Connaissezvous cet endroit 2016 Check Point Software Technologies

![3 cas, 1 similarité… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 3 cas, 1 similarité… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-4.jpg)


![Que s’est-il passé ? © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content Que s’est-il passé ? © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-9.jpg)


![Dans les pays étrangers… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content Dans les pays étrangers… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-26.jpg)
![Mais aussi en France… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content Mais aussi en France… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-27.jpg)

![Impressionnant… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 29 Impressionnant… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 29](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-29.jpg)
![Ransomware-as-a-Service (Tox) © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 30 Ransomware-as-a-Service (Tox) © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 30](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-30.jpg)

![MERCI POUR VOTRE ATT ENTION © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential MERCI POUR VOTRE ATT ENTION © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-32.jpg)
- Slides: 32

Connaissez-vous cet endroit ? © 2016 Check Point Software Technologies Ltd. 1

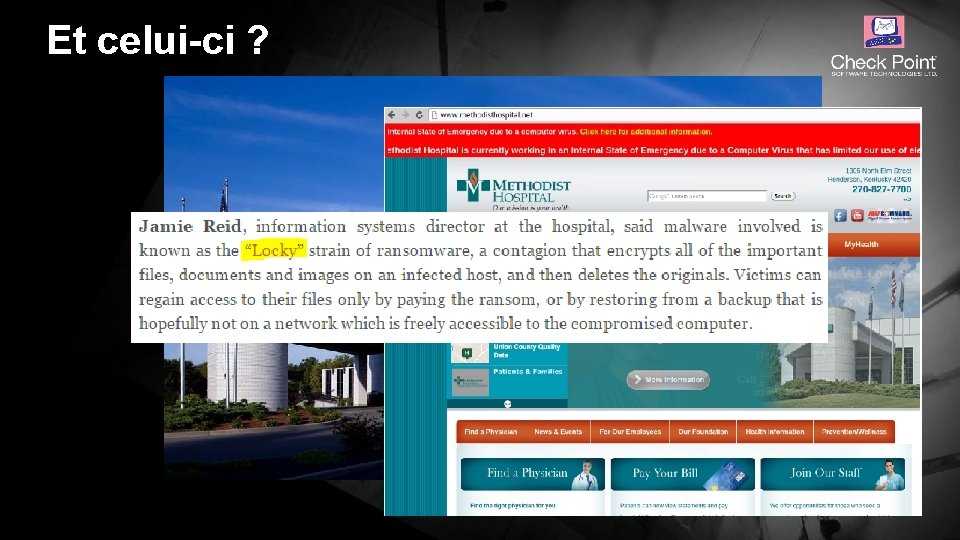
Et celui-ci ? © 2016 Check Point Software Technologies Ltd. 2

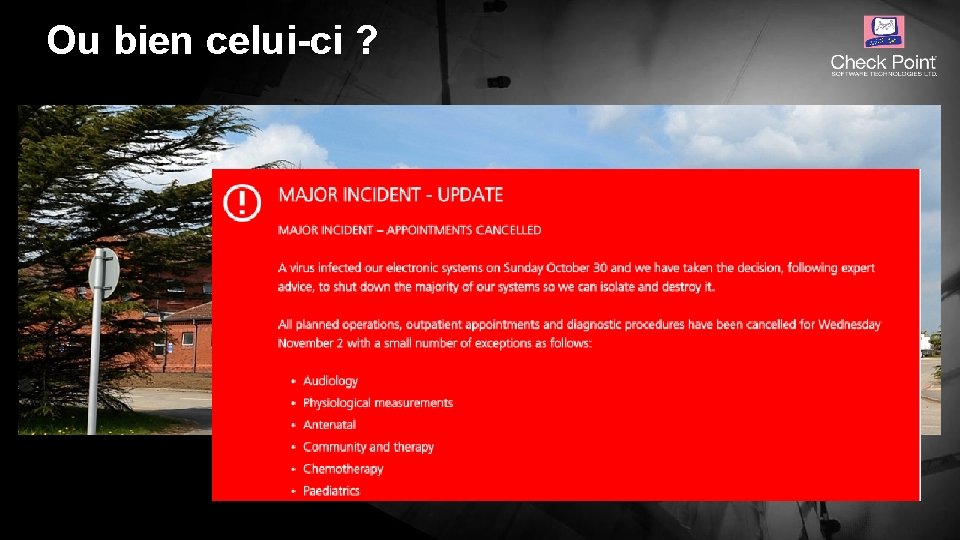
Ou bien celui-ci ? © 2016 Check Point Software Technologies Ltd. 3
![3 cas 1 similarité 2016 Check Point Software Technologies Ltd Protected Nonconfidential content 3 cas, 1 similarité… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-4.jpg)
3 cas, 1 similarité… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 4

