Communication Theory of Secrecy Systems On a paper
















































- Slides: 57

Communication Theory of Secrecy Systems On a paper by Shannon (and the industry it didn’t spawn) Gilad Tsur Yossi Oren December 2005

What you’ll see today Shannon – his life and work l Cryptography before Shannon l Definition of a cryptosystem l Theoretical and practical security l Product ciphers and combined cryptosystems l Closing thoughts l

Shannon – his life and work

Claude E. Shannon (1916 -2001)

Claude E. Shannon (1916 -2001) l Important facts: M. Sc. Thesis founded an industry l Ph. D. finished in 1. 5 years l Married a computer in 1949 l Wrote scientific papers on a variety of topics, including juggling l

Shannon’s Information Theory Paper “Mathematical Theory of Communication”, published in 1948 l Main claim: l All sources of data have a rate l All channels have a capacity l If the capacity is greater than the rate, transmission with no errors is possible l l Introduced concept of entropy of a random variable/process

From http//: www. cqrsoft. com/history/scytale. htm Cryptography before Shannon

Themes in cryptography • Seals were used as authentication means for signing contracts, for royal decrees and for other documents. • Passwords were used by military and other organizations to identify members. From http//: images. encarta. msn. com/xrefme dia/sharemed/targets/images/pho/t 025/ T 025102 A. jpg • Codes are semantic while ciphers are syntactic. • All these methods (in the case of seals, as rubber stamps) are also in use today.

Ancient Ciphers I א ב ג ד ה ו ז ח ט י כ ל מ נ ס ע פ צ ק רש ת תש ר ק צ פ ע ס נ מ ל כ י ט ח ז ו ה ד ג ב א • Atbash cipher used in old testament “ “בבל = ששך • Of course, anyone who’d ever heard of this cipher could easily crack it. • This is also true for another famous cipher, the Caesar cipher. A BC D E F … … X Y Z A B C

Ancient Ciphers II • The Caesar cipher is just a specific case of what are generally known as Shift Ciphers. • A Shift cipher is one where the code is simply a rotation of the alphabet with K steps, where the number K can be considered the key. Easier for us in CS – think of it as a constant added modulo the size of the alphabet. • Obviously, finding the key for such a code is not a lengthy process.

Ancient Ciphers III So what were these ciphers good for? • Text took an active effort to understand (This was used with ROT-13 on Usenet). • Probably the real reason – security through obscurity. • The concept of cryptography was not that well known, and codes such as Atbash were simply assumed not to be known by people you didn’t want reading them.

Ancient Ciphers IV • Both Atbash and Shift ciphers are specific cases of a more general type of ciphers used in the ancient world: Monoalphabetic Substitution Ciphers. • As these ciphers were used by people who wanted to remember them, keyword and keyphrase ciphers were often used. • The keyword could be changed daily to make it harder to decrypt. • Some of these ciphers didn’t use a 1 -1 correspondence, trusting the redundancy of language or allowing multiple representations.

Ancient Ciphers V http//: plus. maths. org/issue 34/features/ekert/ • Not all ancient ciphers used substitution methods. • The earliest known cryptographic device (to the best of our knowledge) is the Spartan scytale. • Using this device the letters of the message weren’t changed, but their order was.

Ancient Ciphers VI • The scytale was a device assisting in the creation of a Transposition Cipher. • Perhaps the most notable example of a transposition cipher is the column transposition. • Other geometrical transposition ciphers abound, mostly route ciphers. • Transposition ciphers based on a local permutation are also common, but offer a less apparently convenient way of writing quickly.

Ancient Ciphers VII • We have written records of frequency analysis dating to the 9 th century. From http//: en. wikipedia. org/wiki/Caesar_cipher http//: plus. maths. org/issue 34/features/ekert/ • Using multiple options to substitute frequent letters could make frequency analysis much harder.

