Ad hoc and Sensor Networks Routing protocols Part







- Slides: 40

Ad hoc and Sensor Networks Routing protocols (Part II)

Outline n 4. 1 Routing Challenges and Design Issues in WSNs n 4. 2 Flat Routing n 4. 3 Hierarchical Routing n 4. 4 Location Based Routing n 4. 5 Qo. S Based Routing n 4. 6 Data Aggregation and Convergecast n 4. 7 Data Centric Networking n 4. 8 Zig. Bee n 4. 9 Conclusions 2

Chapter 4. 6 Data Aggregation and Convergecast

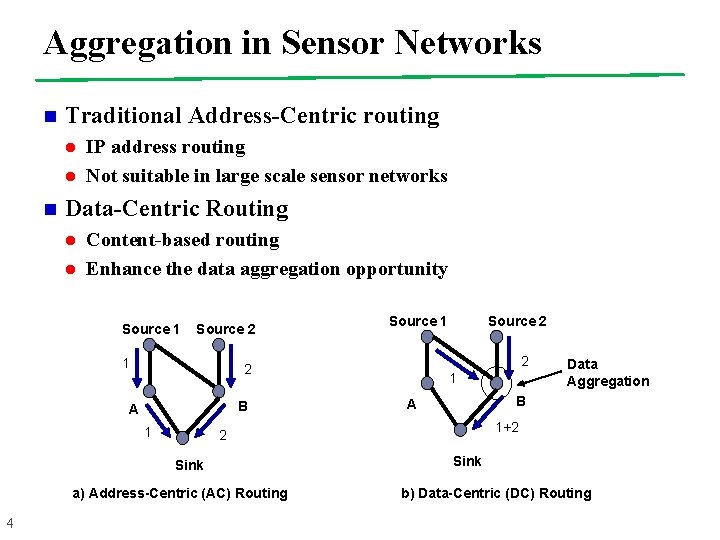
Aggregation in Sensor Networks n Traditional Address-Centric routing l l n IP address routing Not suitable in large scale sensor networks Data-Centric Routing l l Content-based routing Enhance the data aggregation opportunity Source 1 Source 2 1 B 1 Source 2 2 2 A 1 a) Address-Centric (AC) Routing Data Aggregation B A 1+2 2 Sink 4 Source 1 Sink b) Data-Centric (DC) Routing

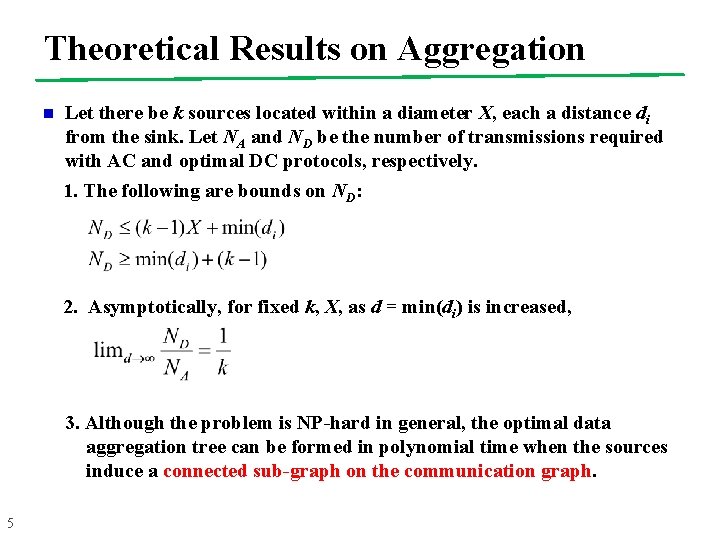
Theoretical Results on Aggregation n Let there be k sources located within a diameter X, each a distance di from the sink. Let NA and ND be the number of transmissions required with AC and optimal DC protocols, respectively. 1. The following are bounds on ND: 2. Asymptotically, for fixed k, X, as d = min(di) is increased, 3. Although the problem is NP-hard in general, the optimal data aggregation tree can be formed in polynomial time when the sources induce a connected sub-graph on the communication graph. 5

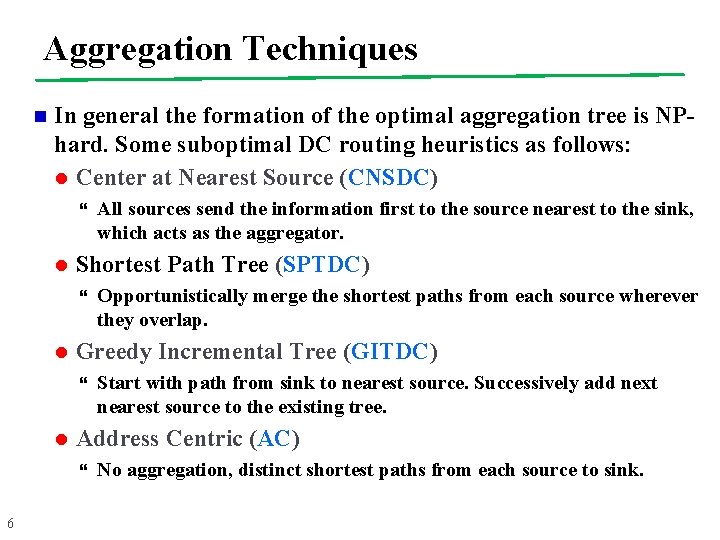
Aggregation Techniques n In general the formation of the optimal aggregation tree is NPhard. Some suboptimal DC routing heuristics as follows: l Center at Nearest Source (CNSDC) l Shortest Path Tree (SPTDC) l Start with path from sink to nearest source. Successively add next nearest source to the existing tree. Address Centric (AC) 6 Opportunistically merge the shortest paths from each source wherever they overlap. Greedy Incremental Tree (GITDC) l All sources send the information first to the source nearest to the sink, which acts as the aggregator. No aggregation, distinct shortest paths from each source to sink.