COMPRENDRE L’IMPACT DES RAMSOMWARES Jean-Charles DUBREUCQ, Responsible commercial Secteur Public © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 5

Cela commence généralement par… © 2016 Check Point Software Technologies Ltd. 6

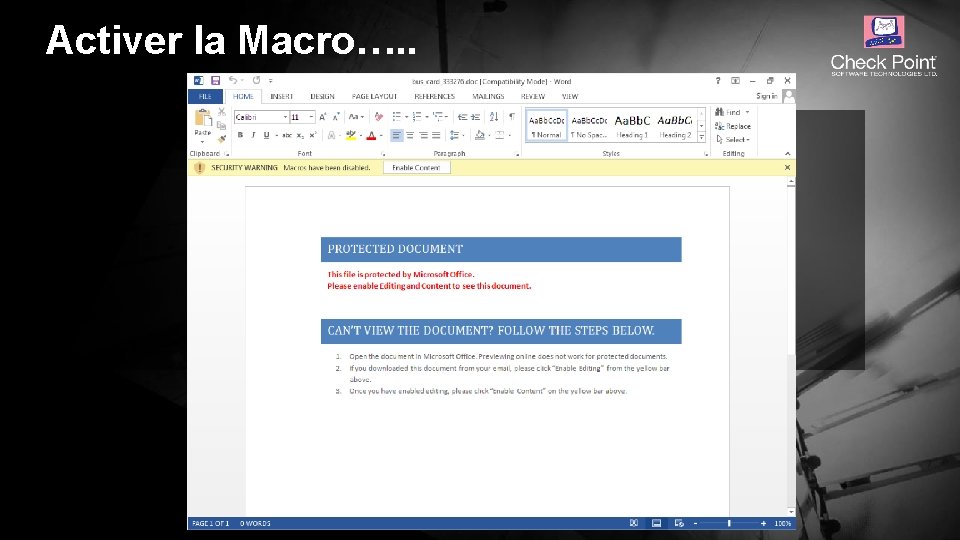
Activer la Macro…. . © 2016 Check Point Software Technologies Ltd. 7

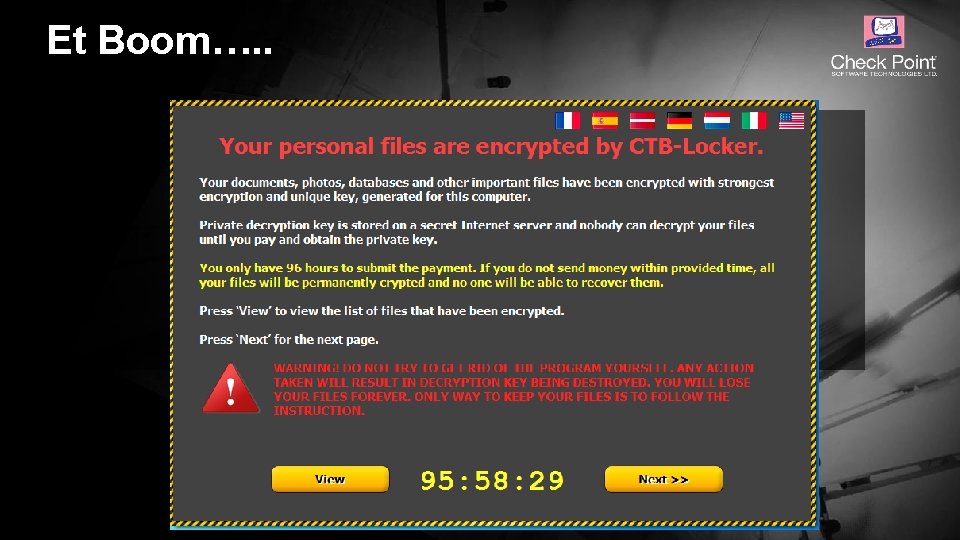
Et Boom…. . © 2016 Check Point Software Technologies Ltd. 8
![Que sestil passé 2016 Check Point Software Technologies Ltd Protected Nonconfidential content Que s’est-il passé ? © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-9.jpg)
Que s’est-il passé ? © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 9

