Dynamic Trust Management for Delay Tolerant Networks and



- Slides: 22

Dynamic Trust Management for Delay Tolerant Networks and Its Application to Secure Routing 1

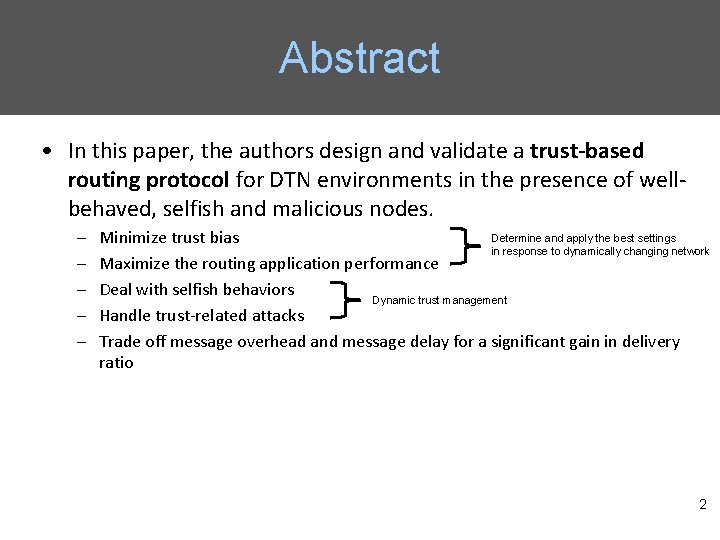
Abstract • In this paper, the authors design and validate a trust-based routing protocol for DTN environments in the presence of wellbehaved, selfish and malicious nodes. – – – Determine and apply the best settings Minimize trust bias in response to dynamically changing network Maximize the routing application performance Deal with selfish behaviors Dynamic trust management Handle trust-related attacks Trade off message overhead and message delay for a significant gain in delivery ratio 2

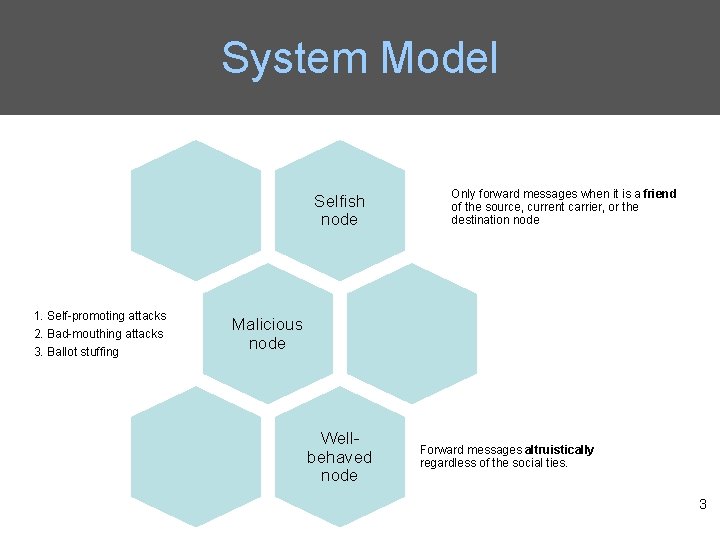
System Model Selfish node 1. Self-promoting attacks 2. Bad-mouthing attacks 3. Ballot stuffing Only forward messages when it is a friend of the source, current carrier, or the destination node Malicious node Wellbehaved node Forward messages altruistically regardless of the social ties. 3