Performance Study Event-Radius model 7 Random Sources model

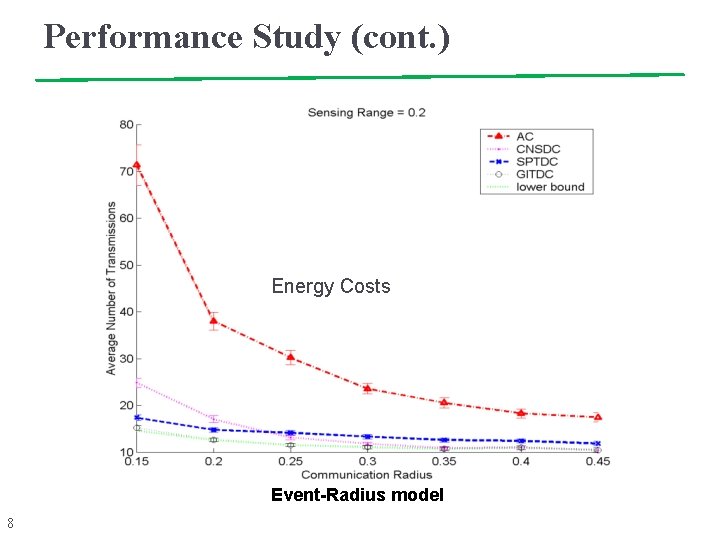
Performance Study (cont. ) Energy Costs Event-Radius model 8

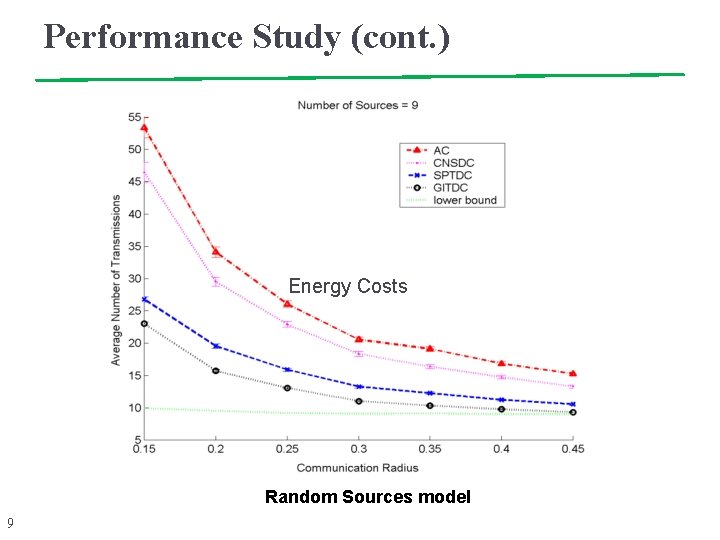
Performance Study (cont. ) Energy Costs Random Sources model 9

Conclusions n Data aggregation can result in significant energy savings for a wide range of operational scenarios. n The gains from aggregation are paid for with potentially higher delay. It should be possible to design routing algorithms for sensor networks in which this tradeoff is made explicitly. 10

Reference n 11 B. Krishnamachari, D. Estrin, and S. B. Wicker, "The impact of data aggregation in wireless sensor networks, " In Proceedings of the 22 nd International Conference on Distributed Computing Systems Workshops (ICDCSW'02), pp. 575 -578, Vienna, Austria, July 02 -05 2002.

Chapter 4. 7 Data centric networking

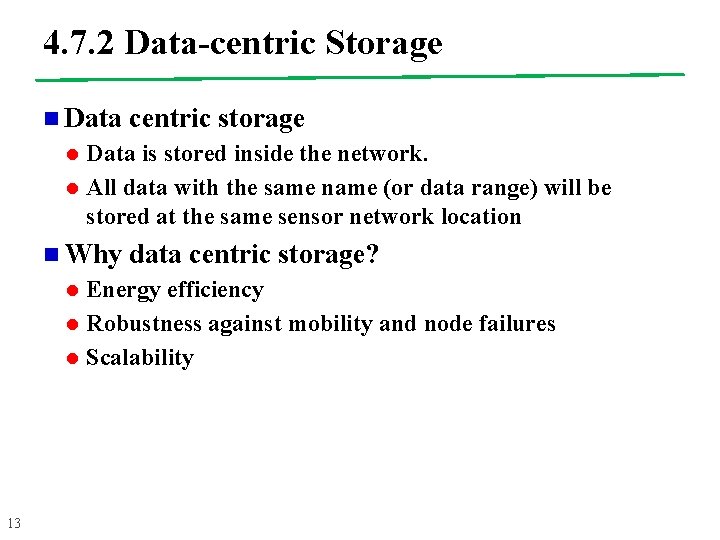
4. 7. 2 Data-centric Storage n Data l l Data is stored inside the network. All data with the same name (or data range) will be stored at the same sensor network location n Why l l l 13 centric storage data centric storage? Energy efficiency Robustness against mobility and node failures Scalability

