Chapter 4 Guarding Against Network Intrusions TRADITIONAL RECONNAISSANCE




































- Slides: 44

Chapter 4 Guarding Against Network Intrusions

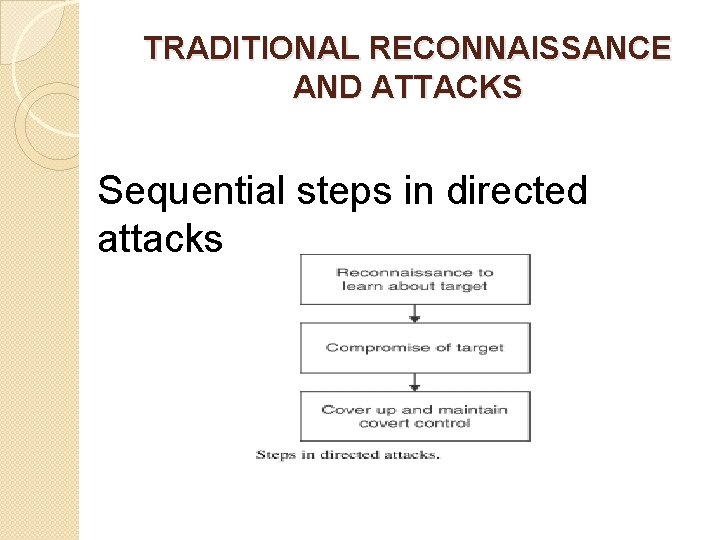
TRADITIONAL RECONNAISSANCE AND ATTACKS Sequential steps in directed attacks

Reconnaissance to learn about the target. �The attacker performs reconnaissance to learn as much as possible about target before the actual attack. �pings and traceroutes can be used to discover IP addresses and map the network around the target. �Pings are ICMP echo request and echo reply messages that verify a host’s IP address and availability.

�Traceroute is a network mapping utility that takes advantage of the time to live (TTL) field in IP packets. �Port scans can reveal open ports. Ex: port 80 (HTTP), port 21 (FTP), port 23 (Telnet), port 25 (SMTP). �NMAP scanner can discover the operating system running on a target. �Knowledge of a target’s operating system can help an attacker identify vulnerabilities and find effective exploits.

�Vulnerability scanning tests a target for the presence of vulnerabilities. �Vulnerability scanners typically contain a database of known vulnerabilities that is used to craft probes to a chosen target.

Compromise the target �The attacker attempts to compromise the target through one or more methods like password attacks. �If an attacker can obtain the password file from the target, numerous passwordcracking tools are available to carry out a brute-force password attack. �Default accounts and passwords intended to set up the equipment will help intruders an easy way to access the target.

�Another common attack method is an exploit attack code written to take advantage of a specific vulnerability. �Vulnerabilities are published through security bulletins by several organizations such as CERT , MITRE and Microsoft. �The severity of vulnerabilities is reflected in the industry-standard Common Vulnerability Scoring System (CVSS).

According to Symantec in 2007 § 3% of vulnerabilities were highly severe § 61% were medium-severe § 36% were low-severe �Buffer overflows have been the most common type of vulnerability. �Buffer overflows arises when a program has allocated a fixed amount of memory space for storing data but receives more data than expected.

The extra data will overwrite adjacent parts of memory which could mess up other variables or pointers. �If an attacker crafts the extra data carefully that benefits the attacker to compromise the target. �An attacker might overwrite the return pointer in a stack, causing the program control to jump to malicious code inserted by the attacker. •

�SQL injection is a type of vulnerability relevant to Web servers with a database backend. �An SQL injection vulnerability can arise if user input is not properly filtered for string literal escape characters , it helps the attacker manipulate the application running on the database �Servers have been attacked and compromised by toolkits designed to automate customized attacks. Ex: MPack toolkit in Russia(2007)

�Different exploits can be written and loaded into Metasploit and then directed at a chosen target. �Metasploit is a popular Perl based tool for developing and using exploits with an easy-to-use Web or command-line interface • A common social engineering attack is phishing.

�Phishing starts with a spam message that appears to be from a legitimate bank or ecommerce business. �The message provokes the reader into visiting a fraudulent Web site pretending to be a legitimate business. �The fraudulent site might even have links to the legitimate Web site , thus tricked into submitting valuable personal information such as account numbers, passwords.

