CellularAutomated Protocol to Safeguard Confidentiality of QR Codes




- Slides: 23

Cellular-Automated Protocol to Safeguard Confidentiality of QR Codes Source: IEEE Access, vol. 7, pp. 144451 -144471, 2019. Authors: Abdullah M. Iliyasu. Speaker: Huang Peng-Cheng Date: 6/11/2021 1

Outline • Introduction • Related works • Proposed scheme • Simulation results • Conclusions • Comments 2

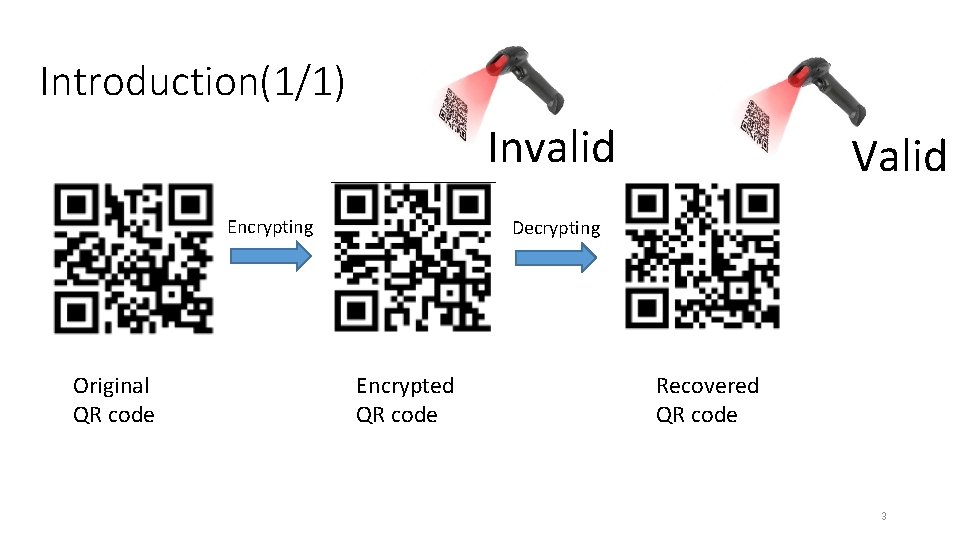
Introduction(1/1) Invalid Encrypting Original QR code Valid Decrypting Encrypted QR code Recovered QR code 3

Related works(1/6) Cellular Automata (CA) • Homogeneity – all cell states are updated by the same set of rules • Parallelism – all cell states are updated simultaneously • Locality – all interactions take place on a purely local basis and a cell can only communicate with a few other cells

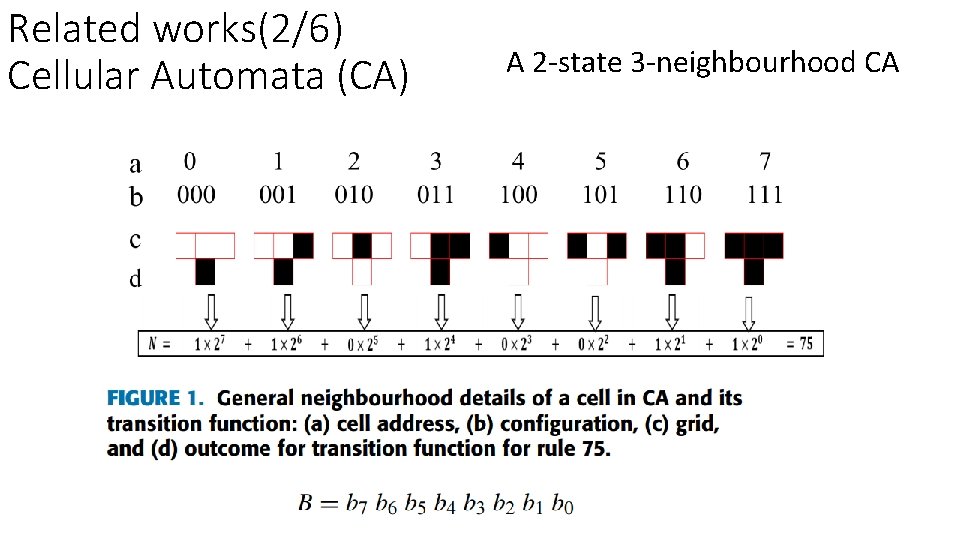
Related works(2/6) Cellular Automata (CA) A 2 -state 3 -neighbourhood CA

