Computer Networks Ivan Marsic Rutgers University Chapter 7












- Slides: 52

Computer Networks Ivan Marsic Rutgers University Chapter 7 – Network Security Chapter 8 – Network Monitoring Chapter 9 – Internet Protocols APPENDIX: Probability Refresher

Network Security Chapter 7

Topic: Secure Communication · Network Security Problem · Symmetric and Public-Key Cryptosystems · Cryptographic Algorithms · Authentication

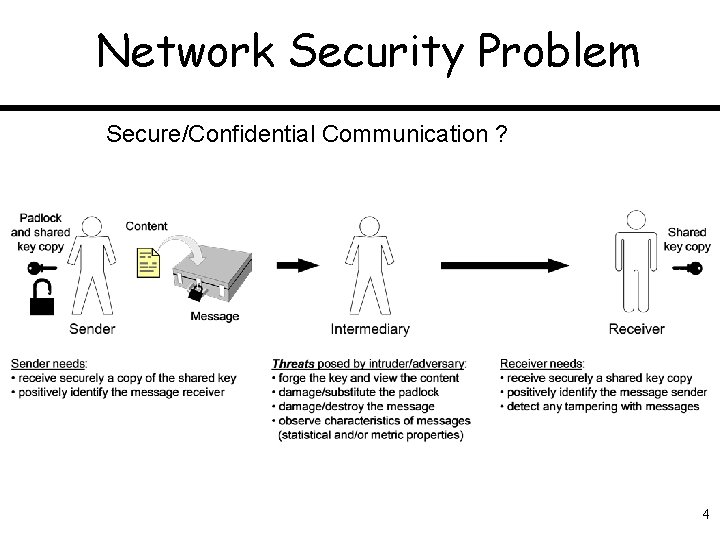
Network Security Problem Secure/Confidential Communication ? 4

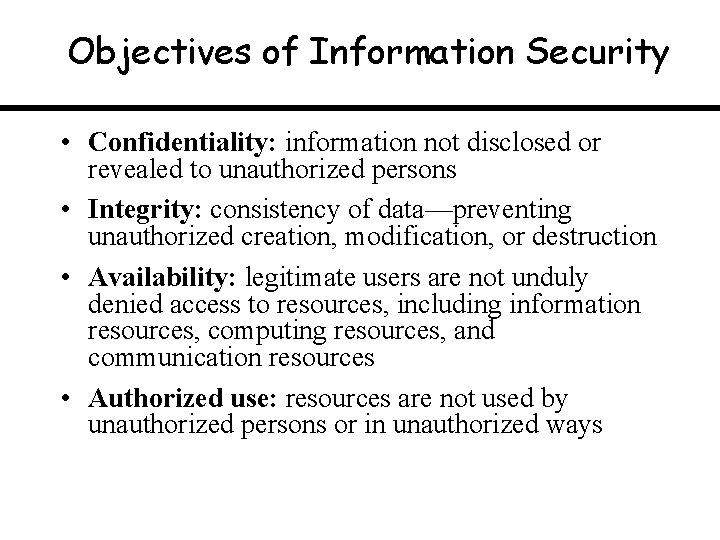
Objectives of Information Security • Confidentiality: information not disclosed or revealed to unauthorized persons • Integrity: consistency of data—preventing unauthorized creation, modification, or destruction • Availability: legitimate users are not unduly denied access to resources, including information resources, computing resources, and communication resources • Authorized use: resources are not used by unauthorized persons or in unauthorized ways

Message Encoding and Decoding • Encoding takes a message M and produces a coded form f(M) • Decoding the message requires an inverse function , such that = M.

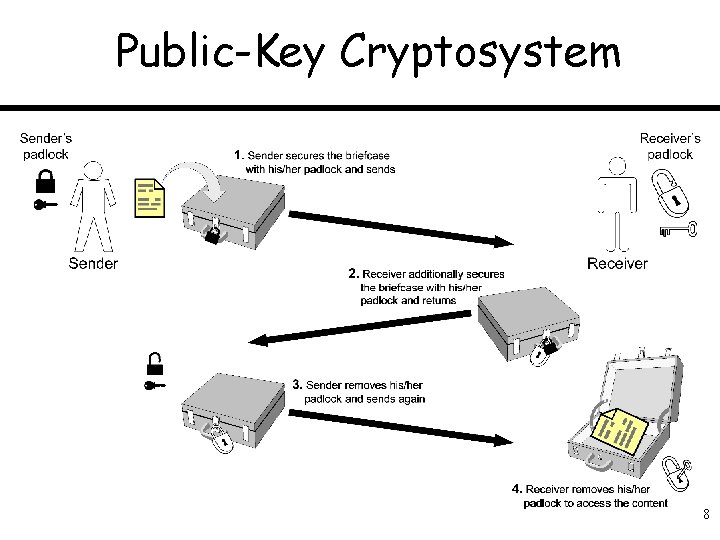
Two Basic Types of Cryptosystems • Symmetric systems: both parties use the same (secret) key in encryption and decryption transformations • Public-key systems (aka asymmetric systems): the parties use two related keys, one of which is secret and the other can be publicly disclosed

Public-Key Cryptosystem 8

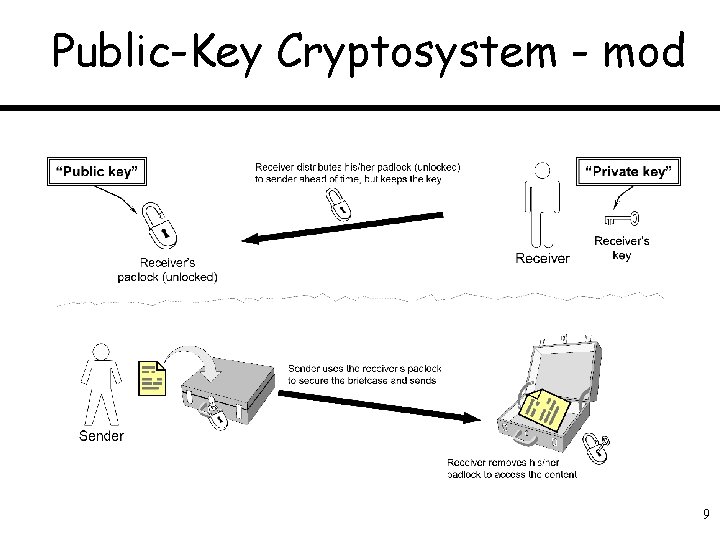
Public-Key Cryptosystem - mod 9

Public-Key Cryptography In RSA, receiver does the following: • Randomly select two large prime numbers p and q, which always must be kept secret. • Select an integer number E, known as the public exponent, such that (p 1) and E have no common divisors, and (q 1) and E have no common divisors. • Determine the product n = p q, known as public modulus. • Determine the private exponent, D, such that (E D 1) is exactly divisible by both (p 1) and (q 1). In other words, given E, we choose D such that the integer remainder when E D is divided by (p 1) (q 1) is 1. • Release publicly the public key, which is the pair of numbers n and E, K = (n, E). Keep secret the private key, K = (n, D).