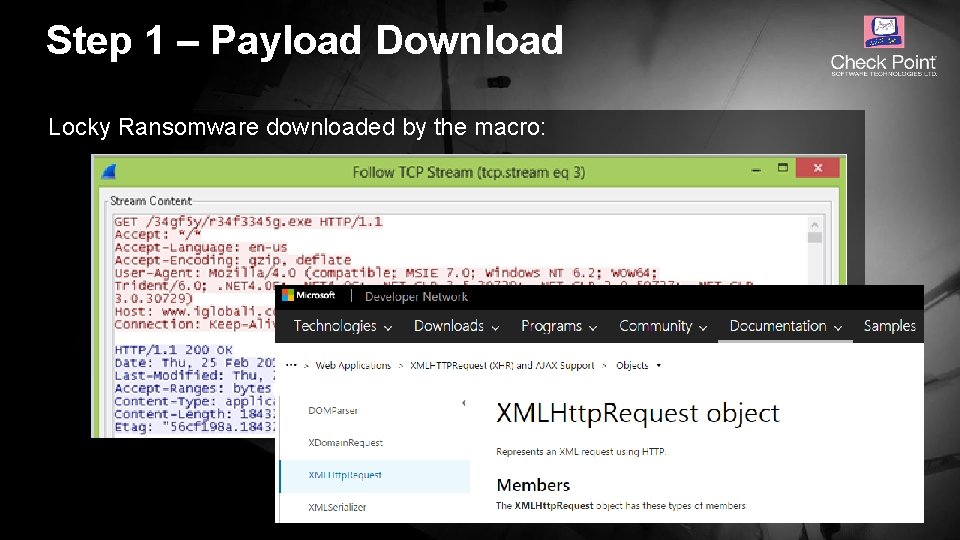
Step 1 – Payload Download Locky Ransomware downloaded by the macro: © 2016 Check Point Software Technologies Ltd. 10

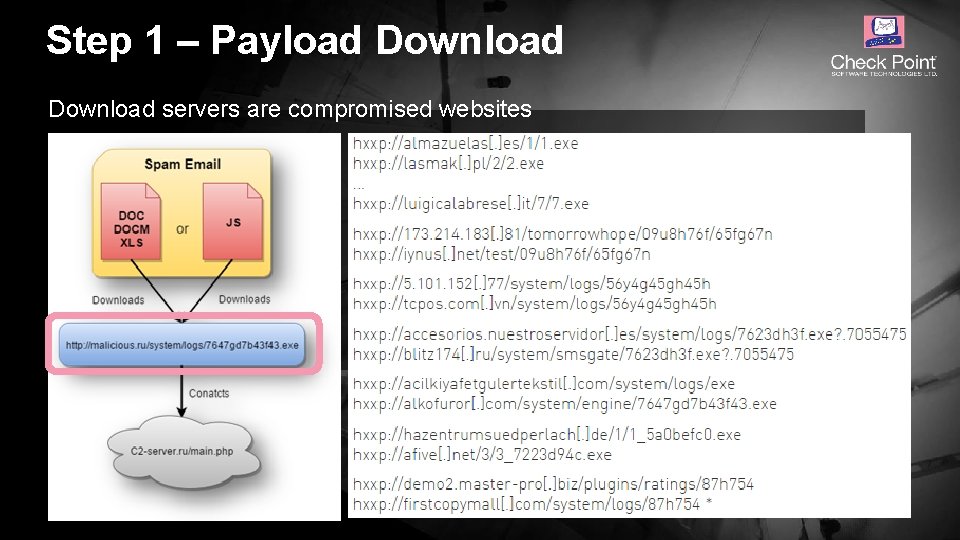
Step 1 – Payload Download servers are compromised websites © 2016 Check Point Software Technologies Ltd. 11

