technology to filter out pirated music in SDMI-compliant devices o New digital recordings will only be able to be played on SDMI-compliant devices (which will not play pirated copies of copyrighted songs) Chapter 14 Electronic Commerce 17

Electronic Commerce Summary q q q Electronic commerce encompasses all business activities that are conducted using computermediated networks Copyright - the creator of an original work has certain rights to restrict the work’s duplication or distribution Intellectual property - the ownership of creations of the mind whether tangible or intangible o Challenges: § Cybersquatting § Song swapping o Proposed legal solutions: DMCA, WIPO, RIAA lawsuits o Proposed technical solutions: SDMI Chapter 14 Electronic Commerce 18

Online Privacy What is online privacy and why is it important? q Addressing online privacy issues q o Government regulation o Self-regulation § P 3 P § TRUSTe o Technical solutions § The Anonymizer § Crowds Chapter 14 Electronic Commerce 19

Online Privacy q Most people safeguard their: o Medical history o Financial records o Other personal information q In order to avoid: o o q Loss of privacy Embarrassment Inconvenience Harm Legal status of individual privacy (in the U. S. ): o The fourth amendment of the U. S. Constitution grants citizens the right “to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures” by the government o Other statues Chapter 14 Electronic Commerce 20

Effect of the Internet on Privacy q q Increase in the amount of available information about individuals: o o Online people finders Electronic phone books Search engines E-mail directories o o Collection Correlation Analysis Use Easy automation of data: Chapter 14 Electronic Commerce 21

Addressing Online Privacy Issues q Governmental regulation o Example: library materials and video rentals § Subject to laws which stipulate that records cannot be kept about which titles (or even which types of titles) a particular person has borrowed o Online privacy has been studied by the Senate Judiciary Committee q Self-regulation o P 3 P – a standard format in which a web site can represent its privacy policy describing what personal information is being collected and how it will be used o TRUSTe - utilizes a trusted third party to certify that a web site adheres to certain basic privacy principles q Technical solutions o The Anonymizer – protects privacy by acting as proxy for web requests Chapter Electronic Commerce o 14 Crowds - simulates the anonymous nature of being part of a 22

The Platform for Privacy Preferences Project (P 3 P) Project by the World Wide Web Consortium q Goal: to define a standard format in which web sites can represent their privacy policies: q o o The entity stating the policy The types of data collected How the data will be used Other possible recipients of the data Chapter 14 Electronic Commerce 23

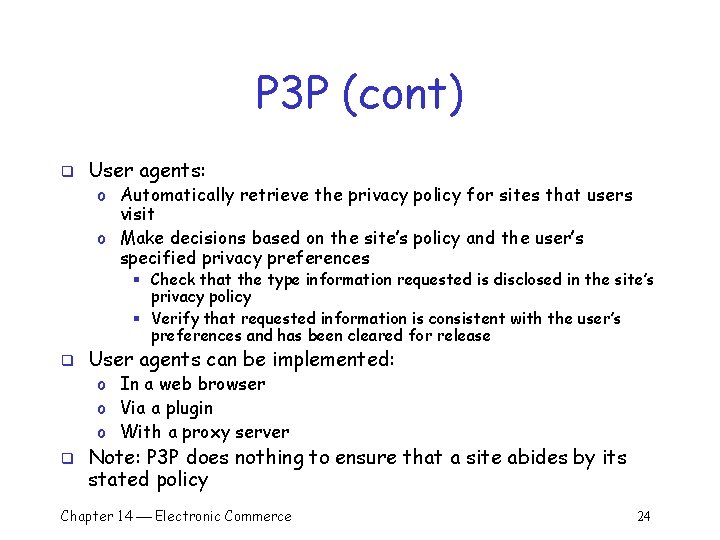
P 3 P (cont) q User agents: o Automatically retrieve the privacy policy for sites that users visit o Make decisions based on the site’s policy and the user’s specified privacy preferences § Check that the type information requested is disclosed in the site’s privacy policy § Verify that requested information is consistent with the user’s preferences and has been cleared for release q User agents can be implemented: o In a web browser o Via a plugin o With a proxy server q Note: P 3 P does nothing to ensure that a site abides by its stated policy Chapter 14 Electronic Commerce 24