Cryptography during the dark ages (‘till around 14 th century) • Cryptography didn’t advance in Europe much during the dark ages. • Some religious and mystical sects used cryptographic techniques to encode their writings, often substitution ciphers to an arcane alphabet. • However, the church considered most people using cryptography as heretics, sorcerers or witches, and was in the habit of burning them. • Coupled with low levels of literacy, cryptography was only studied outside of Europe. • While texts (such as the cryptanalytic one mentioned above) appeared, we are unaware of major advances.

Codes and ciphers in the renaissance • In Italy, and later all over Europe, cryptography returns to fashion. • Different city-states and countries begin to employ professional cryptanalysts for encoding and decoding mail. • The most common codes are Polyalphabetic Substitution Ciphers. • Many devices are made to aid encryption and decryption.

Polyalphabetic substitution ciphers • These ciphers can simply be considered as a list of shift ciphers or monoalphabetic substitution ciphers to be used consecutively. • The use of some of these ciphers was aided by a cipher disk. • Other such ciphers used tables to assist encryption and decryption. • Notably, some in of these cipher were polygraphic – each encoded symbol represented a combination of plaintext symbols.

Cryptanalysis of polyalphabetic substitution ciphers • The major classic techniques used for this process involve two steps: 1. Discover the length of cycle. 2. Use monoalphabetic cryptanalysis techniques for each alphabet (+ information gained from previous alphabets). • Step 1 can be done systematically (Brute force approach) but this may be a very hard process. • A shortcut that often helps (and is published in the 19 th century, ‘though probably known before) is finding repeating sequences in the text.

Cryptography in the 19 th and 20 th Centauries I • WWI sees the full use of cryptography in the battle field. • Advances in radio and telegraph allow military units to communicate better than ever before. This means easy to use, generic ciphers are required. Mechanized cipher machines offer this option.

Cryptography in the 19 th and 20 th Centauries II • WWII is famous for being a scientific war in general, and for cryptography in particular. • German Enigma cracked by British, Japanese “Purple” by the US. • Enigma, in fact, a polyalphabetic cipher system with around 20, 000 alphabets.

Definitions of a Cryptosystem

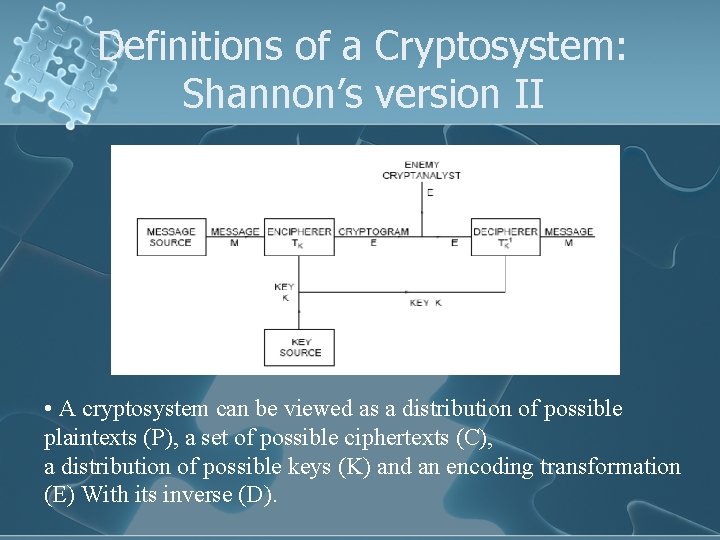
Definitions of a Cryptosystem: Shannon’s version II • A cryptosystem can be viewed as a distribution of possible plaintexts (P), a set of possible ciphertexts (C), a distribution of possible keys (K) and an encoding transformation (E) With its inverse (D).

Definitions of a Cryptosystem: modern variations • Many things have changed in our thinking about cryptography. • Different functions: Not only trying to transmit secret information. • Different settings for “Alice” and “Bob” – we now have public key cryptosystems and extensive use of randomness. • Different settings for “Eve” – we now have a variety of attacks such as known plain text, chosen ciphertext, chosen plain text and side channel attacks.

