Assets Information Assets n Software Assets n Hardware







































































- Slides: 84








資訊資產(Assets)的種類 資訊資產(Information Assets) n 軟體資產(Software Assets) n 硬體資產(Hardware Assets) n 文件資產(Paper Document) n 服務(Service) n 公司形象(Company Image) n 識別 8 分類 鑑價




12

13








在入侵者之前找到漏洞或弱點 Unstructured Structured External Internal Network Threats and Vulnerabilities 21


弱點檢查報告(1/2) Executive Summary We have scanned your host/s XXX for YYY known security holes. This scan took place on 22: 43: 02 09/09/2002 and took 0 hours and 50 minutes to complete. A total of 17 vulnerabilities were found; Out of the 17 vulnerabilities that were found: High Risk Vulnerabilities (Should be attended to as soon as possible) Medium Risk Vulnerabilities (Should be repaired in the next couple of days) Intelligence Gathering or Low Risk Vulnerabilities (Should be added to work list – can be attended at later time) Security 'holes' that allow a remote attacker to: 3 o o o Have read / write access to any file on the server Login to the server remotely easily as administrator Ability to run commands in order to continue hacking to the network Security 'holes' that allow a remote attacker to attack a server by: 5 o o o 9 Conducting a combination attack (using several vulnerabilities simultaneously) Having access to 'sensitive' files Running 'Denial of Service' attacks that will crash the network Security 'holes' which will not help an attacker to gain access to server, but, it will give him information about the local network or hosts In addition, 11 open TCP or UDP ports were found; Make sure all those services are really needed. Remember: Useless services are possible entry points for attackers!! 23




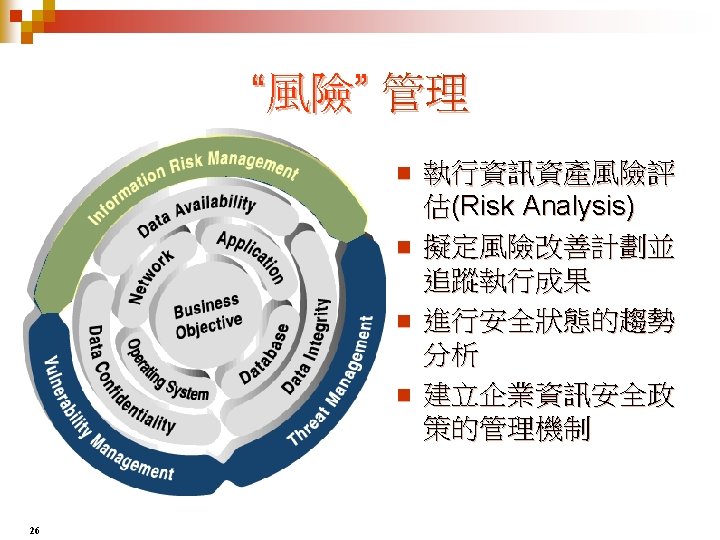
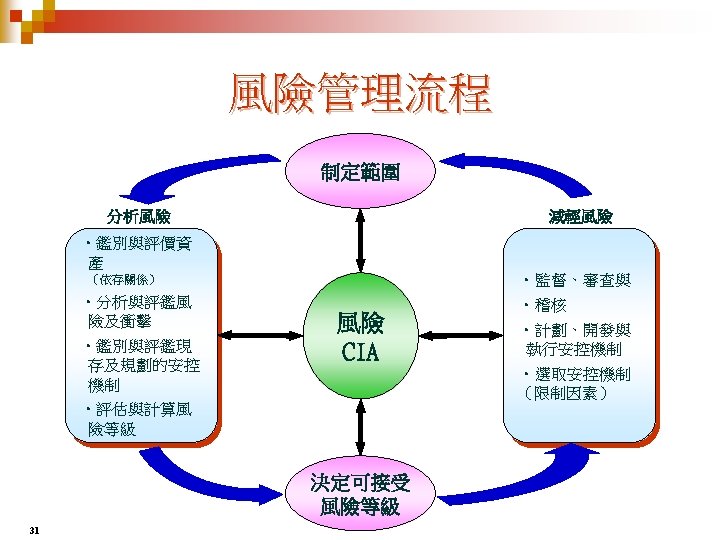
弱點, 威脅, 資產 與 風險 的關係 Threat Agent Give Rise to Threat Exploits Vulnerability Directly Affects Risk Asset Exposure Safeguard (Control) 27 Leads to And Causes an Can be Countermeasured by a Can Damage