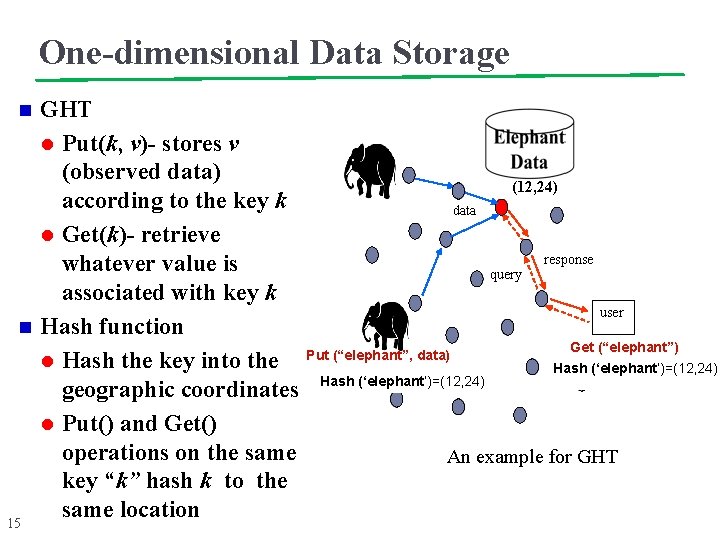
One-dimensional Data Storage n Data-Centric Storage in Sensornets with GHT, a Geographic Hash Table (GHT [Ratnasamy et al. 2003]) l l l 14 Data Storage and Retrieval Perimeter Refresh Protocol Structured Replication

One-dimensional Data Storage n n 15 GHT l Put(k, v)- stores v (observed data) (12, 24) according to the key k data l Get(k)- retrieve response whatever value is query associated with key k user Hash function Get (“elephant”) Put (“elephant”, data) l Hash the key into the Hash (‘elephant’)=(12, 24) geographic coordinates l Put() and Get() operations on the same An example for GHT key “k” hash k to the same location

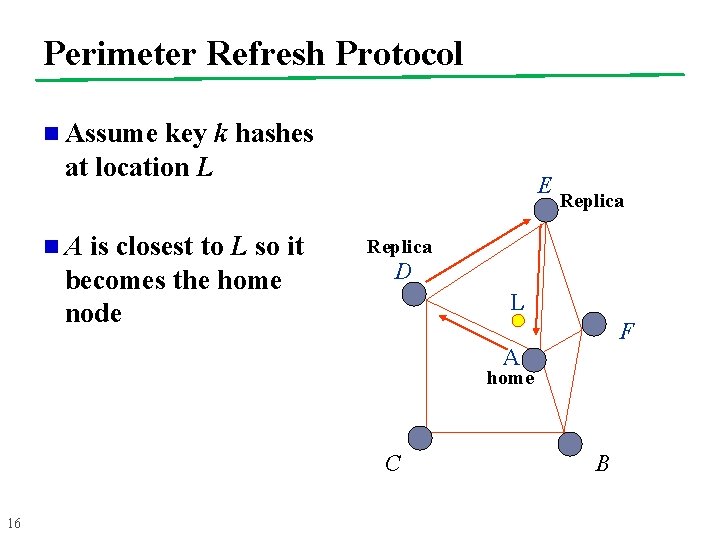
Perimeter Refresh Protocol n Assume key k hashes at location L n. A is closest to L so it becomes the home node E Replica D L F A home C 16 B

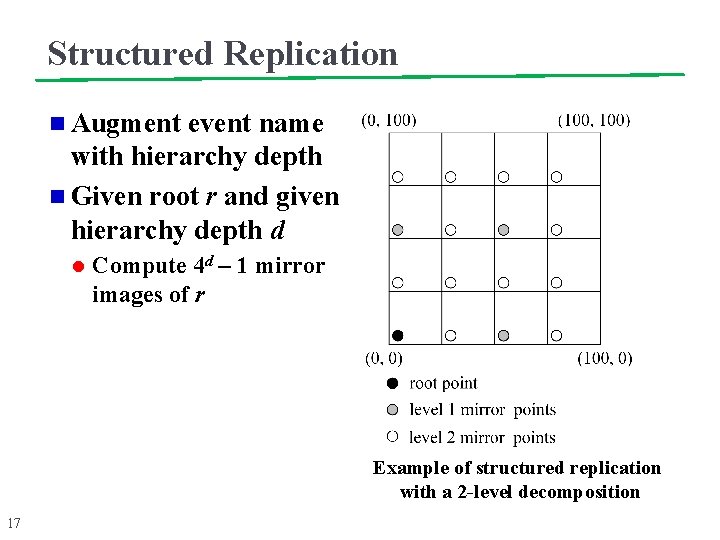
Structured Replication n Augment event name with hierarchy depth n Given root r and given hierarchy depth d l Compute 4 d – 1 mirror images of r Example of structured replication with a 2 -level decomposition 17

Conclusions n Data centric storage entails naming of data and storing data at nodes within the sensor network n GHT uses Perimeter Refresh Protocol and structured replication to enhance robustness and scalability n DCS is useful in large sensor networks and there are many detected events but not all event types are Queried 18