Related works(3/6) Cellular Automata (CA)

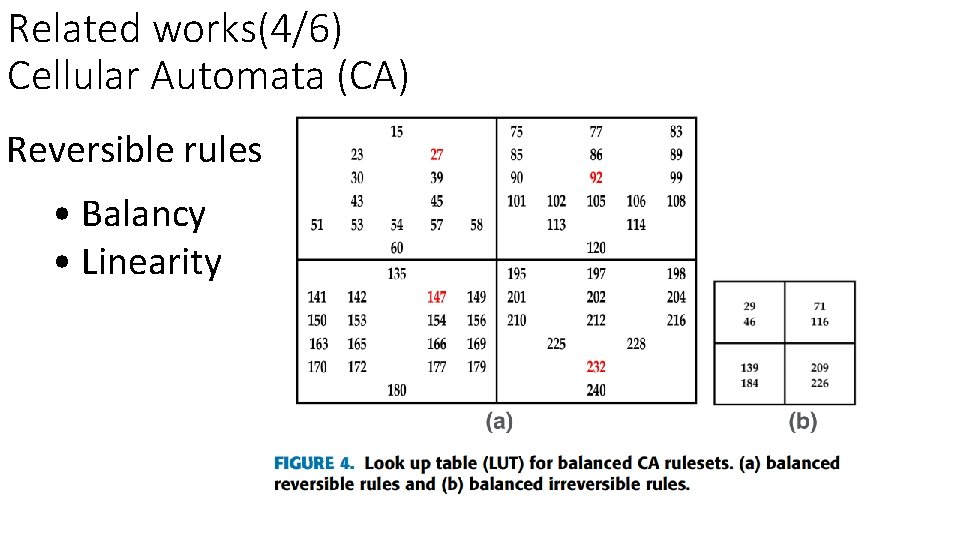
Related works(4/6) Cellular Automata (CA) Reversible rules • Balancy • Linearity

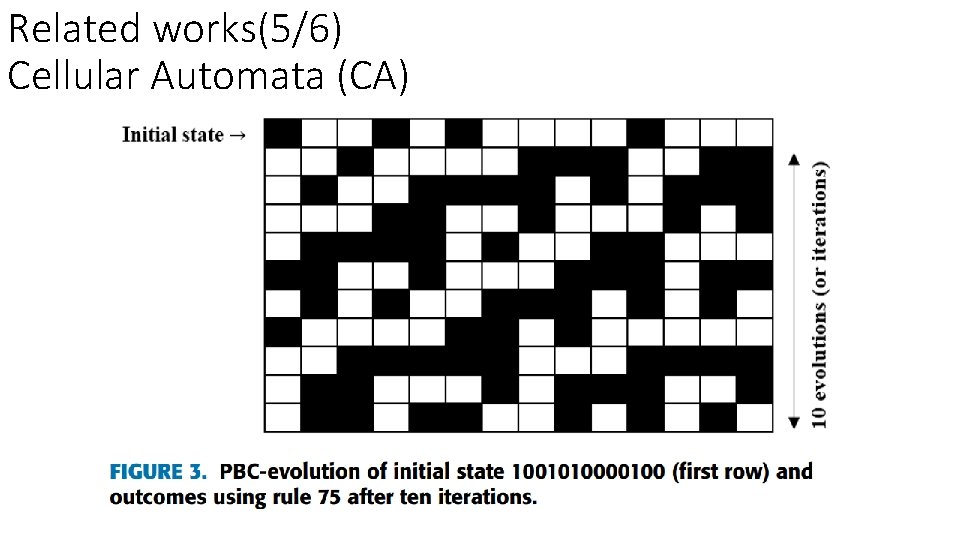
Related works(5/6) Cellular Automata (CA)