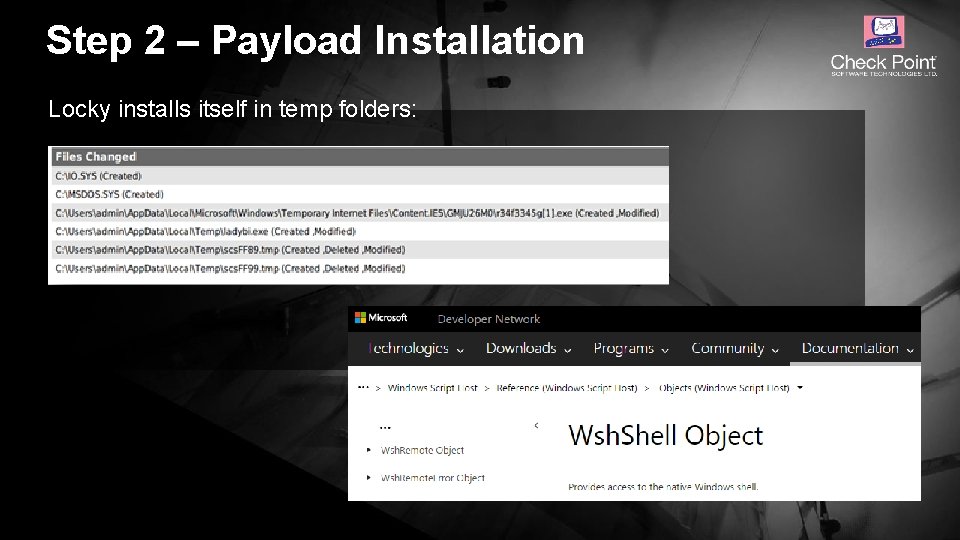
Step 2 – Payload Installation Locky installs itself in temp folders: © 2016 Check Point Software Technologies Ltd. 12

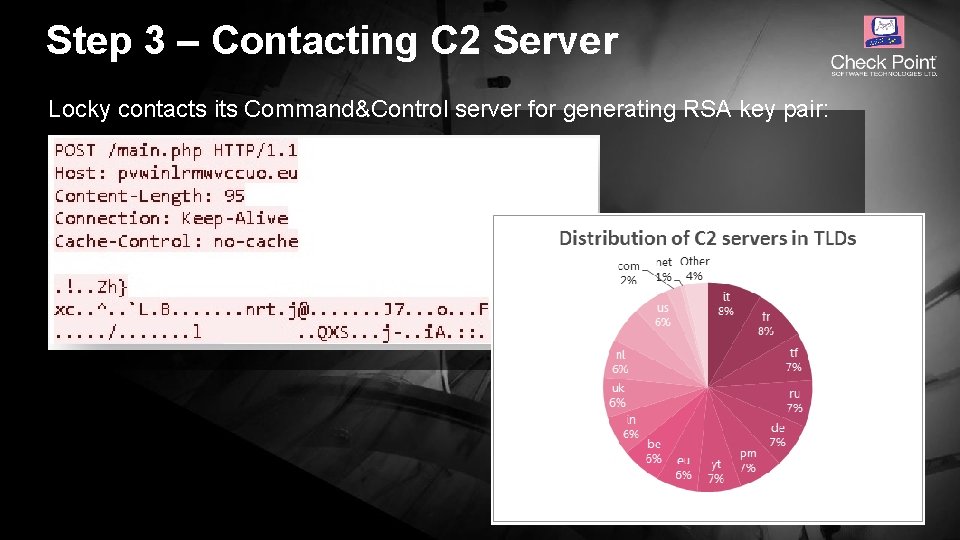
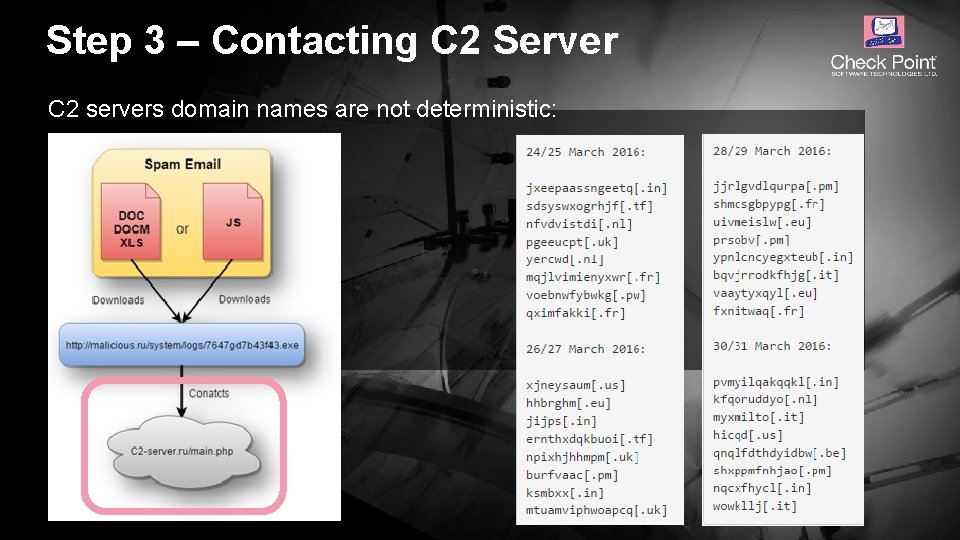
Step 3 – Contacting C 2 Server Locky contacts its Command&Control server for generating RSA key pair: © 2016 Check Point Software Technologies Ltd. 13