TRUSTe An independent, non-profit organization founded by the Electronic Frontier Foundation q Privacy Seal Program: q o A trusted third party certifies that a web site adheres to certain basic privacy principles o Trusted third party issues a seal that member sites can display o Member sites are subject to ongoing oversight by that third party for compliance Chapter 14 Electronic Commerce 25

TRUSTe (cont) q Privacy principles: o Adoption and implementation of an acceptable privacy policy o Notice and disclosure of information collection and use practices o Giving users the opportunity to exercise control over their information o Security measures to help protect the privacy and integrity of personal information q TRUSTe oversight: o Initial and periodic reviews of the site by TRUSTe or other third party firms o Analysis of feedback and complaints from the Internet community o Seeding, whereby TRUSTe itself submits fictitious user information to a member site to verify that the information is not misused Chapter 14 Electronic Commerce 26

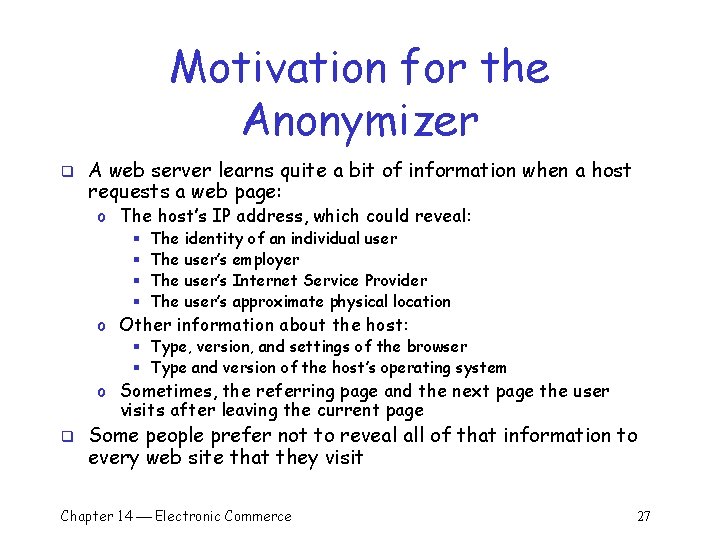
Motivation for the Anonymizer q A web server learns quite a bit of information when a host requests a web page: o The host’s IP address, which could reveal: § § The identity of an individual user The user’s employer The user’s Internet Service Provider The user’s approximate physical location o Other information about the host: § Type, version, and settings of the browser § Type and version of the host’s operating system o Sometimes, the referring page and the next page the user visits after leaving the current page q Some people prefer not to reveal all of that information to every web site that they visit Chapter 14 Electronic Commerce 27

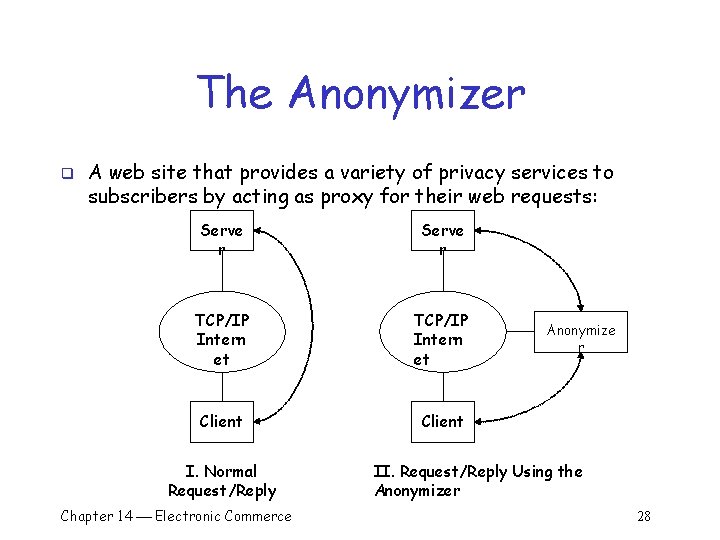
The Anonymizer q A web site that provides a variety of privacy services to subscribers by acting as proxy for their web requests: Serve r TCP/IP Intern et Client I. Normal Request/Reply Chapter 14 Electronic Commerce Anonymize r II. Request/Reply Using the Anonymizer 28