Multi-dimensional Data Storage n Multi-Dimensional Range Queries in Sensor Networks (DIM [Li et al. 2003]) l l l 19 Building Zones Data Insertion Query Propagation

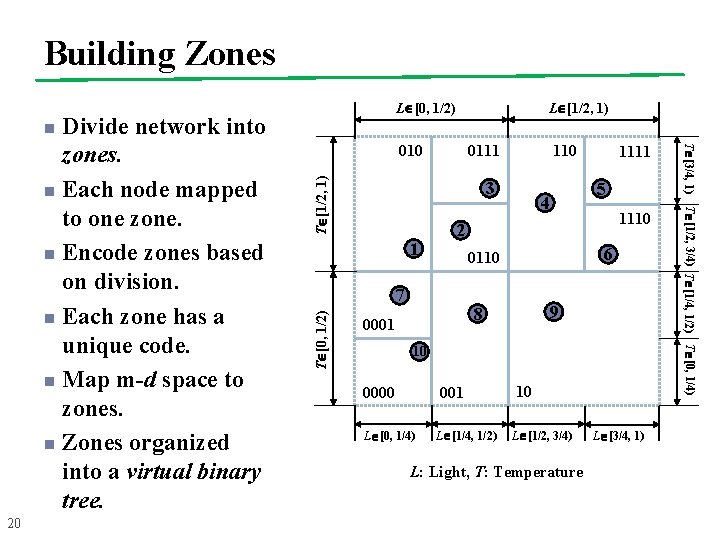
Building Zones Divide network into zones. n Each node mapped to one zone. n Encode zones based on division. n Each zone has a unique code. n Map m-d space to zones. n Zones organized into a virtual binary tree. L [0, 1/2) L [1/2, 1) n T [1/2, 1) 0111 3 1 4 1111 5 1110 2 6 0110 7 T [0, 1/2) 110 9 8 0001 10 0000 001 L [0, 1/4) L [1/4, 1/2) 10 L [1/2, 3/4) L: Light, T: Temperature L [3/4, 1) T [1/2, 3/4) T [1/4, 1/2) T [0, 1/4) 20 010

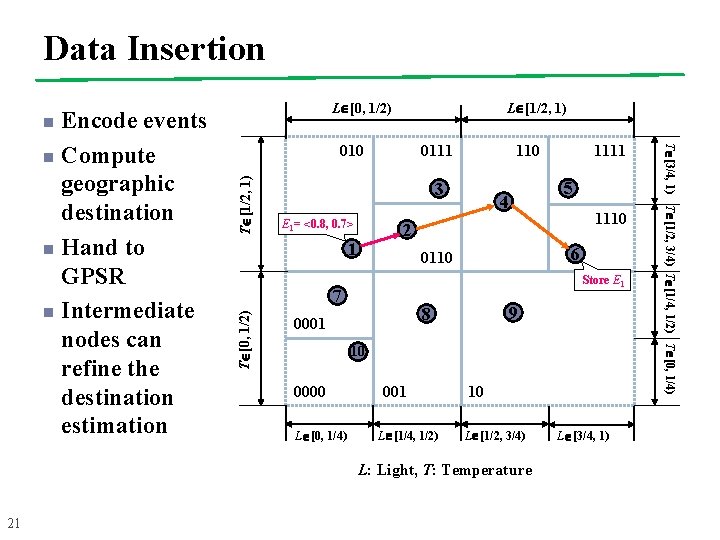
Data Insertion n L [1/2, 1) T [1/2, 1) 010 0111 3 E 1= <0. 8, 0. 7> 1110 2 1 6 0110 Store E 1 7 T [0, 1/2) 5 4 9 8 0001 10 0000 L [0, 1/4) 001 L [1/4, 1/2) 10 L [1/2, 3/4) L: Light, T: Temperature 21 1111 110 L [3/4, 1) T [1/2, 3/4) T [1/4, 1/2) T [0, 1/4) Encode events n Compute geographic destination n Hand to GPSR n Intermediate nodes can refine the destination estimation L [0, 1/2)

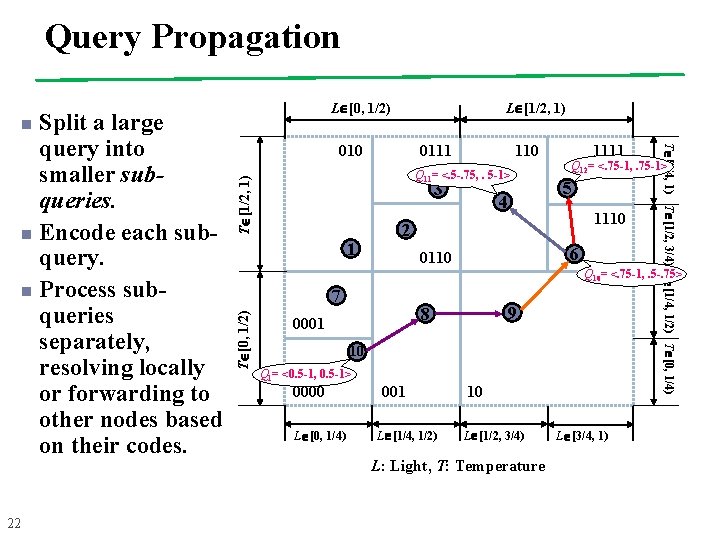
Query Propagation n 22 L [1/2, 1) 010 0111 110 T [1/2, 1) Q 11= <. 5 -. 75, . 5 -1> 3 1 4 1111 Q 12= <. 75 -1, . 75 -1> 5 1110 2 6 0110 T [3/4, 1) T [1/2, 3/4) T [1/4, 1/2) T [0, 1/4) Split a large query into smaller subqueries. n Encode each subquery. n Process subqueries separately, resolving locally or forwarding to other nodes based on their codes. L [0, 1/2) Q 10= <. 75 -1, . 5 -. 75> T [0, 1/2) 7 9 8 0001 10 Q 1= <0. 5 -1, 0. 5 -1> 0000 L [0, 1/4) 001 L [1/4, 1/2) 10 L [1/2, 3/4) L: Light, T: Temperature L [3/4, 1)

