Course on Computer Communication and Networks Lecture 4

![UDP: User Datagram Protocol [RFC 768] “best effort” service, UDP segments may be: – UDP: User Datagram Protocol [RFC 768] “best effort” service, UDP segments may be: –](https://slidetodoc.com/presentation_image_h/d7fd5ed90c2335c99455df5a7c8614f2/image-14.jpg)
![UDP Checksum[RFC 1071]: check bit flips Sender: Receiver: r treat segment contents as r UDP Checksum[RFC 1071]: check bit flips Sender: Receiver: r treat segment contents as r](https://slidetodoc.com/presentation_image_h/d7fd5ed90c2335c99455df5a7c8614f2/image-16.jpg)





- Slides: 54

Course on Computer Communication and Networks Lecture 4 Chapter 3; Transport Layer, Part A EDA 344/DIT 420, CTH/GU Based on the book Computer Networking: A Top Down Approach, Jim Kurose, Keith Ross, Addison-Wesley. Marina Papatriantafilou – Transport layer part 1 1

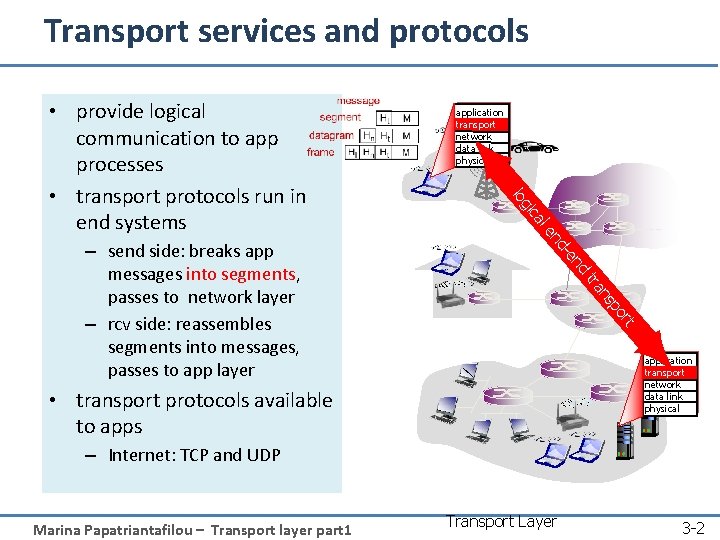
Transport services and protocols l ca d en d- en rt po ns tra – send side: breaks app messages into segments, passes to network layer – rcv side: reassembles segments into messages, passes to app layer application transport network data link physical gi lo • provide logical communication to app processes • transport protocols run in end systems application transport network data link physical • transport protocols available to apps – Internet: TCP and UDP Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -2

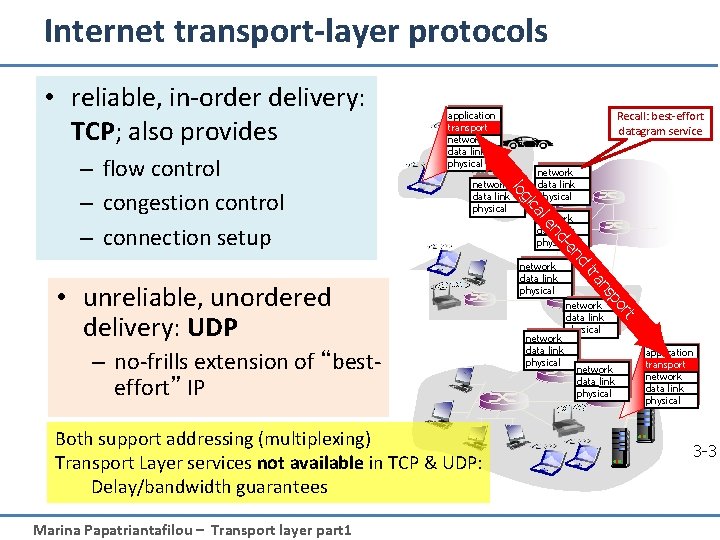
Internet transport-layer protocols • reliable, in-order delivery: TCP; also provides network data link physical rt network data link physical po ns tra Marina Papatriantafilou – Transport layer part 1 network data link physical nd Both support addressing (multiplexing) Transport Layer services not available in TCP & UDP: Delay/bandwidth guarantees -e nd – no-frills extension of “besteffort” IP network data link physical le • unreliable, unordered delivery: UDP network data link physical ca gi lo – flow control – congestion control – connection setup Recall: best-effort datagram service application transport network data link physical 3 -3

Transport Layer: Learning goals: • understand principles behind transport layer services: – Addressing, multiplexing/demultiplexing – reliable data transfer – flow control – congestion control (not mainly a Transport-layer issue --some study now; more in connection with Real. Time traffic) • instantiation and implementation in the Internet Marina Papatriantafilou – Transport layer part 1 3 a-4

Roadmap • • Transport layer services in Internet Addressing, multiplexing/demultiplexing Connectionless, unreliable transport: UDP principles of reliable data transfer • Next lecture: connection-oriented transport: TCP – reliable transfer – flow control – connection management – TCP congestion control Marina Papatriantafilou – Transport layer part 1 3 a-5

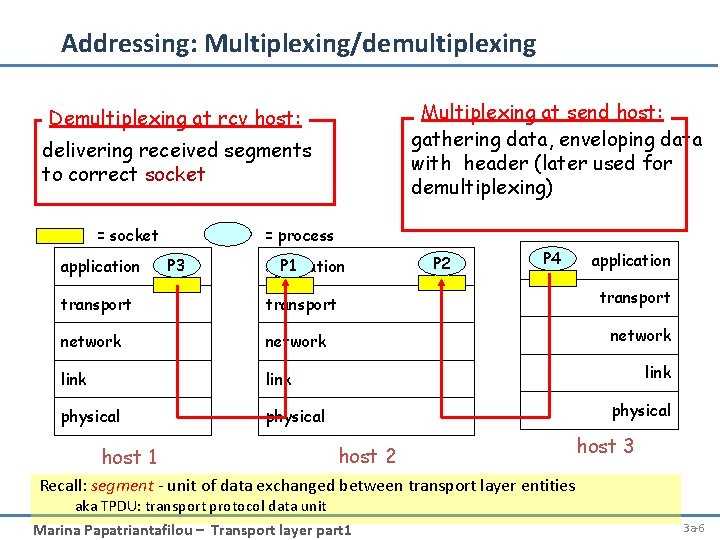
Addressing: Multiplexing/demultiplexing Multiplexing at send host: gathering data, enveloping data with header (later used for demultiplexing) Demultiplexing at rcv host: delivering received segments to correct socket = socket application = process P 3 P 1 application transport network link physical host 1 P 2 P 4 application transport network link physical host 2 host 3 Recall: segment - unit of data exchanged between transport layer entities aka TPDU: transport protocol data unit Marina Papatriantafilou – Transport layer part 1 3 a-6

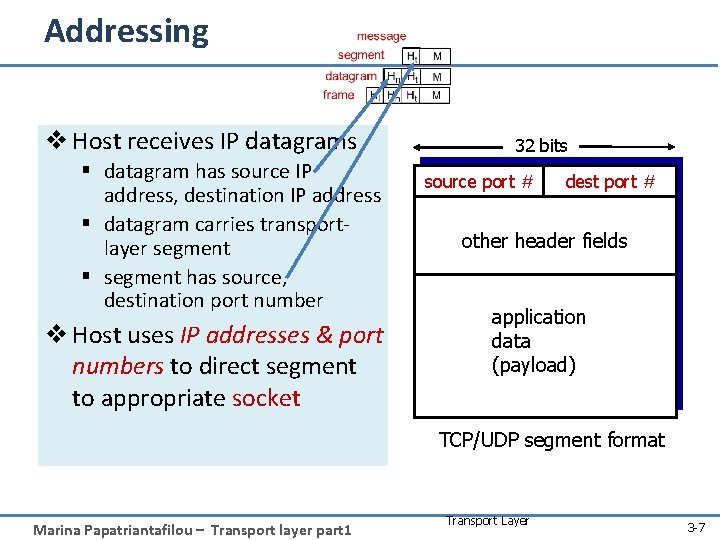
Addressing v Host receives IP datagrams § datagram has source IP address, destination IP address § datagram carries transportlayer segment § segment has source, destination port number v Host uses IP addresses & port numbers to direct segment to appropriate socket 32 bits source port # dest port # other header fields application data (payload) TCP/UDP segment format Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -7

