CS 259 Password Authentication J Mitchell User Password








- Slides: 20

CS 259 Password Authentication J. Mitchell

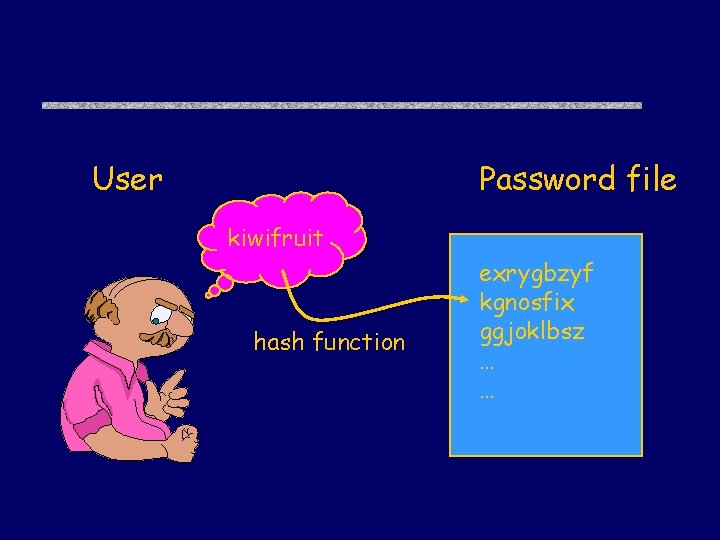
User Password file kiwifruit hash function exrygbzyf kgnosfix ggjoklbsz … …

Basic password authentication u. Setup • User chooses password • Hash of password stored in password file u. Authentication • User logs into system, supplies password • System computes hash, compares to file u. Attacks • Online dictionary attack – Guess passwords and try to log in • Offline dictionary attack – Steal password file, try to find p with hash(p) in file

Dictionary Attack – some numbers u Typical password dictionary • 1, 000 entries of common passwords – people's names, common pet names, and ordinary words. • Suppose you generate and analyze 10 guesses per second – This may be reasonable for a web site; offline is much faster • Dictionary attack in at most 100, 000 seconds = 28 hours, or 14 hours on average u If passwords were random • Assume six-character password – Upper- and lowercase letters, digits, 32 punctuation characters – 689, 869, 781, 056 password combinations. – Exhaustive search requires 1, 093 years on average

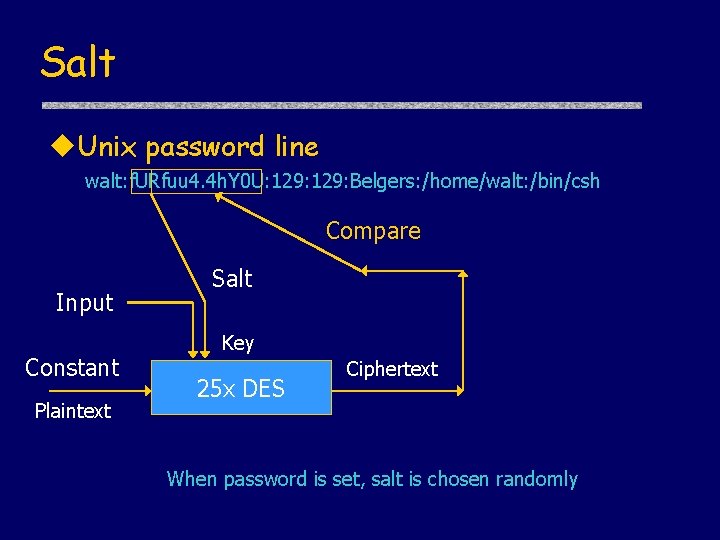
Salt u. Unix password line walt: f. URfuu 4. 4 h. Y 0 U: 129: Belgers: /home/walt: /bin/csh Compare Input Constant Plaintext Salt Key 25 x DES Ciphertext When password is set, salt is chosen randomly

Advantages of salt u. Without salt • Same hash functions on all machines – Compute hash of all common strings once – Compare hash file with all known password files u. With salt • One password hashed 212 different ways – Precompute hash file? • Need much larger file to cover all common strings – Dictionary attack on known password file • For each salt found in file, try all common strings