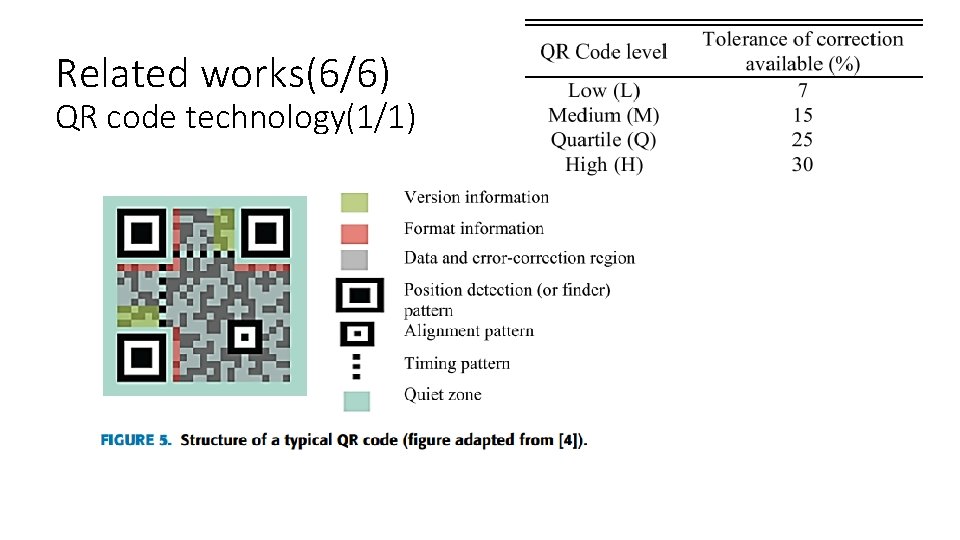
Related works(6/6) QR code technology(1/1)

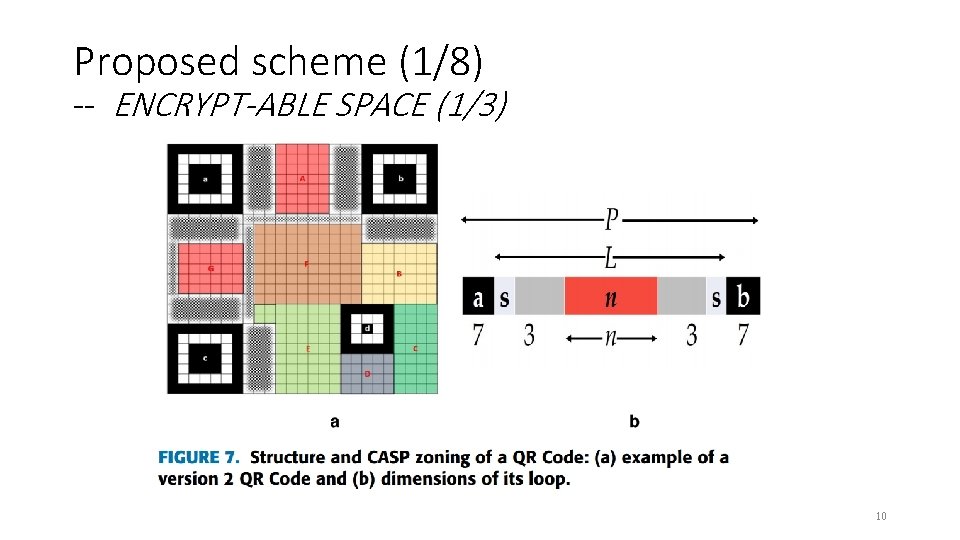
Proposed scheme (1/8) -- ENCRYPT-ABLE SPACE (1/3) 10

