Windows Security Archana Galipalli Agenda Windows Security and














- Slides: 21

Windows Security -- Archana Galipalli

Agenda § § § § § Windows Security and CLR Implementing Windows Security for IIS Configuring Security settings DEMO- By pass traverse checking Token, Principal and Identity objects DEMO- Accessing Token DEMO- User Roles Runtime security through windows

Why windows security? § To make application more secure § Configuring the system level settings along with application level settings

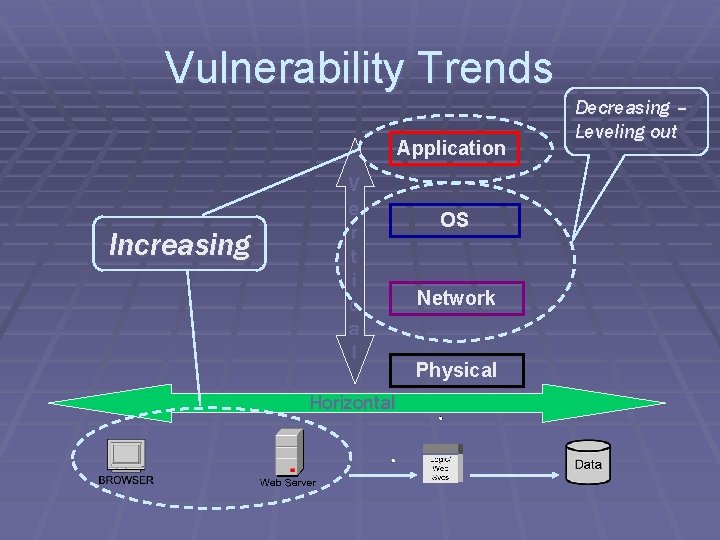
Vulnerability Trends Application Increasing V e r t i c a l Horizontal OS Network Physical Decreasing – Leveling out

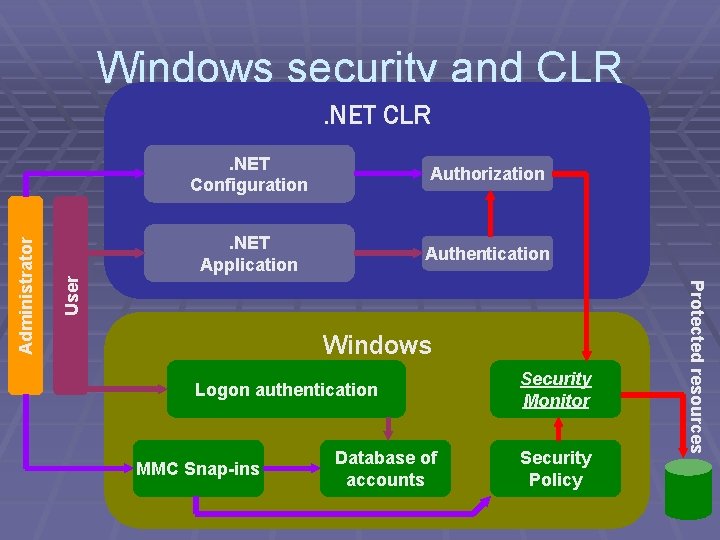
Windows security and CLR Authorization . NET Application Authentication User . NET Configuration Windows Logon authentication MMC Snap-ins Database of accounts Security Monitor Security Policy Protected resources Administrator . NET CLR

Implementing Windows Security § Minimize services § Define the user account for anonymous access § Secure the file system § Apply specific registry settings

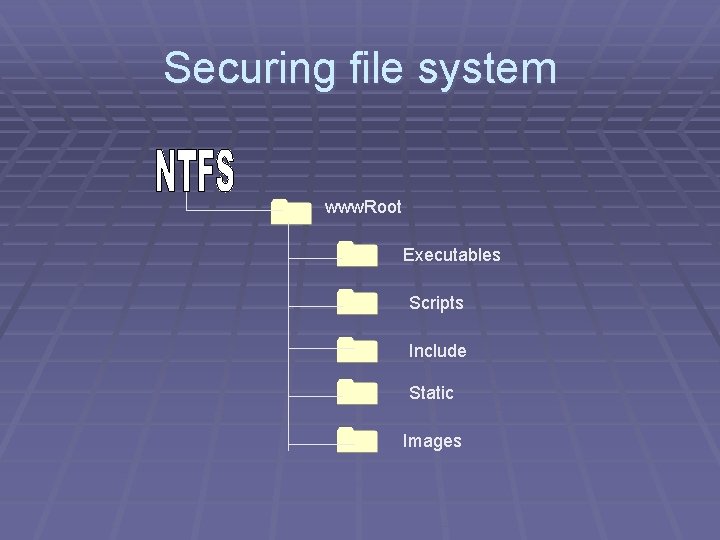
Securing file system www. Root Executables Scripts Include Static Images

Specific registry settings Syn. Attack. Protect register value to HKLMSystemCurrentcontrolsetServices TcpipParametersSyn. Attack. Protect § TCPMax. Ports. Exhausted § TCPMax. Half. Opened. Retired

Configuring Security settings § Configuring account policies • Password policy • Account lock out policy § Configuring Local Policies • Audit policy • User Rights Assignment • Security Options

Walkthrough to configure the Account policies and Local policies….