Example: send the plaintext “hello world” • receiver chooses p = 5 and q = 7 • receiver chooses E = 5, because 5 and (5 1) (7 1) have no common factors. Also, n = p q = 35 • receiver chooses D = 29, because i. e. , they are exactly divisible. • receiver’s public key is K = (n, E) = (35, 5), which is made public. The private key K = (n, D) = (35, 29) is kept secret.

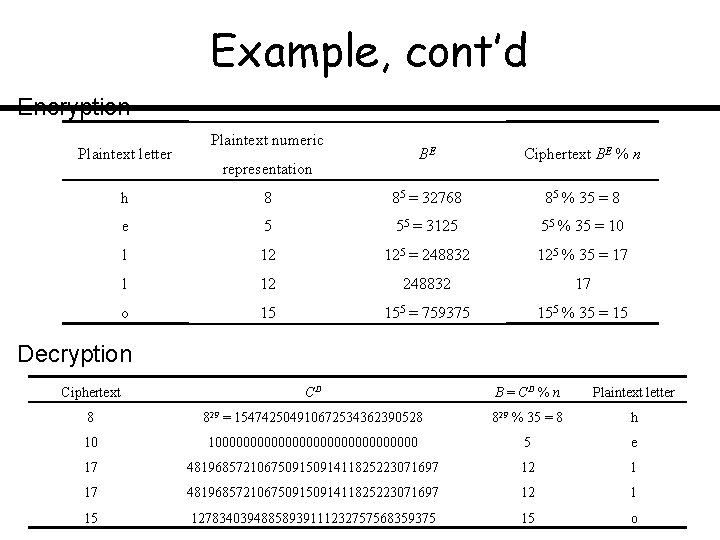
Example, cont’d Encryption Plaintext letter Plaintext numeric representation BE Ciphertext BE % n h 8 85 = 32768 85 % 35 = 8 e 5 55 = 3125 55 % 35 = 10 l 12 125 = 248832 125 % 35 = 17 l 12 248832 17 o 15 155 = 759375 155 % 35 = 15 Decryption Ciphertext CD B = CD % n Plaintext letter 8 829 = 154742504910672534362390528 829 % 35 = 8 h 10 1000000000000000 5 e 17 481968572106750915091411825223071697 12 l 15 12783403948858939111232757568359375 15 o

Example, cont’d • While the adversary knows n and E, he or she does not know p and q, so they cannot work out (p 1) (q 1) and thereby find D.

Topic: Authentication · Network Security Problem · Symmetric and Public-Key Cryptosystems · Cryptographic Algorithms · Authentication

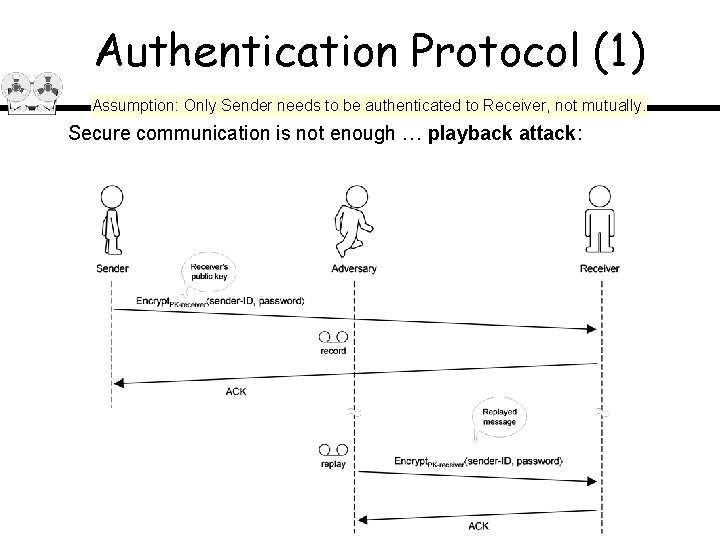
Authentication Protocol (1) Assumption: Only Sender needs to be authenticated to Receiver, not mutually. Secure communication is not enough … playback attack:

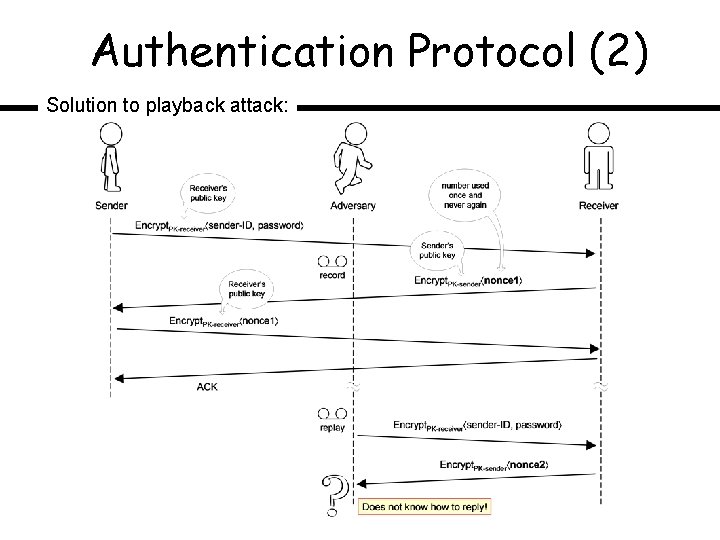
Authentication Protocol (2) Solution to playback attack:

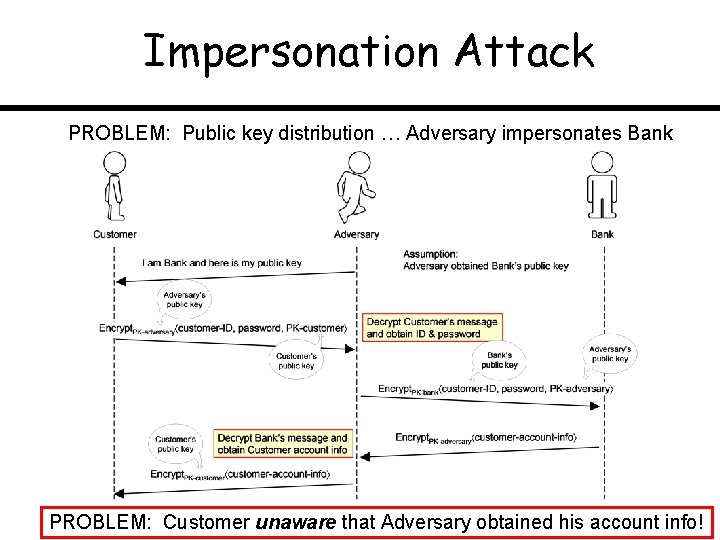
Impersonation Attack PROBLEM: Public key distribution … Adversary impersonates Bank PROBLEM: Customer unaware that Adversary obtained his account info!