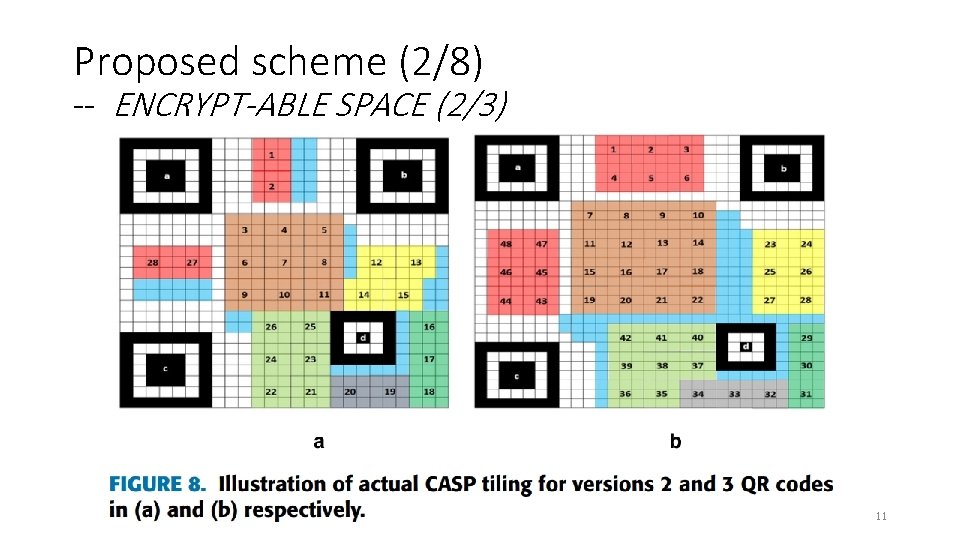
Proposed scheme (2/8) -- ENCRYPT-ABLE SPACE (2/3) 11

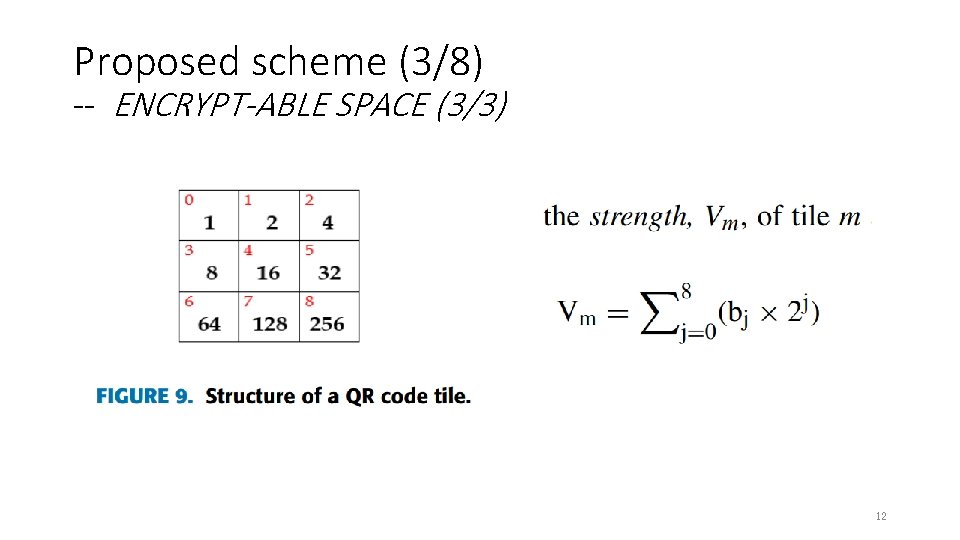
Proposed scheme (3/8) -- ENCRYPT-ABLE SPACE (3/3) 12

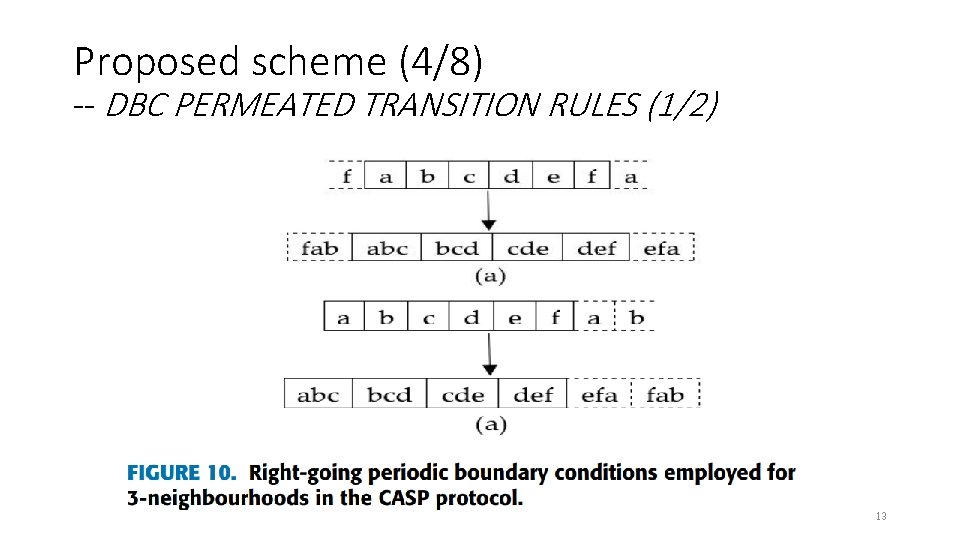
Proposed scheme (4/8) -- DBC PERMEATED TRANSITION RULES (1/2) 13