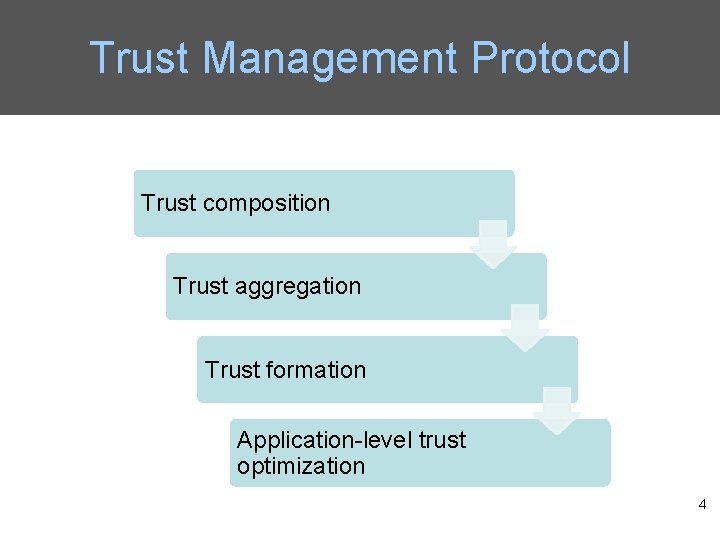
Trust Management Protocol Trust composition Trust aggregation Trust formation Application-level trust optimization 4

