alexandrcheckpoint com Check Point Software Technologies 2011 Check

![Удаленный доступ © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. Удаленный доступ © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved.](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-2.jpg)




![Программный клиент для Windows © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All Программный клиент для Windows © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-7.jpg)
![Программный клиент для Mac © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All Программный клиент для Mac © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-11.jpg)

![Программный клиент для Смартфонов © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All Программный клиент для Смартфонов © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-13.jpg)








![VPN клиент по требованию © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All VPN клиент по требованию © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-23.jpg)
![SSL VPN Portal © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights SSL VPN Portal © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-25.jpg)


![Обобщение © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved Обобщение © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-30.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-35.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-36.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-37.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-38.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-39.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-40.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-41.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-42.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-43.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-44.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-45.jpg)
![Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-46.jpg)

- Slides: 47

Как защитить «мобильную» компанию Алексей Андрияшин alexandr@checkpoint. com Консультант по безопасности Check Point Software Technologies © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved
![Удаленный доступ 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Удаленный доступ © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved.](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-2.jpg)
Удаленный доступ © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 2 2

Ноутбуки принесли свободу … теперь еще проще © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 3 3



План 1 Клиент Windows 2 Клиент MAC 3 Клиент для смартфонов 4 Клиент по требованию 5 SSL VPN портал 6 Обобщение © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 6 6
![Программный клиент для Windows 2011 Check Point Software Technologies Ltd PROTECTED All Программный клиент для Windows © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-7.jpg)
Программный клиент для Windows © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved

Remote Access § CP Mobile клиент E 75. 20 для Windows: – «Легкий» VPN клиент с продвинутым VPN функционалом – Не требует перезагрузки после инсталляции – Compliance Checks – Поддержка всех Microsoft OS (включая 64 bits) © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 8 8

Remote Access + Desktop Firewall § Endpoint Security VPN E 75. 20 – Тот же VPN движок как и CP Mobile для Windows – Firewall и Compliance checks – Desktop firewall управляется со Смартцентра – Замена бывшему Secure. Client в большинстве случаев © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 9 9

Remote Access + Total Security Suite § Check Point Endpoint Security E 80. 20 – FW, ME, Webcheck, FW, AM – Отдельный сервер управления для всех блейдов (FW, Compliance, и т. д. ) за исключением VPN – VPN политики устанавливаются на шлюзе – E 80 может содержать как бывший Secure. Client или Endpoint Сonnect движок © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 10 10
![Программный клиент для Mac 2011 Check Point Software Technologies Ltd PROTECTED All Программный клиент для Mac © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-11.jpg)
Программный клиент для Mac © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved

Remote Access + Desktop Firewall § Secure. Client для Mac R 56 HFA 2 – Содержит FW (без проверок соответствия) – Поддержка OS X Snow Leopard 32 bits – Поддержка OS X Lion (EA) – Будет заменен Endpoint Security VPN в 2012 © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 12 12
![Программный клиент для Смартфонов 2011 Check Point Software Technologies Ltd PROTECTED All Программный клиент для Смартфонов © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-13.jpg)
Программный клиент для Смартфонов © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved





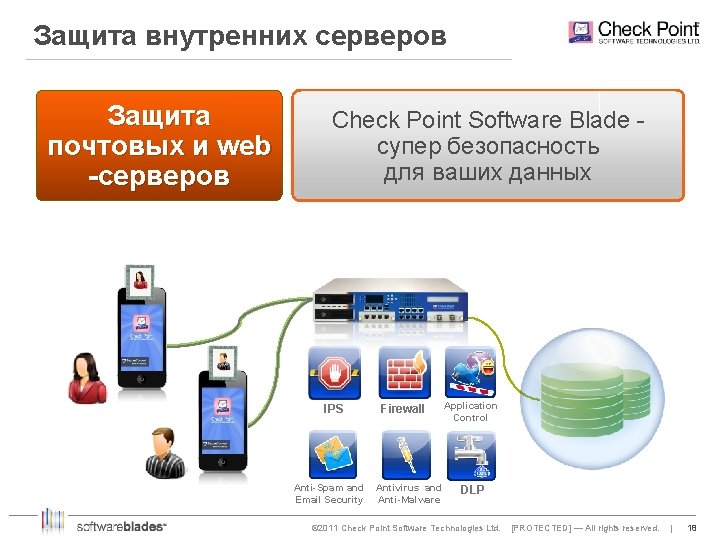
Защита внутренних серверов Защита почтовых и web -серверов Check Point Software Blade супер безопасность для ваших данных IPS Anti-Spam and Email Security Firewall Antivirus and Anti-Malware Application Control DLP © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 18 18