Network Monitoring Chapter 8

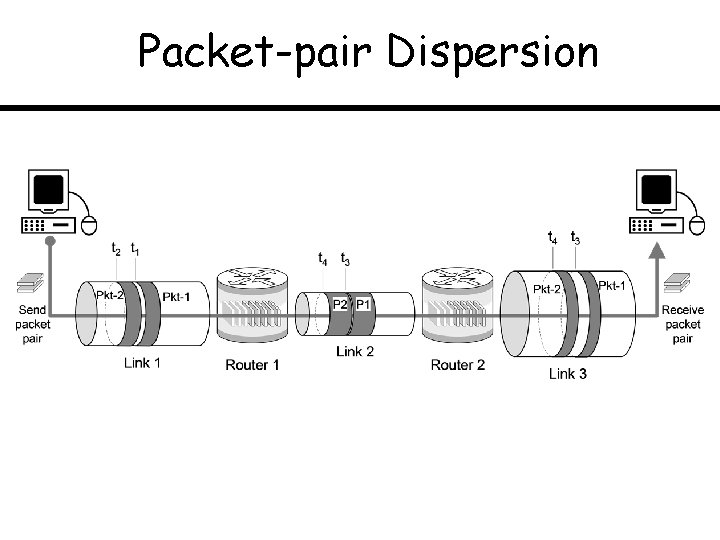
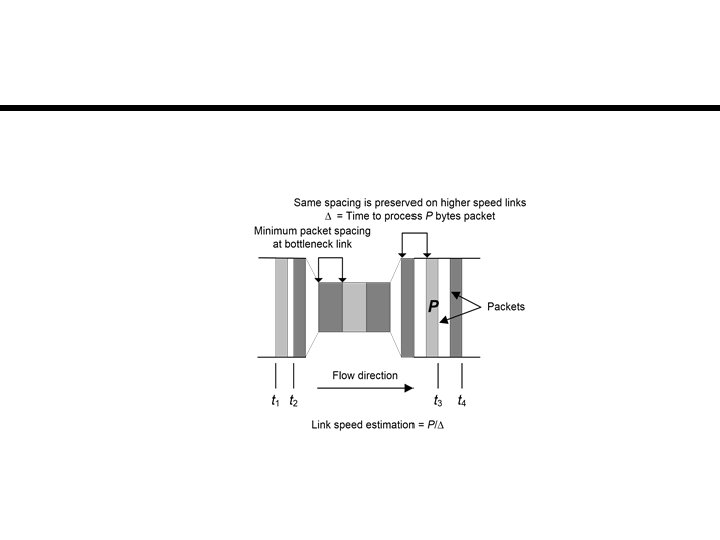
Packet-pair Dispersion


Internet Protocols Chapter 9

The Internet Reference Model Visit http: //en. wikipedia. org/wiki/Internet_reference_model for more details on the Internet reference model http: //en. wikipedia. org/wiki/OSI_model