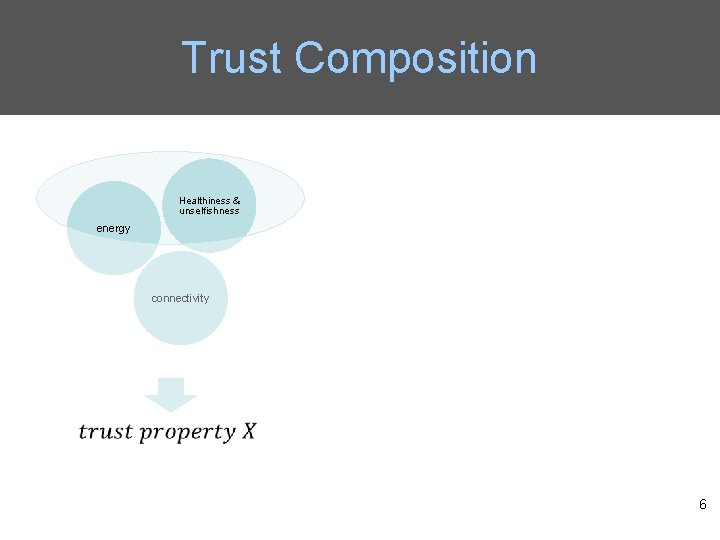
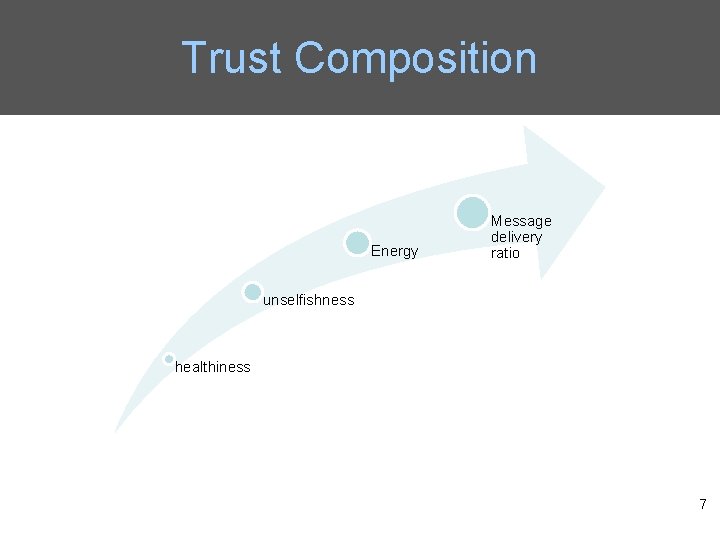
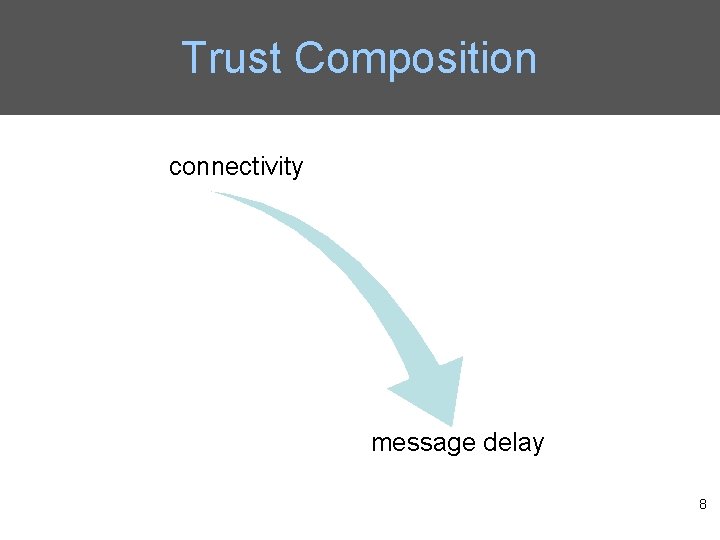
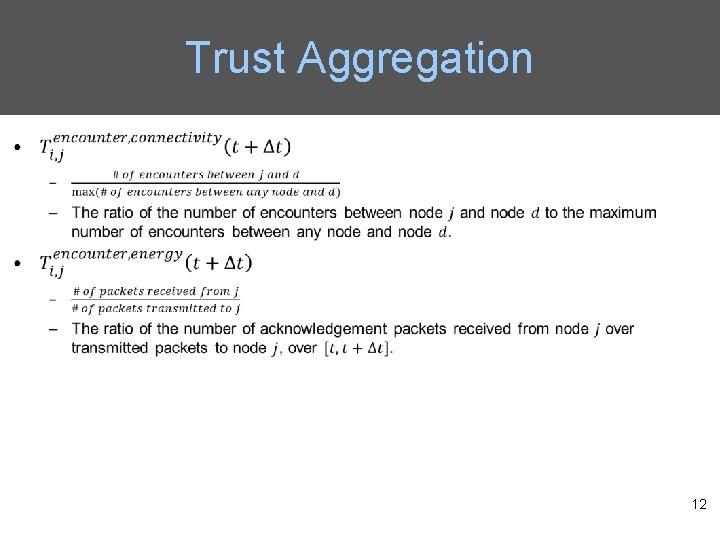
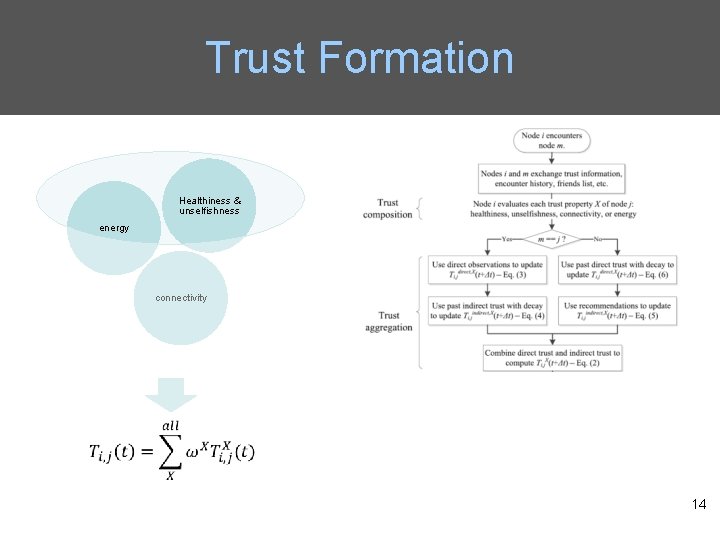
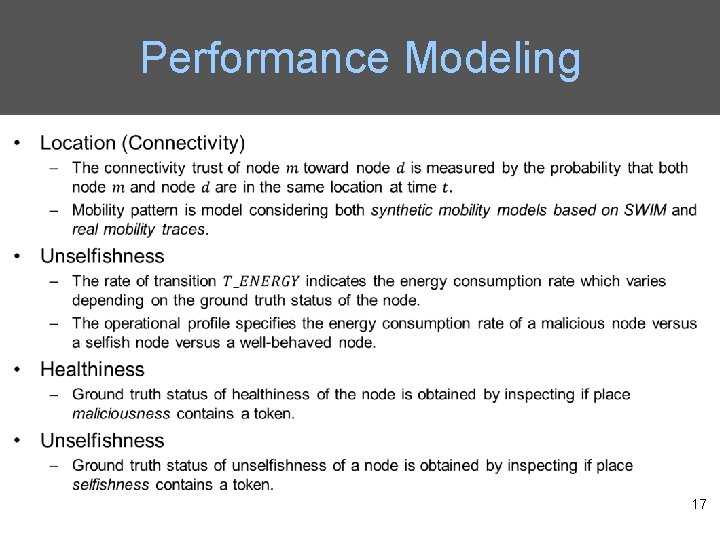
Trust Composition • Qo. S trust is the capability of a node to deliver messages to the destination node. – The connectivity Qo. S trust is about the ability of a node to encounter other nodes due to its movement patterns. – The energy Qo. S trust is about the battery energy of a node to perform the basic routing function. • Social trust is about the honesty in social relationships and friendship in social ties. – The healthiness social trust is the belief of whether a node is malicious. – The unselfishness social trust is the belief of whether a node is socially selfish. 5

