Cryptography Lecture 11 A fixedlength MAC Construction Let


![Analysis • Since F is a pseudorandom function, | Pr[DF outputs 1] - Pr[Df Analysis • Since F is a pseudorandom function, | Pr[DF outputs 1] - Pr[Df](https://slidetodoc.com/presentation_image_h/0527644997302623586444c05cccf4cb/image-6.jpg)










- Slides: 22

Cryptography Lecture 11

A fixed-length MAC

Construction • Let F be a length-preserving pseudorandom function (aka block cipher) • Construct the following MAC : – Gen: choose a uniform key k for F – Mack(m): output Fk(m) – Vrfyk(m, t): output 1 iff Fk(m)=t • Theorem: is a secure MAC

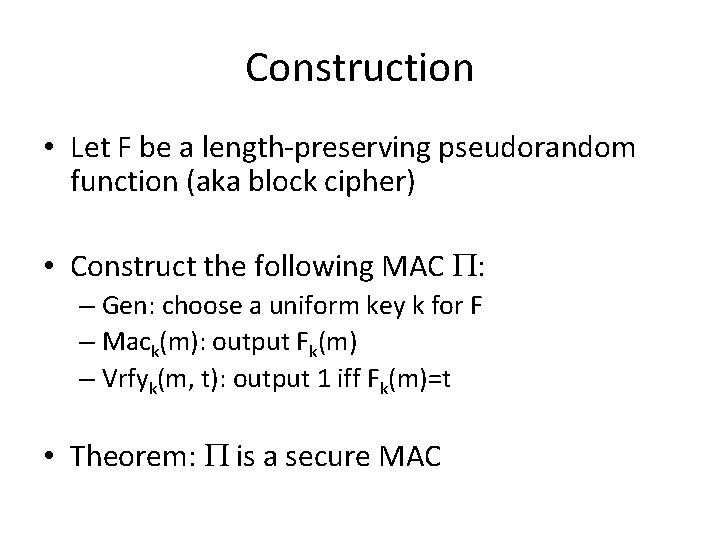
Proof by reduction … m 1 t 1 … PRF/random m 1 t 1 mi ti m t* m, t if (m is new and t=t*) output 1 D

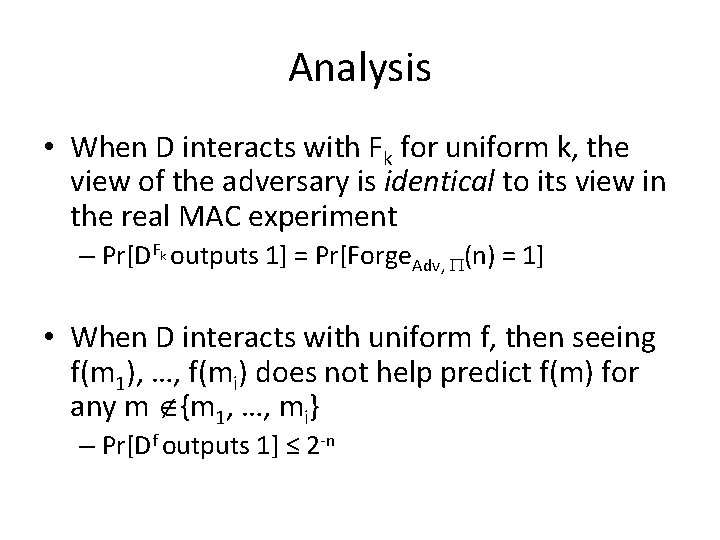
Analysis • When D interacts with Fk for uniform k, the view of the adversary is identical to its view in the real MAC experiment – Pr[DFk outputs 1] = Pr[Forge. Adv, (n) = 1] • When D interacts with uniform f, then seeing f(m 1), …, f(mi) does not help predict f(m) for any m {m 1, …, mi} – Pr[Df outputs 1] ≤ 2 -n
![Analysis Since F is a pseudorandom function PrDF outputs 1 PrDf Analysis • Since F is a pseudorandom function, | Pr[DF outputs 1] - Pr[Df](https://slidetodoc.com/presentation_image_h/0527644997302623586444c05cccf4cb/image-6.jpg)
Analysis • Since F is a pseudorandom function, | Pr[DF outputs 1] - Pr[Df outputs 1] | < negl(n) k Pr[Forge. Adv, (n) = 1] = Pr[DF outputs 1] ≤ 2 -n + negl(n) k

