INFORMATION SECURITY MANAGEMENT LECTURE 8 RISK MANAGEMENT CONTROLLING


















- Slides: 32

INFORMATION SECURITY MANAGEMENT LECTURE 8: RISK MANAGEMENT CONTROLLING RISK You got to be careful if you don’t know where you’re going, because you might not get there. – Yogi Berra

Introduction To keep up with the competition, organizations must design and create a safe environment in which business processes and procedures can function

Qualitative Risk Analysis • • Evaluate opinions, feelings, ideas Scenarios Brainstorming Delphi technique Storyboarding Focus groups Surveys, questionnaires, checklists One-on-one meetings, interviews

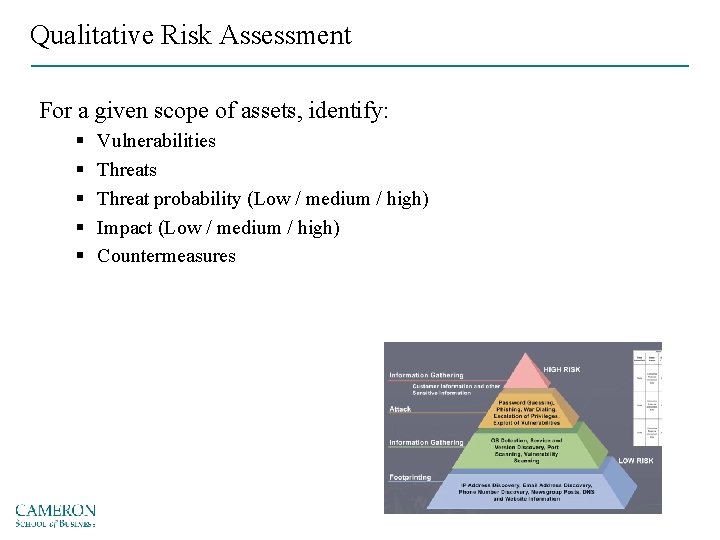
Qualitative Risk Assessment For a given scope of assets, identify: § § § Vulnerabilities Threat probability (Low / medium / high) Impact (Low / medium / high) Countermeasures

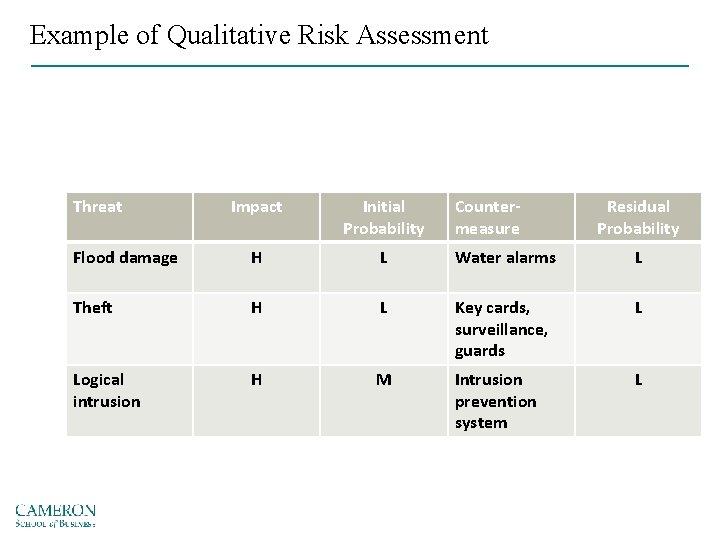
Example of Qualitative Risk Assessment Threat Impact Initial Probability Countermeasure Residual Probability Flood damage H L Water alarms L Theft H L Key cards, surveillance, guards L Logical intrusion H M Intrusion prevention system L