Step 3 – Contacting C 2 Server C 2 servers domain names are not deterministic: © 2016 Check Point Software Technologies Ltd. 14

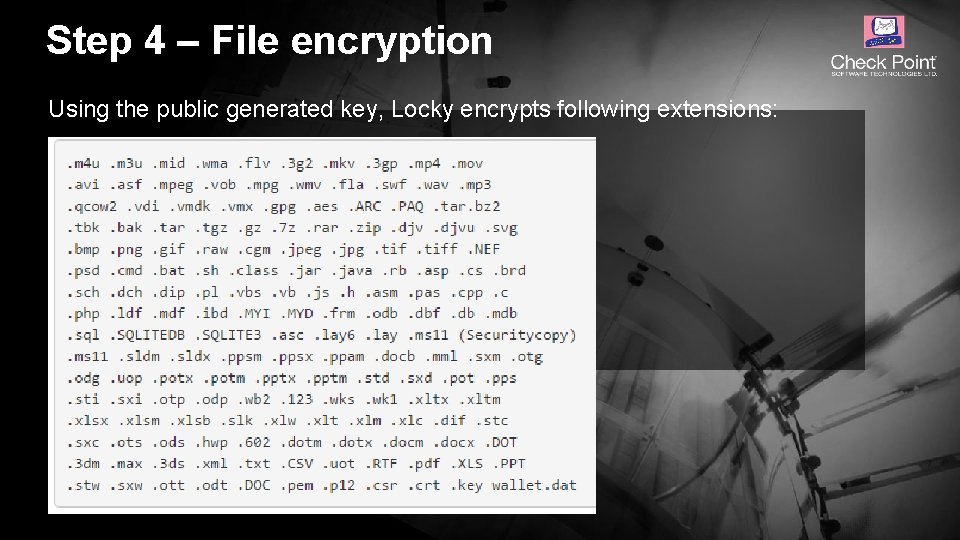
Step 4 – File encryption Using the public generated key, Locky encrypts following extensions: © 2016 Check Point Software Technologies Ltd. 15