Drawbacks? • This only works for fixed-length messages • This only works for short messages – E. g. , AES has a 128 -bit block size (shorter than a tweet!) • So the previous construction is limited to authenticating short, fixed-length messages

Suggestions? • Can you construct a secure MAC for variablelength messages from a MAC for fixed-length messages? • One natural idea: – Mac’k(m 1, …, ml) = Mack(m 1), …, Mack(ml) – Vrfy’k(m 1, …, ml, t 1, …, tl) = 1 iff Vrfyk(mi, ti) = 1 for all i – Is this secure?

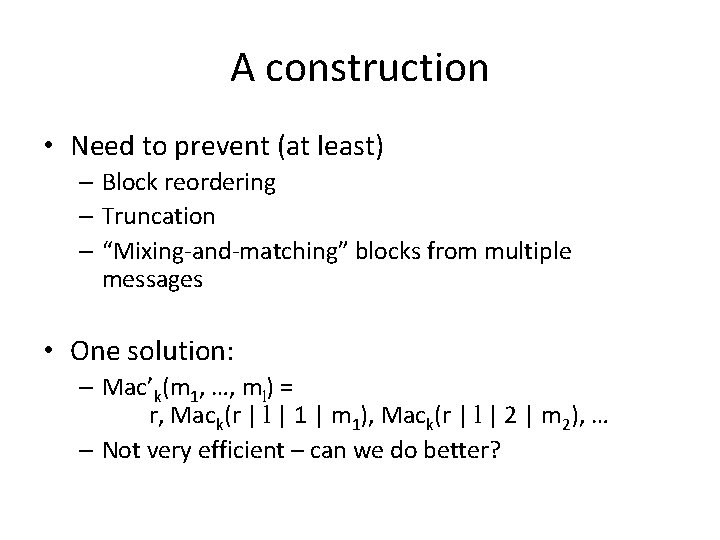
A construction • Need to prevent (at least) – Block reordering – Truncation – “Mixing-and-matching” blocks from multiple messages • One solution: – Mac’k(m 1, …, ml) = r, Mack(r | l | 1 | m 1), Mack(r | l | 2 | m 2), … – Not very efficient – can we do better?

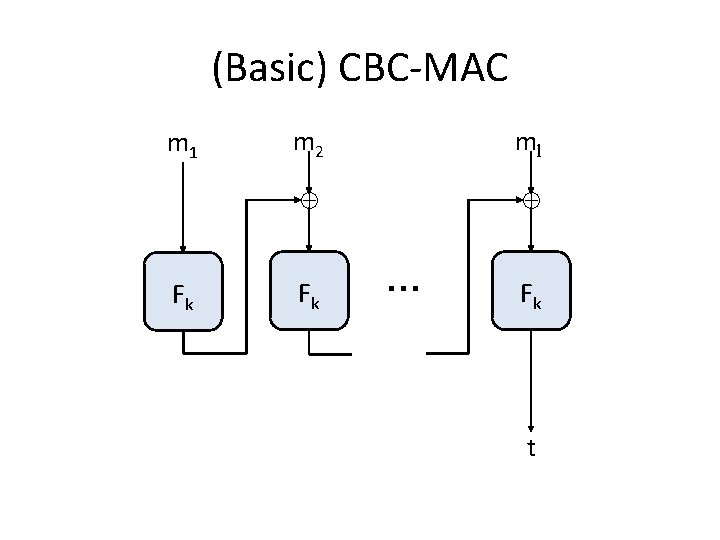
(Basic) CBC-MAC m 1 Fk m 2 ml Fk … Fk t

CBC-MAC vs. CBC-mode • CBC-MAC is deterministic (no IV) – MACs do not need to be randomized to be secure – Verification is done by re-computing the result • In CBC-MAC, only the final value is output • Both are essential for security – Exercise: show attacks

Security of (basic) CBC-MAC? • If F is a pseudorandom function with block length n, then for any fixed l basic CBC-MAC is a secure MAC for messages of length l·n • The sender and receiver must agree on the length parameter l in advance – Basic CBC-MAC is not secure if this is not done! – Attacks?