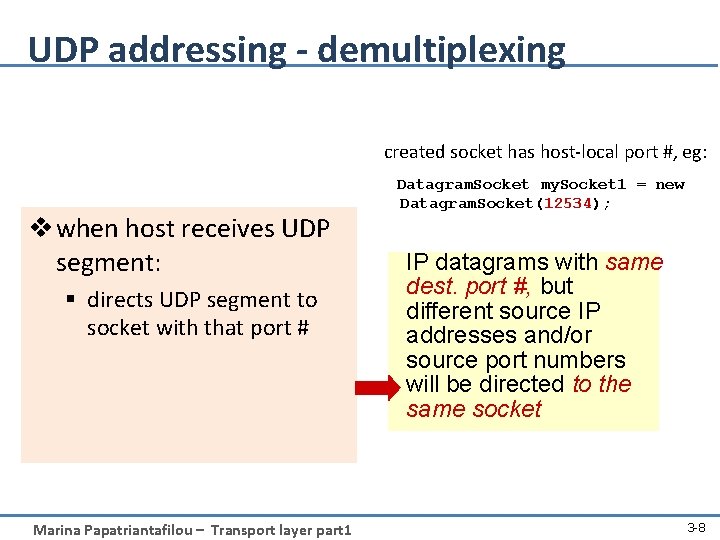
UDP addressing - demultiplexing created socket has host-local port #, eg: v when host receives UDP segment: § directs UDP segment to socket with that port # Marina Papatriantafilou – Transport layer part 1 Datagram. Socket my. Socket 1 = new Datagram. Socket(12534); IP datagrams with same dest. port #, but different source IP addresses and/or source port numbers will be directed to the same socket 3 -8

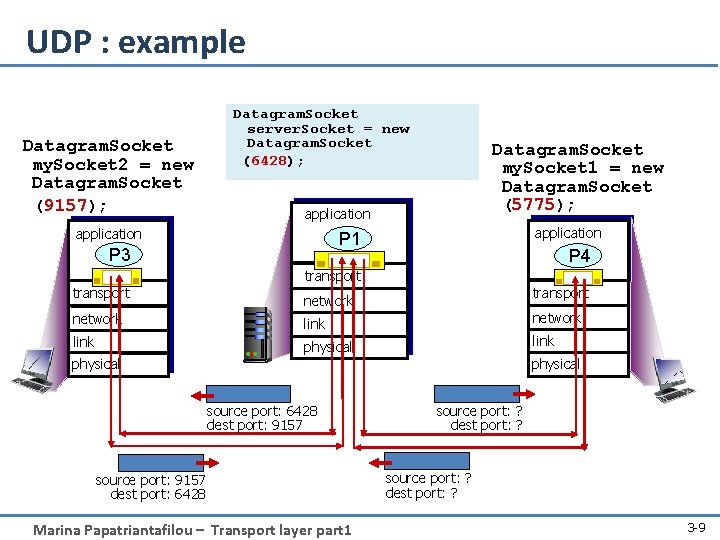
UDP : example Datagram. Socket my. Socket 2 = new Datagram. Socket (9157); Datagram. Socket server. Socket = new Datagram. Socket (6428); Datagram. Socket my. Socket 1 = new Datagram. Socket (5775); application P 1 P 3 P 4 transport network link physical source port: 6428 dest port: 9157 source port: 9157 dest port: 6428 Marina Papatriantafilou – Transport layer part 1 source port: ? dest port: ? 3 -9

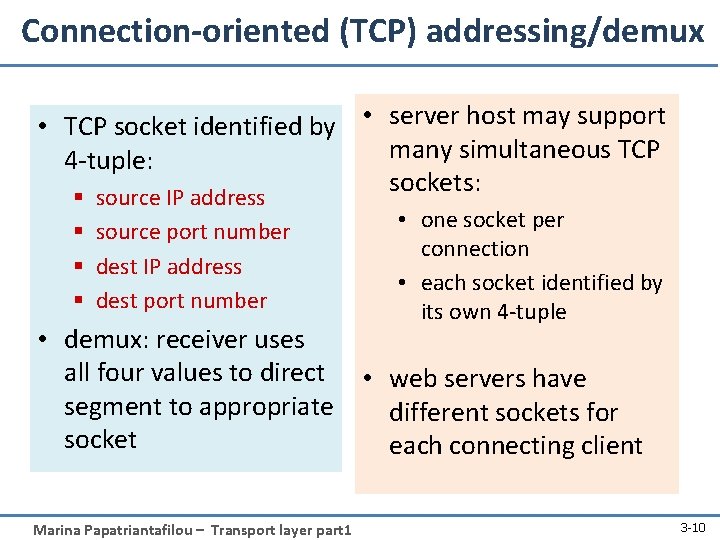
Connection-oriented (TCP) addressing/demux • TCP socket identified by • server host may support many simultaneous TCP 4 -tuple: sockets: § source IP address § source port number § dest IP address § dest port number • one socket per connection • each socket identified by its own 4 -tuple • demux: receiver uses all four values to direct • web servers have segment to appropriate different sockets for socket each connecting client Marina Papatriantafilou – Transport layer part 1 3 -10

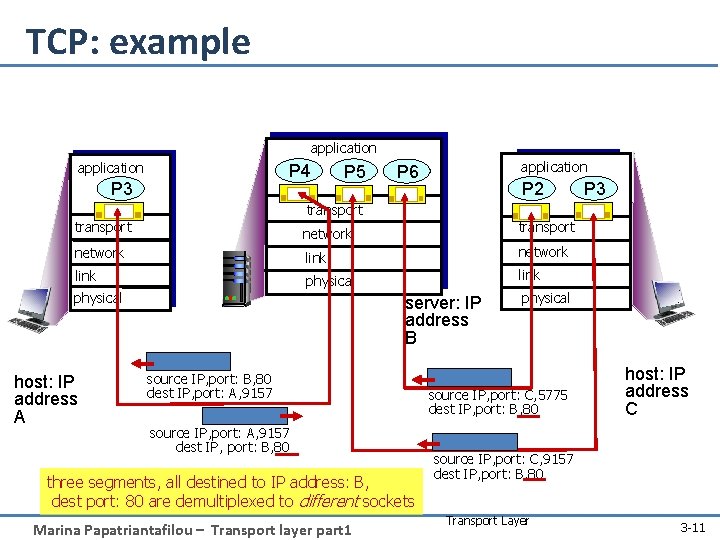
TCP: example application P 4 P 3 P 5 application P 6 P 2 P 3 transport network link physical host: IP address A server: IP address B source IP, port: B, 80 dest IP, port: A, 9157 source IP, port: A, 9157 dest IP, port: B, 80 three segments, all destined to IP address: B, dest port: 80 are demultiplexed to different sockets Marina Papatriantafilou – Transport layer part 1 physical source IP, port: C, 5775 dest IP, port: B, 80 host: IP address C source IP, port: C, 9157 dest IP, port: B, 80 Transport Layer 3 -11

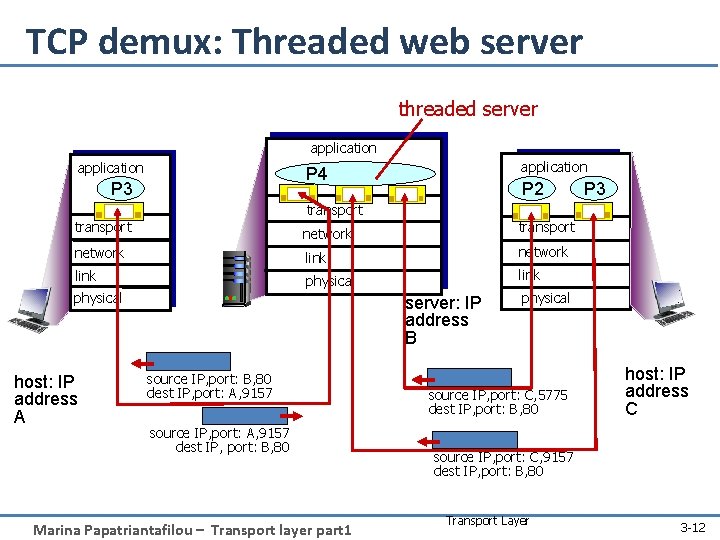
TCP demux: Threaded web server threaded server application P 4 P 3 P 2 P 3 transport network link physical host: IP address A server: IP address B source IP, port: B, 80 dest IP, port: A, 9157 source IP, port: A, 9157 dest IP, port: B, 80 Marina Papatriantafilou – Transport layer part 1 physical source IP, port: C, 5775 dest IP, port: B, 80 host: IP address C source IP, port: C, 9157 dest IP, port: B, 80 Transport Layer 3 -12