![VPN клиент по требованию 2011 Check Point Software Technologies Ltd PROTECTED All VPN клиент по требованию © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-23.jpg)
VPN клиент по требованию © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved

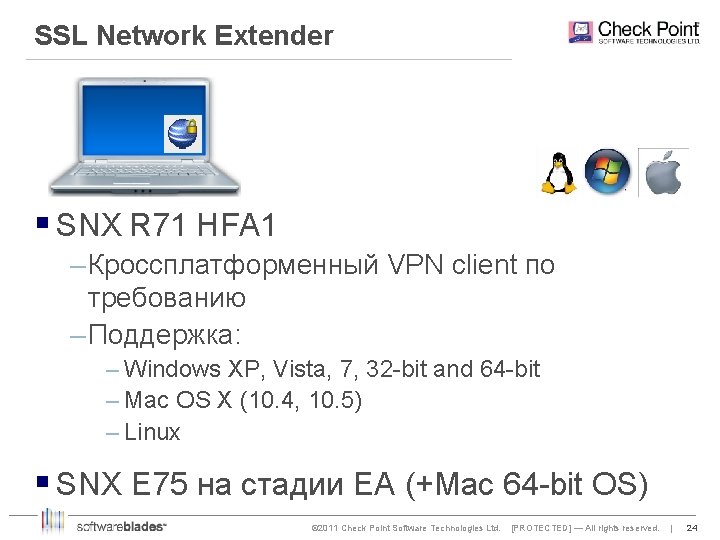
SSL Network Extender § SNX R 71 HFA 1 – Кроссплатформенный VPN client по требованию – Поддержка: – Windows XP, Vista, 7, 32 -bit and 64 -bit – Mac OS X (10. 4, 10. 5) – Linux § SNX E 75 на стадии EA (+Mac 64 -bit OS) © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 24 24
![SSL VPN Portal 2011 Check Point Software Technologies Ltd PROTECTED All rights SSL VPN Portal © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-25.jpg)
SSL VPN Portal © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved


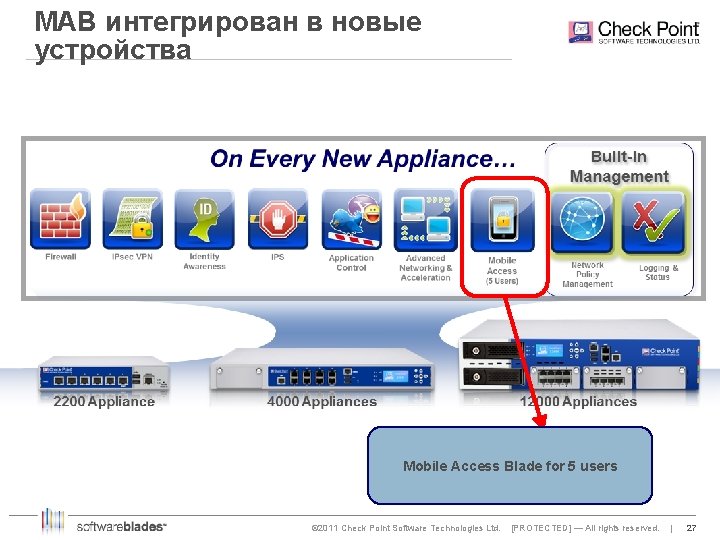
MAB интегрирован в новые устройства Mobile Access Blade for 5 users © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 27 27

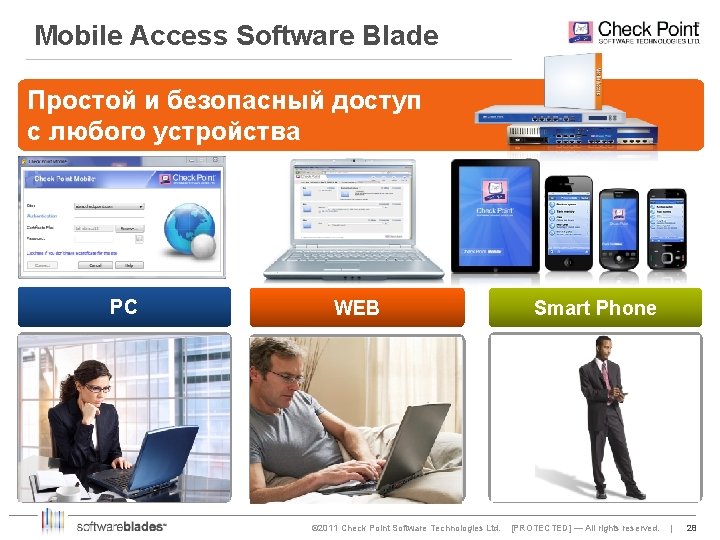
Mobile Access Software Blade Простой и безопасный доступ с любого устройства PC § Check Point Mobile for Windows § Windows 7 64 -bit support § On-demand light VPN client (Windows, Mac and Linux) WEB § SSL VPN user portal § Endpoint Compliance § Secure Workspace © 2011 Check Point Software Technologies Ltd. Smart Phone § Check Point Mobile for Smart Phones § i. Phone / i. Pad / Android § Secure Microsoft Exchange (Active Sync) [PROTECTED] — All rights reserved. | 28 28