Shannon’s 1948 Paper Published one year after his monumental “information theory” paper l Inspired by Von-Neumann’s paper on game theory l “transformed cryptography from art to science” l

Main Contributions l l Notions of theoretical security and practical security Observation that the secret is all in the key, not in the algorithm – “the enemy knows the system” (also attributed to Auguste Kerckhoffs) Product ciphers and mixing transformations – inspiration for LUCIFER and later DES Proof that Vernam’s cipher (one-time pad) was theoretically secure

Theoretical Security and Practical Security

Theoretical Security and Practical Security l l l Theoretically secure cryptosystems cannot be broken – even by an all-powerful adversary Practically secure cryptosystems “require a large amount of work to solve” Bad news: l l l The only theoretically secure cryptosystem is the onetime pad The only practically secure cryptosystem is… the one -time pad We do have some cryptosystems which are provably [as] secure as a difficult problem

Review: Bayes’ Theorem l Let X and Y be two random variables. Define: l Theorem (Chain Rule): l Theorem (Bayes): Apriori Aposteriori

Theoretical (Perfect) Security What does it mean for a cryptosystem to be perfectly secure? l Essentially, the adversary doesn’t learn anything from the ciphertext: l

Perfect Security means |K|¸|P| Reminder: adversary “knows the system” and has unlimited power l If key-space is finite, each ciphertext must map to a finite number of plaintexts l If |P|>|K|, some plaintexts will be l “impossible” for some ciphertexts

The Vernam Cipher (1) l Is there a perfectly secure cryptosystem for which |K|=|P|? l Theorem (Shannon): Let (P, K, C, E, D) be a cryptosystem for which |K|=|P|=|C|. Then the cryptosystem provides perfect secrecy iff:

The Vernam Cipher (2) l Proof: Let (P, K, C, E, D) be a cryptosystem for which |K|=|P|=|C|. l Because of perfect secrecy: l |K|=|P|=|C|, so there is a unique key associated with every pair (p, c)

The Vernam Cipher (3) l l Fix c. For all possible plaintexts pi, let ki be the key satisfying eki(pi)=c By Bayes:

The Vernam Cipher (4) Cipher was invented by Gilbert Vernam of Bell Labs in 1919 l Idea – key is a long random sequence, C=P©K l By above proof, cipher is unbreakable l Disadvantage – key is huge and cannot be used twice l Advantage – algorithm is so simple we can give it to the Soviets… l

Towards real-world cryptography l l How secure are cryptosystems with a smaller key space? Rules of the game: l l l Symmetric (deterministic) encryption |P|=|C|, all keys chosen equiprobably Ciphertext-only attack Adversary wishes to recover the key Question: How fast does the set of possible keys shrink as the amount of ciphertext grows?

A Brief Introduction to Information Theory Some random events are more unexpected than others l Some facts are more significant than others l Shannon Entropy measures the amount of uncertainty regarding a random variable, or the amount of information an event provides l Entropy Rate measures the growth of information in an infinitely-long sequence l

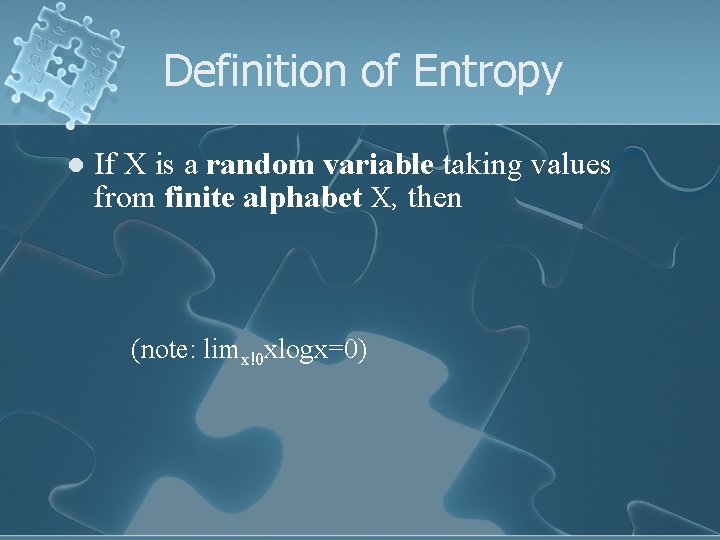
Definition of Entropy l If X is a random variable taking values from finite alphabet X, then (note: limx!0 xlogx=0)

