Disaster Recover Planning Federal Information Systems Management Act






















- Slides: 26

Disaster Recover Planning & Federal Information Systems Management Act Requirements December 2007 Central Maryland ISACA Chapter

Samuel Bower. Craft, MIS, CISA Consulting Manager

Preliminary Items • Ask and you shall receive. – Questions? – Thoughts? – Focus! • We will all get a break. • Get coffee when you need it…I will.

FISMA • Federal Information Security Management Act of 2002 • Places requirements on government agencies to improve the security of federal information and information systems. • Who has ever done SOX work?

Purpose of FISMA • Provide a consistent framework for protecting information at the federal level. • Provide effective management of risks to information security. • Provide for the development of adequate controls to protect information and systems. • Provides a mechanism for effective oversight of federal security programs.

FISMA Summary • Federal agencies are required to establish an integrated, risk-based information security program that adheres to high-level requirements governing how information security is conducted within their agency. • Agencies are required to: – assess the current level of risk associated with their information and information systems – define controls to protect those systems – implement policies and procedures to cost-effectively reduce risk – periodically test and evaluate those controls – train personnel on information security policies and procedures – and manage incidents (incident response plan/process).

FISMA Dictates… • • Responsibilities of chief security officers. Actions required to assess risk. Actions required to mitigate risk. Security awareness training. Testing of security practices and controls. Procedures for responding to security issues. Procedures for business continuity.

NIST • National Institute of Standards and Technology • Mission: to promote U. S. innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life.

FISMA and NIST • Provides guidance on FISMA that is detailed and in-depth, and how! • Vision includes: • Standards for categorizing information and information systems by mission impact. • Standards for minimum security requirements for information and information systems. • Guidance for selecting appropriate security controls for information systems. • Guidance for assessing security controls in information systems and determining security control effectiveness. • Guidance for certifying and accrediting information systems.

NIST & FISMA • Goals Include: • • The implementation of cost-effective, risk-based information security programs. The establishment of a level of security due diligence for federal agencies and contractors supporting the federal government. More consistent and cost-effective application of security controls across the federal information technology infrastructure. More consistent, comparable, and repeatable security control assessments. A better understanding of enterprise-wide mission risks resulting from the operation of information systems. More complete, reliable, and trustworthy information for authorizing officials-facilitating more informed security accreditation decisions. More secure information systems within the federal government including the critical infrastructure of the United States.

FISMA Implementation Timeline • Phase 1: Standards and Guidelines Dev. – Focuses on the development of the security standards and guidance required to effectively implement the provisions of the legislation. – The implementation of the NIST standards and guidance will help agencies create robust information security programs and effectively manage risk – 2003 - 2007

FISMA Implementation Timeline • Phase 2: Credentialing Program – Focus on the development of a program for credentialing public and private sector organizations to provide security assessment services for federal agencies. – Security services involve the comprehensive assessment of the management, operational, and technical security controls in federal information systems to determine the extent to which the controls are implemented correctly. – 2007 - 2009

Compliance Deadlines • Legacy Systems: within one (1) year of publication of NIST security standards. • Systems under development: upon deployment.

Effective Security Program • • Periodic Assessment of Risk Policies and procedures based on risk. Plans for providing adequate security. Security awareness training. Periodic testing of controls, at least annually. A formal remediation process. Security incident response process. Business continuity procedures.