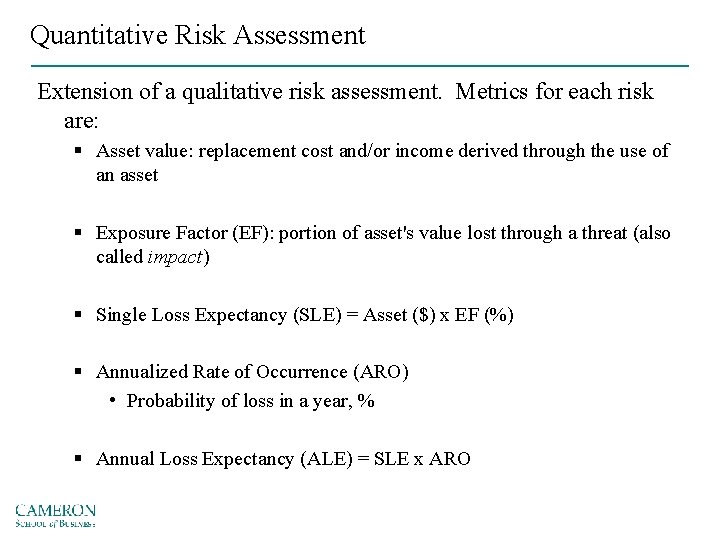
Quantitative Risk Assessment Extension of a qualitative risk assessment. Metrics for each risk are: § Asset value: replacement cost and/or income derived through the use of an asset § Exposure Factor (EF): portion of asset's value lost through a threat (also called impact) § Single Loss Expectancy (SLE) = Asset ($) x EF (%) § Annualized Rate of Occurrence (ARO) • Probability of loss in a year, % § Annual Loss Expectancy (ALE) = SLE x ARO

Example of Quantitative Risk Assesment Theft of a laptop computer, with the data encrypted Asset value: $4, 000 Exposure factor ? SLE, ARO, ALE ?

Example of Quantitative Risk Assesment Dropping a laptop computer and breaking the screen Asset value: $4, 000 Exposure factor ? SLE, ARO, ALE ?

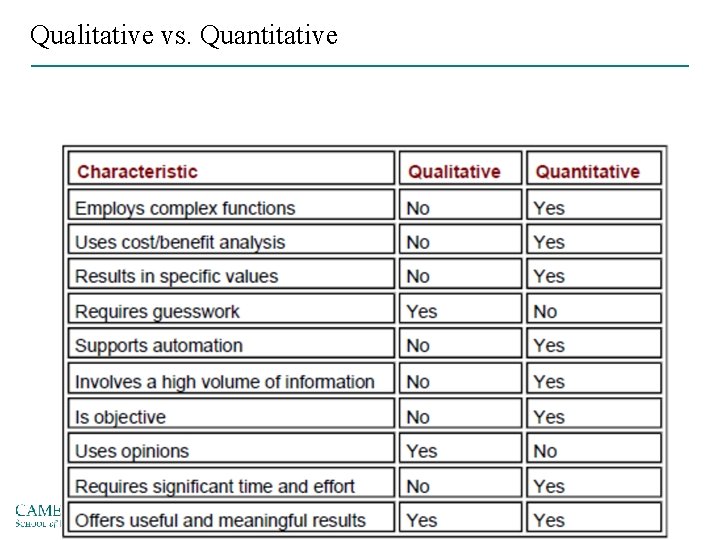
Qualitative vs. Quantitative

Documenting the Results of Risk Assessment • Goals of the risk management process – To identify information assets and their vulnerabilities – To rank them according to the need for protection • In preparing this list, a wealth of factual information about the assets and the threats they face is collected • The final summarized document is the ranked vulnerability risk worksheet

Risk Control Strategies Choose one of four basic strategies: q Avoidance q Transference q Mitigation q Acceptance

Avoidance The risk control strategy that attempts to prevent the exploitation of the vulnerability • Examples

Transference The control approach that attempts to shift the risk to other assets, other processes, or other organizations • Examples

Mitigation The control approach that attempts to reduce the damage caused by exploitation of vulnerability • Types of Mitigation Plans

Acceptance • Do nothing to protect an information asset – To accept the loss when it occurs

Managing Risk • Risk appetite (also known as risk tolerance)

Managing Risk – Residual Risk • Residual Risk is a combined function of: – Threats, vulnerabilities and assets, less the effects of the safeguards in place

Managing Risk – Residual Risk • Once a control strategy has been selected and implemented: – The effectiveness of controls should be monitored and measured on an ongoing basis (remember our discussion on metrics and baselining) • determines effectiveness and accuracy of the residual risk estimate

Managing Risk – Risk Control • Risk control involves selecting one of the four risk control strategies Should the organization ever accept the risk?