The Anonymizer (con) q Caveats: o The communication channel between a user and the Anonymizer is not secure § Possible that a user’s ISP or a machine on the path between the user and the Anonymizer can determine what sites a user is visiting § The Anonymizer offers a secure tunneling service at an additional cost o Subscribers must trust the Anonymizer § It learns a lot about them (including all the sites that they visit anonymously) o Requests/replies may follow an inefficient route o Anonymity can be circumvented by mobile code § E. g. A java applet that opens a network connection from the machine it runs on back to the server from which it was Chapter 14 downloaded Electronic Commerce 29

Crowds q Collect users into a group called a crowd which performs requests on behalf of its members o User joins crowd by running a process (called a jondo) on his/her local machine § Learn other current members of the crowd and cryptographic key shared by the crowd § Current members of the crowd are informed of your membership o Crowd members can issue requests through the crowd such that: § Servers can’t determine which crowd member initiated the request § Other crowd members can’t determine which crowd member initiated the request Chapter 14 Electronic Commerce 30

Issuing Requests Through the Crowd q q q All requests are sent to the jondo Jondo randomly chooses another member of the crowd and sends the request to them Whenever a crowd member receives a request from another crowd member it chooses either: o With probability p (where p>1/2): to send the request to another randomly selected member of the crowd o With probability (1 -p): to submit the request to the server q Request does not change from one jondo to the next o Each jondo can tell which other jondo sent it the request o Each jondo cannot tell whether its predecessor initiated the request or is just forwarding it q All communications between jondos is encrypted with the crowd key Chapter 14 Electronic Commerce 31

Receiving a Reply Through the Crowd q q q Every request takes some path through the jondos to the server Reply follows the same path (in reverse) back through the jondos and to the initiator Example: o Jondo 4 joins the crowd consisting of jondo 1, jondo 2, jondo 3, and jondo 5 o Jondo 4 constructs a request and sends it to jondo 3 o Jondo 3 receives the request and sends it to jondo 1 o Jondo 1 receives the request and sends it to jondo 4 o Jondo 4 receives the request and sends it to jondo 2 o Jondo 2 receives the request and sends it to the server o The server’s reply goes to jondo 2, jondo 4, jondo 1, jondo 3, and finally to jondo 4 Chapter 14 Electronic Commerce 32

Crowds Paths q Paths through the crowd remain static as long as possible o One path through the crowd for each jondo o Each jondo keeps track of its predecessor and successor for a given path o Each jondo knows where to send a request next based on its path identifier and the jondo from which it was received § Subsequent requests initiated by the same jondo follow the same path through the crowd even if the request is bound for a different server § Example: Ø Ø Jondo 4 generates a new request to a new server It still travels to the server through jondos 3, 1, 4, and 2 Paths through the crowd only change when jondos join Chapter 14 Electronic Commerce 33 or leave the crowd at which point all paths are q

Crowds – Anonymity Properties q q No single point at which a passive eavesdropper can compromise all users’ anonymity Server obtains no information about who initiated a request (except that it came from a member of the crowd) o Jondo originating the request always forwards it to a randomly chosen member of the crowd o Server receives each request from any member of the crowd with equal likehood o Sender of request is beyond suspicion (no more likely than any other member of the crowd to have originated the request) Chapter 14 Electronic Commerce 34

Crowds – Anonymity Properties (cont) q No jondo can learn the initiator of a request (unless it initiated the request itself) o Messages received from a predecessor on a particular path may have been originated by the predecessor or may have just been forwarded o Sender is probably innocent (no more likely to have originated a given request than to have not originated it) q No local eavesdropper who can observe all (and only) communication involving a user’s machine can determine the eventual destination of a request (unless the initiator winds up submitting the request itself) o Messages are encrypted and cannot be read by the eavesdropper Chapter 14 Electronic Commerce 35

Crowds – Risks and Limitations q If your jondo is the last on some path requests you did not initiate may be attributed to you o Plausible deniability q No mechanism in crowds to protect the privacy of the request contents from other crowd members o E. g. username and password, credit card number q Can be circumvented by mobile code that opens a network connection back to the server o E. g. java applets and Active X controls q Increases response times and network traffic Chapter 14 Electronic Commerce 36