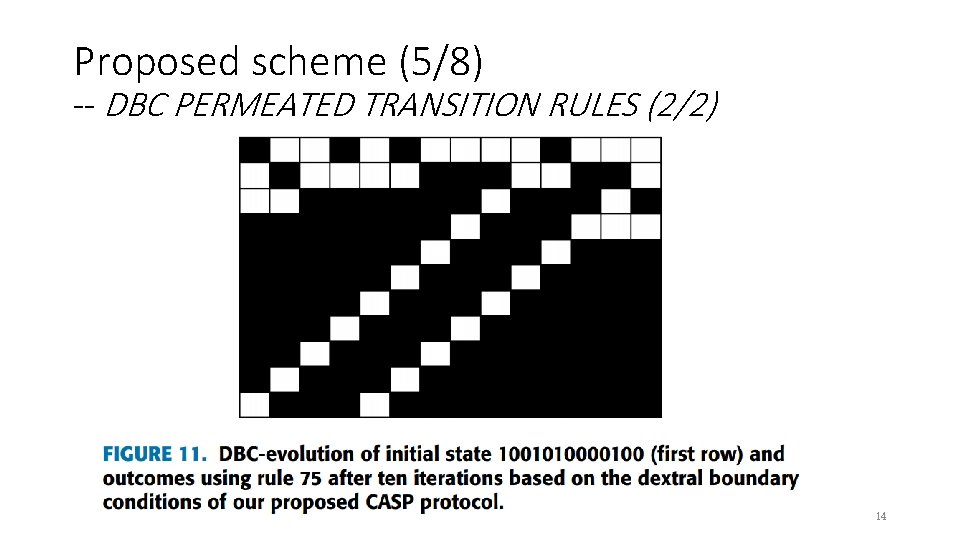
Proposed scheme (5/8) -- DBC PERMEATED TRANSITION RULES (2/2) 14

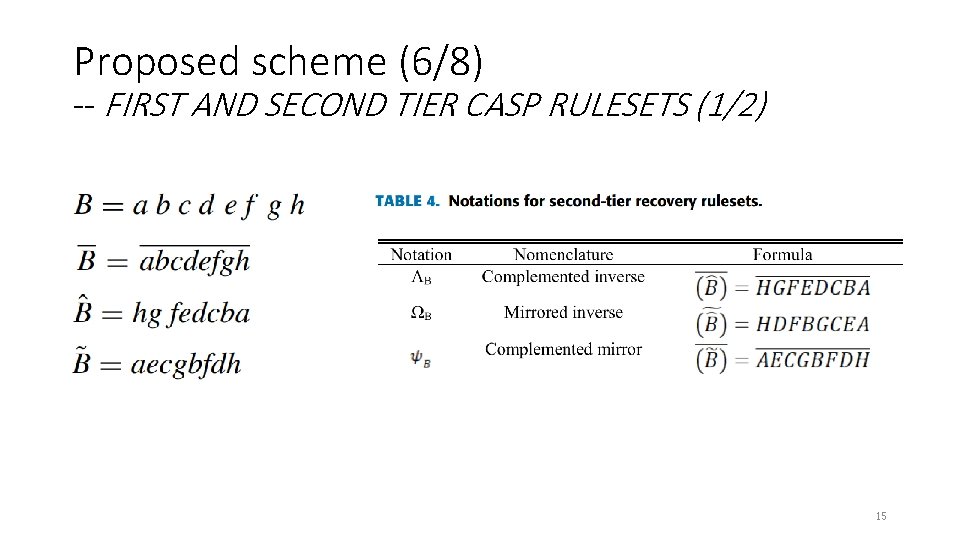
Proposed scheme (6/8) -- FIRST AND SECOND TIER CASP RULESETS (1/2) 15