�Another social engineering attacks are spam messages that entice the reader into opening an email attachment.

Cover up and maintain covert control �After a successful attack, intruders want to maintain remote control and evade detection. �Remote control can be maintained if the attacker has managed to install any of a number types of malicious software �Intruders might change the system logs on the target, which will likely contain evidence of their attack.

�A rootkit is a stealthy type of malicious software designed to hide the existence of certain processes or programs from normal methods of detection. �Ex . kernel-mode FU rootkit that manipulates kernel memory in Windows 2000, XP, and 2003. �Intrusion Detection Systems (IDSs) are designed to listen to network traffic and look for signs of suspicious activities.

�The intruder want to conceal the communications between himself and the compromised target from IDSs. �Concealment methods are Ø Tunneling -is a commonly used method to place packets of one protocol into the payload of another packet. Here the exterior packets serves a vehicle to carry and deliver the “ interior ” packet intact. Ø Encryption is another obvious concealment method. Ø Fragmentation of IP packets is another means to conceal the contents of messages from IDSs

MALICIOUS SOFTWARE �Malicious software which includes viruses and worms. �Viruses are pieces of code attached to a normal file or program. �Worms are standalone automated programs. �Viruses need a human action to spread �Worms look for vulnerable targets across the network and transfer a copy of themselves.

�An important feature of viruses and worms is their capability to carry a payload — malicious code that is executed on a compromised host. �Worms are popular delivery vehicles because of their ability to spread by themselves and carry anything in their payload. �The second class includes Trojan horses and rootkits , they are characterized by attempts to conceal themselves.

�Trojan horses are a type of malware that appears to perform a useful function but hides a malicious function. � Rootkits are hiding the presence of files or processes from normal means of detection. �Rootkits are often installed as drivers or kernel modules.

� Third class includes remote access Trojans (RATs) and bots. • RAT is sometimes interpreted as remote administration tool because it can be used for legitimate purposes by systems administrators. • Ex: Back Orifice, Netbus, and Sub 7.

� Bots are remote-control programs installed covertly on innocent hosts. �All bots under control of the same bot herder form a botnet. � One of the most publicized bots is the Storm worm. � Another major class of malware is designed for data theft. This class includes keyloggers and spyware. � Keyloggers are planted by criminals on unsuspecting hosts to steal passwords

�Spyware is designed to monitor and report user activities for the purposes of learning personal information without the user’s consent. �Spyware might or might not display an end-user license agreement (EULA) before installation.

Lures and “ Pull ” Attacks �Sending malware through email can only be seen as an attack attempt. �The Web has become the primary vector for infecting computers. • Web-based attacks have significant advantages for attackers. • They are stealthier and not as “ noisy ” as active attacks, making it easier to continue undetected for a longer

�A visitor will be attacked only once, which makes the attack harder to detect. � Web server can serve up different attacks, depending on the visitor’s operating system and browser. � A phishing site is typically disguised as a legitimate financial organization or ecommerce business. � Another attack is a malicious site �that attempts to download malware through a visitor’s browser, called a drive-by download.

�Pull-based attacks must attract visitors to the malicious site while avoiding detection by security researchers.

DEFENSE IN DEPTH �Defense-in-depth strategy is to hinder the attacker as much as possible with multiple layers of defense. �A combination of multiple layers will be more effective against unpredictable attacks than will a single defense optimized for a particular type of attack. �Defense in depth is to involve people, technology, and operations.

�Include firewalls, IDSs, routers with ACLs, antivirus software, access control, spam filters etc. . �Preventive activities include vulnerability assessments, software patching, system hardening (closing unnecessary ports), and access controls.