Online Privacy - Summary q q Problem – privacy and personal information must be protected Possible solutions: o Government regulation o Self-regulation § P 3 P – a standard format in which a web site can represent its privacy policy describing what personal information is being collected and how it will be used § TRUSTe - utilizes a trusted third party to certify that a web site adheres to certain basic privacy principles o Technical solutions § The Anonymizer § Crowds Chapter 14 Electronic Commerce 37

Electronic Payment Systems q Needed thrive for electronic commerce to o Desirable properties o Systems based on credit cards § SSL-encrypted credit card numbers § Cyber. Cash o Systems based on digital money § Ecash § Net. Cash § Millicent Chapter 14 Electronic Commerce 38

Desirable Properties q Secure – resistant to forgery or alteration o Checks – bad; cash – good; credit cards – in between q Buyer anonymity o Checks and credit cards – bad; cash – good q Two-way – anyone can make or receive payment o Credit cards – bad; checks and cash – good q Off-line - neither the buyer nor the seller must communicate with a third party at the time of the transaction o Credit cards – bad; cash – good; checks – in between Chapter 14 Electronic Commerce 39

Using SSL and Credit Cards q Advantages: o Built on an existing infrastructure already used by merchants and customers) o Good protection against theft of credit card information in transit q Disadvantages: o o o Not anonymous Not off-line Not two-way Does not support micro-payments Merchant learns customer’s credit card number § Used by unscrupulous employees § “Accidental” charges by the merchant § Theft from merchant’s database by an intruder Chapter 14 Electronic Commerce 40

Cyber. Cash q Participants: o Customer o Merchant o Cyber. Cash server (CC) q Overview: o Customer creates a message containing credit card number and authorization to charge a specific amount: § (12345678, $37. 17) o Encrypts message using the public key of the CC server: § Encrypt((12345678, $37. 17), CCPublic) o Customer sends encrypted message to the merchant Chapter 14 Electronic Commerce 41

Cyber. Cash (cont) q Merchant receives encrypted message from customer: o Encrypt((12345678, $37. 17), CCPublic) q Merchant adds identification information to the message, signs it, and sends it to the CC server: o Encrypt((M, Encrypt((12345678, $37. 17), CCPublic)), MPrivate) q q q CC server decrypts message, verifies the credit card number, and returns authorization to the merchant The merchant returns a receipt to the customer Issues: o Merchant never learns the customers credit card information Chapter 14 Electronic Commerce o Does not operate off-line 42

Digital Money q Cash can be: o Spent anonymously § Buyer need not reveal his/her identity to a merchant § Issuer cannot track where people are spending their money o Carried out off-line and without authorization from a third party o Accepted by anyone as payment (and subsequently use to make other purchases) o Used without transaction fees § 2 -5% for credit cards § 1 -2% for checks q Problem: o Currency issued by most governments (paper bills and metal coins) do not lend themselves easily to electronic Chapter 14 Electronic Commerce 43 exchange

Ecash q q In 1990, David Chaum (creator of blind signatures) founded a company, Digi. Cash, which developed digital money called Ecash Overview: o o o Banks convert currency to ecash (and vice versa) User has an account with an ecash-enabled bank User withdraws ecash from his/her account Customer sends ecash to merchant Merchant sends ecash to bank for validation Merchant sends customer receipt Chapter 14 Electronic Commerce 44

Withdrawing Ecash Coins q Assume: o Alice has $100 deposited in an Ecash-enabled bank o Alice has a unique public/private key pair (APublic and APrivate) o The bank has a unique public/private key pair (BPublic and BPrivate) q q Alice wants to withdraw $50 (ten $1 Ecash coins, two $5 coins, and three $10 coins) Alice generates a random serial number for each coin: s 1, s 2, …, s 15 o o o Coin 1 = (one dollar, s 1) Coin 2 = (one dollar, s 2). . Coin 10 = (one dollar, s 10) Chapter 14 Electronic Commerce Coin 11 = (five dollars, s 11) Coin 12 = (five dollars, s 12) Coin 13 = (ten dollars, s 13) Coin 14 = (ten dollars, s 14) Coin 15 = (ten dollars, s 15) 45