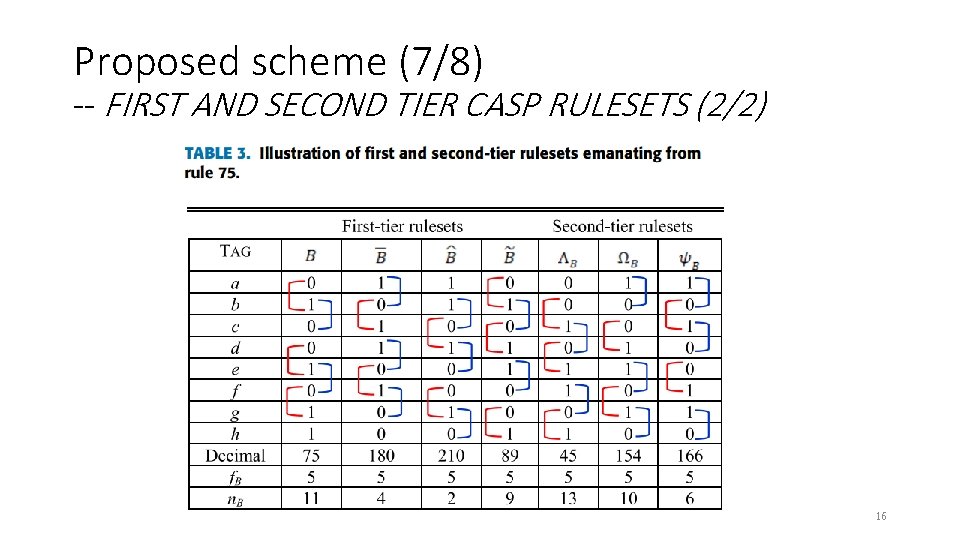
Proposed scheme (7/8) -- FIRST AND SECOND TIER CASP RULESETS (2/2) 16

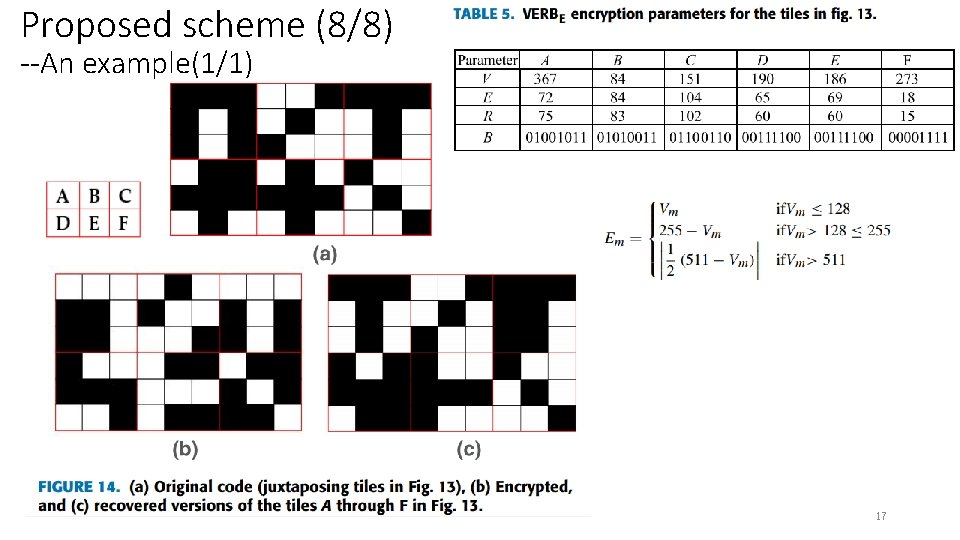
Proposed scheme (8/8) --An example(1/1) 17