Conclusions n DIM resolves multi-dimensional range queries efficiently. n Work that still needs to be done l l l 23 Skewed data distribution These can cause storage and transmission hotspots. Existential queries Whethere exists an event matching a multidimensional range. Node heterogeneity Nodes with larger storage space assert larger-sized zones for themselves.

Chapter 4. 8 Zig. Bee 24

The Zig. Bee Standard n 25 Zig. Bee is a low cost, low power, low complexity, and low data rate wireless communication technology at short range. Based on IEEE 802. 15. 4, it is mainly used as a low data rate monitoring and controlling sensor network

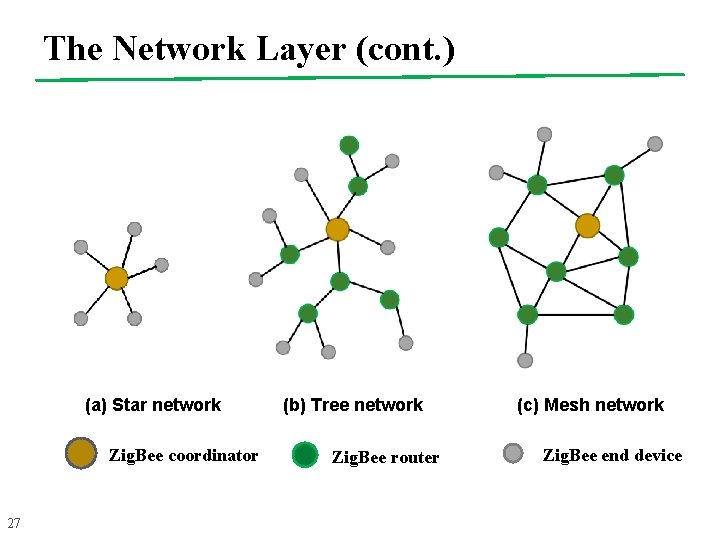
The Network Layer 26 n Zig. Bee identifies three device types l The Zig. Bee coordinator (one in the network) is an FFD managing the whole network l A Zig. Bee router is an FFD with routing capabilities l A Zig. Bee end-device corresponds to a RFD or FFD acting as a simple device n The Zig. Bee network layer supports three types of network configurations: l Star topology l Tree topology l Mesh topology

The Network Layer (cont. ) (a) Star network Zig. Bee coordinator 27 (b) Tree network Zig. Bee router (c) Mesh network Zig. Bee end device

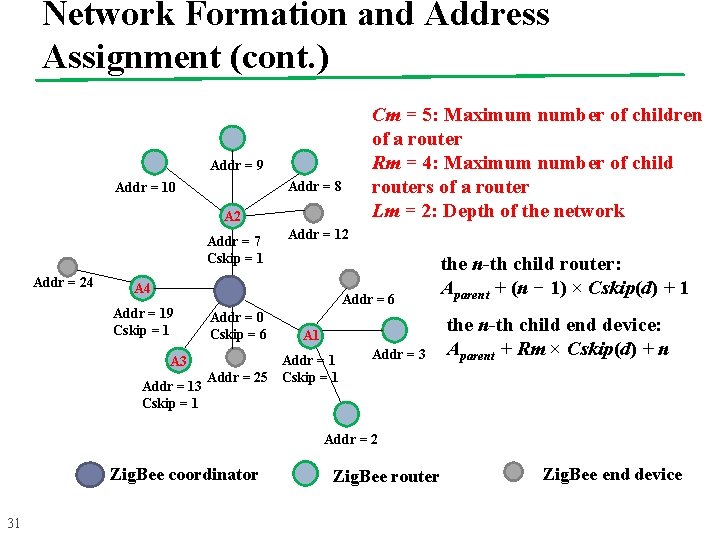
Network Formation and Address Assignment (Tree Network) n Before forming a network, the coordinator determines 28 l Maximum number of children of a router (Cm) l Maximum number of child routers of a router (Rm) l Depth of the network (Lm) l Note that a child of a router can be a router or an end device, so Cm ≥ Rm l The coordinator and routers can each have at most Rm child routers and at most Cm − Rm child end devices