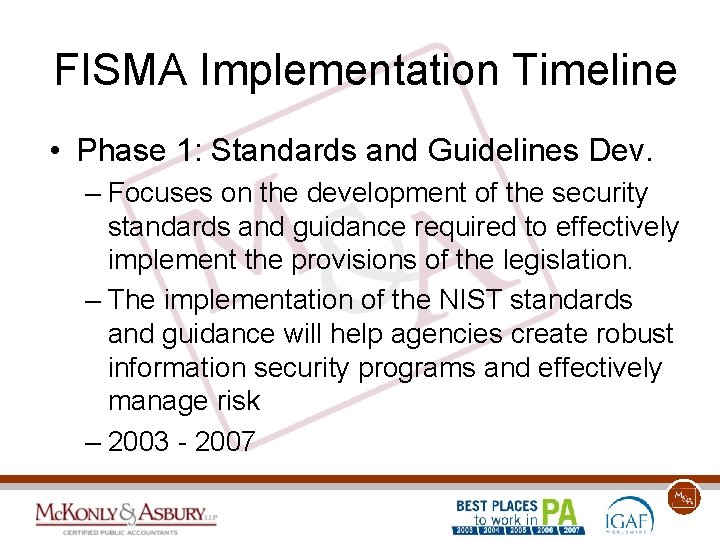
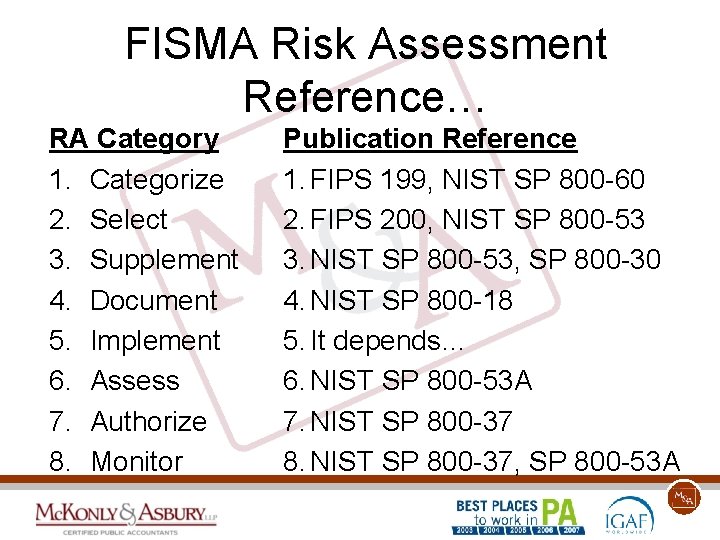
FISMA: Risk Assessment 1. 2. 3. 4. 5. 6. 7. 8. Categorize the information system. Select an initial set of security controls. Supplement controls based on risk. Document the controls in the security plan. Implement the security controls. Assess the controls (test). Authorize systems based on risk. Monitor and continually assess controls.

FISMA Risk Assessment Reference… RA Category 1. Categorize 2. Select 3. Supplement 4. Document 5. Implement 6. Assess 7. Authorize 8. Monitor Publication Reference 1. FIPS 199, NIST SP 800 -60 2. FIPS 200, NIST SP 800 -53 3. NIST SP 800 -53, SP 800 -30 4. NIST SP 800 -18 5. It depends… 6. NIST SP 800 -53 A 7. NIST SP 800 -37 8. NIST SP 800 -37, SP 800 -53 A


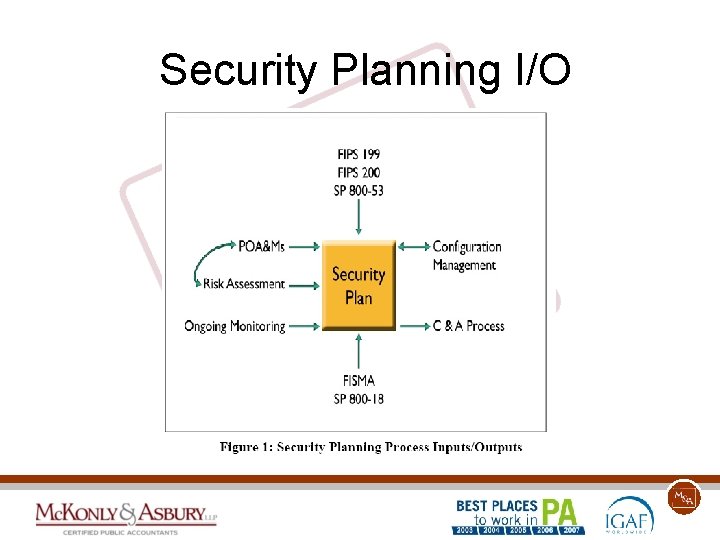
Security Planning I/O

Publication Summary FIPS 199 • Standards for Security Categorization of Federal Information and Information Systems – Categorization of information and/or information systems. – Based on potential impact based on certain events being experienced by the organization.