Roadmap • • Transport layer services Addressing, multiplexing/demultiplexing Connectionless, unreliable transport: UDP principles of reliable data transfer • Next lecture: connection-oriented transport: TCP – reliable transfer – flow control – connection management – TCP congestion control Marina Papatriantafilou – Transport layer part 1 3 a-13
![UDP User Datagram Protocol RFC 768 best effort service UDP segments may be UDP: User Datagram Protocol [RFC 768] “best effort” service, UDP segments may be: –](https://slidetodoc.com/presentation_image_h/d7fd5ed90c2335c99455df5a7c8614f2/image-14.jpg)
UDP: User Datagram Protocol [RFC 768] “best effort” service, UDP segments may be: – lost – delivered out-of-order • connectionless: – no handshaking between UDP sender, receiver – each UDP segment handled independently of others Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -14

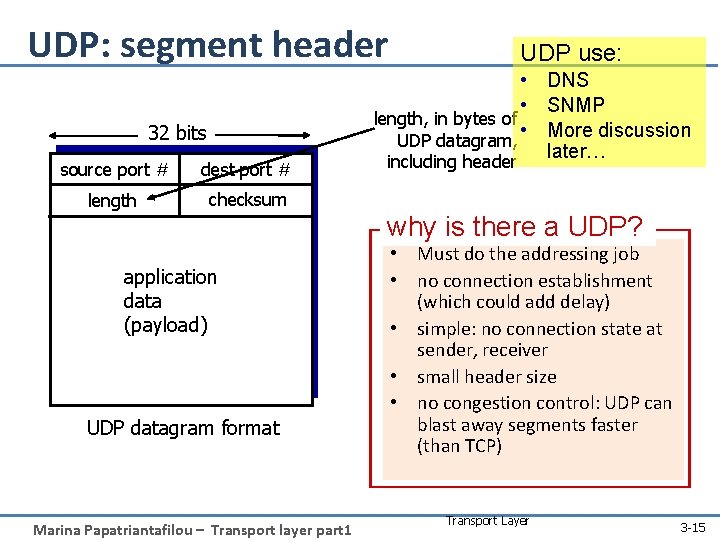
UDP: segment header 32 bits source port # dest port # length checksum UDP use: • DNS • SNMP length, in bytes of • More discussion UDP datagram, later… including header why is there a UDP? application data (payload) UDP datagram format Marina Papatriantafilou – Transport layer part 1 • Must do the addressing job • no connection establishment (which could add delay) • simple: no connection state at sender, receiver • small header size • no congestion control: UDP can blast away segments faster (than TCP) Transport Layer 3 -15
![UDP ChecksumRFC 1071 check bit flips Sender Receiver r treat segment contents as r UDP Checksum[RFC 1071]: check bit flips Sender: Receiver: r treat segment contents as r](https://slidetodoc.com/presentation_image_h/d7fd5ed90c2335c99455df5a7c8614f2/image-16.jpg)
UDP Checksum[RFC 1071]: check bit flips Sender: Receiver: r treat segment contents as r compute checksum of received sequence of 16 -bit integers r checksum: addition (1’s complement sum) of segment contents r sender puts checksum value into UDP checksum field segment r check if computed checksum equals checksum field value: m NO - error detected (report error to app or discard) m YES - no error detected. • But maybe (rarely) errors nonethless? More later …. 1 1 0 0 1 1 1 0 1 0 1 Wraparound: 1 1 0 1 1 Add to final sum checksum 1 1 0 1 1 0 0 0 1 0 0 1 1 Marina Papatriantafilou – Transport layer part 1 3 -16

Roadmap • • Transport layer services Addressing, multiplexing/demultiplexing Connectionless, unreliable transport: UDP principles of reliable data transfer • Next lecture: connection-oriented transport: TCP – reliable transfer – flow control – connection management – TCP congestion control Marina Papatriantafilou – Transport layer part 1 3 a-17

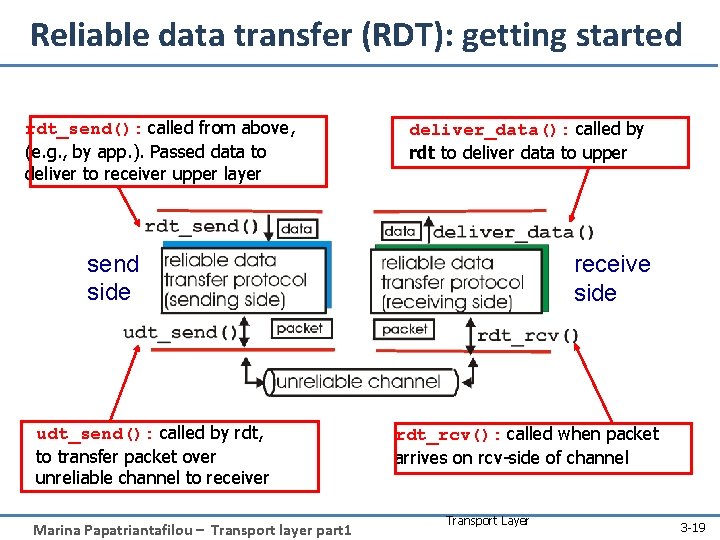
Principles of reliable data transfer top-10 list of important networking topics! characteristics of unreliable channel will determine complexity of reliable data transfer protocol (rdt) Marina Papatriantafilou – Transport layer part 1 3 -18

Reliable data transfer (RDT): getting started rdt_send(): called from above, (e. g. , by app. ). Passed data to deliver to receiver upper layer deliver_data(): called by rdt to deliver data to upper send side udt_send(): called by rdt, to transfer packet over unreliable channel to receiver Marina Papatriantafilou – Transport layer part 1 receive side rdt_rcv(): called when packet arrives on rcv-side of channel Transport Layer 3 -19

Is it possible to have reliable transfer over UDP? Marina Papatriantafilou – Transport layer part 1 20

reliable transfer over UDP? • add reliability at application layer • application-specific error recovery • But best to: not “reinvent “TCP on top of UDP • i. e. . if you need TCP, use TCP Marina Papatriantafilou – Transport layer part 1 21

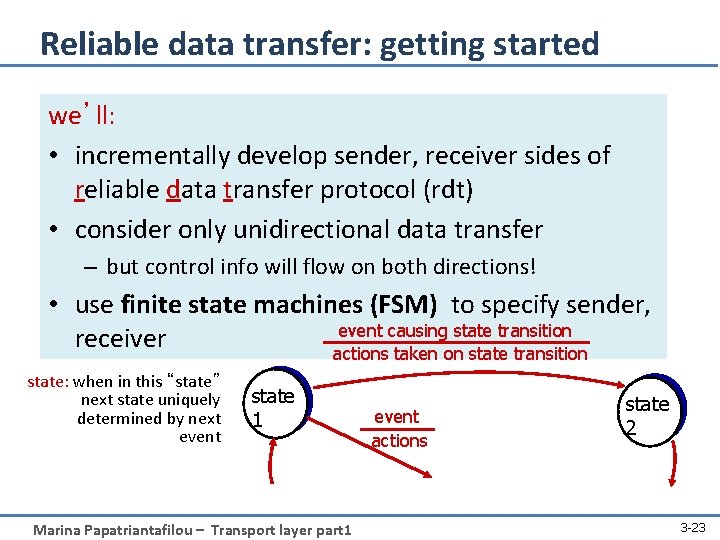
RDT: S application: Author Writes and Sends pages S transport: secretary Alice Must send pages on behalf of author R application: publisher Receives & publishes written pages S transport: secretary Bob Receives pages; Must pass on to publisher in-order Birirectional 1 -page-at-a-time-MMS connection A sends one page at a time; How do A & B do their job if MMS connection… • …is reliable? • …might introduce errors? • …might lose MMSs? Marina Papatriantafilou – Transport layer part 1 22