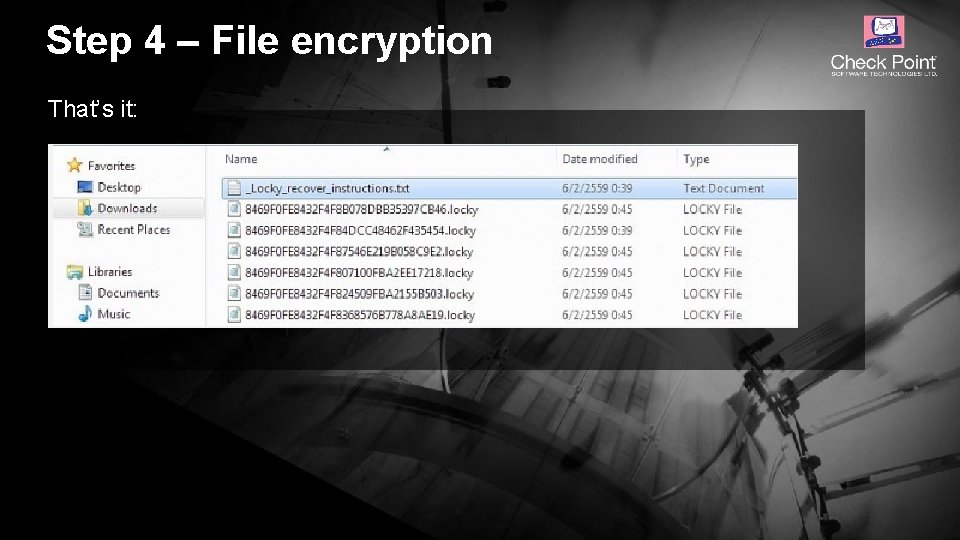
Step 4 – File encryption That’s it: © 2016 Check Point Software Technologies Ltd. 16

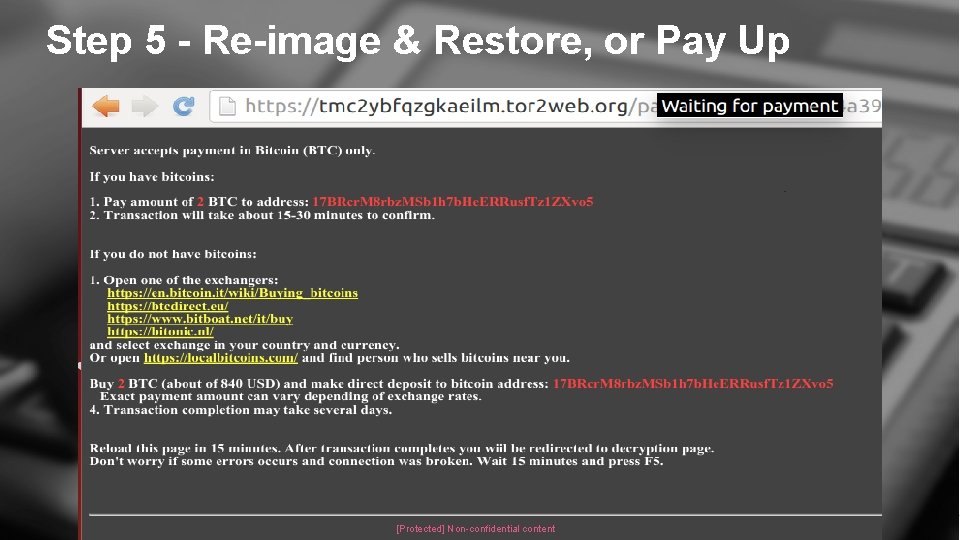
Step 5 - Re-image & Restore, or Pay Up © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 17

« Je n’utilise pas Windows, donc pas de risque…» © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 18

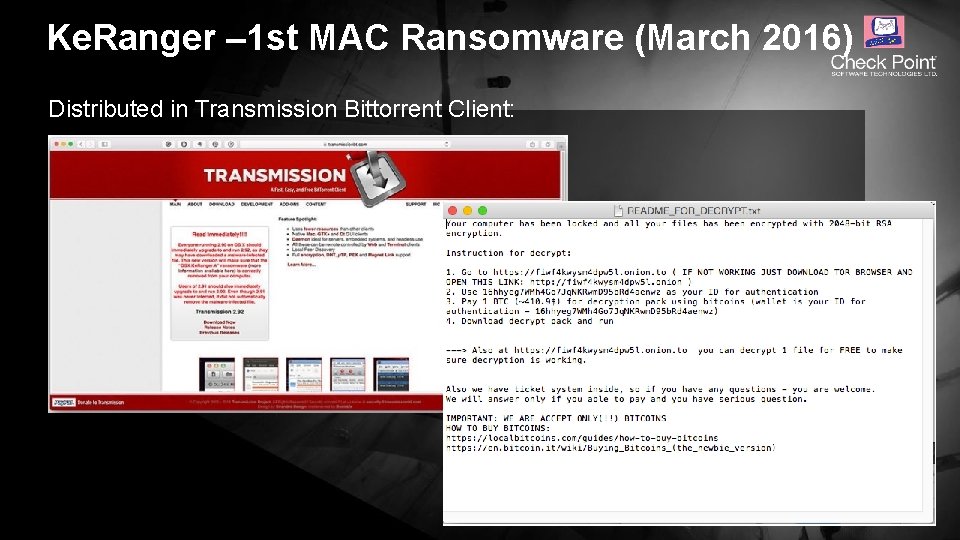
Ke. Ranger – 1 st MAC Ransomware (March 2016) Distributed in Transmission Bittorrent Client: © 2016 Check Point Software Technologies Ltd. 19