Withdrawing Ecash Coins (cont) q Alice chooses a blinding factor, b, and uses it to blind the serial number of each coin: o o o o o Coin 1 = (one dollar, b*s 1) Coin 2 = (one dollar, b*s 2) … Coin 10 = (one dollar, b*s 10) Coin 11 = (five dollars, b*s 11) Coin 12 = (five dollars, b*s 12) Coin 13 = (ten dollars, b*s 13) Coin 14 = (ten dollars, b*s 14) Coin 15 = (ten dollars, b*s 15) Chapter 14 Electronic Commerce 46

Withdrawing Ecash Coins (cont) q Alice signs each coin with her private key and encrypts the result with the bank’s public key: Coin 1 = Encrypt((one dollar, b*s 1), APrivate), BPublic) Coin 2 = Encrypt((one dollar, b*s 2), APrivate), BPublic) … Coin 10 = Encrypt((one dollar, b*s 10), APrivate), BPublic) o Coin 11 = Encrypt((five dollars, b*s 11), APrivate), BPublic) o Coin 12 = Encrypt((five dollars, b*s 12), APrivate), BPublic) o Coin 13 = Encrypt((ten dollars, b*s 13), APrivate), B ) Chapter 14 Public Electronic Commerce 47 o Coin = Encrypt((ten dollars, b*s ), A ), o o

Withdrawing Ecash Coins (cont) q Alice transmits the blinded, signed, encrypted coins to the bank o Each coin is encrypted with the bank’s public key so only the bank will be able to decrypt it q q q The bank decrypts each coin and checks Alice’s signature The bank adds up the value of all the coins requested, and deducts that amount from Alice’s account The bank signs each coin with its private key and encrypts each signed coin with Alice’s public key Chapter 14 Electronic Commerce 48

Withdrawing Ecash Coins (cont) q The bank sends the blinded, signed, encrypted coins to Alice: o o o o o q Coin 1 = Encrypt((one dollar, b*s 1), BPrivate), APublic) Coin 2 = Encrypt((one dollar, b*s 2), BPrivate), APublic) … Coin 10 = Encrypt((one dollar, b*s 10), BPrivate), APublic) Coin 11 = Encrypt((five dollars, b*s 11), BPrivate), APublic) Coin 12 = Encrypt((five dollars, b*s 12), BPrivate), APublic) Coin 13 = Encrypt((ten dollars, b*s 13), BPrivate), APublic) Coin 14 = Encrypt((ten dollars, b*s 14), BPrivate), APublic) Coin 15 = Encrypt((ten dollars, b*s 15), BPrivate), APublic) Each coin is encrypted with Alice’s public key so only she will be able to decrypt it Chapter 14 Electronic Commerce 49

Withdrawing Ecash Coins (cont) q Alice decrypts the coins, checks the bank’s signature, and unblinds them: o o o o o Coin 1 = Encrypt((one dollar, s 1), BPrivate) Coin 2 = Encrypt((one dollar, s 2), BPrivate) … Coin 10 = Encrypt((one dollar, s 10), BPrivate) Coin 11 = Encrypt((five dollars, s 11), BPrivate) Coin 12 = Encrypt((five dollars, s 12), BPrivate) Coin 13 = Encrypt((ten dollars, s 13), BPrivate) Coin 14 = Encrypt((ten dollars, s 14), BPrivate) Coin 15 = Encrypt((ten dollars, s 15), BPrivate) Chapter 14 Electronic Commerce 50

Spending Ecash Coins q q q Alice selects goods she wishes to purchase at an online merchant who accepts Ecash as payment Alice selects a set of Ecash coins with which to pay Example: o Alice’s bill comes to $7 o Alice selects a set of Ecash coins valued at $7: § Coin 12 = Encrypt((five dollars, s 12), BPrivate) § Coin 2 = Encrypt((one dollar, s 2), BPrivate) § Coin 8 = Encrypt((one dollar, s 8), BPrivate) q Alice encrypts this set of coins with the merchant’s public key, MPublic, and transmits them to the merchant: o Encrypt((Coin 12, Coin 8), MPublic) Chapter 14 Electronic Commerce 51

Spending Ecash Coins (cont) q The merchant receives the coins and: o Uses his private key to decrypt them o Checks to see that their value equals the amount owed by Alice q The merchant attempts to redeem the coins with the issuing bank: o The merchant encrypts the coins using the bank’s public key and sends them to the bank: § Encrypt((Coin 12, Coin 8), BPublic) o The bank decrypts the message and checks each coin: § Its signature is valid § Checks its database of serial numbers for all coins it has issued that have already been spent Chapter 14 Electronic Commerce 52

