Access Control Lists ACL AccessList Overview 4 A











- Slides: 14

Access Control Lists (ACL)

Access-List Overview 4 A Filter through which all traffic must pass 4 Used to Permit or Deny Access to Network 4 Provides Security 4 Bandwidth Management 4 Come in two flavors – STANDARD AND EXTENDED

What is an Access-List 4 A List of Criteria to which all Packets are compared. – Is this Packet from Network 10. 5. 2. 0 • Yes - Forward the Packet • No - Check with Next Statement – Is this a Telnet Protocol Packet from 25. 0. 0 • Yes - Forward the Packet • No - Check Next Statement – Deny All Other Traffic

How an Access-List Works 4 Packets are compared to Each Statement in an Access-list SEQUENTIALLY - From the Top Down. 4 The sooner a decision is made the better. 4 Well written Access-lists take care of the most abundant type of traffic first. 4 All Access-lists End with an Implicit Deny All statement

Standard Access Lists 4 Are given a # from 1 -99 4 Filtering based only on Source Address 4 Should be applied closest to the Destination

Extended Access-lists 4 Are given a # from 100 -199 4 Much more flexible and complex 4 Can filter based on: – Source address – Destination address – Session Layer Protocol (ICMP, TCP, UDP. . ) – Port Number (80 http, 23 telnet…) 4 Should be applied closest to the Source

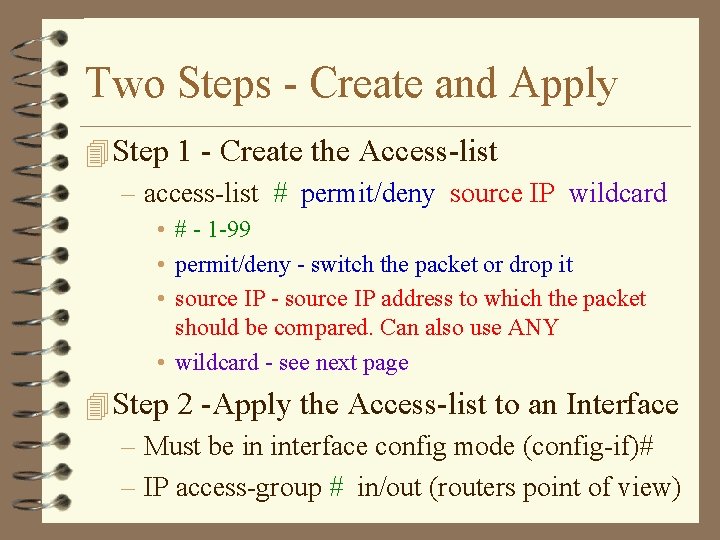
Two Steps - Create and Apply 4 Step 1 - Create the Access-list – access-list # permit/deny source IP wildcard • # - 1 -99 • permit/deny - switch the packet or drop it • source IP - source IP address to which the packet should be compared. Can also use ANY • wildcard - see next page 4 Step 2 -Apply the Access-list to an Interface – Must be in interface config mode (config-if)# – IP access-group # in/out (routers point of view)

Wildcards 4 Allows you to indicate a Range of IP addresses 4 Two Values are Used: – 0 = Must Match Exactly – 1 = Does Not Matter

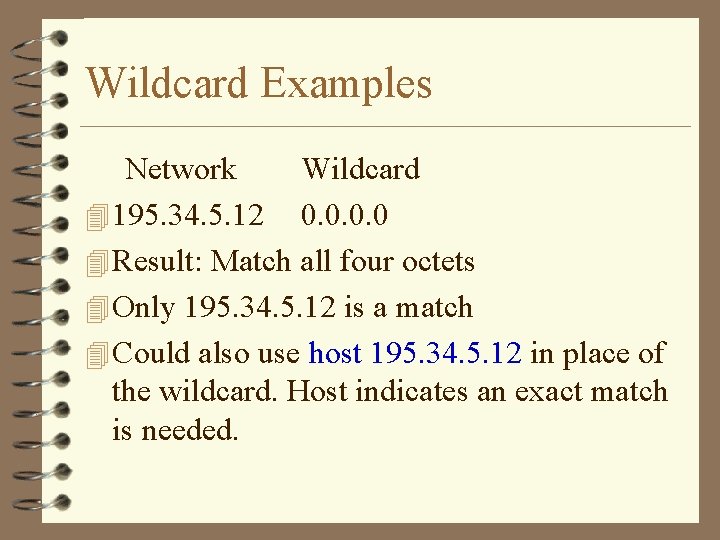
Wildcard Examples Network Wildcard 4 195. 34. 5. 12 0. 0 4 Result: Match all four octets 4 Only 195. 34. 5. 12 is a match 4 Could also use host 195. 34. 5. 12 in place of the wildcard. Host indicates an exact match is needed.

Wildcard Examples 4 Network Wildcard 4 172. 16. 10. 0. 0. 255 4 Result: Match the first three octets exactly but ignore the last octet. 4 172. 16. 10. 0 thru 172. 16. 10. 255 is a match since the last octet does not matter.

Implementing Access-lists 4 Remember the Implicit Deny All at the end of each access-list. 4 Two Approaches: – 1. List the traffic you know you want to permit – Deny all other traffic – 2. List the traffic you want to deny – Permit all other traffic (permit any)

Implementing Access-lists 4 You cannot selectively add or remove statements from an Access-list 4 Typically modifications are made in a text editor and then pasted to the router as a new access-list. The new access list is then applied and the old one removed 4 Document your Access-list – After each line indicate exactly what that line is supposed to do.

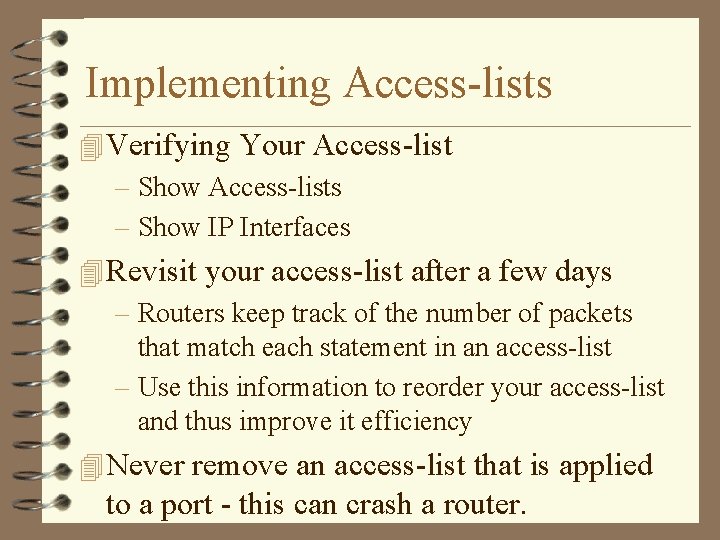
Implementing Access-lists 4 Verifying Your Access-list – Show Access-lists – Show IP Interfaces 4 Revisit your access-list after a few days – Routers keep track of the number of packets that match each statement in an access-list – Use this information to reorder your access-list and thus improve it efficiency 4 Never remove an access-list that is applied to a port - this can crash a router.

Summary: Access-Lists 4 Are Created and then Applied to an interface 4 Are Implemented Sequentially- Top Down 4 End with an implicit Deny ALL statement 4 #1 -99 Standard and # 100 -199 Extended 4 Standard - source address only 4 Extended - source, destination, protocol, port