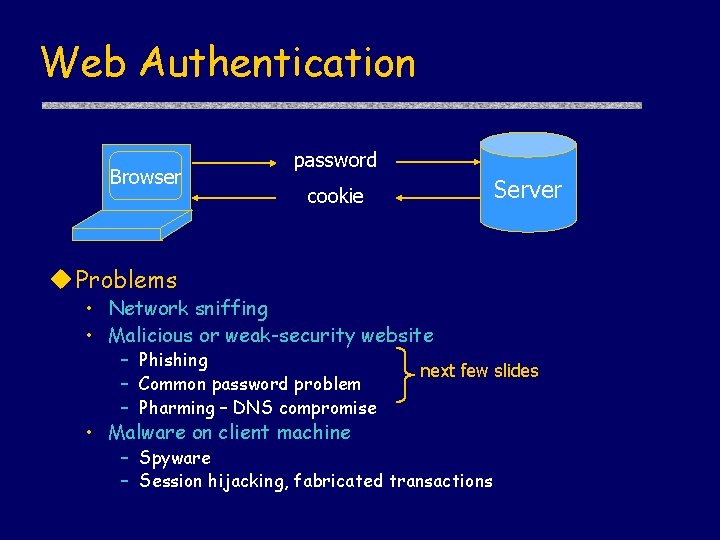
Web Authentication Browser password Server cookie u Problems • Network sniffing • Malicious or weak-security website – Phishing – Common password problem – Pharming – DNS compromise • Malware on client machine next few slides – Spyware – Session hijacking, fabricated transactions

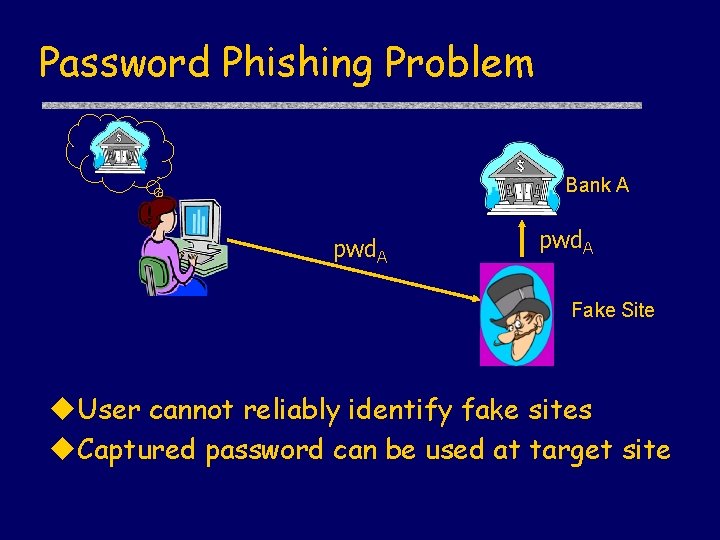
Password Phishing Problem Bank A pwd. A Fake Site u. User cannot reliably identify fake sites u. Captured password can be used at target site

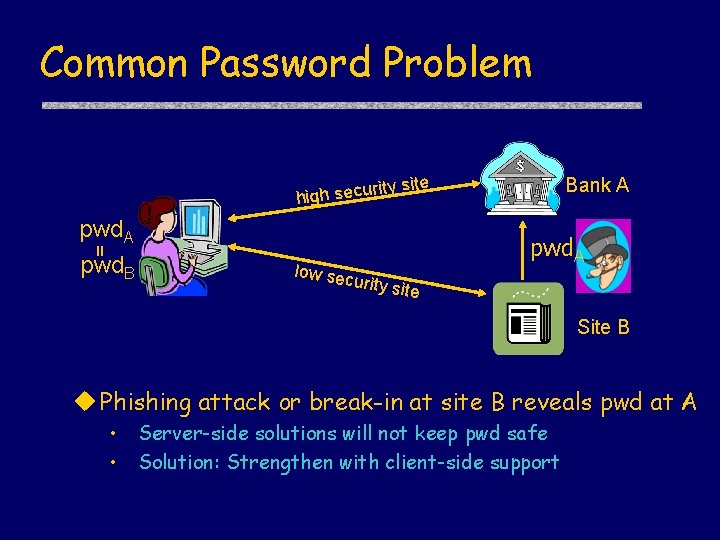
Common Password Problem rit high secu y site pwd. A = pwd. B Bank A low sec urity si te Site B u Phishing attack or break-in at site B reveals pwd at A • • Server-side solutions will not keep pwd safe Solution: Strengthen with client-side support

