Chapter 25 Intrusion Detection Dr Wayne Summers Department





- Slides: 11

Chapter 25: Intrusion Detection Dr. Wayne Summers Department of Computer Science Columbus State University Summers_wayne@colstate. edu http: //csc. colstate. edu/summers

Principles ¨ Computer Systems under attack – Actions of users and processes do not conform to a statistically predictable pattern – Actions of users and processes include sequences of commands that attempt to subvert the security policy of the system – Actions of processes do not conform to set of specifications that are allowed for the process 2

Basic Intrusion Detection ¨ Attack tool- automated script designed to violate a security policy (ex. rootkit) ¨ Goals of an IDS – Detect a wide variety of intrusions (inside / outside; known/unknown attacks) – Detect intrusions in a timely fashion – Present the analysis in simple, easy-to-use format – Be accurate (minimize false positives and false negatives) 3

Models ¨ Anomaly Modeling – analyzes set of characteristics of system and compares behavior to expected values – Threshold metric: uses minimum/maximum values – Statistical moments: uses mean/std. dev. & other measures of correlation – Markov model: uses set of probabilities of transition (requires training data) ¨ Misuse Modeling – determines whether a sequence of instructions being executed is known to violate the site security policy ¨ Specification Modeling – determines whether a sequence of instructions violates a specification of how a program/system should execute 4

Architecture ¨ Agent – obtains information from data source (“logger”) – Host-based Intrusion Detection System (HIDS) • Uses system and application logs – Network-based Intrusion Detection System (NIDS) • Uses devices and software to monitor network traffic ¨ Director – reduces log entries and then determines if an attack is underway (“analyzer”) ¨ Notifier – accepts information from director and takes appropriate action (GUI, email) 5

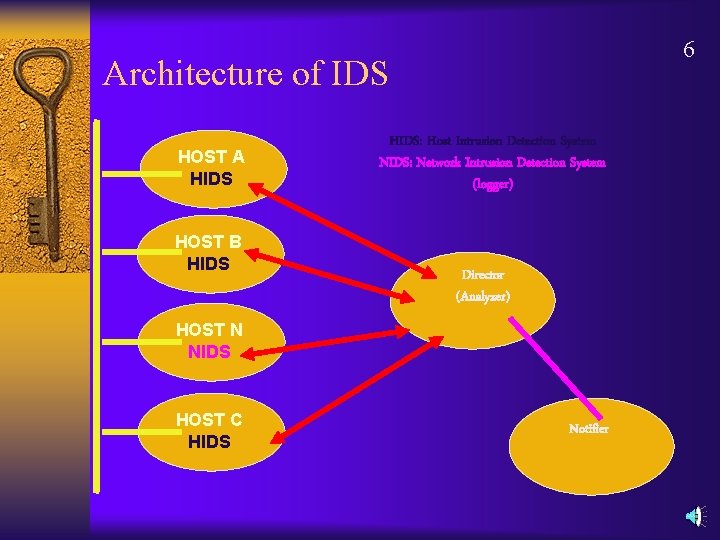
6 Architecture of IDS HOST A HIDS HOST B HIDS: Host Intrusion Detection System NIDS: Network Intrusion Detection System (logger) Director (Analyzer) HOST N NIDS HOST C HIDS Notifier

Host-based IDS – Periodically analyze logs, perform file system integrity check. – Examples: • Generic: ISS Real. Secure Server Sensor. • Check host file system: Tripwire, AIDE • Check host network connections: Black. ICE, Port. Sentry • Check host’s log files: Log. Sentry, Swatch • Intrusion Prevention System: Cisco Security Agent (Okena Stormwatch). 7

Network-based IDS – Analyze network traffic content and pattern for signs of intrusion – Examples: • Snort • Cisco Sensors 8

Organization of IDSs ¨ Monitoring Network Traffic for Intrusions – Network Security Monitor • Develops profile of expected usage of network and compares current usage with the profile – Distributed IDS – combines abilities of NSM with host-based IDS – Autonomous Agents for ID – autonomous agents that work together 9

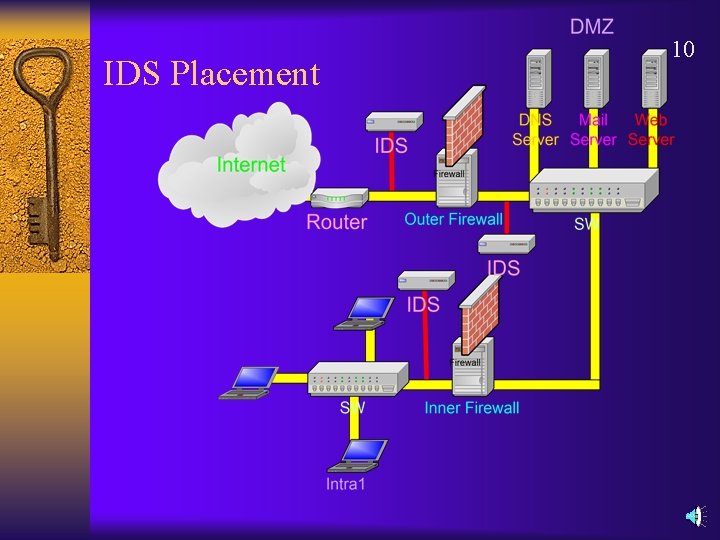
IDS Placement 10

Intrusion Response ¨ Incident Prevention – Intrusion Prevention Systems – Identify attack before it completes – Jail (sandbox) attacks ¨ Intrusion Handling – – – Preparation for attack Identification of attack Containment of the attack Eradication of the attack (blocks further attacks) Recovery from the attack Follow-up to the attack • Pursue legal action • Tracing attack: thumbprinting, IP header markers 11