Spending Ecash Coins (cont) q q Double spending - a common problem with many digital money schemes) A bank must insure that a user cannot spend the same coin twice (in payments to two different merchants) o A bank maintains a database of serial numbers for all coins it has issued that have already been spent o When a merchant attempts to redeem coins (before accepting them as payment), the bank checks to see that each coin’s serial number is not already in the database § Yes – add the serial numbers to the bank’s database, credit the merchant’s account for the value of the coins, notify the merchant that the payment has been accepted § No – notify the merchant that the payment has not been Chapter 14 accepted Electronic Commerce 53

Ecash - Properties q Ecash coins are: o Secure - users have very little chance of forging coins that a bank will accept or of altering coins issued by the bank to increase their value o Valid - anyone can use the bank’s public key to verify the signature on them o Unlinkable - the bank cannot link any coin to a blinded coin that it signed o Anonymous - when coins are returned to the bank it will not be able to determine: § Buyer is not required to disclose his or her identity to the seller § The issuing bank cannot link a payment to a specific user § No merchant, bank, or other third party can link two separate payments to the same user q Limitations: o Does not operate off-line Chapter Electronic 54 o 14 A bank must Commerce maintain a database of the serial number of every

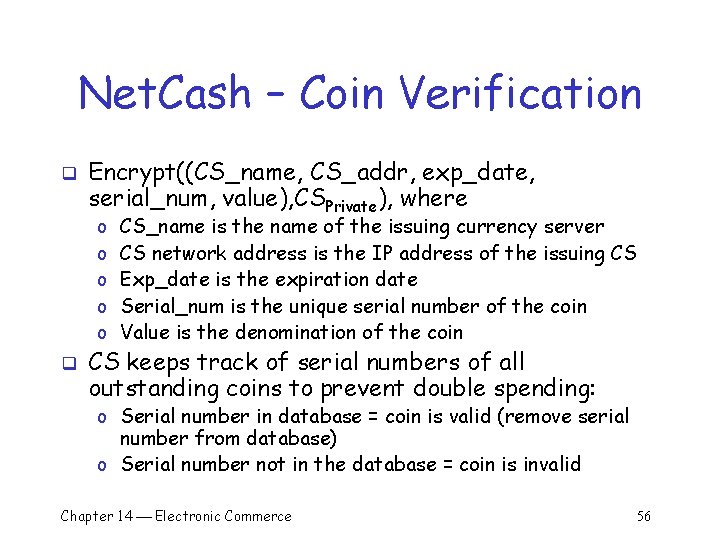
Net. Cash q q Developed by Information Sciences Institute of the University of Southern California Overview: o Currency servers (CS) convert between anonymous electronic currency and non-anonymous instruments o Each CS has a unique public/private key pair and a certificate for minting currency o CS services: § Conversion between coins and non-electronic currency § Coin verification § Coin exchange (for untraceability) Chapter 14 Electronic Commerce 55

Net. Cash – Coin Verification q Encrypt((CS_name, CS_addr, exp_date, serial_num, value), CSPrivate), where o o o q CS_name is the name of the issuing currency server CS network address is the IP address of the issuing CS Exp_date is the expiration date Serial_num is the unique serial number of the coin Value is the denomination of the coin CS keeps track of serial numbers of all outstanding coins to prevent double spending: o Serial number in database = coin is valid (remove serial number from database) o Serial number not in the database = coin is invalid Chapter 14 Electronic Commerce 56

Net. Cash – Coin Exchange q Anonymity o An issuing CS could store identity of the person to whom a coin was issued along with the coin’s serial number o When a merchant redeems coins the CS could determine who spent them q Net. Cash addresses this problem by allowing users to perform coin exchange: o Users can go to any currency server and anonymously exchange valid coins for new ones (issued by that CS) § CS 1 issues coins to Alice § Alice takes those coins to CS 2 § CS 2 contacts CS 1 to make sure the coins are valid (CS 1 doesn’t tell CS 2 to whom the coins were issued) § CS 2 issues Alice new coins Chapter 14 Electronic Commerce 57