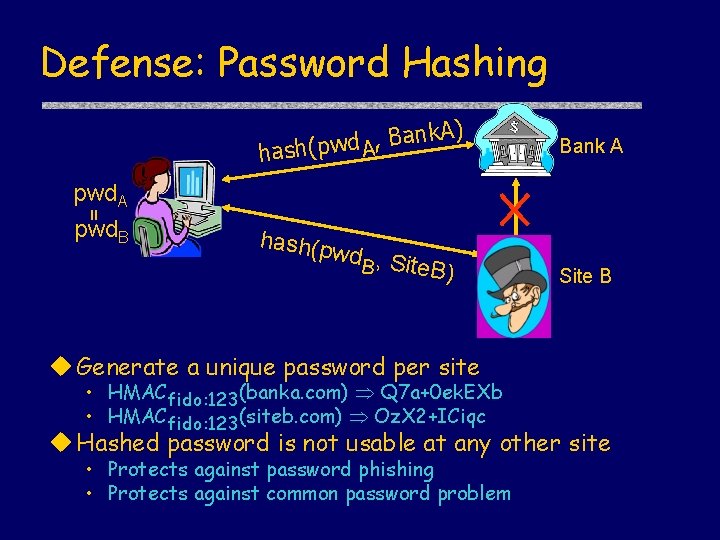
Defense: Password Hashing k. A ) n a B , d hash(pw A = pwd. A pwd. B Bank A hash(p wd , S B ite. B) Site B u Generate a unique password per site • HMACfido: 123(banka. com) Q 7 a+0 ek. EXb • HMACfido: 123(siteb. com) Oz. X 2+ICiqc u Hashed password is not usable at any other site • Protects against password phishing • Protects against common password problem

Defense: Spy. Block

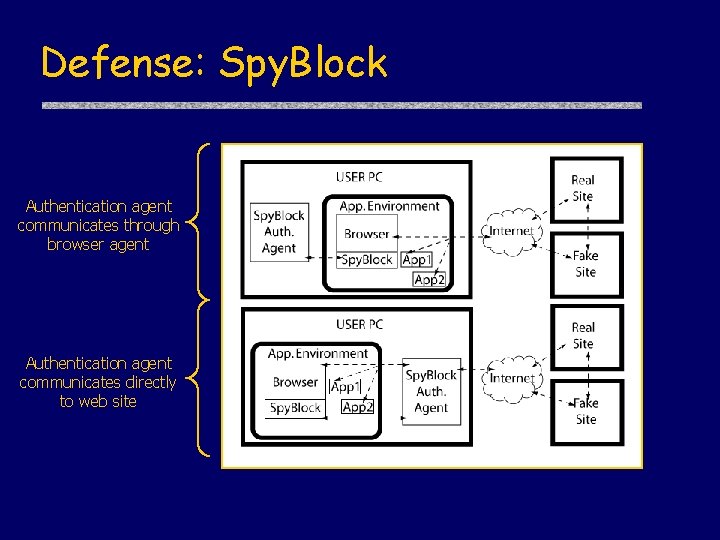
Defense: Spy. Block Authentication agent communicates through browser agent Authentication agent communicates directly to web site

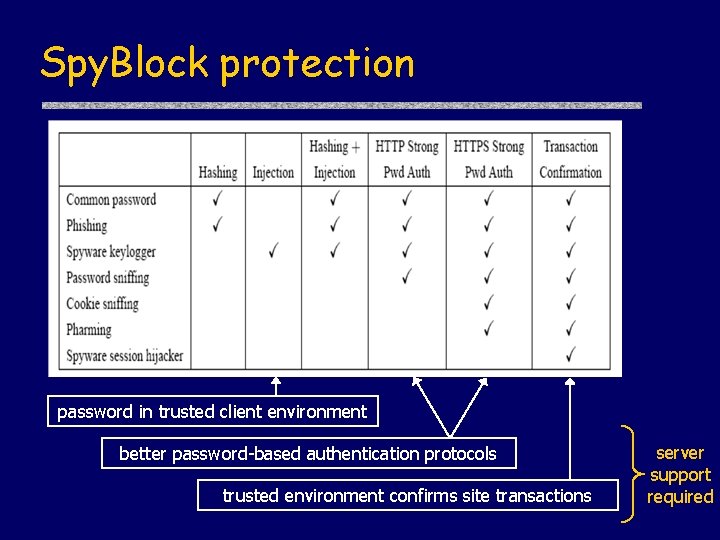
Spy. Block protection password in trusted client environment better password-based authentication protocols trusted environment confirms site transactions server support required

Goals for password protocol u. Authentication relies on password • User can remember password, use anywhere • No additional client-side certificates, etc. u. Protect against attacks • Network does not carry cleartext passwords • Malicious user cannot do offline dictionary attack • Malicious server (as in phishing) does not learn password from communication with honest user