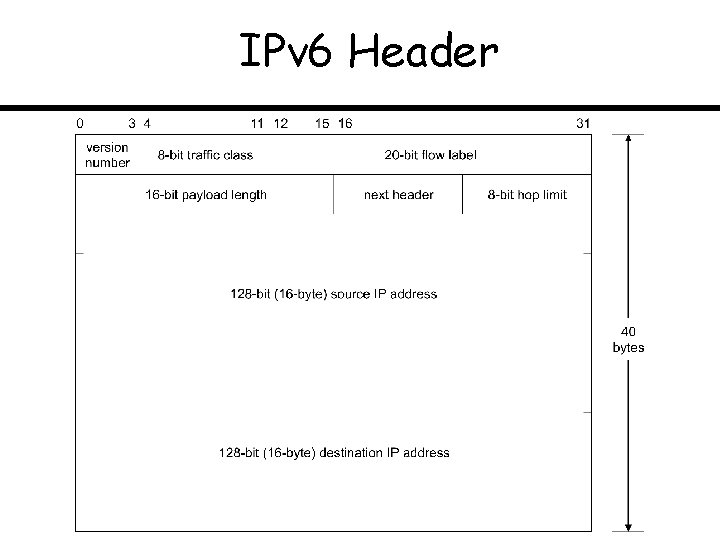
IPv 6 Header

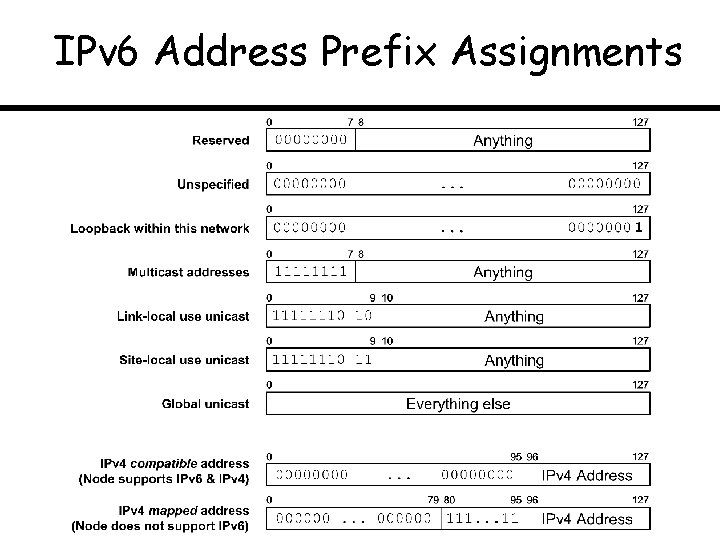
IPv 6 Address Prefix Assignments

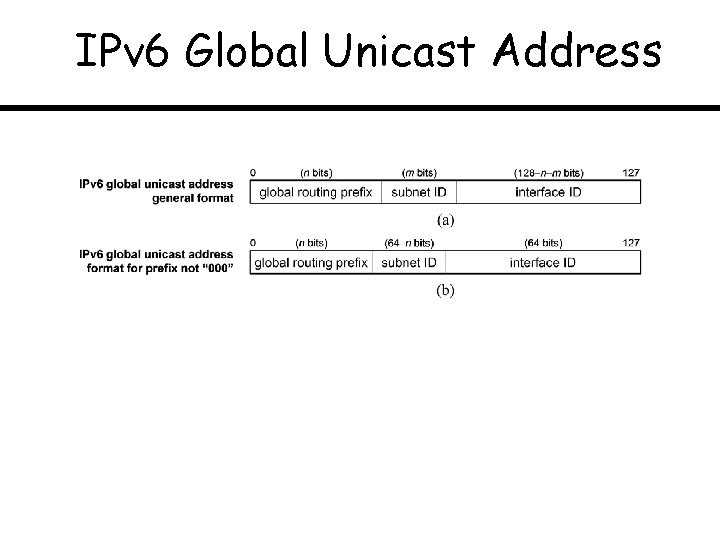
IPv 6 Global Unicast Address

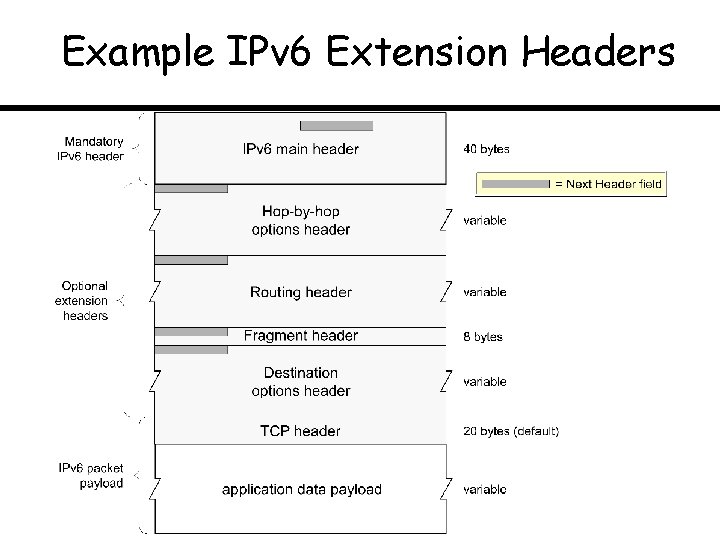
Example IPv 6 Extension Headers

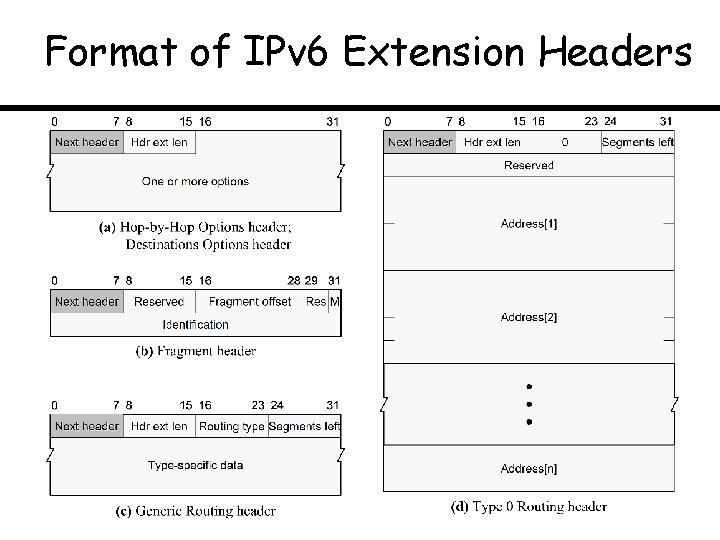
Format of IPv 6 Extension Headers

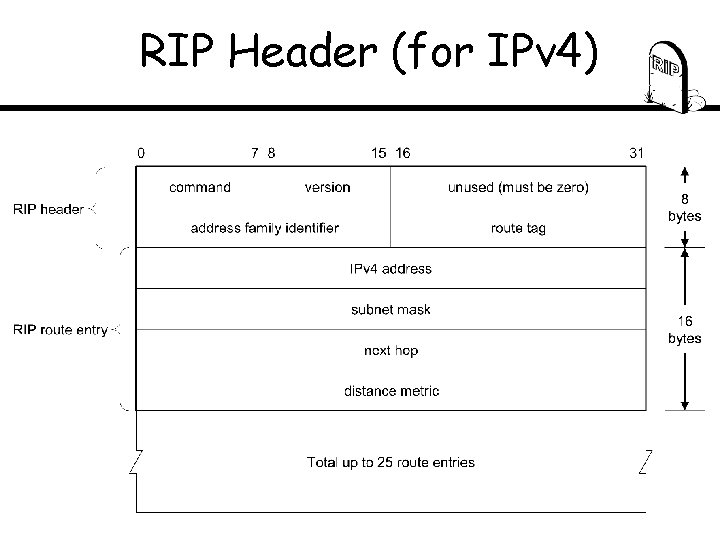
RIP Header (for IPv 4)

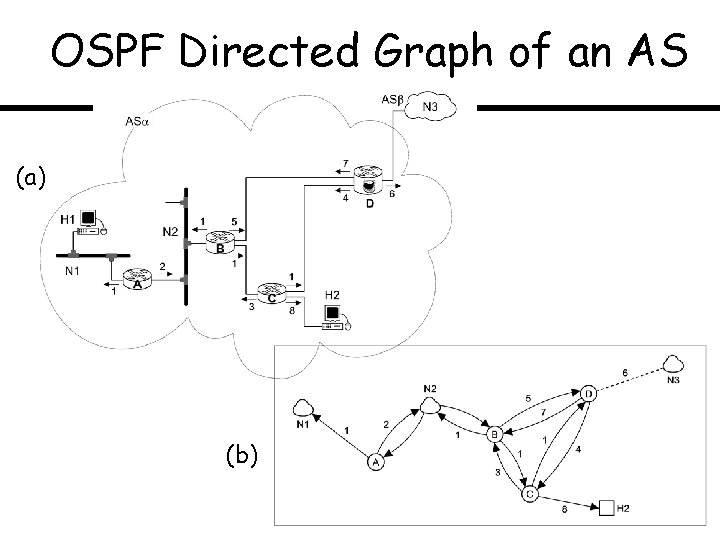
OSPF Directed Graph of an AS (a) (b)