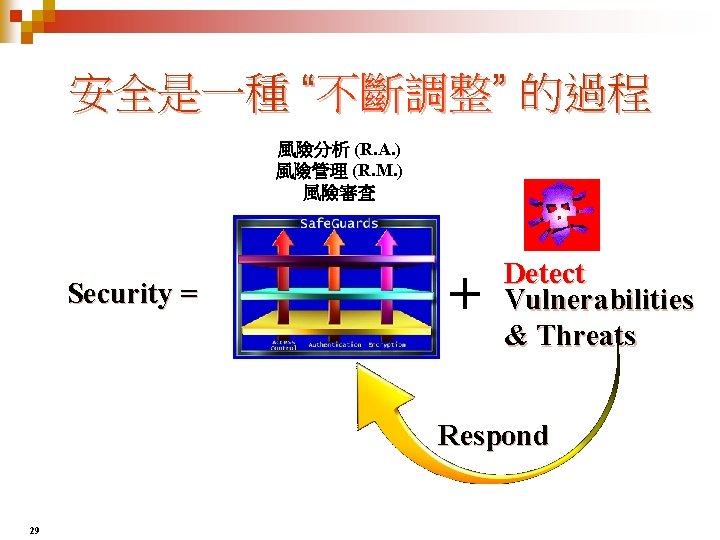
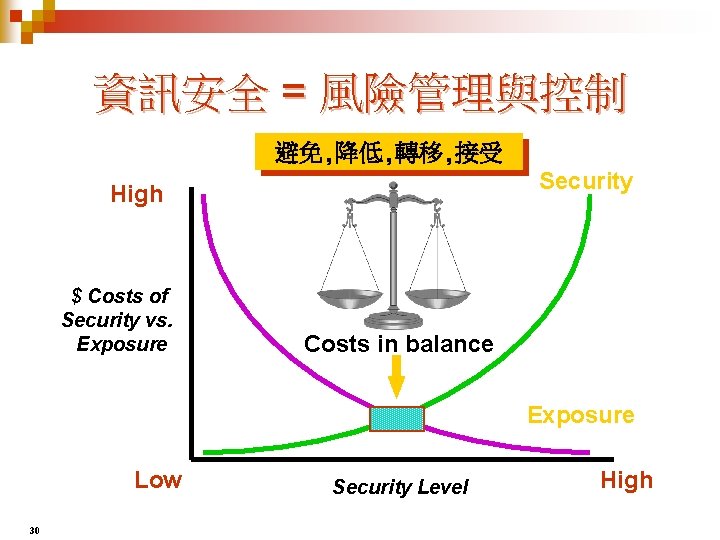
資訊安全 = 風險管理與控制 避免, 降低, 轉移, 接受 Security High $ Costs of Security vs. Exposure Costs in balance Exposure Low 30 Security Level High





ISMS/BS 7799 教育訓練簡報 BS 7799/ CNS 17800 十大控制方法

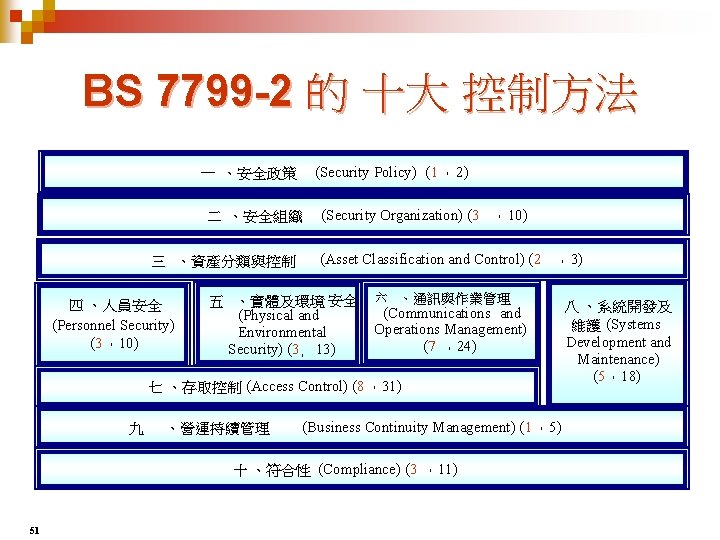
BS 7799 -2 的 十大 控制方法 (Security Policy) (1 ,2) 一 、安全政策 二 、安全組織 三 、資產分類與控制 四 、人員安全 (Personnel Security) (3 ,10) (Security Organization) (3 , 10) (Asset Classification and Control) (2 , 3) 五 、實體及環境 安全 (Physical and Environmental Security) (3, 13) 六 、通訊與作業管理 (Communications and Operations Management) (7 ,24) 七 、存取控制 (Access Control) (8 ,31) 九 、營運持續管理 (Business Continuity Management) (1 ,5) 十 、符合性 (Compliance) (3 ,11) 36 八 、系統開發及 維護 (Systems Development and Maintenance) (5 ,18)