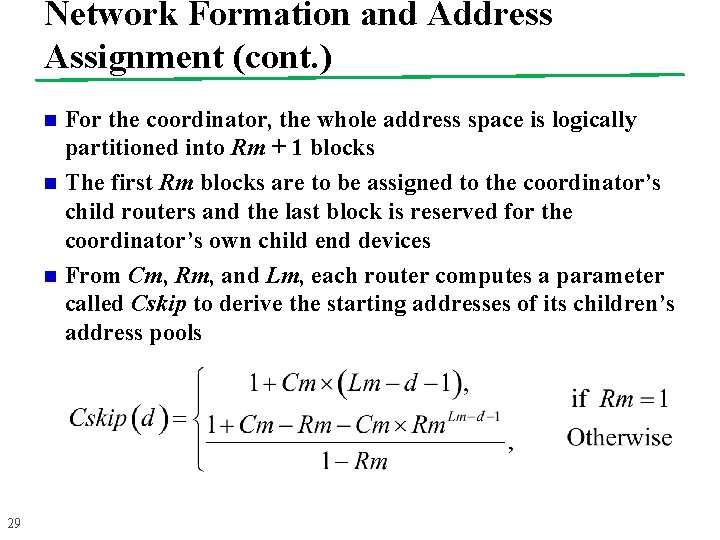
Network Formation and Address Assignment (cont. ) n n n 29 For the coordinator, the whole address space is logically partitioned into Rm + 1 blocks The first Rm blocks are to be assigned to the coordinator’s child routers and the last block is reserved for the coordinator’s own child end devices From Cm, Rm, and Lm, each router computes a parameter called Cskip to derive the starting addresses of its children’s address pools

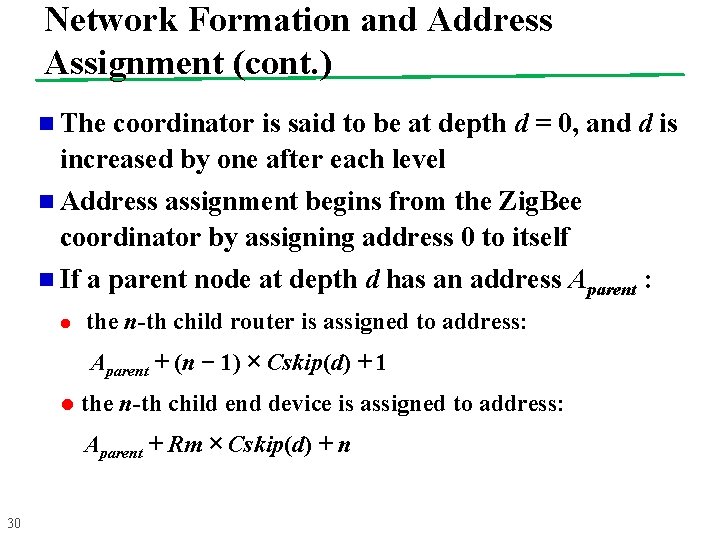
Network Formation and Address Assignment (cont. ) n The coordinator is said to be at depth d = 0, and d is increased by one after each level n Address assignment begins from the Zig. Bee coordinator by assigning address 0 to itself n If a parent node at depth d has an address Aparent : l the n-th child router is assigned to address: Aparent + (n − 1) × Cskip(d) + 1 l the n-th child end device is assigned to address: Aparent + Rm × Cskip(d) + n 30

Network Formation and Address Assignment (cont. ) Addr = 9 Addr = 8 Addr = 10 A 2 Addr = 7 Cskip = 1 Addr = 24 Addr = 12 A 4 Addr = 19 Cskip = 1 A 3 Addr = 13 Cskip = 1 Cm = 5: Maximum number of children of a router Rm = 4: Maximum number of child routers of a router Lm = 2: Depth of the network Addr = 6 Addr = 0 Cskip = 6 A 1 Addr = 25 Cskip = 1 Addr = 3 the n-th child router: Aparent + (n − 1) × Cskip(d) + 1 the n-th child end device: Aparent + Rm × Cskip(d) + n Addr = 2 Zig. Bee coordinator 31 Zig. Bee router Zig. Bee end device

Zig. Bee Routing Protocol n In a Zig. Bee network, the coordinator and routers can directly transmit packets along the tree n When a device receives a packet, it first checks if it is the destination or one of its child end devices is the destination n If so, this device will accept the packet or forward this packet to the designated child. Otherwise, it forwards the packet to its parent 32