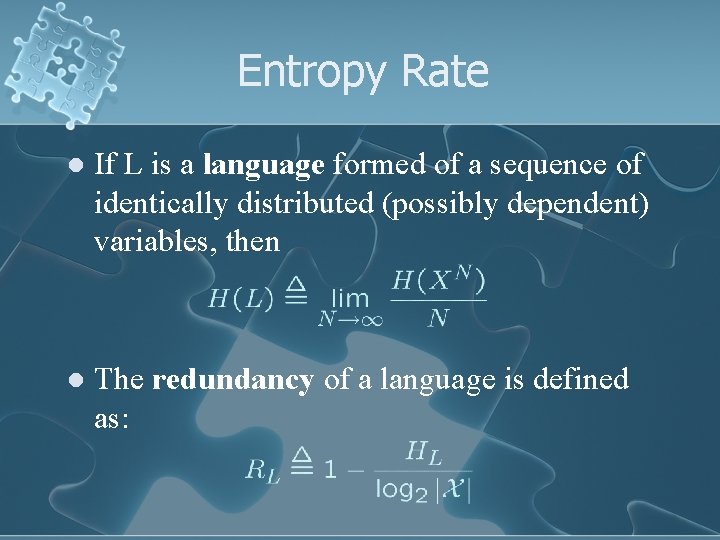
Entropy Rate l If L is a language formed of a sequence of identically distributed (possibly dependent) variables, then l The redundancy of a language is defined as:

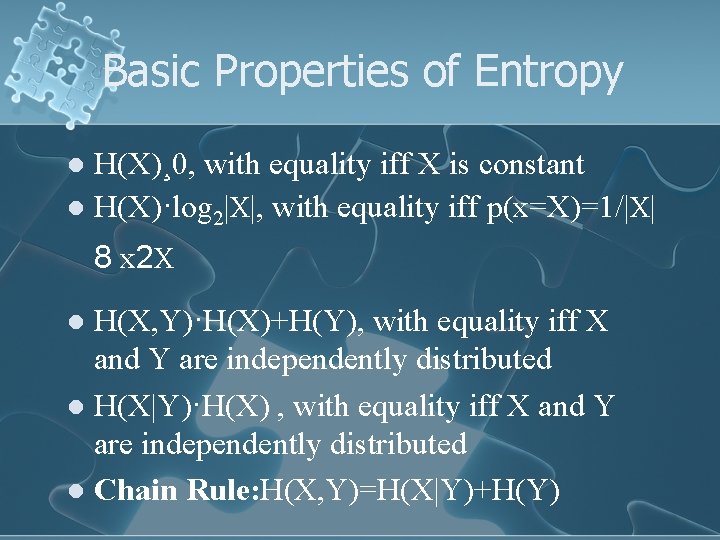
Basic Properties of Entropy H(X)¸ 0, with equality iff X is constant l H(X)·log 2|X|, with equality iff p(x=X)=1/|X| l 8 x 2 X H(X, Y)·H(X)+H(Y), with equality iff X and Y are independently distributed l H(X|Y)·H(X) , with equality iff X and Y are independently distributed l Chain Rule: H(X, Y)=H(X|Y)+H(Y) l