Reliable data transfer: getting started we’ll: • incrementally develop sender, receiver sides of reliable data transfer protocol (rdt) • consider only unidirectional data transfer – but control info will flow on both directions! • use finite state machines (FSM) to specify sender, event causing state transition receiver actions taken on state transition state: when in this “state” next state uniquely determined by next event state 1 Marina Papatriantafilou – Transport layer part 1 event actions state 2 3 -23

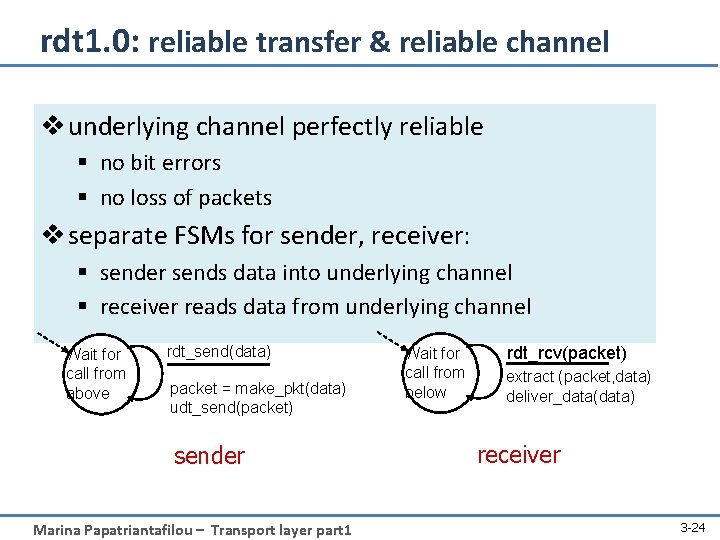
rdt 1. 0: reliable transfer & reliable channel v underlying channel perfectly reliable § no bit errors § no loss of packets v separate FSMs for sender, receiver: § sender sends data into underlying channel § receiver reads data from underlying channel Wait for call from above rdt_send(data) packet = make_pkt(data) udt_send(packet) sender Marina Papatriantafilou – Transport layer part 1 Wait for call from below rdt_rcv(packet) extract (packet, data) deliver_data(data) receiver 3 -24

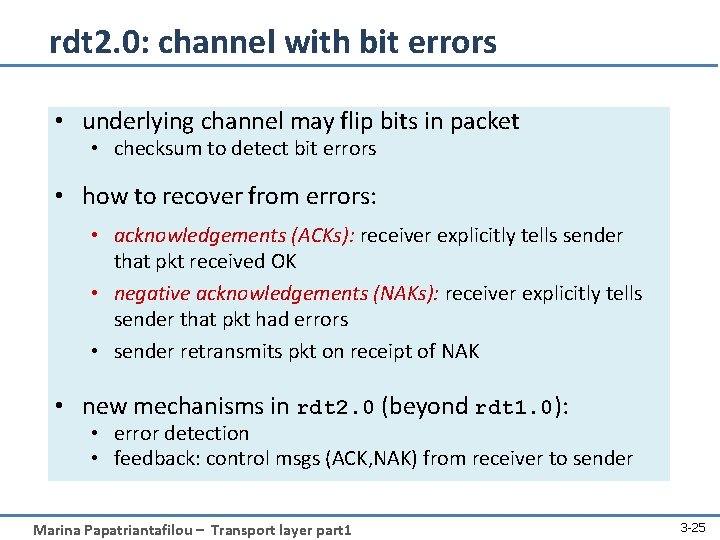
rdt 2. 0: channel with bit errors • underlying channel may flip bits in packet • checksum to detect bit errors • how to recover from errors: • acknowledgements (ACKs): receiver explicitly tells sender that pkt received OK • negative acknowledgements (NAKs): receiver explicitly tells sender that pkt had errors • sender retransmits pkt on receipt of NAK • new mechanisms in rdt 2. 0 (beyond rdt 1. 0): • error detection • feedback: control msgs (ACK, NAK) from receiver to sender Marina Papatriantafilou – Transport layer part 1 3 -25

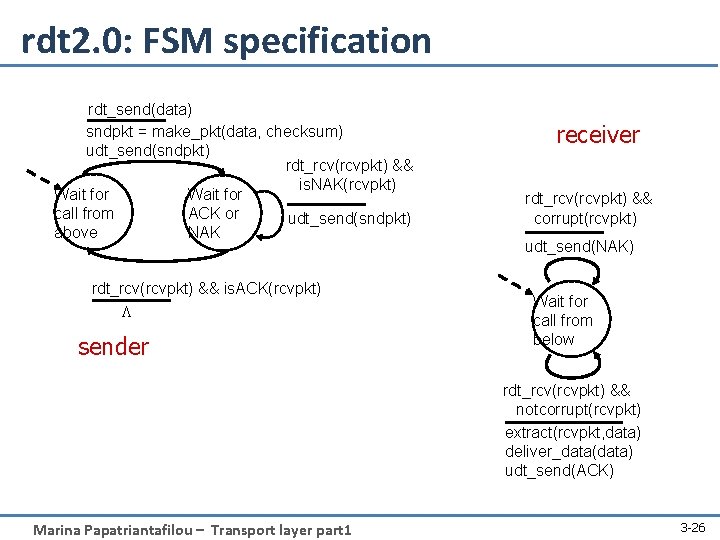
rdt 2. 0: FSM specification rdt_send(data) sndpkt = make_pkt(data, checksum) udt_send(sndpkt) rdt_rcv(rcvpkt) && is. NAK(rcvpkt) Wait for call from ACK or udt_send(sndpkt) above NAK rdt_rcv(rcvpkt) && is. ACK(rcvpkt) L sender receiver rdt_rcv(rcvpkt) && corrupt(rcvpkt) udt_send(NAK) Wait for call from below rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) extract(rcvpkt, data) deliver_data(data) udt_send(ACK) Marina Papatriantafilou – Transport layer part 1 3 -26

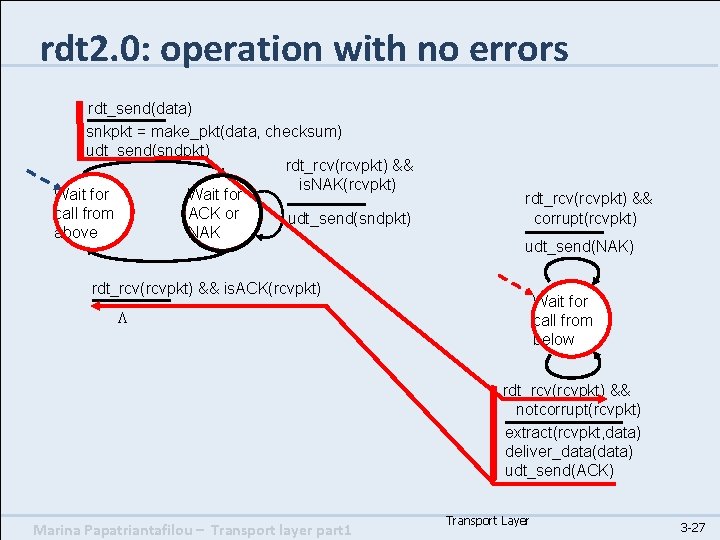
rdt 2. 0: operation with no errors rdt_send(data) snkpkt = make_pkt(data, checksum) udt_send(sndpkt) rdt_rcv(rcvpkt) && is. NAK(rcvpkt) Wait for call from ACK or udt_send(sndpkt) above NAK rdt_rcv(rcvpkt) && corrupt(rcvpkt) udt_send(NAK) rdt_rcv(rcvpkt) && is. ACK(rcvpkt) Wait for call from below L rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) extract(rcvpkt, data) deliver_data(data) udt_send(ACK) Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -27