Publication Summary SP 800 -60 • Guide for Mapping Types of Information and Information Systems to Security Categories – Assists in mapping information and information systems to impact levels for: • Confidentiality, Integrity, & Availability. – Volume 1: Relevant to multiple agencies. – Volume 2: Agency and mission specific.

Publication Summary SP 800 -53 • Guide for Assessing the Security Controls in Federal Information Systems – Guide to establish common methods and to assess the effectiveness of controls (test). – Designed to foster standardization, and consistent and comparable assessments of information systems.

Publication Summary SP 800 -53 • Recommended Security Controls for Federal Information Systems – Provides guidelines for selecting controls for information systems. – For ISACA and CISA and Co. BIT lovers…

SP 800 -53 Security Control Topic Areas • Risk assessment • Certification, Accreditation and Security Assessments • System Services and Acquisition • Security Planning • Configuration Mgmt. • System and Communications Protection • Incident Response • Identification and Authorization • Personnel Security • Awareness and Training • Physical and Environmental Protection • Media Protection • Contingency Planning • Maintenance • System and Information Integrity • Access Control • Accountability and Audit

Publication Summary SP 800 -37 • Guide for the Security Certification and Accreditation of Federal Information Systems – Provides guidelines for the certification of information systems to enable consistent, comparable and repeatable evaluations of security controls. – Help achieve more secure systems.

Publication Summary SP 800 -18 • Guide for Developing Security Plans for Federal Information Systems – Provides background a structure for developing a security plan. – Has Information System Security Plan Template!

FISMA Summary • FISMA is about information security and a formalized process to attest to the security • The process flow is standard audit framework. • NIST provides clear guidelines on how to document and proceed. • Check out: http: //csrc. nist. gov/groups/SMA/fisma/index. html
 Sql server management studio recover unsaved queries
Sql server management studio recover unsaved queries Philippine disaster risk reduction and management act
Philippine disaster risk reduction and management act Disaster management in libraries and information centres
Disaster management in libraries and information centres Can you recover from a flat spin
Can you recover from a flat spin Withdrawal of status respect meaning
Withdrawal of status respect meaning What exactly does gatsby want to recover
What exactly does gatsby want to recover Number restoration
Number restoration Fume hood accessories
Fume hood accessories Recover pki certificates
Recover pki certificates When the royalties are less than the minimum rent?
When the royalties are less than the minimum rent? Recover your life
Recover your life Prepare mitigate respond recover
Prepare mitigate respond recover Recover pori
Recover pori Recover a tree from preorder traversal
Recover a tree from preorder traversal Explain the dawes plan
Explain the dawes plan Information systems planning
Information systems planning Cissp business continuity and disaster recovery planning
Cissp business continuity and disaster recovery planning Ad disaster recovery planning scenario
Ad disaster recovery planning scenario Disaster recovery planning in system analysis and design
Disaster recovery planning in system analysis and design Perbedaan irp, drp dan bcp
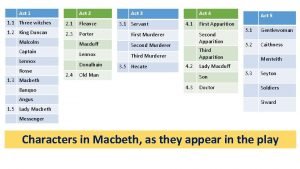
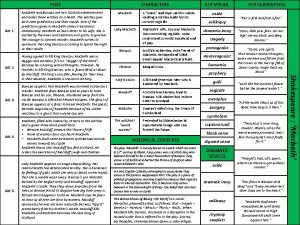
Perbedaan irp, drp dan bcp Macbeth act 2 summary
Macbeth act 2 summary Livingston federal employee retirement planning
Livingston federal employee retirement planning Lower court
Lower court Federal and state court systems
Federal and state court systems Disaster scenario media and information literacy
Disaster scenario media and information literacy Federal insecticide, fungicide, and rodenticide act (fifra)
Federal insecticide, fungicide, and rodenticide act (fifra) Federal tort claims act coverage
Federal tort claims act coverage