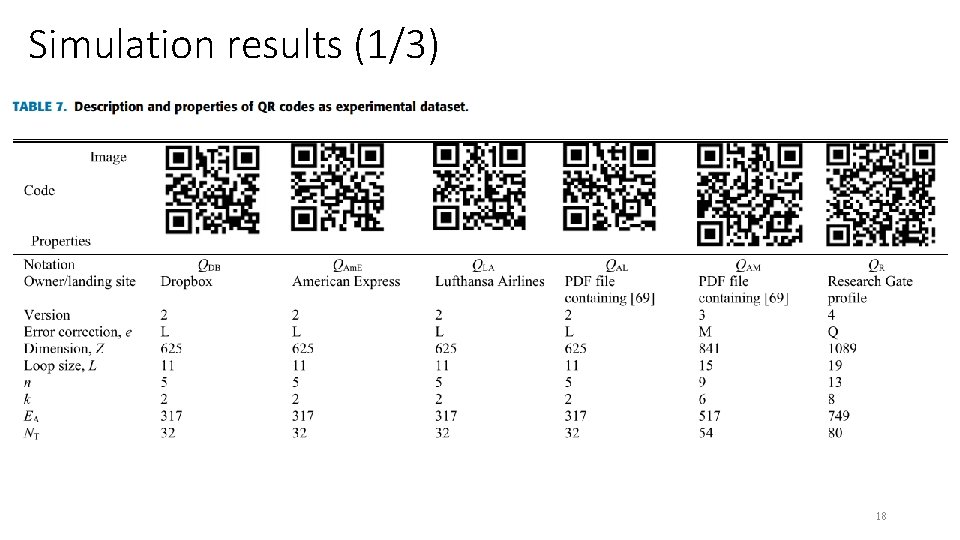
Simulation results (1/3) 18

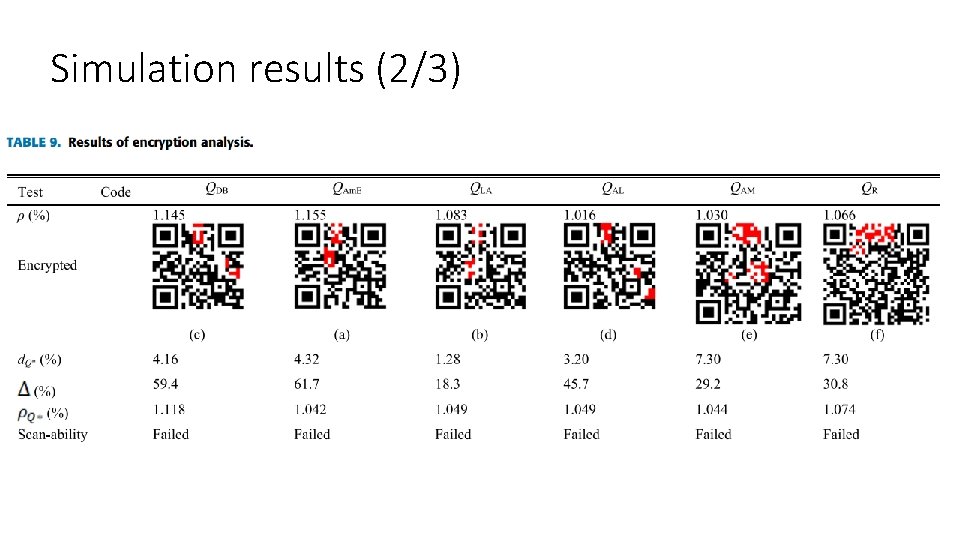
Simulation results (2/3)