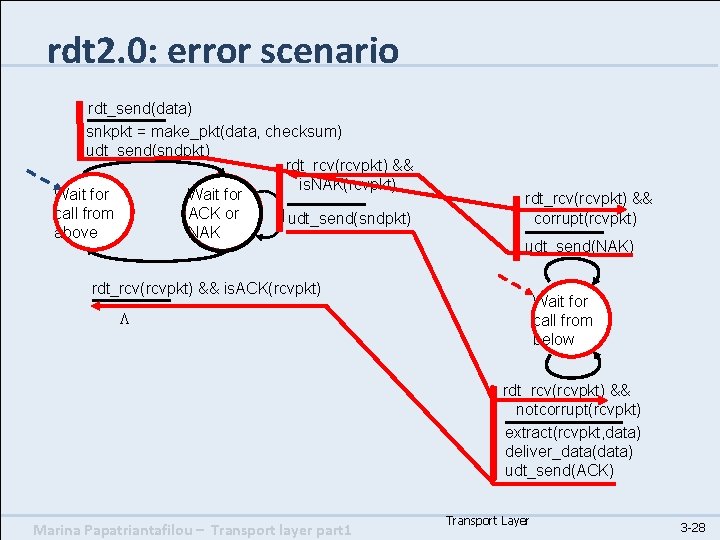
rdt 2. 0: error scenario rdt_send(data) snkpkt = make_pkt(data, checksum) udt_send(sndpkt) rdt_rcv(rcvpkt) && is. NAK(rcvpkt) Wait for call from ACK or udt_send(sndpkt) above NAK rdt_rcv(rcvpkt) && corrupt(rcvpkt) udt_send(NAK) rdt_rcv(rcvpkt) && is. ACK(rcvpkt) Wait for call from below L rdt_rcv(rcvpkt) && notcorrupt(rcvpkt) extract(rcvpkt, data) deliver_data(data) udt_send(ACK) Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -28

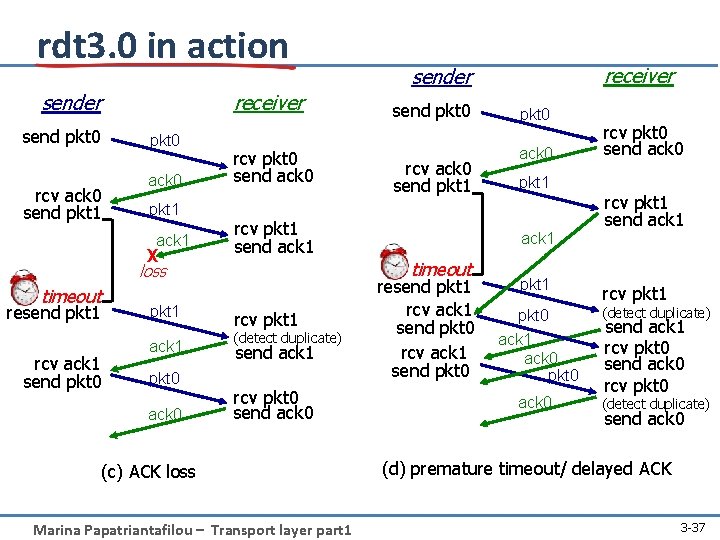
rdt 3. 0: channels with errors and loss new assumption: underlying channel can also lose packets (data, ACKs) approach: sender waits “reasonable” amount of time for ACK • retransmits if no ACK received in this time • requires countdown timer • if pkt (or ACK) just delayed (not lost): – Must handle duplicates -> Marina Papatriantafilou – Transport layer part 1 handling duplicates: • sender adds sequence number to each pkt • receiver discards (doesn’t deliver up) duplicate pkt 3 -34

rdt 3. 0 in action receiver send pkt 0 rcv ack 0 send pkt 1 rcv ack 1 send pkt 0 ack 0 pkt 1 ack 1 pkt 0 ack 0 send pkt 0 rcv pkt 0 send ack 0 rcv pkt 1 send ack 1 rcv pkt 0 send ack 0 (a) no loss receiver sender rcv ack 0 send pkt 1 pkt 0 ack 0 rcv pkt 0 send ack 0 pkt 1 X loss timeout resend pkt 1 rcv ack 1 send pkt 0 pkt 1 ack 1 pkt 0 ack 0 rcv pkt 1 send ack 1 rcv pkt 0 send ack 0 (b) packet loss Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -36

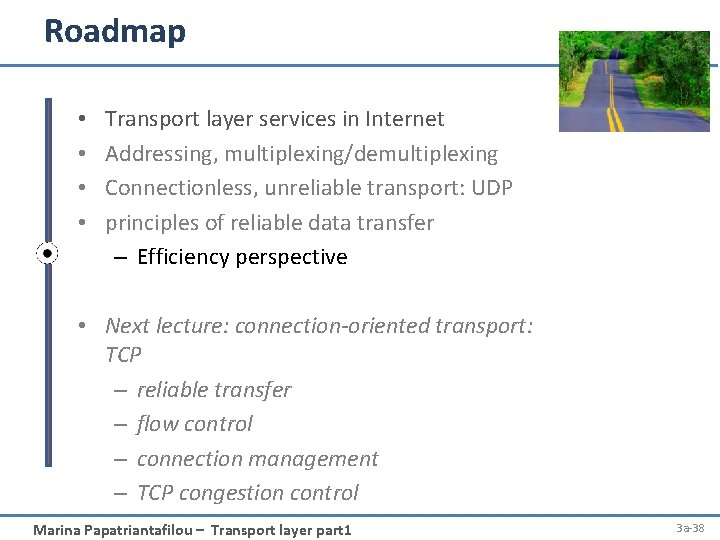
rdt 3. 0 in action receiver send pkt 0 rcv ack 0 send pkt 1 ack 0 pkt 1 ack 1 X rcv pkt 0 send ack 0 timeout resend pkt 1 rcv ack 1 send pkt 0 pkt 1 ack 1 pkt 0 ack 0 send pkt 0 rcv ack 0 send pkt 1 rcv pkt 1 send ack 1 rcv pkt 1 (detect duplicate) send ack 1 rcv pkt 0 send ack 0 (c) ACK loss Marina Papatriantafilou – Transport layer part 1 pkt 0 ack 0 pkt 1 ack 1 timeout loss receiver sender resend pkt 1 rcv ack 1 send pkt 0 pkt 1 rcv pkt 0 send ack 0 rcv pkt 1 send ack 1 rcv pkt 1 pkt 0 ack 1 ack 0 pkt 0 (detect duplicate) ack 0 (detect duplicate) send ack 1 rcv pkt 0 send ack 0 (d) premature timeout/ delayed ACK 3 -37

Roadmap • • Transport layer services in Internet Addressing, multiplexing/demultiplexing Connectionless, unreliable transport: UDP principles of reliable data transfer – Efficiency perspective • Next lecture: connection-oriented transport: TCP – reliable transfer – flow control – connection management – TCP congestion control Marina Papatriantafilou – Transport layer part 1 3 a-38

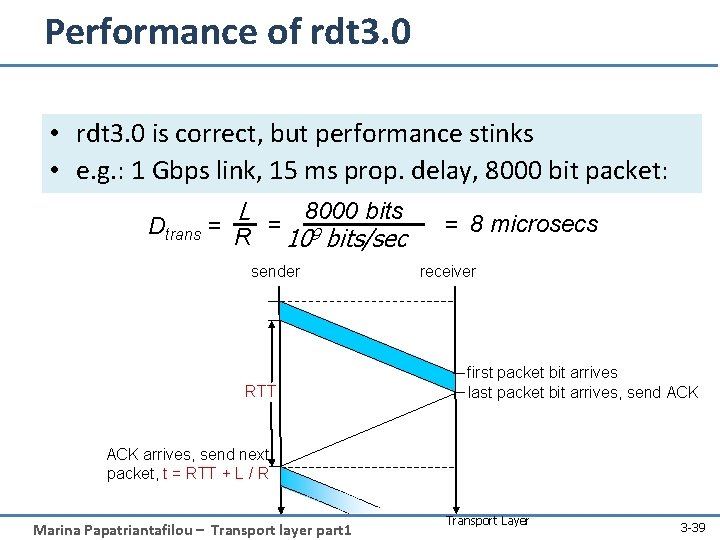
Performance of rdt 3. 0 • rdt 3. 0 is correct, but performance stinks • e. g. : 1 Gbps link, 15 ms prop. delay, 8000 bit packet: L 8000 bits Dtrans = R = 9 10 bits/sec sender RTT = 8 microsecs receiver first packet bit arrives last packet bit arrives, send ACK arrives, send next packet, t = RTT + L / R Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -39

