Chapter 8 Risk Assessment Risk Treatment Assets and
































- Slides: 35

Chapter 8 風險評鑑


Risk Assessment & Risk Treatment Assets and asset values n Security threats and vulnerabilities (威脅和弱 點) n Risk assessment n Treatment of the risks n Security controls and countermeasures (對策) 相關標準: ISO 13335 Risk Assessment 方法 n Statement of applicabiliity AN 4360 (紐澳標準) n


What is Risk? n n The possibility of incurring misfortune or loss; hazard Vulnerable(脆弱性); likely to be lost or damaged To proceed in an action without regard to the possibility of danger involved in it. To expose to danger or loss


Risk Assessment Process n 用流程的方法 n Identifying assets and assigning values n n n 資產非僅限於財務部資產清冊內容 以重要性評估非購入價格 Identifying threats to these assets and assessing their likelihood (定性評估) Identifying vulnerabilities and assessing how easily they might be exploited (如何被利用) Identifying the protection provided by the controls in place Assessing the overall risk resulting from the above



Assets n Examples of assets associated with information systems are n n n n Information assets – data files, user manuals etc. Paper documents – contracts, guidelines etc. Software assets – application & system software etc. Physical assets – computer, magnetic media etc. People – customers, personnel etc. Company image and reputation Services – communications, 電力, 網路, technical etc.


Asset Values (and Potential Impacts) n n n Has the organization identified the value of their information assets? 決定每個資產的價值是決定一個有效率 安全策略的第一步 資產價值衡量的系統 n n 0~5 or low to very high (何者較佳? ) 這是風險評鑑過程中極為重要的一部份






Risk n Risk=Value + Threat + Vulnerability n Risk=Value X Threat X Vulnerability Impact Likelihood of Occurrence

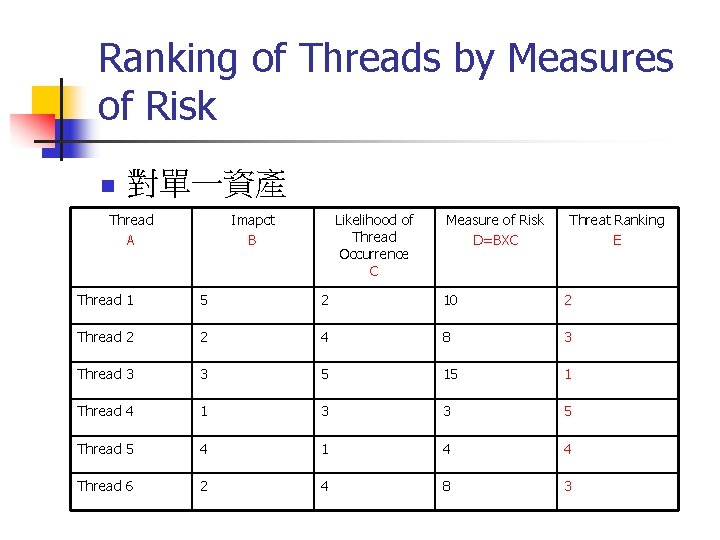
Ranking of Threads by Measures of Risk n 對單一資產 Thread A Imapct B Likelihood of Thread Occurrence C Measure of Risk D=BXC Threat Ranking E Thread 1 5 2 10 2 Thread 2 2 4 8 3 Thread 3 3 5 15 1 Thread 4 1 3 3 5 Thread 5 4 1 4 4 Thread 6 2 4 8 3

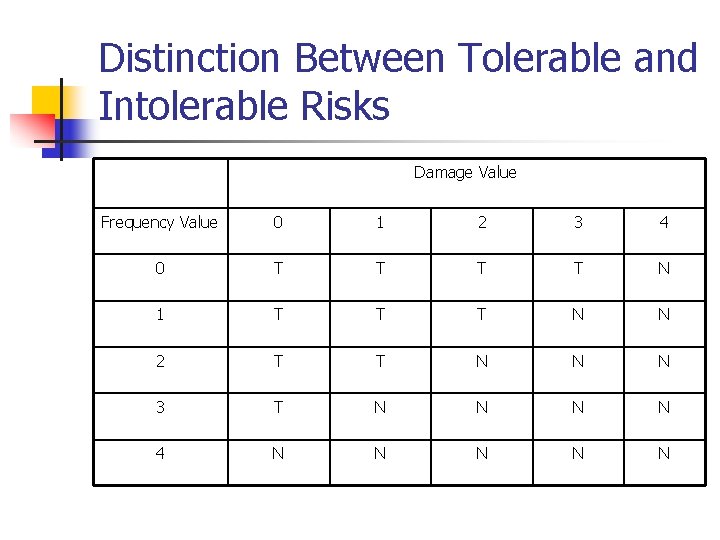
Distinction Between Tolerable and Intolerable Risks Damage Value Frequency Value 0 1 2 3 4 0 T T N 1 T T T N N 2 T T N N N 3 T N N 4 N N N

Tools and Methods for Risk Assessment n What tool does BS 7799 recommend? n 風險評鑑應該鑑別對組織資產的威脅,脆弱 性,和衝擊而且應該決定風險程度。