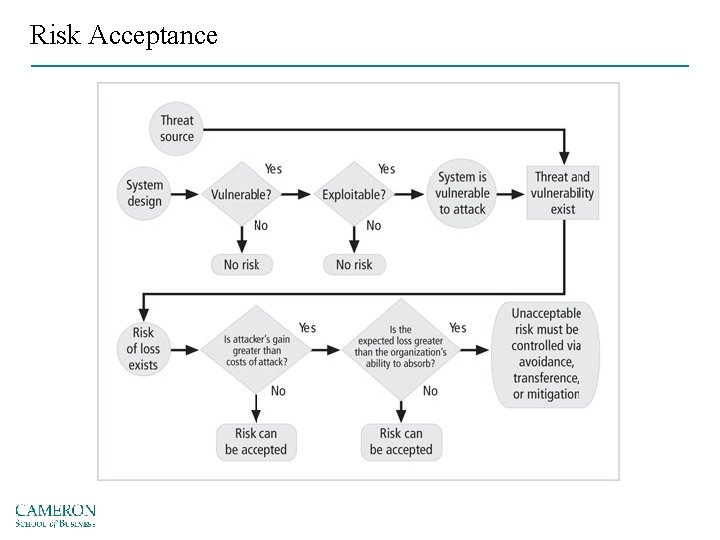
Risk Acceptance Figure 9 -2 Risk-handling action points Source: Course Technology/Cengage Learning

Feasibility and Cost-Benefit Analysis • There a number of ways to determine the advantage or disadvantage of a specific control • The primary means are based on the value of the information assets that it is designed to protect • Economic feasibility – Evaluating the worth of the information assets to be protected and the loss in value if those information assets are compromised

Cost-Benefit Analysis: Cost • Factors that affect the cost of a safeguard – Cost of development or acquisition of hardware, software, and services – Training fees – Cost of implementation – Service and maintenance costs

Cost-Benefit Analysis: Benefit The value to the organization of using controls to prevent losses associated with a specific vulnerability

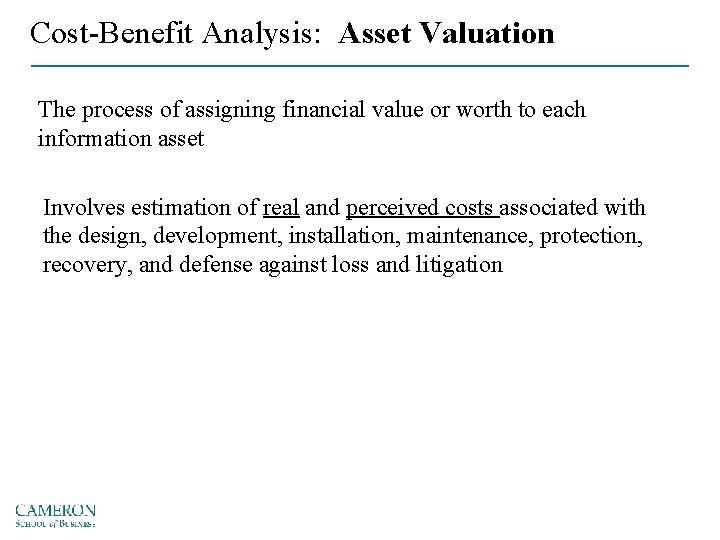
Cost-Benefit Analysis: Asset Valuation The process of assigning financial value or worth to each information asset Involves estimation of real and perceived costs associated with the design, development, installation, maintenance, protection, recovery, and defense against loss and litigation