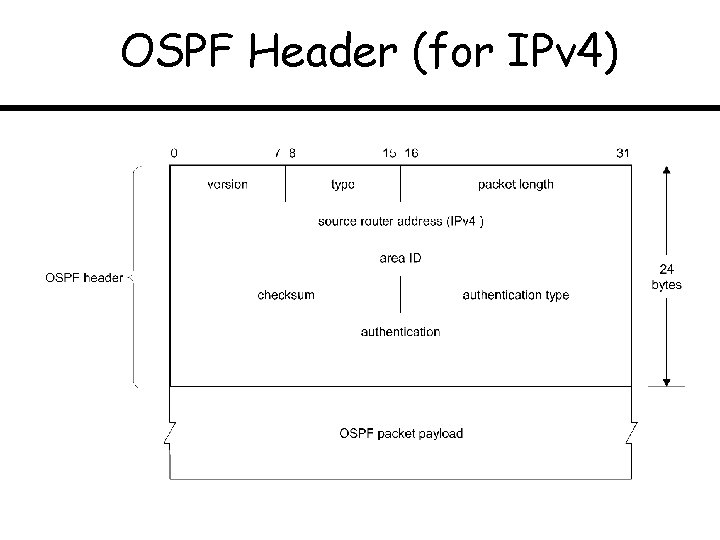
OSPF Header (for IPv 4)

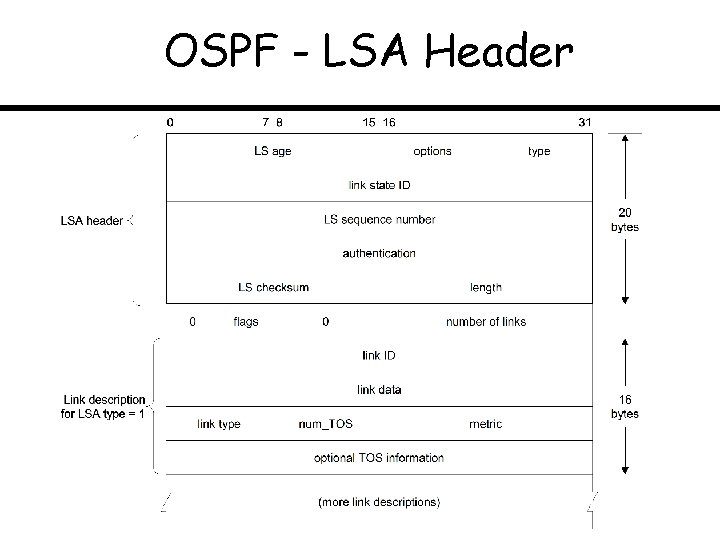
OSPF - LSA Header

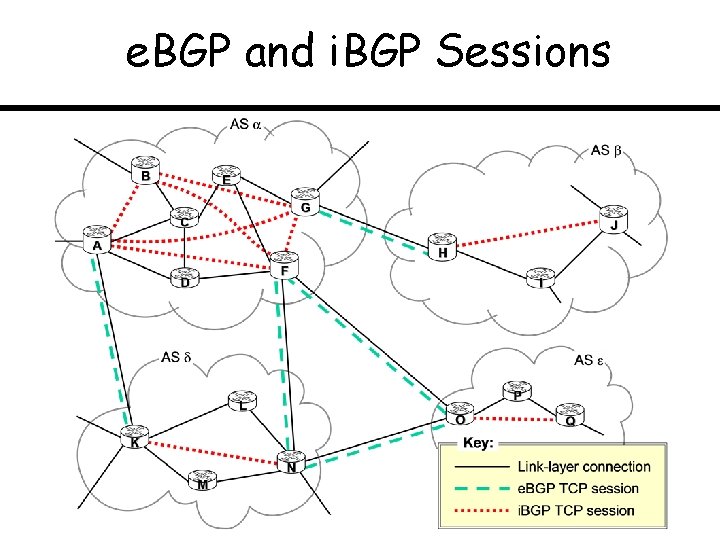
e. BGP and i. BGP Sessions

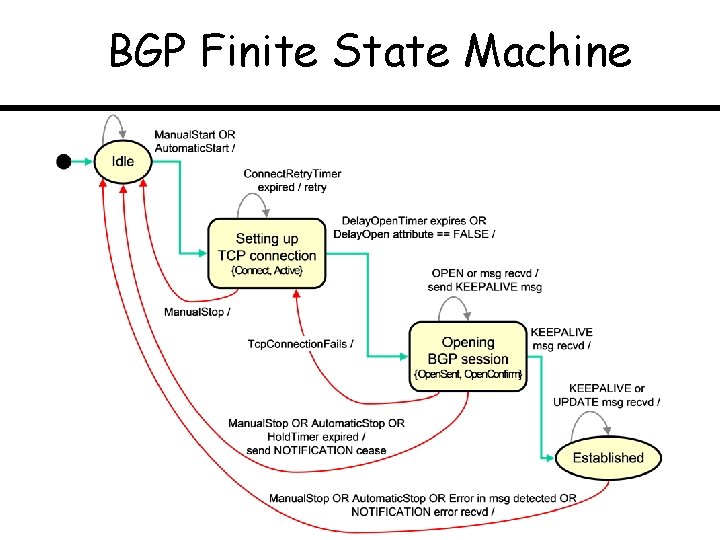
BGP Finite State Machine

Detail from Figure 1 -49:

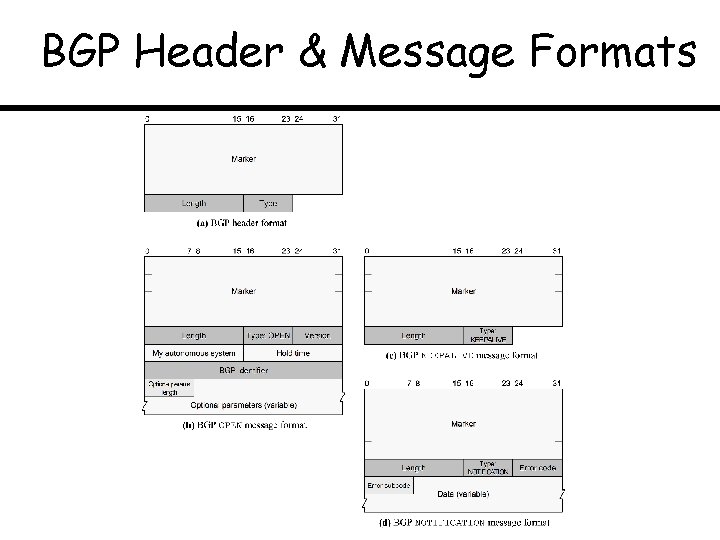
BGP Header & Message Formats

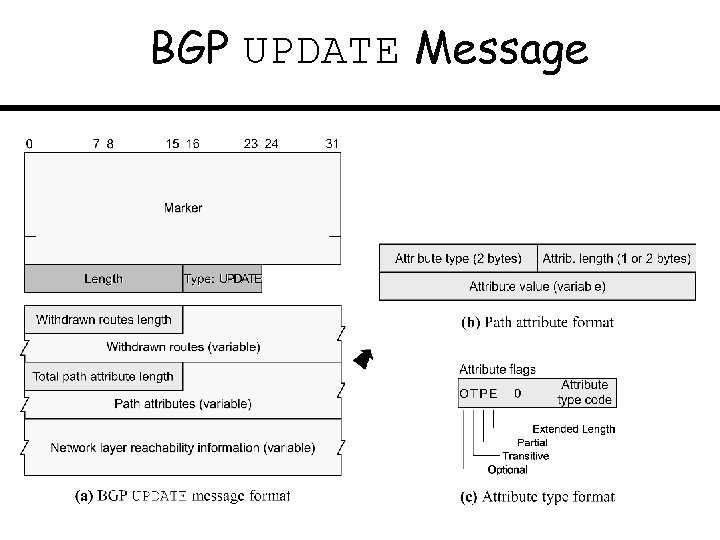
BGP UPDATE Message

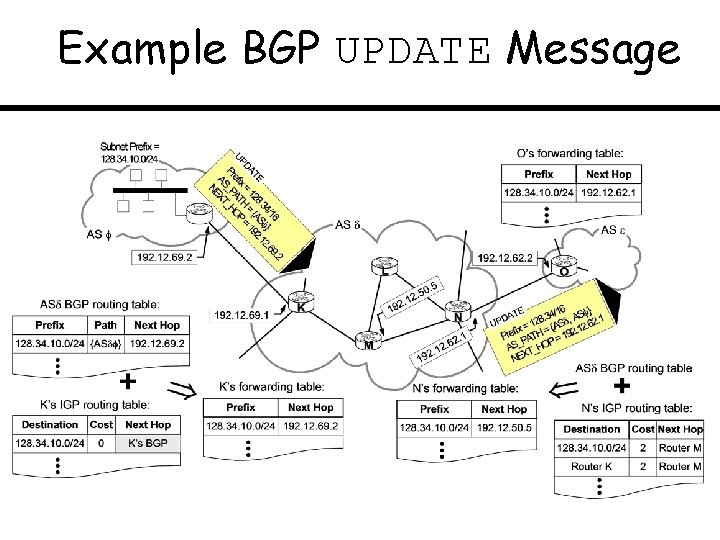
Example BGP UPDATE Message

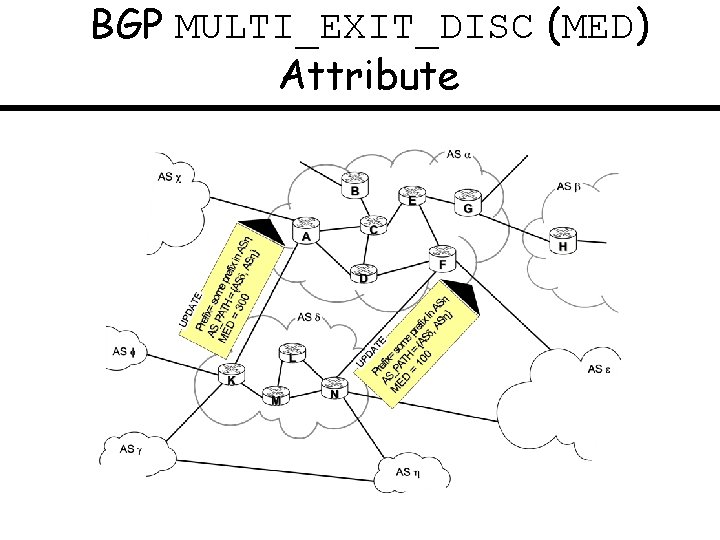
BGP MULTI_EXIT_DISC (MED) Attribute

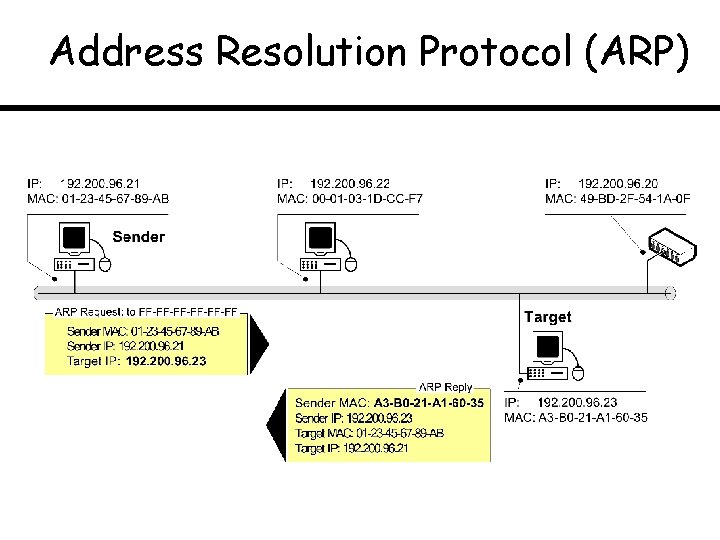
Address Resolution Protocol (ARP) Need for multiple addresses, hierarchical vs. non-hierarchical

Address Resolution Protocol (ARP)