Trust Composition Healthiness & unselfishness energy connectivity 6

Trust Composition Energy Message delivery ratio unselfishness healthiness 7

Trust Composition connectivity message delay 8

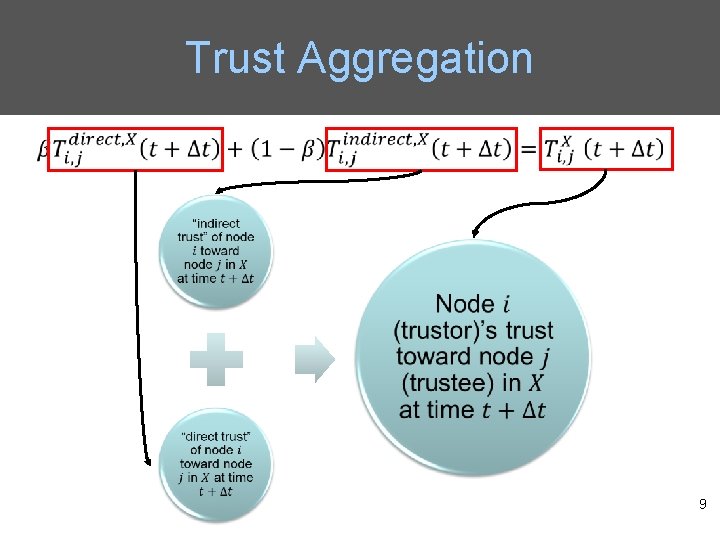
Trust Aggregation • 9

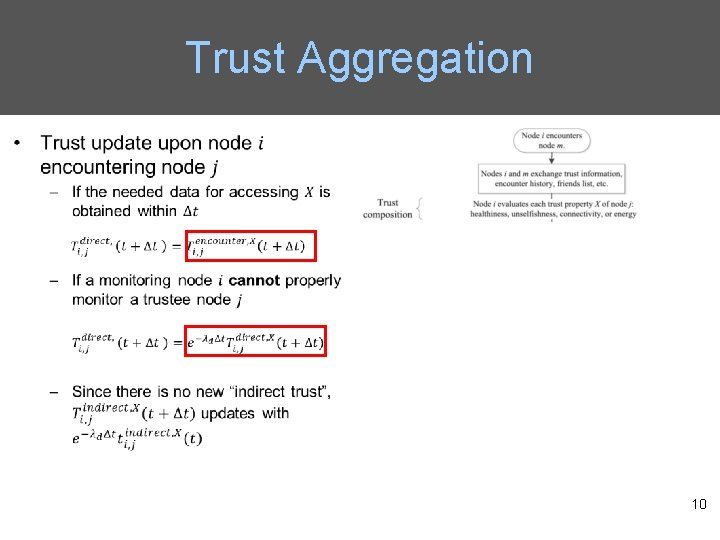
Trust Aggregation 10

Trust Aggregation 11

Trust Aggregation 12

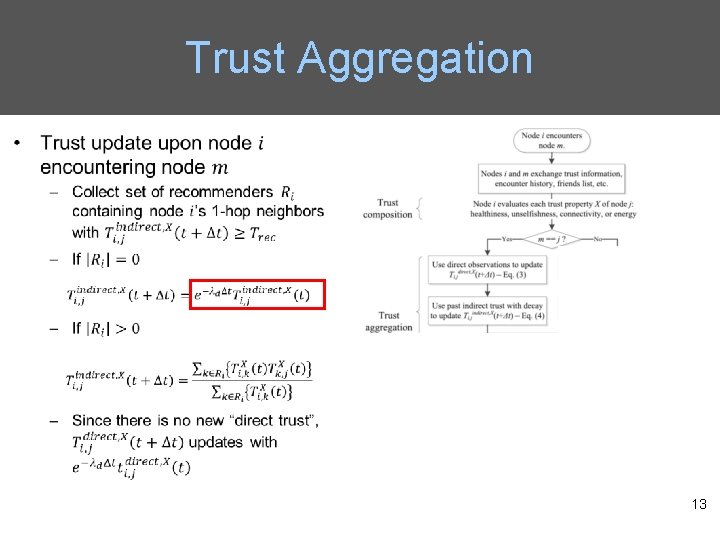
Trust Aggregation 13

Trust Formation Healthiness & unselfishness energy connectivity 14

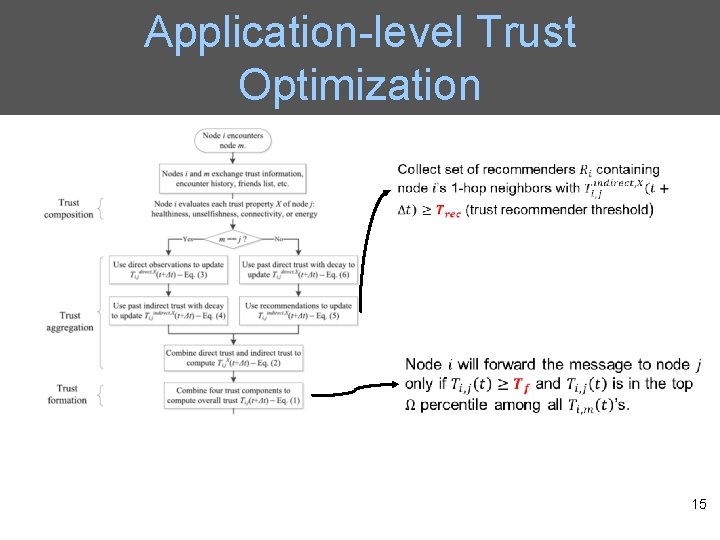
Application-level Trust Optimization 15

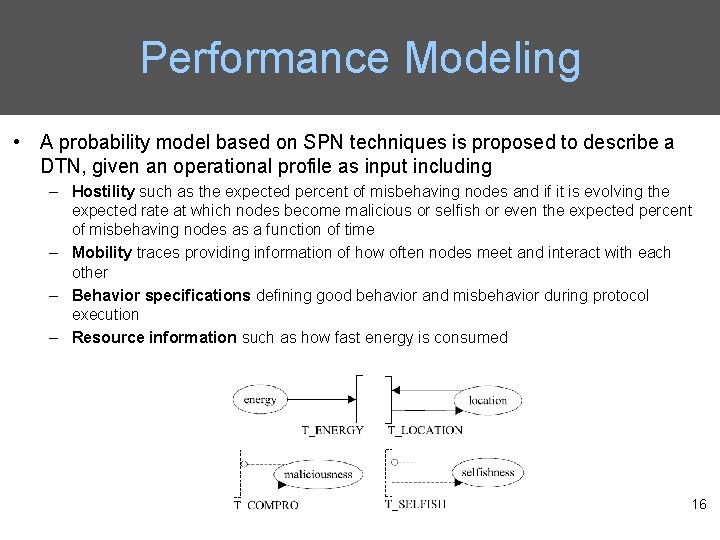
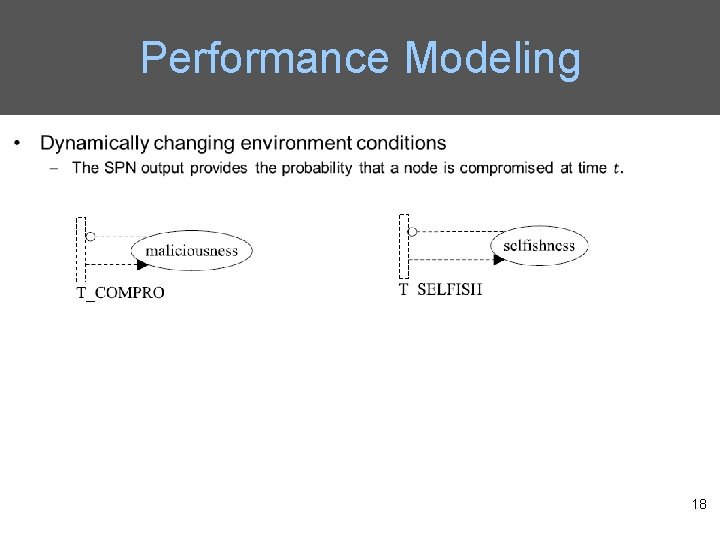