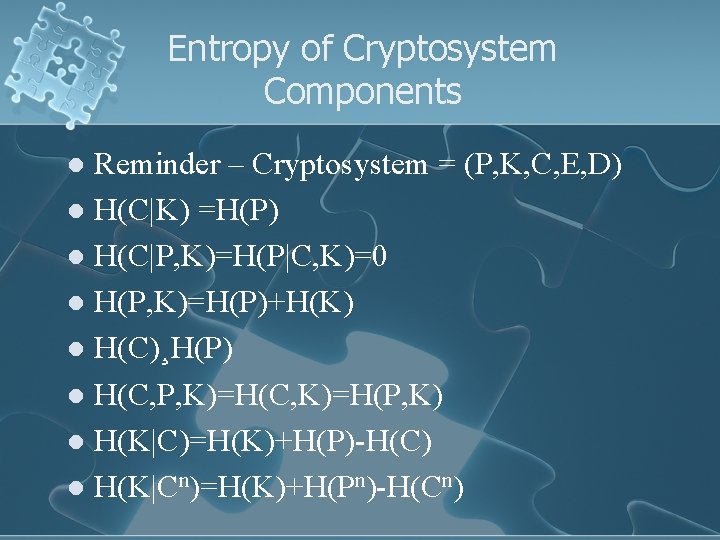
Entropy of Cryptosystem Components Reminder – Cryptosystem = (P, K, C, E, D) l H(C|K) =H(P) l H(C|P, K)=H(P|C, K)=0 l H(P, K)=H(P)+H(K) l H(C)¸H(P) l H(C, P, K)=H(C, K)=H(P, K) l H(K|C)=H(K)+H(P)-H(C) l H(K|Cn)=H(K)+H(Pn)-H(Cn) l

Example: A strong cipher which is very weak (1) l l l Everything Haley says is encrypted with a monoalphabetic substitution cipher Could you break it? Q: Which 2 romantic era authors had their heroes break this cipher? (archive. org cache)

A strong cipher which is very weak (2) Observation: There are 26!¼ 1026 possible substitution ciphers over the lowercase English alphabet l This is equivalent to 88 -bit security – so why was it so easy to break? l Shannon: Any monoalphabetic cipher over the English language is easily broken, given a sequence of 25 letters of unknown ciphertext l

Unicity distance of a language (1) l By definition of the entropy rate: l Since |P|=|C|, we have: l Substituting into the formula for H(K|Cn):

Unicity distance of a language (2) l The cryptosystem is broken when H(K|Cn)=0: l Plug in English (|P|=26, RL¼ 0. 75) and the substitution cipher (log 2|K|¼ 88) and we get n 0¼ 25 (woops).

Tricks to raise the unicity distance The idea – raise the entropy of the language without disturbing content l Adding random nulls – “hello” becomes “h; e; ; l; lo; ; ” l Replace characters with homophonic sets – “hello” becomes “hello” l Compress the data l Good compression – good for encryption l Good encryption – bad for compression l

Product Ciphers and Combined Cryptosystems

“Weighted Sum” Cryptosystems Different cryptosystems can be combined to create a new cryptosystem. l Given two cryptosystems with the same message space, consider a probabilistic combination of the two systems: with probability p use system A, otherwise use system B. l

Endomorphic cryptosystems and product ciphers l l l Another way to use two cryptosystems is to encrypt and decrypt messages consecutively. We call this a product cipher. An endomorphic cryptosystem is a system where the message space is transformed to itself. With such a system we can even create a product of the system with itself. The set of endomorphic cryptosystems with the aforementioned operations almost create a linear associative algebra.

Idempotent and commutative cryptosystems A cryptosystem S is called idempotent if S 2 = S. l Combining two idempotent secrecy systems that commute will create another idempotent secrecy system – isn’t of any use. l

Designing cryptosystems that are hard to attack I Shannon recognizes that aside of brute force attacks, reasonable attacks attempt to find keys according to their probability, hopefully reducing the probability of many of them near 0 without actually testing each and every one. l To do this one needs to create statistics of the ciphertext. l

Designing cryptosystems that are hard to attack II l Statistics must be: Simple to measure l Depend more on the key (if we’re trying to find the key) than the message l Useful – divide the key-space into areas of similar probability and eliminate most l Usable – the separation of the key-space must be natural l

Confusion and Diffusion l To make finding such statistics harder (without an ideal system) Shannon suggests: l l l Diffusion: Spreading the information in such a way that it is hard to get exact results. Confusion: Make the natural separation of the keyspace hard to use. (Make all parameters of key dependant in natural decryption). He believes that a combination of an initial transposition with alternating substitutions and linear operations may do the trick.