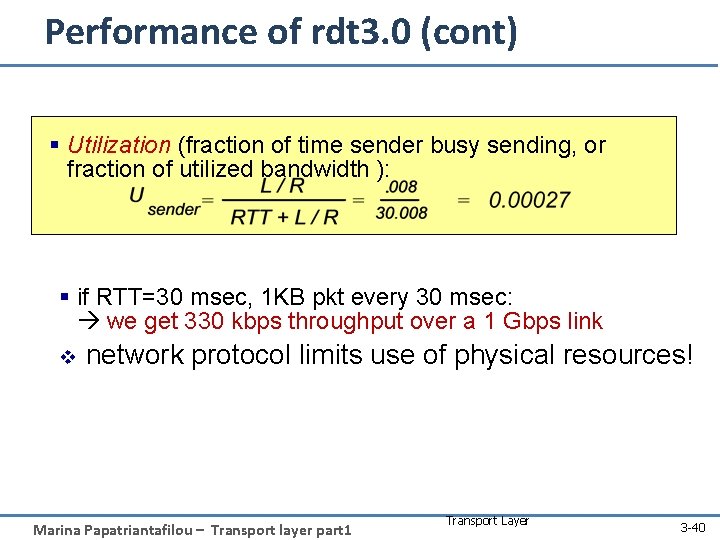
Performance of rdt 3. 0 (cont) § Utilization (fraction of time sender busy sending, or fraction of utilized bandwidth ): § if RTT=30 msec, 1 KB pkt every 30 msec: we get 330 kbps throughput over a 1 Gbps link v network protocol limits use of physical resources! Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -40

Is RDT necessarily that slow/inefficient? Marina Papatriantafilou – Transport layer part 1 41

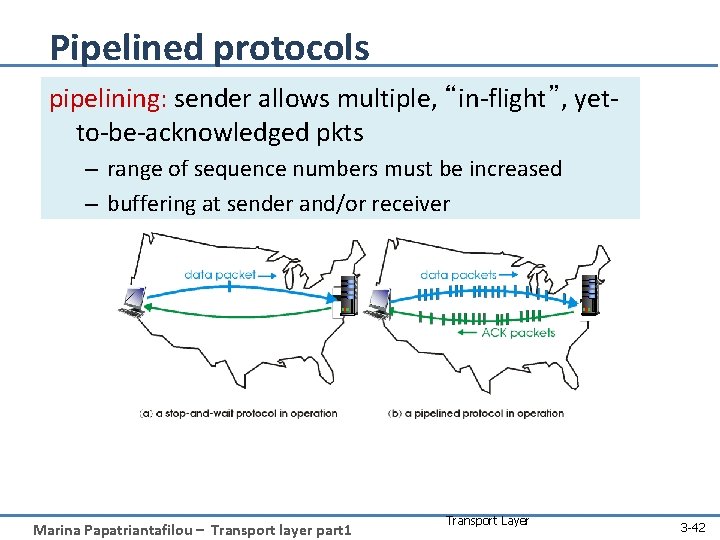
Pipelined protocols pipelining: sender allows multiple, “in-flight”, yetto-be-acknowledged pkts – range of sequence numbers must be increased – buffering at sender and/or receiver Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -42

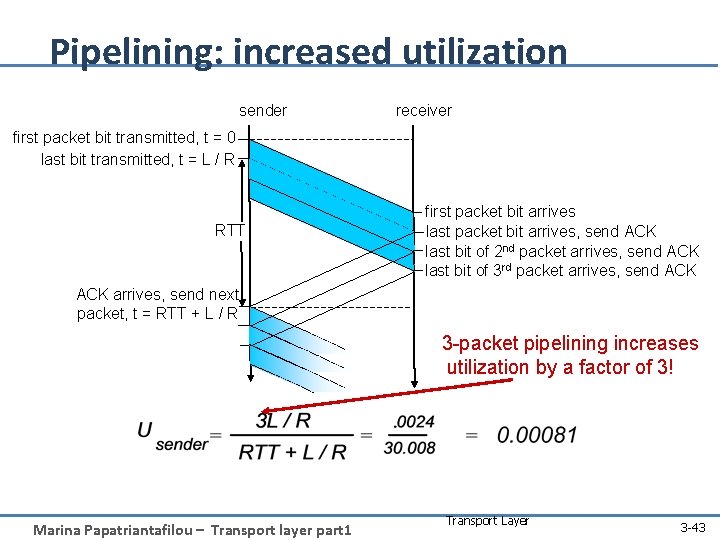
Pipelining: increased utilization sender receiver first packet bit transmitted, t = 0 last bit transmitted, t = L / R RTT first packet bit arrives last packet bit arrives, send ACK last bit of 2 nd packet arrives, send ACK last bit of 3 rd packet arrives, send ACK arrives, send next packet, t = RTT + L / R 3 -packet pipelining increases utilization by a factor of 3! Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -43

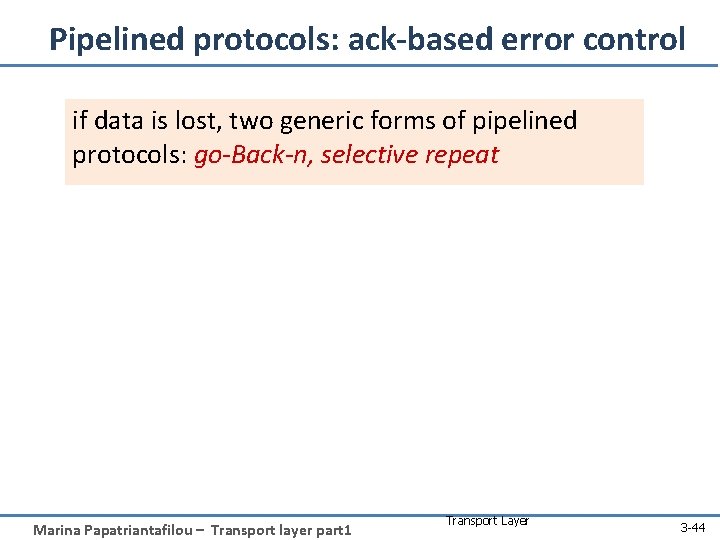
Pipelined protocols: ack-based error control if data is lost, two generic forms of pipelined protocols: go-Back-n, selective repeat Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -44

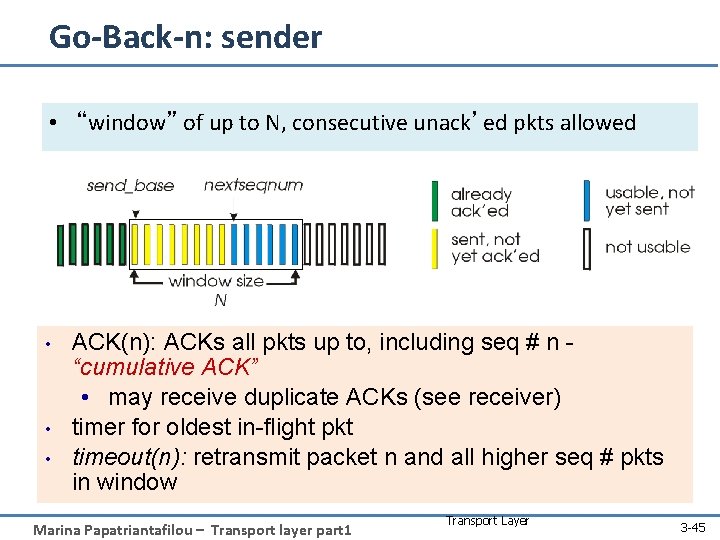
Go-Back-n: sender • “window” of up to N, consecutive unack’ed pkts allowed • • • ACK(n): ACKs all pkts up to, including seq # n “cumulative ACK” • may receive duplicate ACKs (see receiver) timer for oldest in-flight pkt timeout(n): retransmit packet n and all higher seq # pkts in window Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -45

