DLP Incident Remediation Process Overview June 3 2009


- Slides: 7

DLP Incident Remediation Process Overview June 3, 2009 Confidential and Proprietary

Today’s Agenda q Introduction q DLP Infrastructure Overview q Incident Remediation Process Key Parties q Workflow Examples § No Information Protection Review § Information Protection Reviewed § Information Protection Assisted

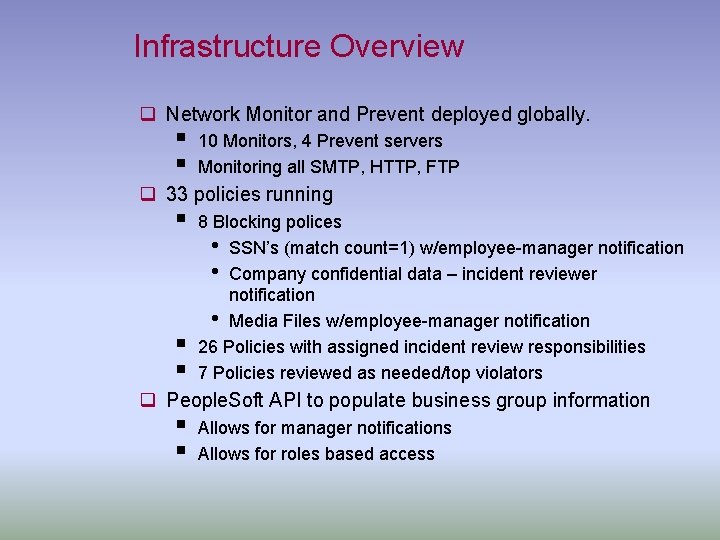
Infrastructure Overview q Network Monitor and Prevent deployed globally. § § 10 Monitors, 4 Prevent servers Monitoring all SMTP, HTTP, FTP q 33 policies running § § § 8 Blocking polices • SSN’s (match count=1) w/employee-manager notification • Company confidential data – incident reviewer notification • Media Files w/employee-manager notification 26 Policies with assigned incident review responsibilities 7 Policies reviewed as needed/top violators q People. Soft API to populate business group information § § Allows for manager notifications Allows for roles based access

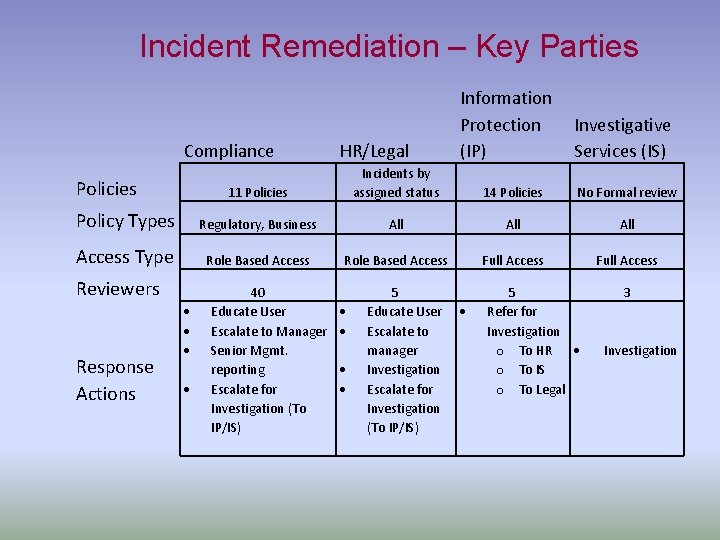
Incident Remediation – Key Parties Compliance Policies HR/Legal Information Protection Investigative (IP) Services (IS) Incidents by assigned status 11 Policies 14 Policies No Formal review Policy Types Regulatory, Business All All Access Type Role Based Access Full Access Reviewers Response Actions 40 Educate User Escalate to Manager Senior Mgmt. reporting Escalate for Investigation (To IP/IS) 5 Educate User Escalate to manager Investigation Escalate for Investigation (To IP/IS) 5 Refer for Investigation o To HR o To IS o To Legal 3 Investigation