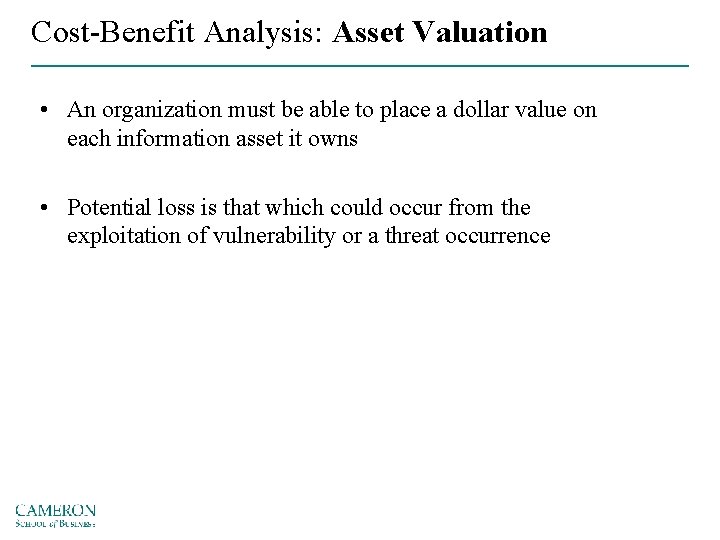
Cost-Benefit Analysis: Asset Valuation • An organization must be able to place a dollar value on each information asset it owns • Potential loss is that which could occur from the exploitation of vulnerability or a threat occurrence

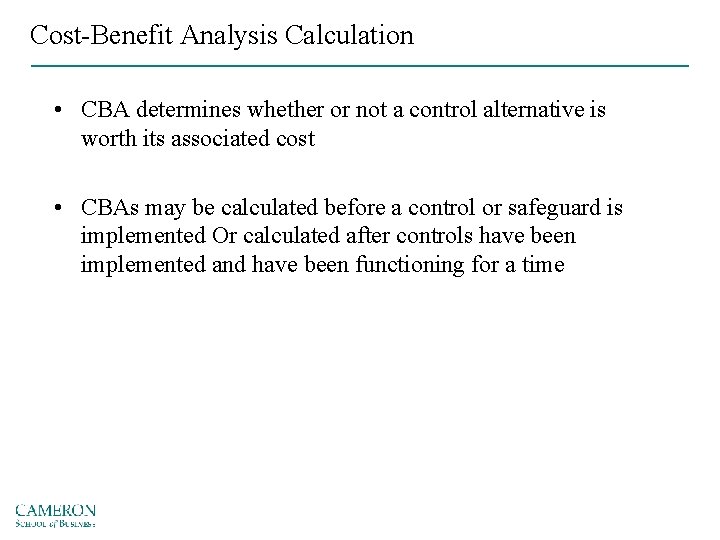
Cost-Benefit Analysis Calculation • CBA determines whether or not a control alternative is worth its associated cost • CBAs may be calculated before a control or safeguard is implemented Or calculated after controls have been implemented and have been functioning for a time

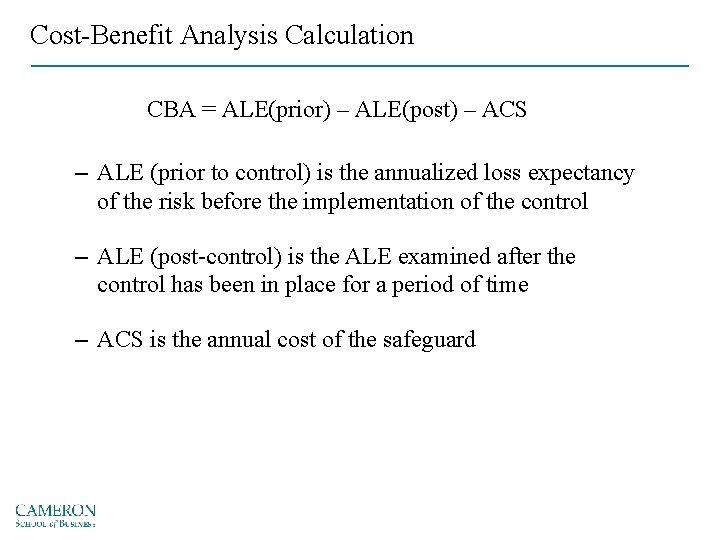
Cost-Benefit Analysis Calculation CBA = ALE(prior) – ALE(post) – ACS – ALE (prior to control) is the annualized loss expectancy of the risk before the implementation of the control – ALE (post-control) is the ALE examined after the control has been in place for a period of time – ACS is the annual cost of the safeguard