Closing Thoughts

Effect of this Paper l l Paper did not bring forth an explosion similar to the 1947 paper “The problem of good cipher design is essentially one of finding difficult problems” This type of problem was made very public with the creation of DES. Both DES and AES use Shannon’s ideas of combining confusion and diffusion (although other ideas that he hadn’t mentioned appear in both).

Some closing thoughts l l Cryptography is always in the context of communication between agents. Not only what messages are transmitted but from whom to whom is important. We can hardly hide the size of messages. One can encrypt messages in ways that allow breaking them, to misinform. In huge information environments one could easily(? ) conceal the existence of messages and the identities of the sender and the receiver.

 Communication theory of secrecy systems
Communication theory of secrecy systems Why is confidentiality important
Why is confidentiality important Secrecy
Secrecy Engineering elegant systems: theory of systems engineering
Engineering elegant systems: theory of systems engineering Engineering elegant systems: theory of systems engineering
Engineering elegant systems: theory of systems engineering Paper 2 aice general paper
Paper 2 aice general paper Aice general paper paper 1
Aice general paper paper 1 Decision support systems and intelligent systems
Decision support systems and intelligent systems Embedded systems vs cyber physical systems
Embedded systems vs cyber physical systems Principles of electronic communication systems 3rd edition
Principles of electronic communication systems 3rd edition Iec 61850 communication networks and systems in substations
Iec 61850 communication networks and systems in substations Information systems and communication technologies quiz
Information systems and communication technologies quiz Business and communication systems
Business and communication systems Modeling of digital communication systems using simulink
Modeling of digital communication systems using simulink Characteristics of interprocess communication
Characteristics of interprocess communication Analog vs digital communication systems
Analog vs digital communication systems Ccea microsite
Ccea microsite Modeling of digital communication systems using simulink
Modeling of digital communication systems using simulink Indirect communication in distributed systems
Indirect communication in distributed systems Ambulance communication systems
Ambulance communication systems Principles of electronic communication systems 3rd edition
Principles of electronic communication systems 3rd edition Group communication in distributed systems
Group communication in distributed systems Communication systems
Communication systems Communication interface in embedded systems
Communication interface in embedded systems Gcse business and communication systems
Gcse business and communication systems Telex football headsets
Telex football headsets Wallerstein's model
Wallerstein's model Wallerstein's model
Wallerstein's model Modernization theory vs dependency theory
Modernization theory vs dependency theory Systems theory example
Systems theory example Aree seekheo
Aree seekheo Wallerstein's world systems theory map
Wallerstein's world systems theory map Generalist intervention model social work
Generalist intervention model social work Dynamical systems theory motor development
Dynamical systems theory motor development Betty neuman's model
Betty neuman's model Example of centripetal force ap human geography
Example of centripetal force ap human geography Human systems dynamics theory
Human systems dynamics theory Dorothy johnson metaparadigm
Dorothy johnson metaparadigm Bronfenbrenner's ecological systems theory
Bronfenbrenner's ecological systems theory Bronfenbrenner's ecological systems theory
Bronfenbrenner's ecological systems theory Urie bronfenbrenner ecological systems theory
Urie bronfenbrenner ecological systems theory Neuman's systems theory
Neuman's systems theory Family systems theory powerpoint
Family systems theory powerpoint Yr.eo
Yr.eo Systems theory
Systems theory What are the 5 stages of rostow's model
What are the 5 stages of rostow's model The nature of theory in information systems
The nature of theory in information systems Parallel and serial port
Parallel and serial port What is oral communication and written communication
What is oral communication and written communication Parallel communication arduino
Parallel communication arduino Mass communication
Mass communication Meaning of oral communication
Meaning of oral communication Serial communication vs parallel communication
Serial communication vs parallel communication Multi step flow theory
Multi step flow theory Normative theory
Normative theory What is constructivism
What is constructivism Politeness theory in communication
Politeness theory in communication Gibbs theory communication
Gibbs theory communication