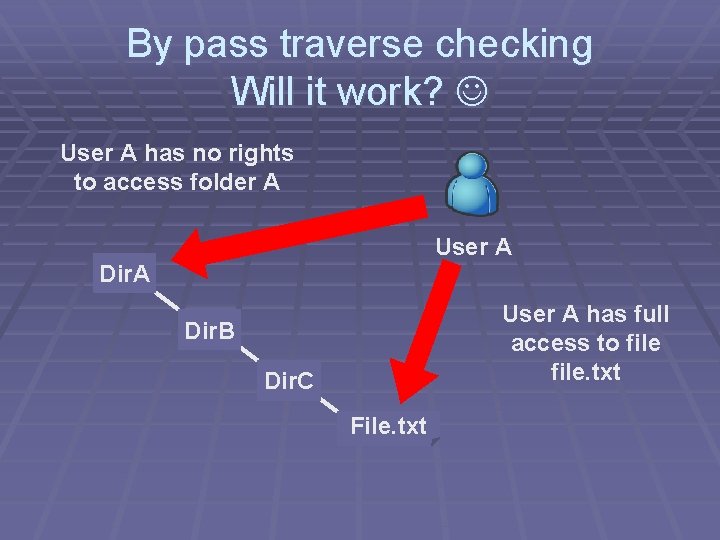
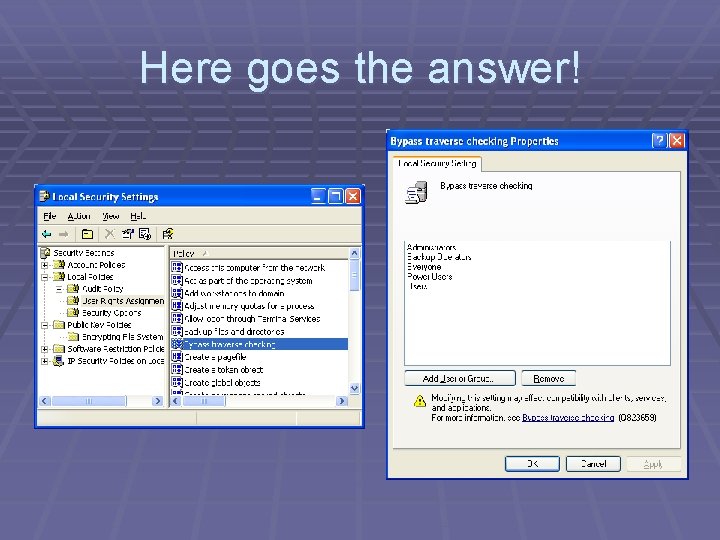
By pass traverse checking Will it work? User A has no rights to access folder A User A Dir. A User A has full access to file. txt Dir. B Dir. C File. txt

Here goes the answer!

By pass traverse checking § Is user checked for permissions? ? ?

Token § Token unifies data about identity: § User’s SID § Group SID § Privileges § Every process has own token representing principal § First process are running on behalf of the SYSTEM account when computer is started § When user logs on then shell is running in user mode under specific principal § Win. Logon. exe (SYSTEM) starts user’s shell with Create. Process. As. User method => then user’s token is propagated to other processes

What are Principal and Identity objects? § Windows. Identity: This object encapsulates the § § § Windows login user name and the type of protocol adopted for authentication by Windows Generic. Identity: also stores information about a user, but is used when an application needs to implement custom logon. Generic. Principal: This object encapsulates the identity object and the role Windows. Principal: also stores identity and the Windows group membership of the user.

User Roles § Acquiring User’s name. § Displaying all the roles in which user is a member.

Accessing token § Is token in Windows. Identity? § Acquiring token from running process § User’s name and SID from Get. Token. Information

Runtime security through windows § Increase Assembly Trust § Adjust Zone Security § Evaluate Assembly § Create Deployment Package § Reset All Policy Levels

Walkthrough to configure the runtime security policies….

References § Windows Security 2 nd Edition by Ben Smith and Brain Komar. § http: //pluralsight. com/wiki/default. aspx/Keit h. Guide. Book/How. To. Get. AToken. For. AUser. html § http: //www. skilldrive. com/Windows. Sec. Int. E ng. Out. zip

Questions?