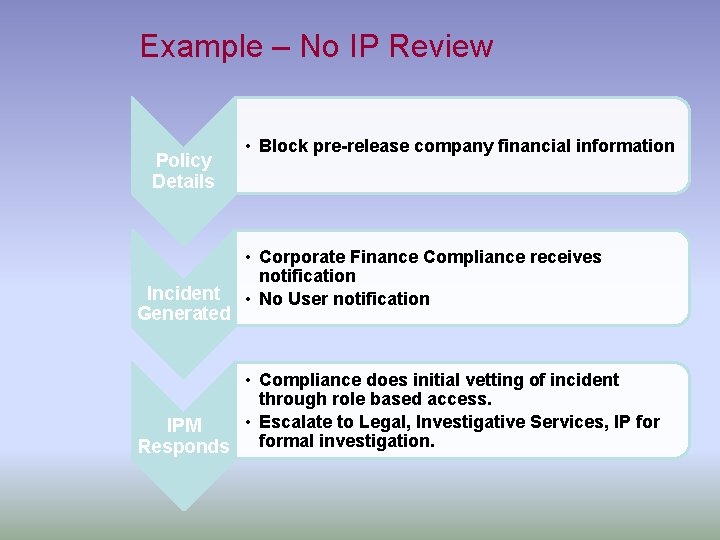
Example – No IP Review Policy Details Incident Generated • Block pre-release company financial information • Corporate Finance Compliance receives notification • No User notification • Compliance does initial vetting of incident through role based access. • Escalate to Legal, Investigative Services, IP for IPM formal investigation. Responds

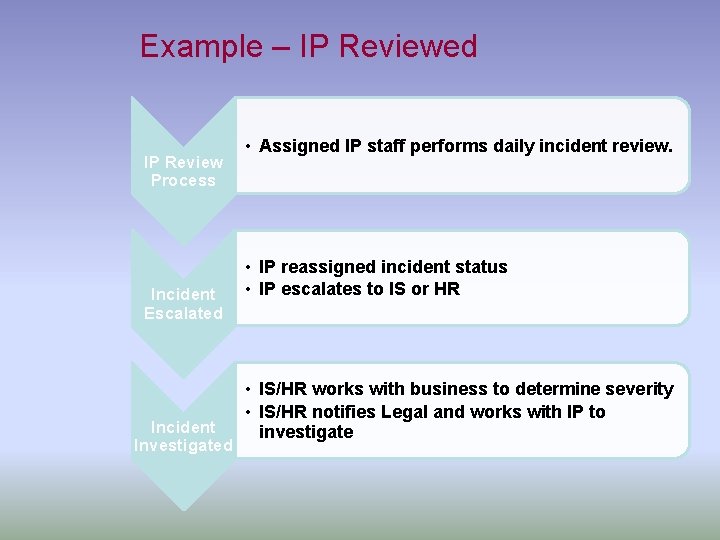
Example – IP Reviewed IP Review Process Incident Escalated Incident Investigated • Assigned IP staff performs daily incident review. • IP reassigned incident status • IP escalates to IS or HR • IS/HR works with business to determine severity • IS/HR notifies Legal and works with IP to investigate

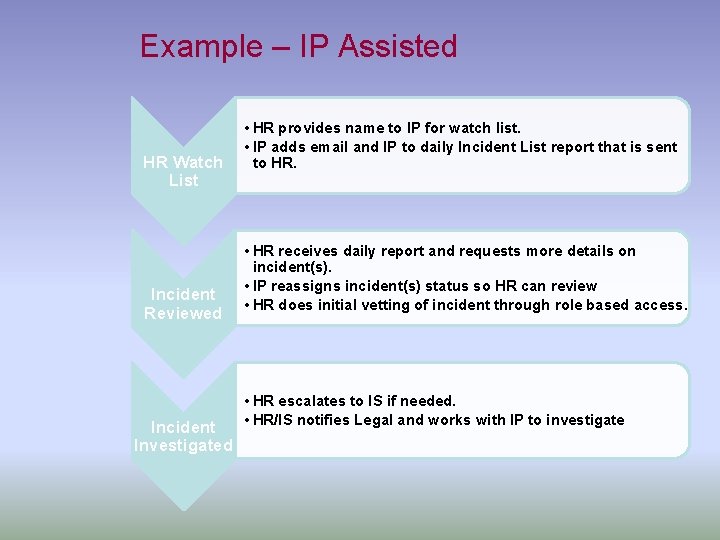
Example – IP Assisted HR Watch List Incident Reviewed Incident Investigated • HR provides name to IP for watch list. • IP adds email and IP to daily Incident List report that is sent to HR. • HR receives daily report and requests more details on incident(s). • IP reassigns incident(s) status so HR can review • HR does initial vetting of incident through role based access. • HR escalates to IS if needed. • HR/IS notifies Legal and works with IP to investigate