PREVENTIVE MEASURES Access Control Authentication of users � Authorization of their privileges � Auditing to monitor and record user actions � � Authentication is the process of verifying a user’s identity. � Ex. Password or PIN , Smart card or token finger print, retinal pattern, or biometric identifier

�A combination of two factors, such as a password and a fingerprint, called two-factor (multifactor) authentication. � Authorization is the process of determining what an authenticated user can do. � Ex. Permissions like read , write , execute �Auditing is necessary to ensure that users are accountable. (Ex. Log file)

Vulnerability Testing and Patching �Vulnerabilities are being discovered constantly in different ways and reported confidentially to the vendor. � Vulnerability testing is an exercise to probe systems for known vulnerabilities. Closing ports: �Port numbers 1 to 1023 are well known and assigned by the Internet Assigned Numbers Authority (IANA) to standardized services running with root privileges.

�Port numbers 1024 to 49151 are used by various applications with ordinary user privileges. �It is good practice to close ports that are unnecessary, because attackers can use open ports. Firewalls : • A firewall selectively allows or blocks incoming and outgoing traffic. • Various types of firewalls: packetfiltering firewalls, stateful firewalls, and proxy firewalls.

�Packet-filtering firewalls analyze packets in both directions and either permit or deny passage based on a set of rules. Antivirus and Antispyware Tools: Challenges faced by antivirus software: • Malware tactics are sophisticated and constantly evolving. • Even the operating system on infected hosts cannot be trusted. • Malware can exist entirely in memory without affecting files • Malware can attack antivirus processes. • Users can be annoyed and turn the antivirus off.

�Detection can be Signature based or behavior based. �It is analyzed for unique characteristics that can be described in a signature. �Behavior-based detection looks at what malware tries to do. �We must define what is suspicious behavior, or what is normal behavior.

Spam Filtering �Spam is unsolicited, sent in bulk, and commercial in nature. �Spam is a popular vehicle to distribute malware and lures to malicious Web sites. �Spam filters work at an enterprise level and a personal level. �Bayesian filtering is one of the more popular techniques. An incoming message is parsed into tokens, and calculates token probabilities based on Bayes ’ theorem

Honeypots � The basic idea of a honeypot is to learn about attacker techniques by attracting attacks to a seemingly vulnerable host. �Requirements: • A honeypot should not be used for legitimate services or traffic. • A honeypot should have comprehensive and reliable capabilities for monitoring and logging all activities.

Network Access Control �The general idea of Network Access Control (NAC) is to restrict a host from accessing a network unless the host can provide evidence of a strong security posture.

INTRUSION MONITORING AND DETECTION Host-Based Monitoring �Host-based IDS runs on a host and monitors system activities for signs of suspicious behavior. Draw backs: • Visibility is limited to a single host • IDS process consumes resources and reduces the performance of the host. • Attacks will not be seen until they have already reached the host.

Traffic Monitoring �Network-based IDSs typically monitor network packets. �Advantages over host based Detection • Network-based IDSs can see traffic for a population of hosts • They can recognize patterns shared by multiple hosts. • They have the potential to see attacks before they reach the hosts

Signature-Based Detection (SBD) �SBD depends on patterns that uniquely identify an attack. � The central issue is how to define signatures. Ex: Snort Drawbacks: New attacks can be missed if a matching signature is not known. • Signatures require time to develop for new attacks. • New signatures must be distributed continually. •

Behavior Anomalies �A behavior-based IDS recognize new attacks without a known signature. � The critical issue is how to define normal behavior and suspicious behavior. �Major challenges: Normal behavior is based on past behavior hence past behavior must be available for training the IDS. • IDS approach must be adaptive because behavior change over time. • Anomalies are just unusual events, not necessarily be malicious. •

Intrusion Prevention Systems � An intrusion prevention system (IPS ) automatically reconfiguring firewalls to block an attack. REACTIVE MEASURES Quarantine : Logically disrupting the connectivity between hosts or networks as a means to impede the malware from spreading further.

Traceback: Problems faced in tracing the attacker: Source address in IP packets can be easily spoofed • Routers are stateless by design and do not keep records of forwarded packets. • Attackers can use a series of intermediary hosts (called stepping stones or zombies ) to carry out their attacks. •

Conclusions: �To guard against network intrusions, we must understand the variety of attacks. �Direct attacks are prevalent but Pull attacks are much more difficult to uncover. �Defense in depth is a most practical defense strategy. �One of the essential defenses is intrusion detection. �Host-based and network-based intrusion detection systems have their respective strengths and weaknesses. �Research continues to be needed to improve intrusion detection.

End of Chapter 4