Comparison of Ecash and Net. Cash q Anonymity o Ecash uses blind signatures o Net. Cash uses coin exchange (must trust issuing CS) q Storage requirements o Banks must store serial numbers of all ecash ever spent o Currency server must store serial numbers of all outstanding Net. Cash Chapter 14 Electronic Commerce 58

Milli. Cent q q Developed by Compaq Computer Corporation A micropayment scheme for transactions involving less than one cent: o Examples: stock quotes, online news stories, search engine queries q Based on scrip, currency that has intrinsic value but only with a particular merchant o Example: a pre-paid phone card has a set value, but it cannot be used to buy a hamburger or anything other than phone time from the issuer Chapter 14 Electronic Commerce 59

Milli. Cent Scrip q Milli. Cent scrip has the following fields: o Merchant_name – identifies the merchant that created the scrip o Value – the value of the scrip o Serial_number – unique identifier for this piece of scrip o Owner_ID – used to ensure that scrip can only be spent by the rightful owner o Expiration_date – the date on which the scrip expires o Properties – some general properties of the customer (e. g. age, state of residence, etc. ) o Certificate – allows validation of the scrip § A one-way hash of the contents of the scrip and a secret known only to the merchant § Certificate = Hash(Merchant_name, Value, Serial_number, Owner_ID, Expiration_date, Properties, Scrip secreti) Chapter 14 Electronic Commerce 60

Scrip Secrets q q q A merchant may have many different scrip secrets Some group of bits in the serial number determine which scrip secret to use to create the certificate Example: o Merchant has four different scrip secrets: scrip_secret 0, scrip_secret 1, scrip_secret 2, scrip_secret 3 o The first two bits in the serial number select which secret to use to generate the certificate: § § 00 = scrip_secret 0 01 = scrip_secret 1 10 = scrip_secret 2 11 = scrip_secret 3 Chapter 14 Electronic Commerce 61

Generating Scrip q Merchant generates a serial number o Assume that the first two binary digits in the serial number are 10 q Merchant generates a certificate: o Certificate = Hash(Merchant_name, Value, Serial_number, Owner_ID, Expiration_date, Properties, Scrip_secret 2) q The merchant records the serial number in its database of outstanding scrip Chapter 14 Electronic Commerce 62

Using Scrip q q Customer purchases a certain amount of scrip The merchant generates the scrip and sends it to the customer: o Scrip = (Merchant_name, Value, Serial_number, Owner_ID, Expiration_date, Properties, Certificate) q q Later, the customer submits scrip to the merchant as payment: Merchant checks that the customer has not tampered with the scrip o Use the scrip’s serial number to select the proper scrip secret o Recreate the certificate and check for a match Chapter 14 Electronic Commerce 63

Using Scrip q Merchant checks that the scrip has not already been spent: o The merchant checks to see that the serial number for that piece of scrip is in its database: § Yes – removed the serial number from the database and accept the scrip § No – scrip is not accepted (it has already been spent or has expired) Chapter 14 Electronic Commerce 64

Brokers q q Customers would not normally buy scrip directly from merchants Customers would buy scrip from intermediaries called brokers o Customers buy broker scrip from brokers o Brokers buy merchant scrip in bulk (and at a discount) from various merchants o Customers exchange broker scrip for scrip issued by a specific merchant q Result - the total number of accounts required is greatly reduced (especially for customers and merchants ) Chapter 14 Electronic Commerce 65

Milli. Cent - Properties q q q Secure Somewhat anonymous (brokers know what merchant a customer is requesting scrip for) Lower overhead costs = better suited for micropayments o The signature on scrip is created by a merchant, and its authenticity and integrity need only to be verified by that same merchant o A merchant need not communicate with any third party to validate the digital money being spent by a customer o A one-way hash function (rather than a public-key cryptosystem) can be used to produce the signature Chapter 14 Electronic Commerce 66

Electronic Payment Systems Summary q q Desirable properties – security, buyer anonymity, twoway, off-line Using credit cards: o SSL-encrypted credit card numbers § Some security, but merchant learns customer’s credit card number o Cyber. Cash § Merchant does not learn customer’s credit card number, but requires transaction to be cleared by a Cyber. Cash server q Using digital money: o Ecash – a digital money scheme based on blind signatures o Net. Cash – a digital money scheme based on currency servers o Millicent – a micropayment scheme based on scrip Chapter 14 Electronic Commerce 67