What to look for in a risk assessment/management tool? n 具應該至少包含下列模組 n n n Data collection Analysis Output of results

Some Tools and Methods for Risk Assessment @Risk Security By Analysis (SBA) Analy. Z XRM (e. Xpert Risk Management) BDSS (Bayesian Decision Support System) Analyse Risques Programmes COBRA (Consultative, Objective and Bi-functional Risk Analysis) CONTROL-IT AROME+ CRAMM (CCTA Risk Analysis and management method) BDS Risk Assessor DDIS (Datenschutz-und-datensicherheits informations system) IST/RAMP (International Security Technology / Risk analysis management program) LAVA (Los Alamos Vulnerability Analysis) Buddy System LRAM & ALRAM ([Automated] Livemore Risk Analysis Methodology) MELISA CRITI_CALC PREDICT MINIRISK RANK-IT PSICHE Risiko RISAN Risk. PAC Risk. Watch SISSI Risk. CALC


Risk Treatment - Direction n n Accepting the residual risk Avoiding the risk Transferring the risk Reducing the risk to an acceptable level




Control Selection n 考量因素 n n n n Risk Degree of assurance required Cost Easy of implementing Servicing (支援服務) 法律和法規的要求 客戶和其他合約的要求 (加密, 數位簽章, …)





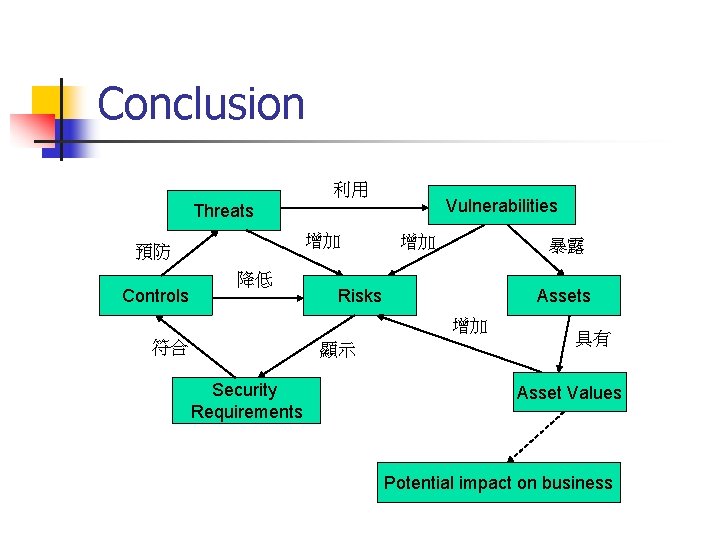
Conclusion 利用 Vulnerabilities Threats 增加 預防 Controls 降低 增加 暴露 Risks Assets 增加 符合 顯示 Security Requirements 具有 Asset Values Potential impact on business
 Depreciation expense formula
Depreciation expense formula Real assets and financial assets ppt
Real assets and financial assets ppt Plant assets natural resources and intangible assets
Plant assets natural resources and intangible assets Real assets versus financial assets
Real assets versus financial assets Plant assets, natural resources, and intangible assets
Plant assets, natural resources, and intangible assets Real assets vs financial assets
Real assets vs financial assets Real assets versus financial assets
Real assets versus financial assets Chapter 1 risk and its treatment
Chapter 1 risk and its treatment Capital allocation between risky and risk free asset
Capital allocation between risky and risk free asset Assessment and treatment alternatives
Assessment and treatment alternatives Market risk credit risk operational risk
Market risk credit risk operational risk How to calculate risk weighted assets
How to calculate risk weighted assets Risk weighted assets example
Risk weighted assets example Chapter 9 plant and intangible assets
Chapter 9 plant and intangible assets Plant and intangible assets chapter 9
Plant and intangible assets chapter 9 Examples intangible assets
Examples intangible assets Chapter 4 transactions that affect assets
Chapter 4 transactions that affect assets Chapter 12 intangible assets
Chapter 12 intangible assets Accounting for intangible assets
Accounting for intangible assets Chapter 4 transactions that affect assets
Chapter 4 transactions that affect assets Ionic compounds
Ionic compounds Chapter 7 chapter assessment ionic compounds and metals
Chapter 7 chapter assessment ionic compounds and metals Chapter 28 oral diagnosis and treatment planning
Chapter 28 oral diagnosis and treatment planning Chapter 28 oral diagnosis and treatment planning
Chapter 28 oral diagnosis and treatment planning Property, plant, and equipment and intangible assets are
Property, plant, and equipment and intangible assets are Hairadc
Hairadc What is framp
What is framp Health and safety risk assessment template
Health and safety risk assessment template Population health risk assessment and management
Population health risk assessment and management Criticality analysis and risk assessment
Criticality analysis and risk assessment Residual risk and secondary risk pmp
Residual risk and secondary risk pmp Business risk vs financial risk capital structure
Business risk vs financial risk capital structure Relative risk
Relative risk Population attributable risk formula
Population attributable risk formula Chapter 10 chemical reactions answer key
Chapter 10 chemical reactions answer key Chapter 11 study guide chemistry stoichiometry answer key
Chapter 11 study guide chemistry stoichiometry answer key