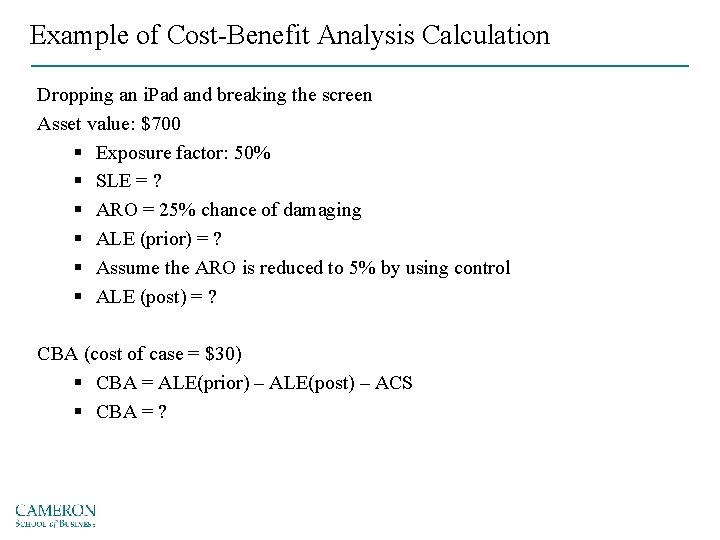
Example of Cost-Benefit Analysis Calculation Dropping an i. Pad and breaking the screen Asset value: $700 § Exposure factor: 50% § SLE = ? § ARO = 25% chance of damaging § ALE (prior) = ? § Assume the ARO is reduced to 5% by using control § ALE (post) = ? CBA (cost of case = $30) § CBA = ALE(prior) – ALE(post) – ACS § CBA = ?

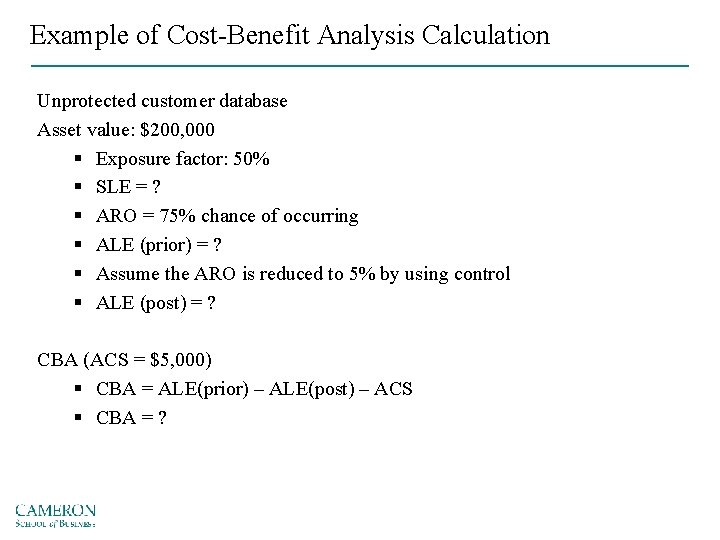
Example of Cost-Benefit Analysis Calculation Unprotected customer database Asset value: $200, 000 § Exposure factor: 50% § SLE = ? § ARO = 75% chance of occurring § ALE (prior) = ? § Assume the ARO is reduced to 5% by using control § ALE (post) = ? CBA (ACS = $5, 000) § CBA = ALE(prior) – ALE(post) – ACS § CBA = ?

Other Methods of Establishing Feasibility • • Organizational feasibility analysis Operational feasibility Technical feasibility Political feasibility

Alternatives to Feasibility Analysis • • • Benchmarking Due care and due diligence Best business practices Gold standard Government recommendations Baseline

Risk Management and Employees “Only two things are infinite, the universe and human stupidity, and I’m not sure about the former. ” - Albert Einstein Types of Employees and Security Knowledge § Those who know § Those who don’t § Those who think they know but don’t