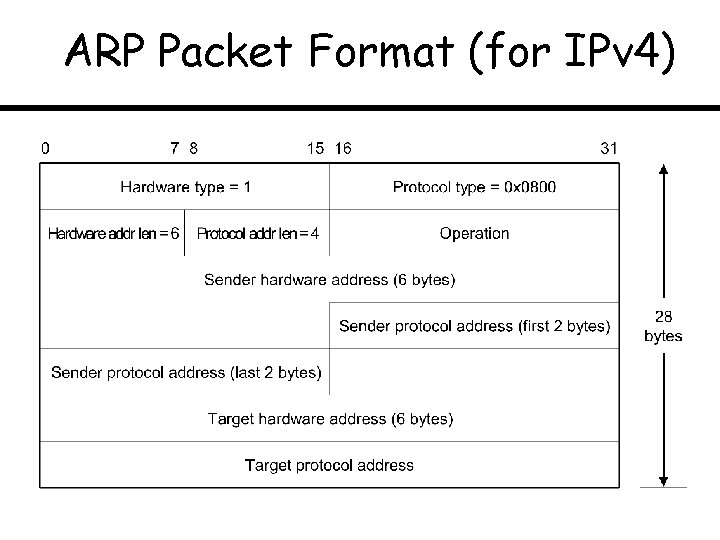
ARP Packet Format (for IPv 4)

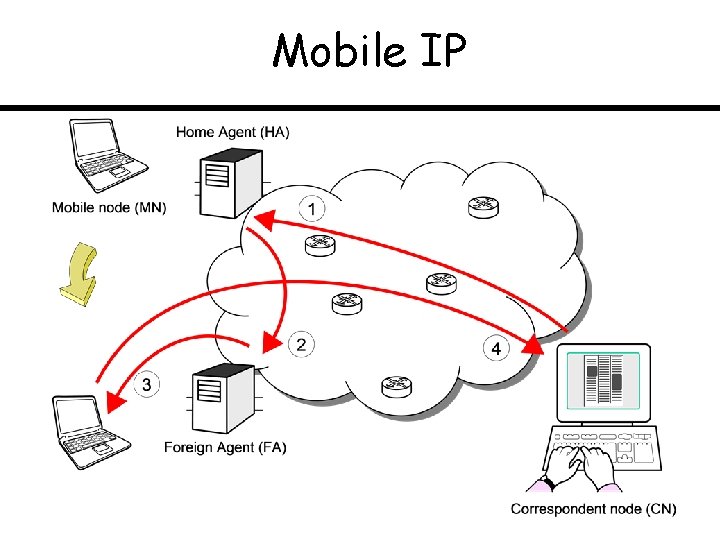
Mobile IP

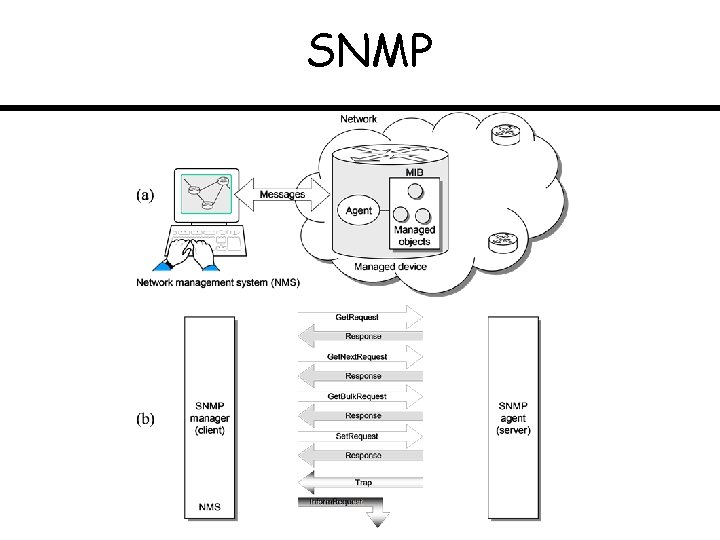
SNMP

Probability Refresher Appendix

Jar with Black & White Balls

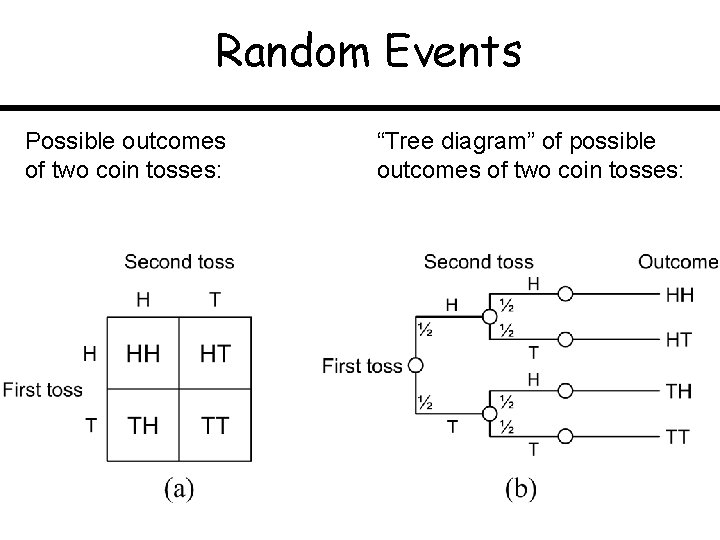
Random Events Possible outcomes of two coin tosses: “Tree diagram” of possible outcomes of two coin tosses:

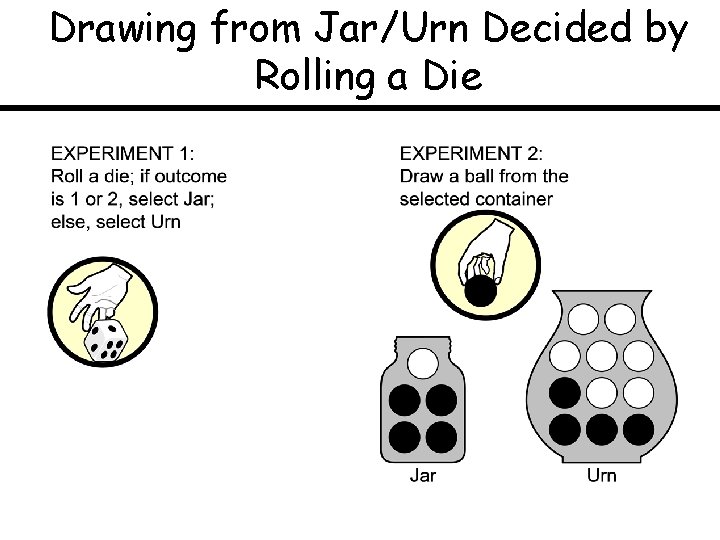
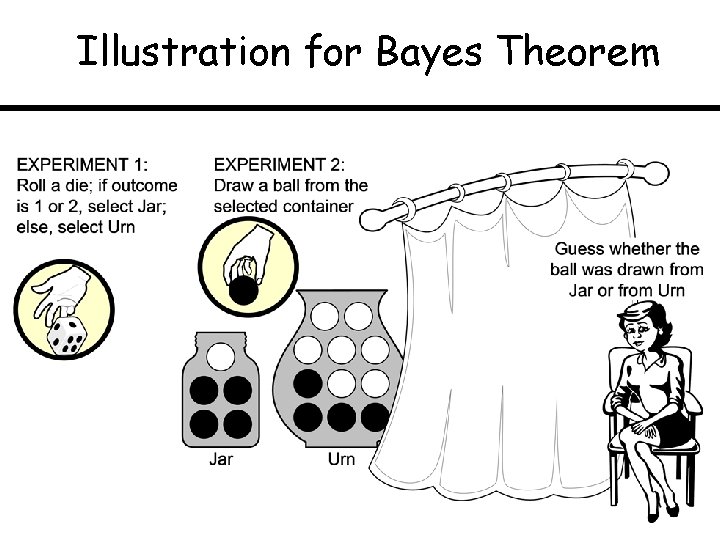
Drawing from Jar/Urn Decided by Rolling a Die