« Je n’ai qu’un smartphone » © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 20

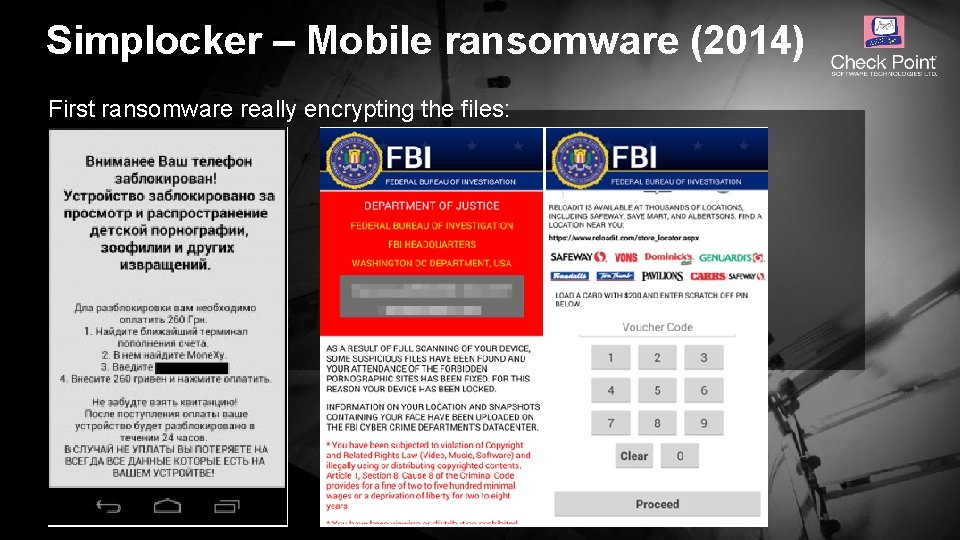
Simplocker – Mobile ransomware (2014) First ransomware really encrypting the files: © 2016 Check Point Software Technologies Ltd. 21

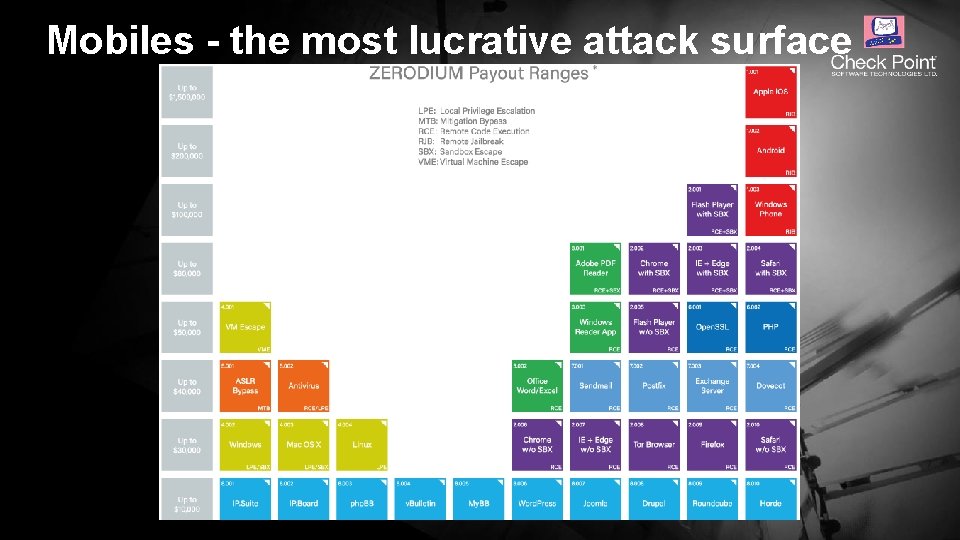
Mobiles - the most lucrative attack surface © 2016 Check Point Software Technologies Ltd. 22