全球 BS 7799 - 2 認證總數 Source : IUG web site, Oct. -2003 38 Total : 399 (OCT-2003)





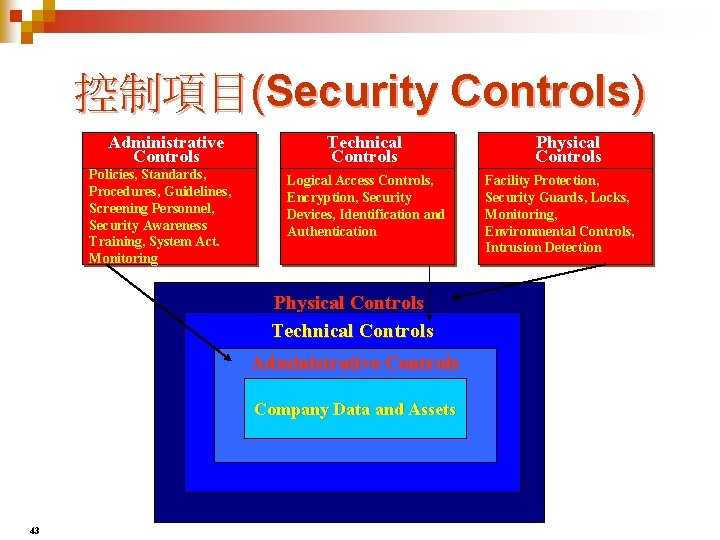
控制項目(Security Controls) Administrative Controls Policies, Standards, Procedures, Guidelines, Screening Personnel, Security Awareness Training, System Act. Monitoring Technical Controls Logical Access Controls, Encryption, Security Devices, Identification and Authentication Physical Controls Technical Controls Administrative Controls Company Data and Assets 43 Physical Controls Facility Protection, Security Guards, Locks, Monitoring, Environmental Controls, Intrusion Detection








BS 7799 -2 的 十大 控制方法 (Security Policy) (1 ,2) 一 、安全政策 二 、安全組織 三 、資產分類與控制 四 、人員安全 (Personnel Security) (3 ,10) (Security Organization) (3 , 10) (Asset Classification and Control) (2 , 3) 五 、實體及環境 安全 (Physical and Environmental Security) (3, 13) 六 、通訊與作業管理 (Communications and Operations Management) (7 ,24) 七 、存取控制 (Access Control) (8 ,31) 九 、營運持續管理 (Business Continuity Management) (1 ,5) 十 、符合性 (Compliance) (3 ,11) 51 八 、系統開發及 維護 (Systems Development and Maintenance) (5 ,18)







資訊資產(Assets)的種類 資訊資產(Information Assets) n 軟體資產(Software Assets) n 硬體資產(Hardware Assets) n 文件資產(Paper Document) n 服務(Service) n 公司形象(Company Image) n 識別 58 分類 鑑價

資產分類的方式 n n Commercial n Military ¨ Confidential ¨ Top Secret ¨ Private ¨ Secret ¨ Sensitive ¨ Confidential ¨ Public ¨ Sensitive but unclassified (SBU) ¨ Unclassified Focus on ¨ Integrity ¨ Availability n Focus on ¨ Non-Disclosure of Confidential 59
