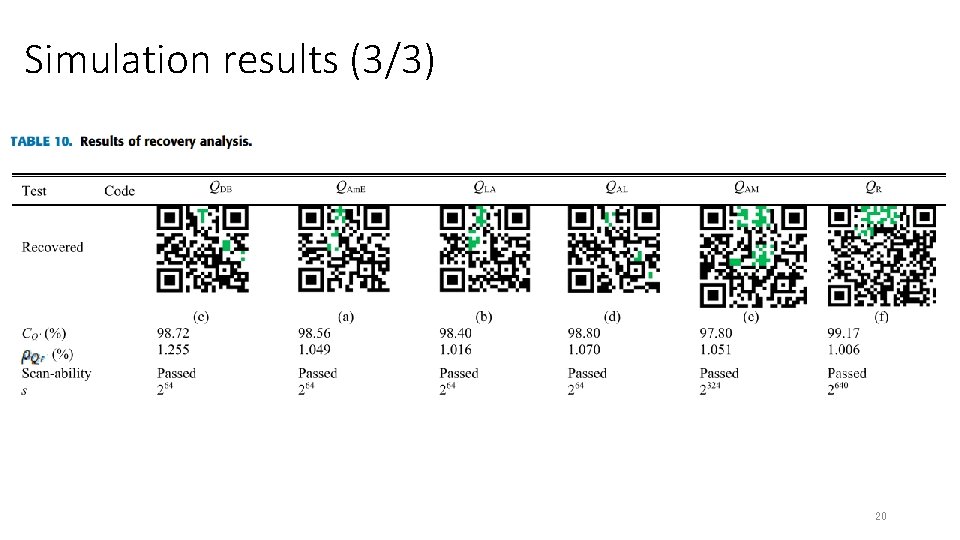
Simulation results (3/3) 20

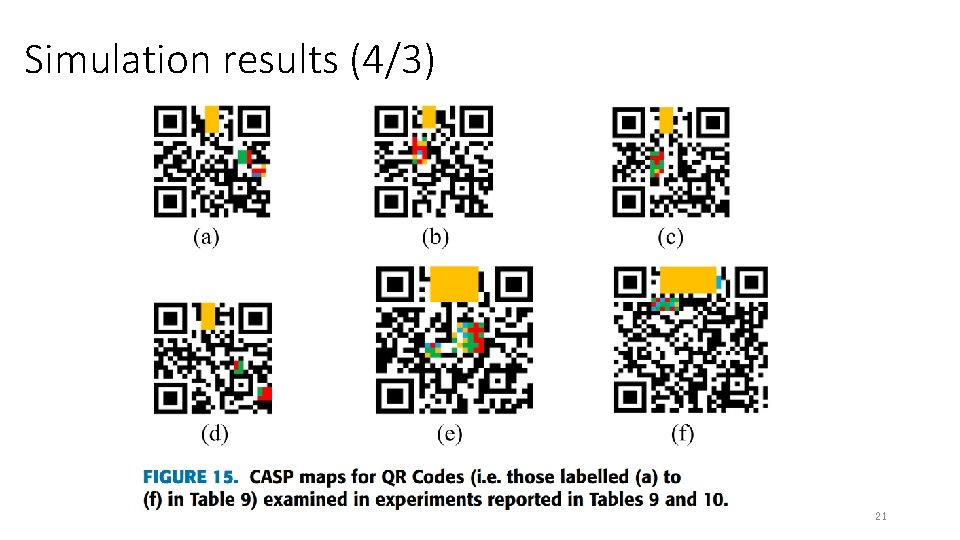
Simulation results (4/3) 21

Conclusions • Retaining the physical appearance. • High security. 22

Comments • A CA-based block SKE method. 23
 Safeguard your business
Safeguard your business Working together to safeguard children’ 2018 summary
Working together to safeguard children’ 2018 summary Sle aro ale examples
Sle aro ale examples Safeguard hosting
Safeguard hosting Safeguard qr code
Safeguard qr code Dr rubina yasmin
Dr rubina yasmin Texas confidentiality laws for minors
Texas confidentiality laws for minors Secondary ethical principles
Secondary ethical principles Safe schools training ferpa answers
Safe schools training ferpa answers Gmc raising concerns flowchart
Gmc raising concerns flowchart Message confidentiality is using
Message confidentiality is using Confidentiality
Confidentiality Conventional encryption and message confidentiality
Conventional encryption and message confidentiality Confidentiality
Confidentiality Confidentiality and privacy controls
Confidentiality and privacy controls Address confidentiality program texas
Address confidentiality program texas Confidentiality disclaimer presentation
Confidentiality disclaimer presentation Confidentiality chapter 5
Confidentiality chapter 5 Potential tension between maintaining confidentiality
Potential tension between maintaining confidentiality Confidentiality in medical ethics
Confidentiality in medical ethics Why is confidentiality important
Why is confidentiality important Confidentiality
Confidentiality Confidentiality statement
Confidentiality statement Confidentiality in ethics
Confidentiality in ethics










