Performance Modeling • A probability model based on SPN techniques is proposed to describe a DTN, given an operational profile as input including – Hostility such as the expected percent of misbehaving nodes and if it is evolving the expected rate at which nodes become malicious or selfish or even the expected percent of misbehaving nodes as a function of time – Mobility traces providing information of how often nodes meet and interact with each other – Behavior specifications defining good behavior and misbehavior during protocol execution – Resource information such as how fast energy is consumed 16

Performance Modeling 17

Performance Modeling 18

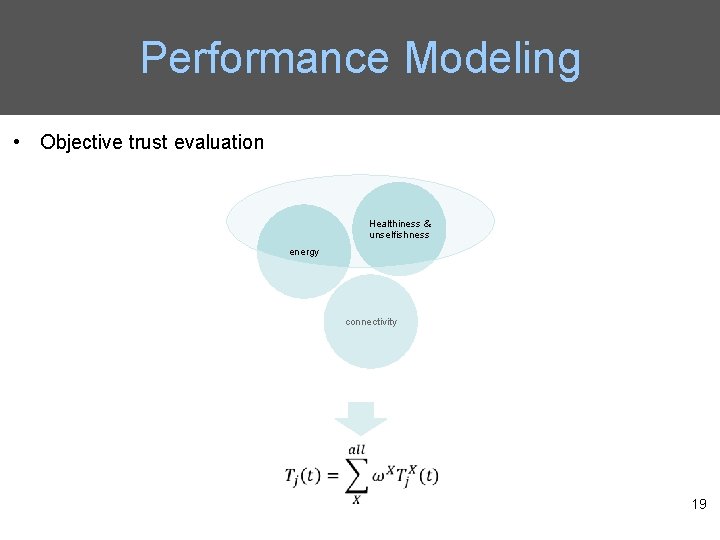
Performance Modeling • Objective trust evaluation Healthiness & unselfishness energy connectivity 19