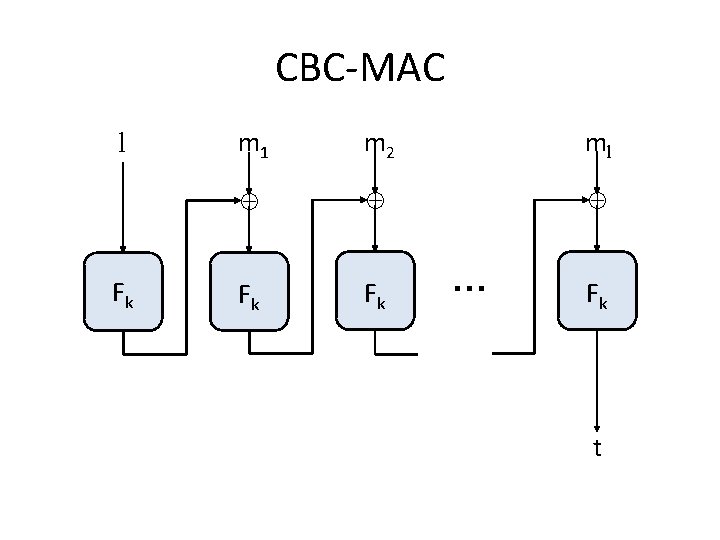
CBC-MAC extensions • Several ways to handle variable-length messages • One of the simplest: prepend the message length before applying (basic) CBC-MAC

CBC-MAC l Fk m 1 m 2 ml Fk Fk … Fk t

CBC-MAC extensions • Several ways to handle variable length messages • One of the simplest: prepend the message length before applying (basic) CBC-MAC – Can also be adapted to handle messages whose length is not a multiple of the block length

Authenticated encryption

Secrecy + integrity? • We have shown primitives for achieving secrecy and integrity in the private-key setting • What if we want to achieve both?

Authenticated encryption • An encryption scheme that achieves both secrecy and integrity • Secrecy notion: CCA-security • Integrity notion: unforgeability – Adversary cannot generate ciphertext that decrypts to a previously unencrypted message

Constructions? • Generic constructions – Encrypt and authenticate – Authenticate then encrypt – Encrypt then authenticate • Direct constructions

Generic constructions • Generically combine an encryption scheme and a MAC – Useful when these are already available in some library • Goal: the combination should be an authenticated encryption scheme when instantiated with any CPA-secure encryption scheme and any secure MAC

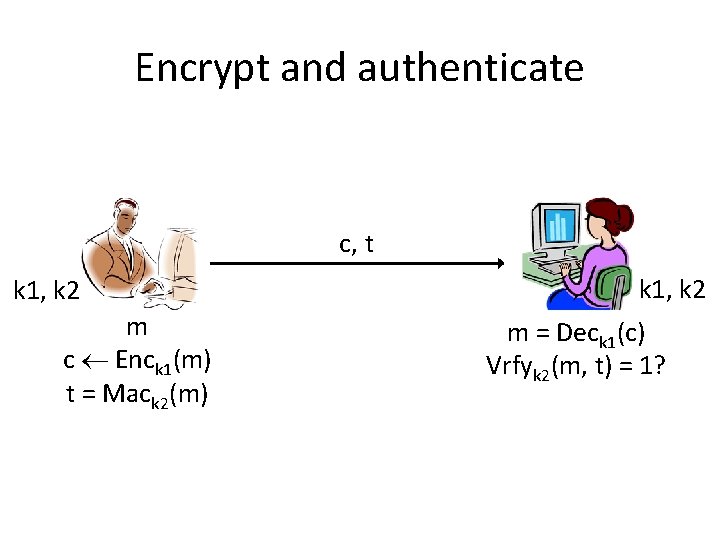
Encrypt and authenticate c, t k 1, k 2 m c Enck 1(m) t = Mack 2(m) k 1, k 2 m = Deck 1(c) Vrfyk 2(m, t) = 1?

Problems • The tag t might leak information about m! – Nothing in the definition of security for a MAC implies that it hides information about m – So the combination may not even be EAV-secure • If the MAC is deterministic (as is CBC-MAC), then the tag leaks whether the same message is encrypted twice – I. e. , the combination will not be CPA-secure