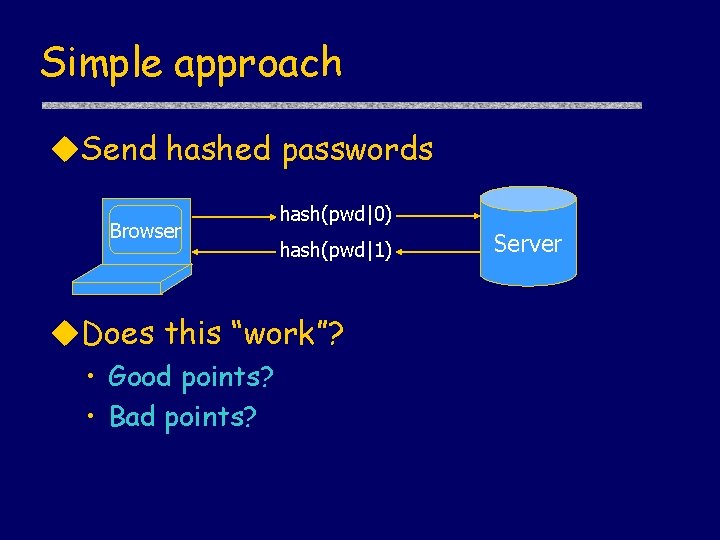
Simple approach u. Send hashed passwords Browser hash(pwd|0) hash(pwd|1) u. Does this “work”? • Good points? • Bad points? Server

“Interlock” password protocols (Set-up Phase) Password p known to both parties (Key Exchange Phase) A B gx B A gy k = gxy or some function of gxy (Authentication Phase) A B mack(p, r) B A mack(p, s), enck(s) A B enck(r) for random r for random s [Rivest, Shamir, Bellovin, Merrit, … Pederson, Ellison]

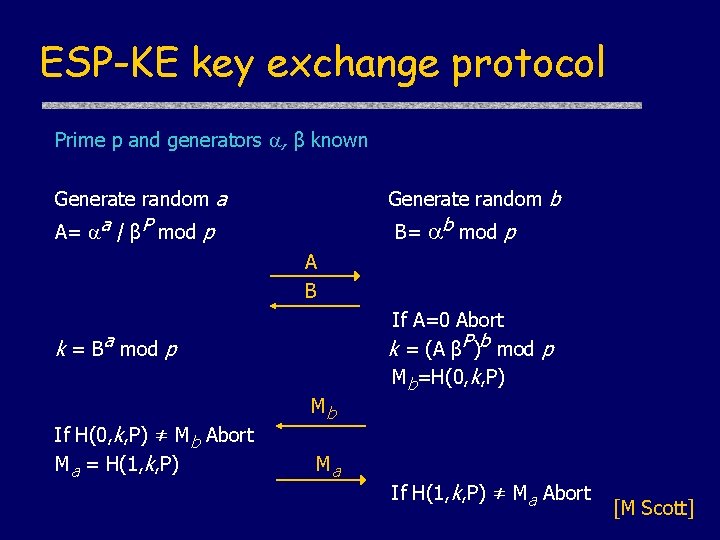
ESP-KE key exchange protocol Prime p and generators , β known Generate random a A= a / βP mod p Generate random b B= b mod p A B k = Ba mod p If H(0, k, P) ≠ Mb Abort Ma = H(1, k, P) Mb Ma If A=0 Abort k = (A βP)b mod p Mb=H(0, k, P) If H(1, k, P) ≠ Ma Abort [M Scott]

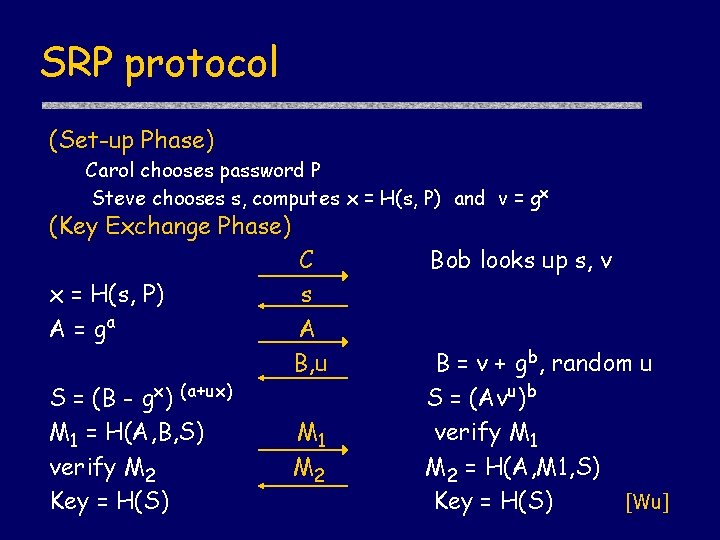
SRP protocol (Set-up Phase) Carol chooses password P Steve chooses s, computes x = H(s, P) and v = gx (Key Exchange Phase) x = H(s, P) A = ga S = (B - gx) (a+ux) M 1 = H(A, B, S) verify M 2 Key = H(S) C s A B, u M 1 M 2 Bob looks up s, v B = v + gb, random u S = (Avu)b verify M 1 M 2 = H(A, M 1, S) [Wu] Key = H(S)

CMU “Phoolproof” proposal u Eliminates reliance on perfect user behavior u Protects against keyloggers, spyware. u Uses a trusted mobile device to perform mutual authentication with the server password?