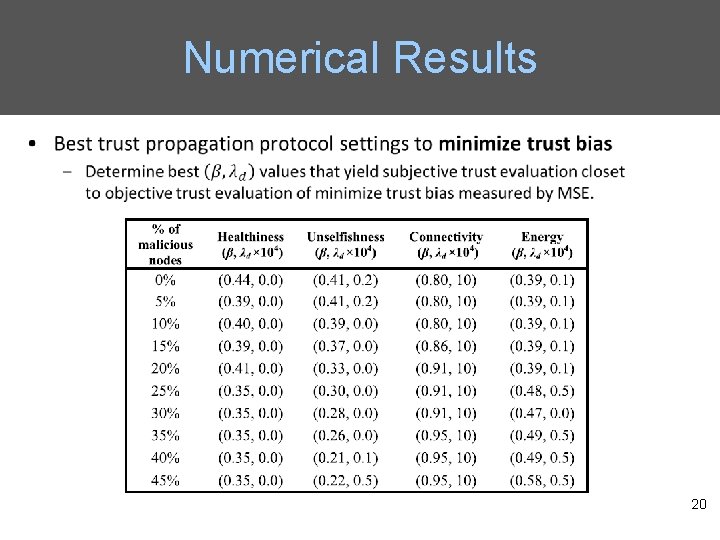
Numerical Results 20

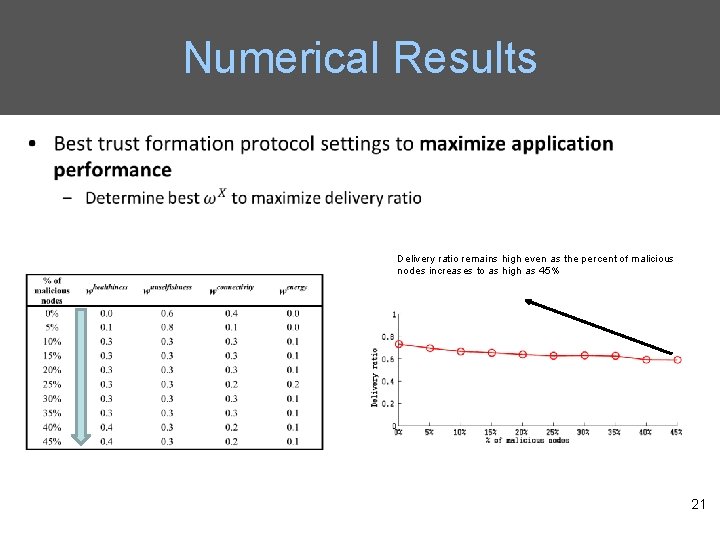
Numerical Results Delivery ratio remains high even as the percent of malicious nodes increases to as high as 45% 21

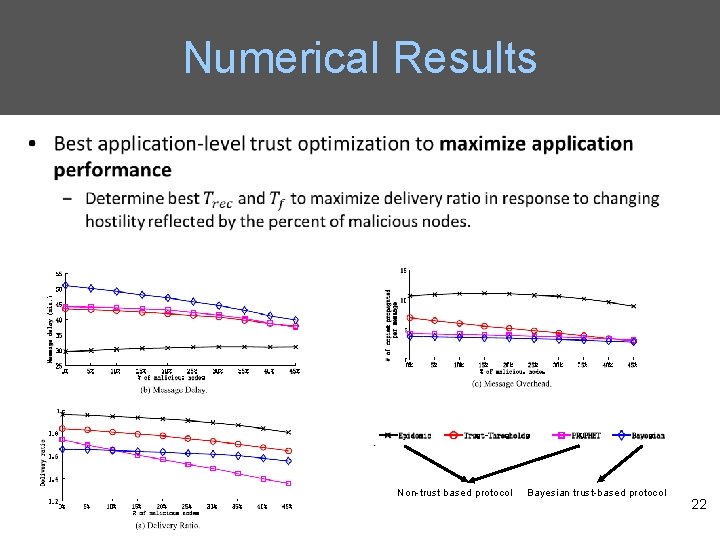
Numerical Results Non-trust based protocol Bayesian trust-based protocol 22