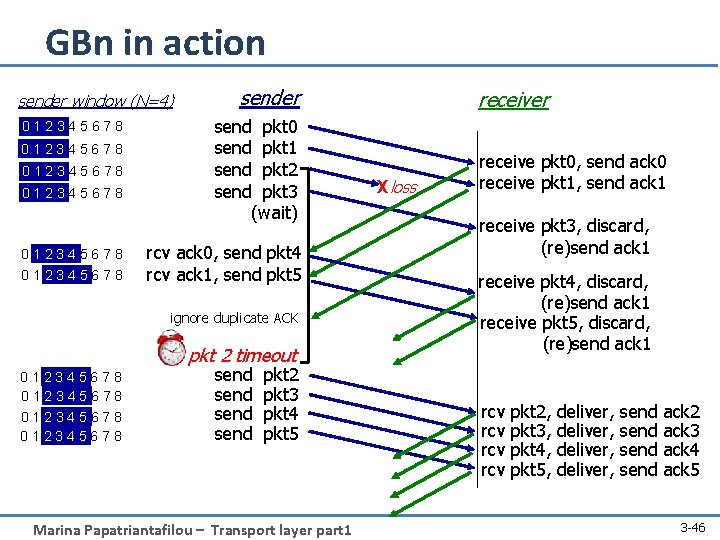
GBn in action sender window (N=4) 012345678 012345678 sender send pkt 0 send pkt 1 send pkt 2 send pkt 3 (wait) rcv ack 0, send pkt 4 rcv ack 1, send pkt 5 ignore duplicate ACK pkt 2 timeout 012345678 send pkt 2 pkt 3 pkt 4 pkt 5 Marina Papatriantafilou – Transport layer part 1 receiver Xloss receive pkt 0, send ack 0 receive pkt 1, send ack 1 receive pkt 3, discard, (re)send ack 1 receive pkt 4, discard, (re)send ack 1 receive pkt 5, discard, (re)send ack 1 rcv rcv pkt 2, pkt 3, pkt 4, pkt 5, deliver, send ack 2 ack 3 ack 4 ack 5 3 -46

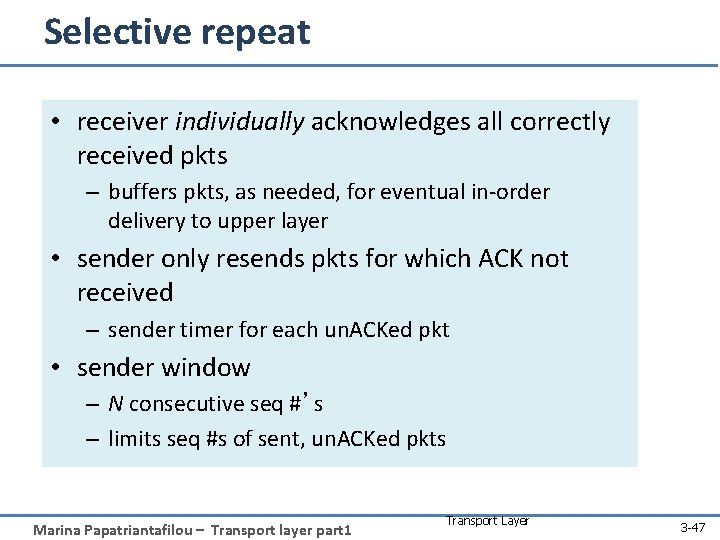
Selective repeat • receiver individually acknowledges all correctly received pkts – buffers pkts, as needed, for eventual in-order delivery to upper layer • sender only resends pkts for which ACK not received – sender timer for each un. ACKed pkt • sender window – N consecutive seq #’s – limits seq #s of sent, un. ACKed pkts Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -47

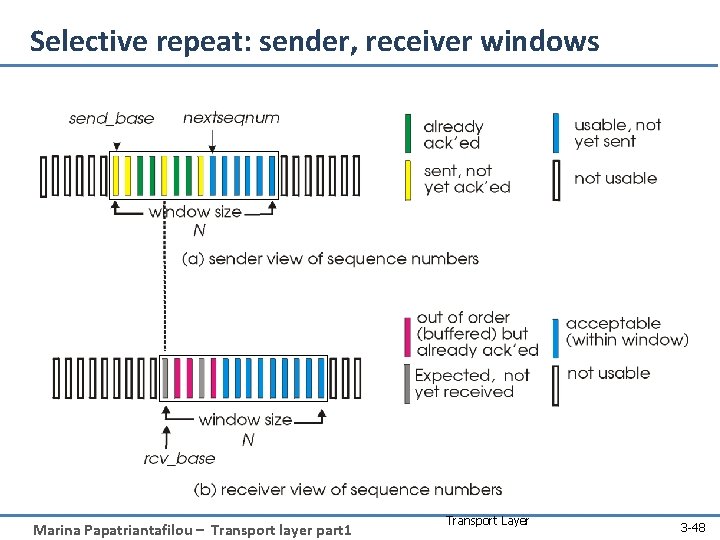
Selective repeat: sender, receiver windows Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -48

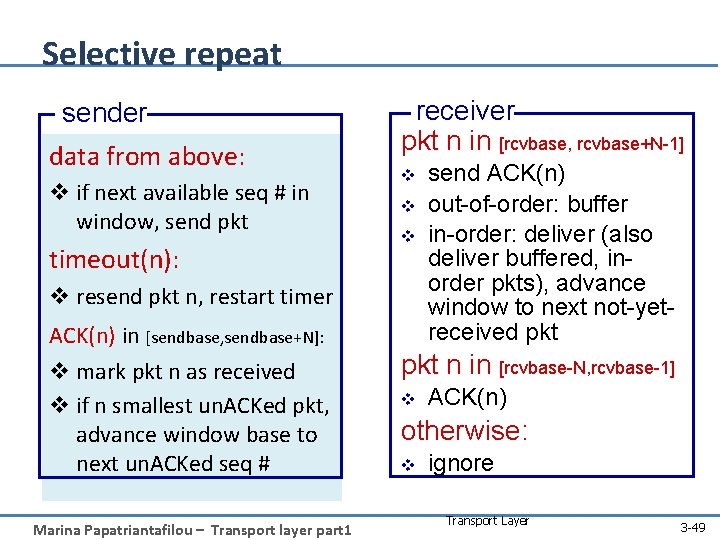
Selective repeat sender data from above: v if next available seq # in window, send pkt timeout(n): receiver pkt n in [rcvbase, rcvbase+N-1] v v resend pkt n, restart timer ACK(n) in [sendbase, sendbase+N]: v mark pkt n as received v if n smallest un. ACKed pkt, advance window base to next un. ACKed seq # Marina Papatriantafilou – Transport layer part 1 send ACK(n) out-of-order: buffer in-order: deliver (also deliver buffered, inorder pkts), advance window to next not-yetreceived pkt n in [rcvbase-N, rcvbase-1] v ACK(n) otherwise: v ignore Transport Layer 3 -49

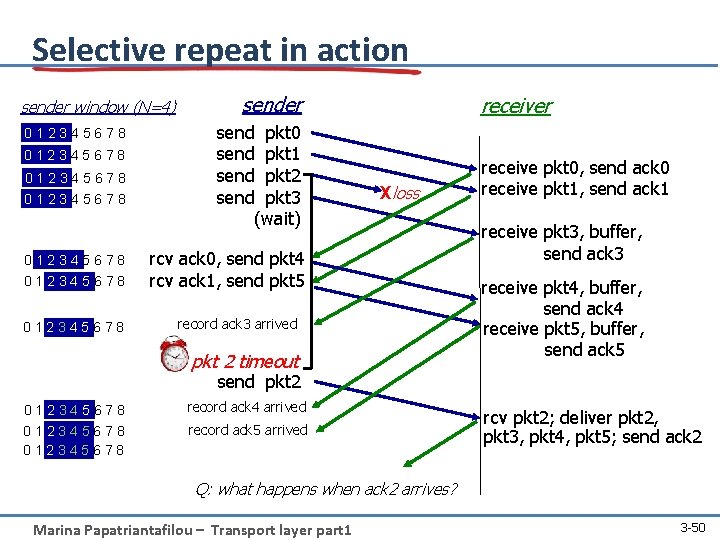
Selective repeat in action sender window (N=4) 012345678 012345678 sender send pkt 0 send pkt 1 send pkt 2 send pkt 3 (wait) receiver Xloss rcv ack 0, send pkt 4 rcv ack 1, send pkt 5 record ack 3 arrived pkt 2 timeout receive pkt 0, send ack 0 receive pkt 1, send ack 1 receive pkt 3, buffer, send ack 3 receive pkt 4, buffer, send ack 4 receive pkt 5, buffer, send ack 5 send pkt 2 012345678 record ack 4 arrived record ack 5 arrived rcv pkt 2; deliver pkt 2, pkt 3, pkt 4, pkt 5; send ack 2 Q: what happens when ack 2 arrives? Marina Papatriantafilou – Transport layer part 1 3 -50