« Je ne me sens pas concerné, cela n’arrive qu’aux autres » © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 23

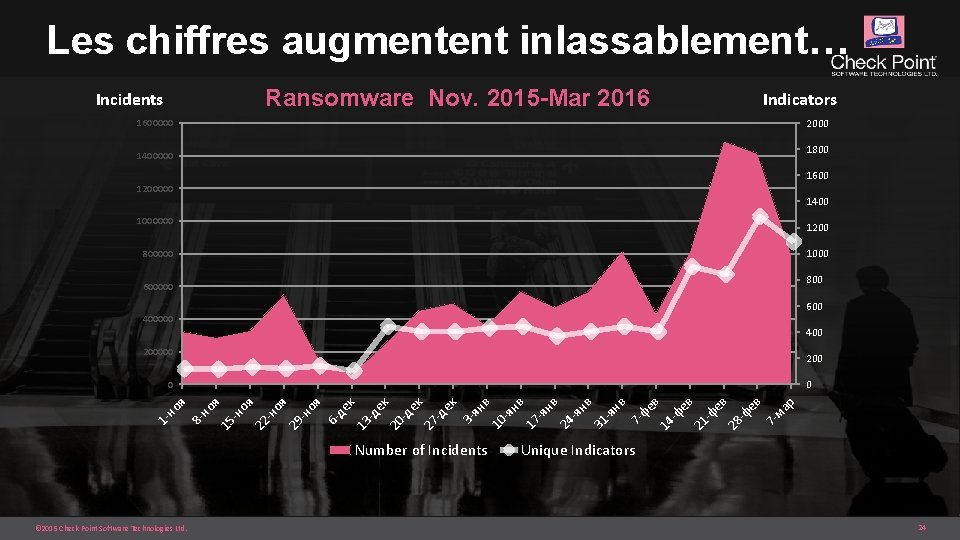
Les chiffres augmentent inlassablement… Ransomware Nov. 2015 -Mar 2016 Incidents Indicators 2000 1600000 1800 1400000 1600 1200000 1400 1000000 1200 1000 800 600000 600 400000 400 200000 200 0 Number of Incidents © 2015 Check Point Software Technologies Ltd. р ма 7 - ев -ф 28 ев -ф ев 21 -ф 14 фе в 7 - нв -я 31 нв -я 24 нв 17 -я нв -я в 10 ян 3 - ек -д 27 ек -д ек 20 -д к 13 де 6 - оя -н 29 оя -н оя 22 -н 15 но я 8 - 1 - но я 0 Unique Indicators 24

La menace grandit… Published March 10, 2016 © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 25
![Dans les pays étrangers 2016 Check Point Software Technologies Ltd Protected Nonconfidential content Dans les pays étrangers… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-26.jpg)
Dans les pays étrangers… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 26
![Mais aussi en France 2016 Check Point Software Technologies Ltd Protected Nonconfidential content Mais aussi en France… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-27.jpg)
Mais aussi en France… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 27

« Est-ce un bon business ? » © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 28
![Impressionnant 2016 Check Point Software Technologies Ltd Protected Nonconfidential content 29 Impressionnant… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 29](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-29.jpg)
Impressionnant… © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 29
![RansomwareasaService Tox 2016 Check Point Software Technologies Ltd Protected Nonconfidential content 30 Ransomware-as-a-Service (Tox) © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 30](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-30.jpg)
Ransomware-as-a-Service (Tox) © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 30

« Comment puis-je m’en prémunir ? » © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 31
![MERCI POUR VOTRE ATT ENTION 2016 Check Point Software Technologies Ltd Protected Nonconfidential MERCI POUR VOTRE ATT ENTION © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential](https://slidetodoc.com/presentation_image_h2/1493dfceb258b930037ed17672b61f9a/image-32.jpg)
MERCI POUR VOTRE ATT ENTION © 2016 Check Point Software Technologies Ltd. [Protected] Non-confidential content 32