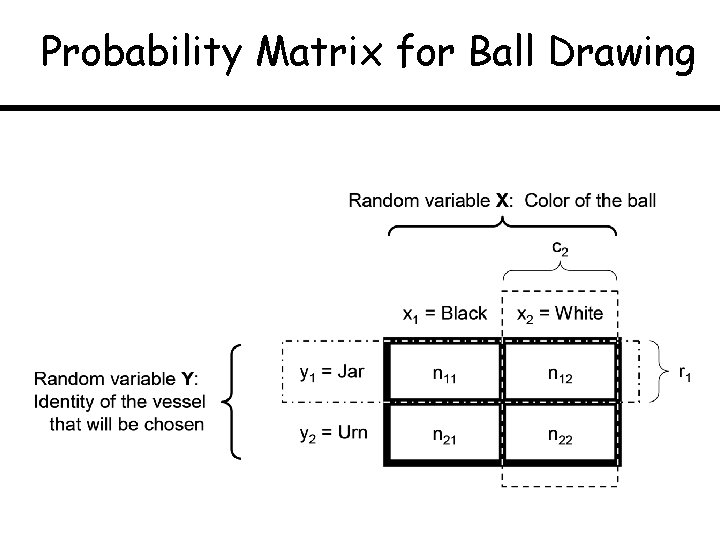
Probability Matrix for Ball Drawing

Illustration for Bayes Theorem

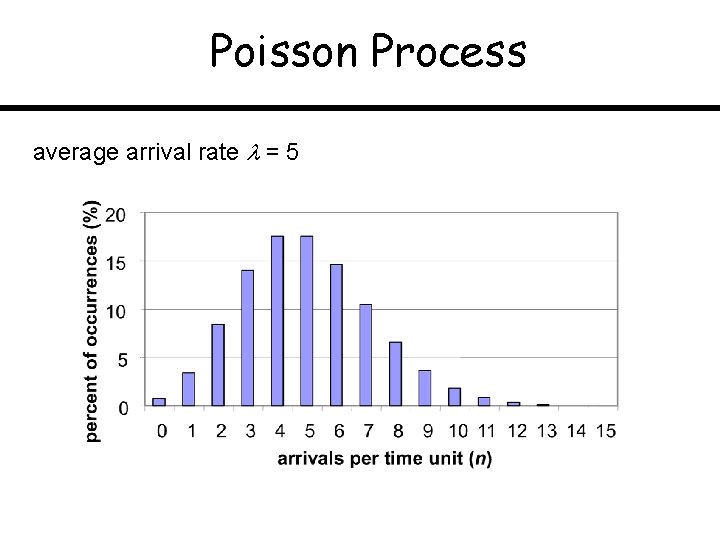
Poisson Process average arrival rate = 5

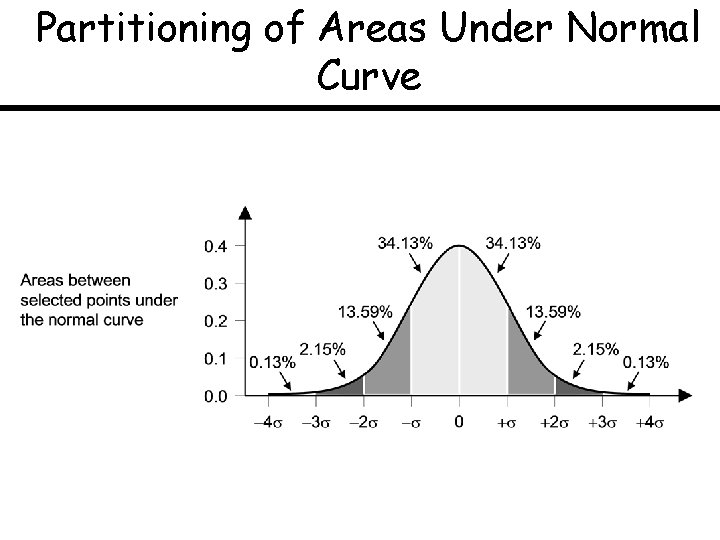
Partitioning of Areas Under Normal Curve

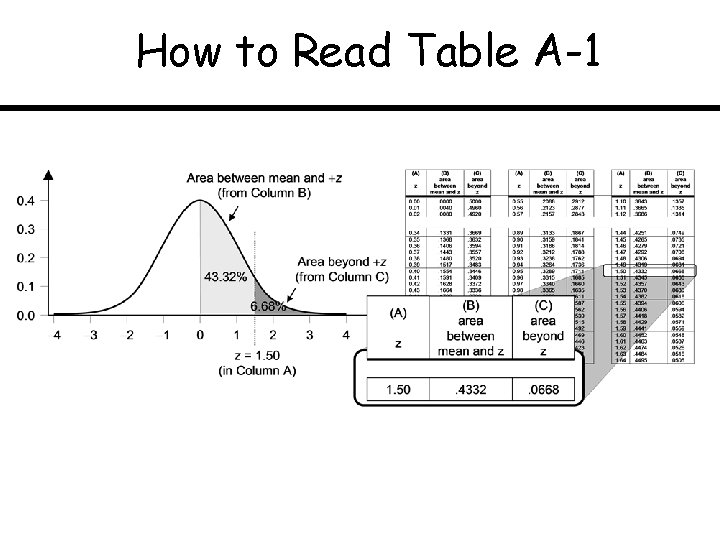
How to Read Table A-1