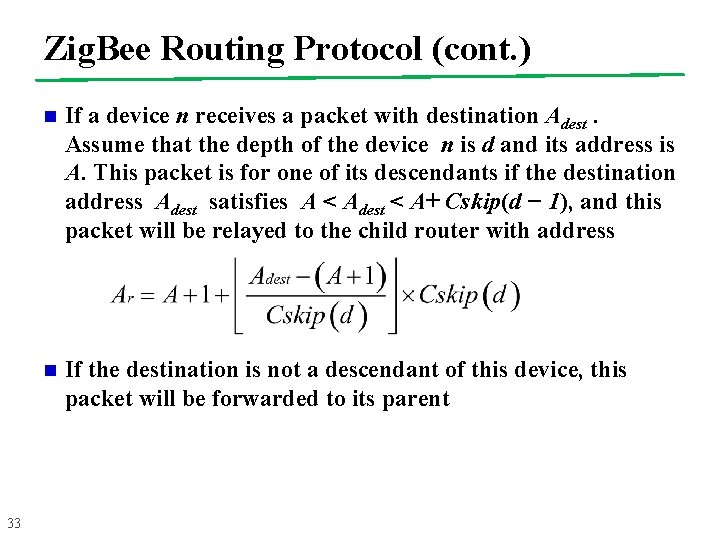
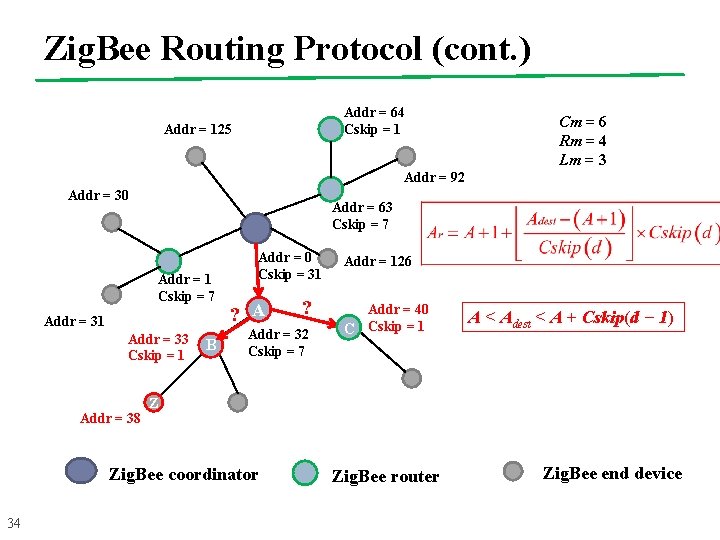
Zig. Bee Routing Protocol (cont. ) 33 n If a device n receives a packet with destination Adest. Assume that the depth of the device n is d and its address is A. This packet is for one of its descendants if the destination address Adest satisfies A < Adest < A+ Cskip(d − 1), and this packet will be relayed to the child router with address n If the destination is not a descendant of this device, this packet will be forwarded to its parent

Zig. Bee Routing Protocol (cont. ) Addr = 64 Cskip = 1 Addr = 125 Cm = 6 Rm = 4 Lm = 3 Addr = 92 Addr = 30 Addr = 63 Cskip = 7 Addr = 1 Cskip = 7 Addr = 31 Addr = 33 Cskip = 1 Addr = 38 B Addr = 0 Cskip = 31 ? A Addr = 32 Cskip = 7 Addr = 40 C Cskip = 1 A < Adest < A + Cskip(d − 1) Z Zig. Bee coordinator 34 ? Addr = 126 Zig. Bee router Zig. Bee end device

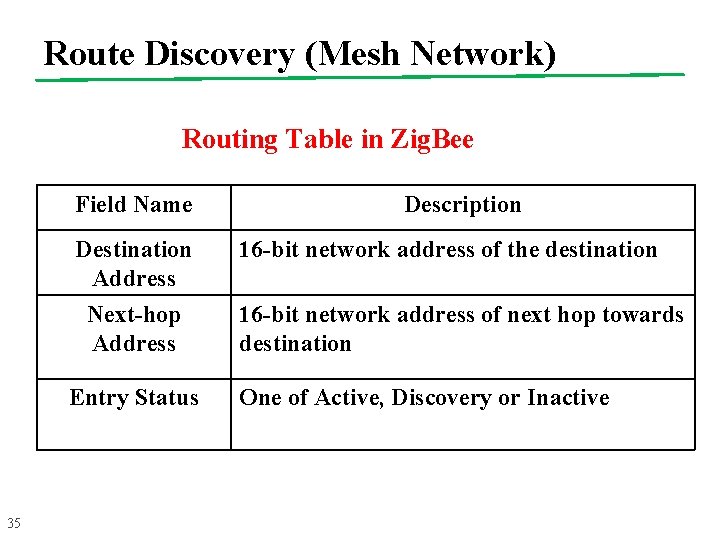
Route Discovery (Mesh Network) Routing Table in Zig. Bee Field Name 35 Description Destination Address Next-hop Address 16 -bit network address of the destination Entry Status One of Active, Discovery or Inactive 16 -bit network address of next hop towards destination

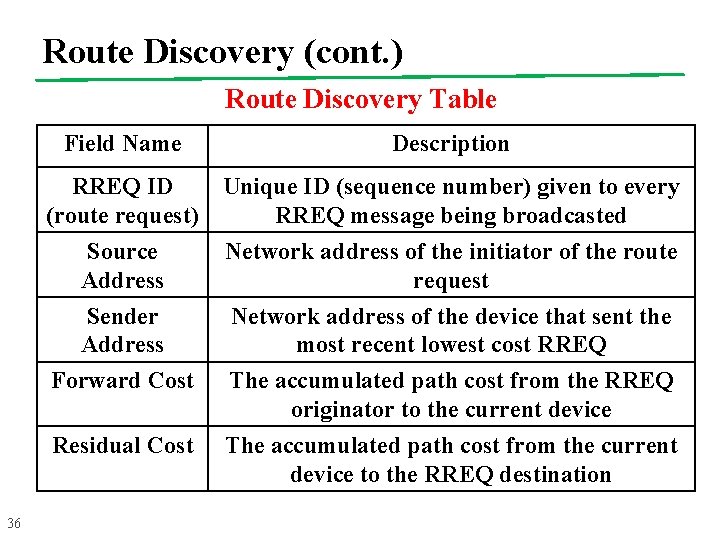
Route Discovery (cont. ) Route Discovery Table 36 Field Name Description RREQ ID (route request) Unique ID (sequence number) given to every RREQ message being broadcasted Source Address Network address of the initiator of the route request Sender Address Forward Cost Network address of the device that sent the most recent lowest cost RREQ The accumulated path cost from the RREQ originator to the current device Residual Cost The accumulated path cost from the current device to the RREQ destination