![Обобщение 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Обобщение © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-30.jpg)
Обобщение © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved

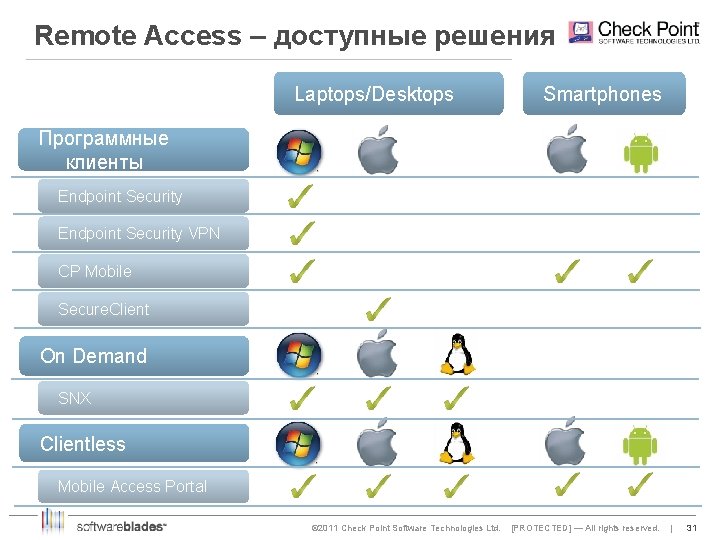
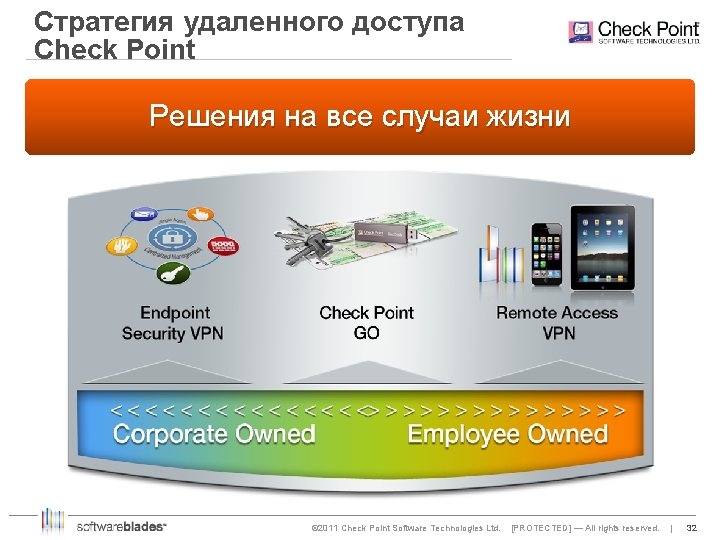
Remote Access – доступные решения Laptops/Desktops Smartphones Программные клиенты Endpoint Security VPN CP Mobile Secure. Client On Demand SNX Clientless Mobile Access Portal © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 31 31

Стратегия удаленного доступа Check Point Решения на все случаи жизни © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 32 32

Скачайте Check Mobile бесплатно § Доступно в App. Store § Демонстрационный режим § Поддержка i. Phone и i. Pad © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 33 33

Скачайте Check Mobile бесплатно § Доступно в App. Store § Демонстрационный режим § Поддержка i. Phone и i. Pad © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 34 34
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-35.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 35 35
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-36.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 36 36
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-37.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 37 37
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-38.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 38 38
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-39.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 39 39
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-40.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 40 40
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-41.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 41 41
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-42.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 42 42
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-43.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 43 43
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-44.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 44 44
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-45.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 45 45
![Demo 2011 Check Point Software Technologies Ltd PROTECTED All rights reserved Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. |](https://slidetodoc.com/presentation_image_h2/c9748c764acd10229d5c750ce19c99ee/image-46.jpg)
Demo © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved. | 46 46

Спасибо! Алексей Андрияшин alexandr@checkpoint. com Консультант по безопасности Check Point Software Technologies © 2011 Check Point Software Technologies Ltd. [PROTECTED] — All rights reserved