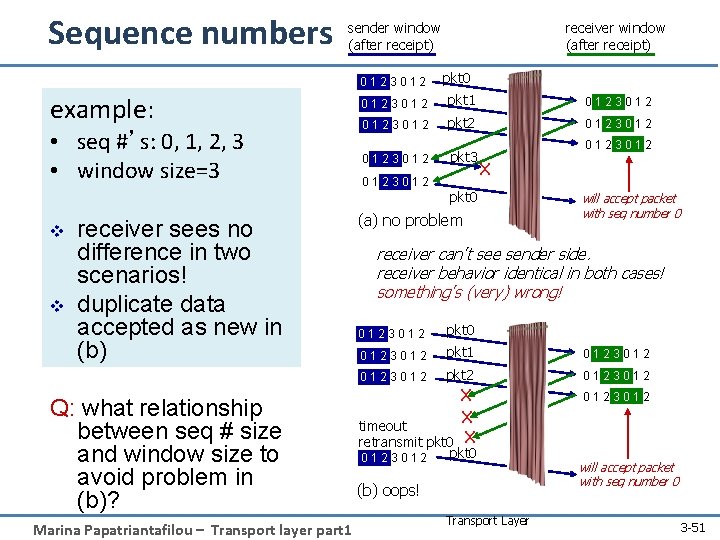
Sequence numbers receiver window (after receipt) sender window (after receipt) 0123012 pkt 0 example: 0123012 pkt 1 0123012 • seq #’s: 0, 1, 2, 3 • window size=3 0123012 pkt 2 0123012 pkt 3 v v receiver sees no difference in two scenarios! duplicate data accepted as new in (b) Q: what relationship between seq # size and window size to avoid problem in (b)? Marina Papatriantafilou – Transport layer part 1 0123012 X pkt 0 (a) no problem will accept packet with seq number 0 receiver can’t see sender side. receiver behavior identical in both cases! something’s (very) wrong! 0123012 pkt 0 0123012 pkt 1 0123012 pkt 2 0123012 X X timeout retransmit pkt 0 X 0123012 pkt 0 (b) oops! Transport Layer will accept packet with seq number 0 3 -51

Question What do Ack’s achieve besides reliability? Flow control: receiver can ack its receiving capacity i. e. avoid swamping the receiver Flow control: Sender/receiver problem: S cares to not overwhelm R Marina Papatriantafilou – Transport layer part 1 52

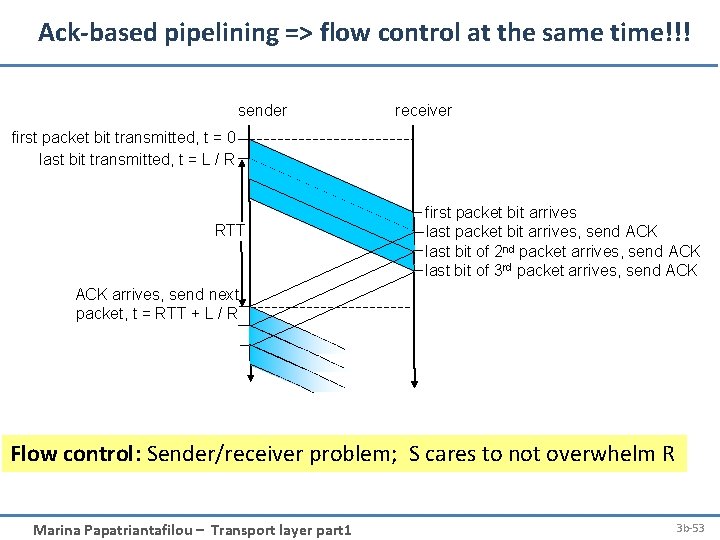
Ack-based pipelining => flow control at the same time!!! sender receiver first packet bit transmitted, t = 0 last bit transmitted, t = L / R RTT first packet bit arrives last packet bit arrives, send ACK last bit of 2 nd packet arrives, send ACK last bit of 3 rd packet arrives, send ACK arrives, send next packet, t = RTT + L / R Flow control: Sender/receiver problem; S cares to not overwhelm R Marina Papatriantafilou – Transport layer part 1 3 b-53

Question: Is congestion control the same as flow control? • No! • Congestion control = Avoid congesting the network • Congestion is network core issue (in contrast to flowcontrol, which is senderreceiver issue) Marina Papatriantafilou – Transport layer part 1 54

Roadmap • • Transport layer services Addressing, multiplexing/demultiplexing Connectionless, unreliable transport: UDP principles of reliable data transfer • Next lecture: connection-oriented transport: TCP – reliable transfer – flow control – connection management – TCP congestion control Marina Papatriantafilou – Transport layer part 1 3 a-55

Reading instructions chapter 3 • • Kurose. Ross book Careful Quick 3. 1, 3. 2, 3. 4 -3. 7 3. 3 Other resources (further, optional study) – Lakshman, T. V. , Upamanyu Madhow, and Bernhard Suter. "Window-based error recovery and flow control with a slow acknowledgement channel: a study of TCP/IP performance. " INFOCOM'97. Sixteenth Annual Joint Conference of the IEEE Computer and Communications Societies. Proceedings IEEE. Vol. 3. IEEE, 1997. – Rizzo, Luigi. "Effective erasure codes for reliable computer communication protocols. " ACM SIGCOMM Computer Communication Review 27. 2 (1997): 24 -36. – A. Agarwal and M. Charikar, “On the advantage of network coding for improving network throughput, ” in Proceedings of the IEEE Information Theory Workshop, Oct. 2004 Harvey, N. J. , Kleinberg, R. , & Lehman, A. R. (2006). On the capacity of information networks. IEEE/ACM Transactions on Networking (TON), 14(SI), 2345 -2364. – Marina Papatriantafilou – Transport layer part 1 Transport Layer 3 -56

Some review questions on this part • Why do we need an extra protocol, i. e. UDP, to deliver the datagram service of Internets IP to the applications? • Draw space-time diagrams without errors and with errors, for the following, for a pair of sender-receive S-R: (assume only 1 link between them) – Stop-and-wait: transmission delay < propagation delay and transmission delay > propagation delay – Sliding window aka pipelined protocol, with window’s transmission delay < propagation delay and window’s transmission delay > propagation delay; illustrate both go-back-n and selective repeat when there are errors – Show to compute the effective throughput between S-R in the above cases, when there are no errors Marina Papatriantafilou – Transport layer part 1 3 a-57

Review questions cont. • What are the goals of reliable data transfer? • Reliable data transfer: show why we need sequence numbers when the sender may retransmit due to timeouts. • Show there can be wraparound in a reliable data transfer session if the sequence-numbers range is not large enough. • Describe the go-back-N and selective repeat methods for reliable data transfer Marina Papatriantafilou – Transport layer part 1 3 a-58

Extra slides, for further study Marina Papatriantafilou – Transport layer part 1 3: Transport Layer 3 a-59

Bounding sequence numbers for stop-and-wait… … s. t. no wraparound, i. e. we do not run out of numbers: binary value suffices for stop-and-wait: Proof sketch: assume towards a contradiction that there is wraparound when we use binary seq. nums. – R expects segment #f, receives segment #(f+2): R rec. f+2 => S sent f+2 => S rec. ack for f+1 => R ack f+1=> R ack f => contradiction – R expects f+2, receives f: R exp. f+2 => R ack f+1 => S sent f+1 => S rec. ack for f => contradiction Marina Papatriantafilou – Transport layer part 1 3: Transport Layer 3 a-60