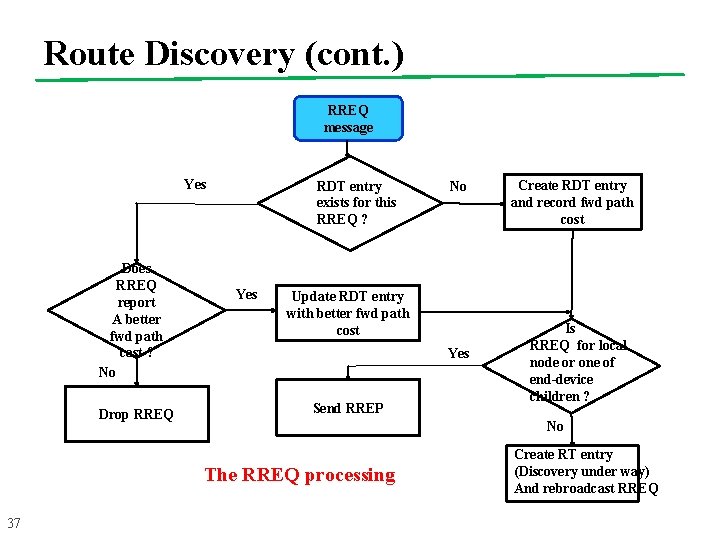
Route Discovery (cont. ) RREQ message Yes Does RREQ report A better fwd path cost ? No Drop RREQ RDT entry exists for this RREQ ? Yes Update RDT entry with better fwd path cost Yes Send RREP Create RDT entry and record fwd path cost Is RREQ for local node or one of end-device children ? No The RREQ processing 37 No Create RT entry (Discovery under way) And rebroadcast RREQ

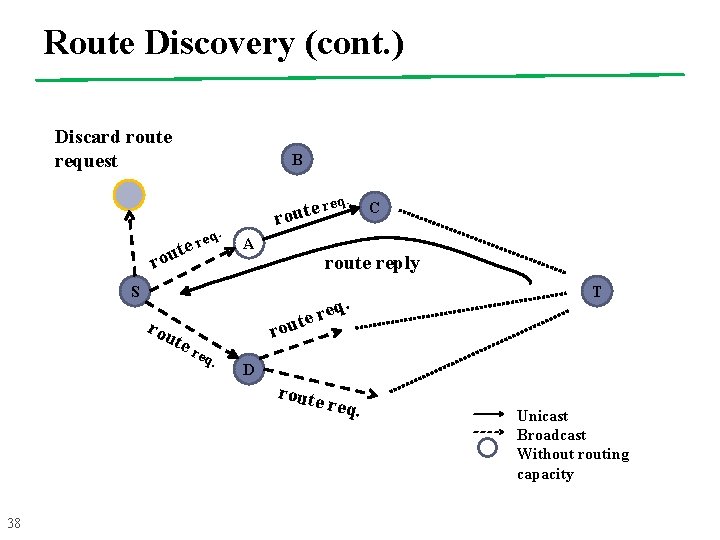
Route Discovery (cont. ) Discard route request B eq. r e t rou er t u o r A route reply S rou te r eq. T D route 38 C req. Unicast Broadcast Without routing capacity

References 39 n P. Baronti, P. Pillai, V. Chook, S. Chessa, and F. Gotta, A. and. Fun Hu. Wireless sensor networks: a survey on the state of the art and the 802. 15. 4 and zigbee standards. Communication Research Centre, UK, May 2006. n J. Bruck, J. Gao and A. A. Jiang, “MAP: Medial Axis Based Geometric Routing in Sensor Network, ” in Proceedings of ACM Mobi. Com, 2005. n Q. Fang, J. Gao, L. Guibas, V. de Silva, and L. Zhang. GLIDER: Gradient landmark-based distributed routing for sensor networks. In Proc. of the 24 th Conference of the IEEE Communication Society (INFOCOM’ 05), March 2005. n B. Chen, K. Jamieson, H. Balakrishnan, and R. Morris. Span: An energyefficient coordination algorithm for topology maintenance in ad hoc wireless networks. In International Conference on Mobile Computing and Networking (Mobi. Com 2001), pages 85– 96, Rome, Italy, July 2001. n Y. Xu, J. Heidemann, and D. Estrin. Geography-informed energy conservation for ad hoc routing. In Proceedings of the ACM/IEEE International Conference on Mobile Computing and Networking, pages 70– 84, Rome, Italy, July 2001.

Conclusions n n 40 Routing in sensor networks is a new area of research, with a limited but rapidly growing set of research results We highlight the design trade-offs between energy and communication overhead savings in some of the routing paradigm, as well as the advantages and disadvantages of each routing technique Overall, the routing techniques are classified based on the network structure into four categories: flat, hierarchical, and location-based routing, and Qo. S based routing protocols. Although many of these routing techniques look promising, there are still many challenges that need to be solved in sensor networks