William Stallings Data and Computer Communications Chapter 12
















- Slides: 34

William Stallings Data and Computer Communications Chapter 12 Congestion in Data Networks

What Is Congestion? z Congestion occurs when the number of packets being transmitted through the network approaches the packet handling capacity of the network z Congestion control aims to keep number of packets below level at which performance falls off dramatically z Data network is a network of queues z Generally 80% utilization is critical z Finite queues mean data may be lost

Congestion Control vs Flow Control z Congestion control is a global issue – involves every router and host within the subnet z Flow control – scope is point-to-point; involves just sender and receiver. 3

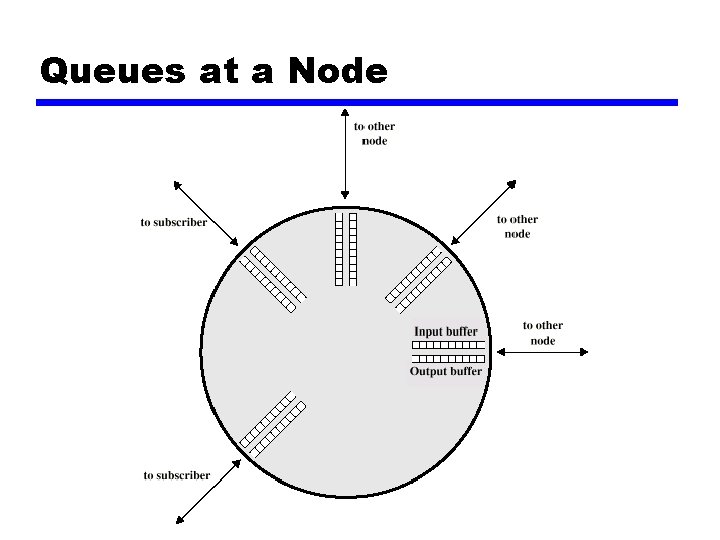
Queues at a Node

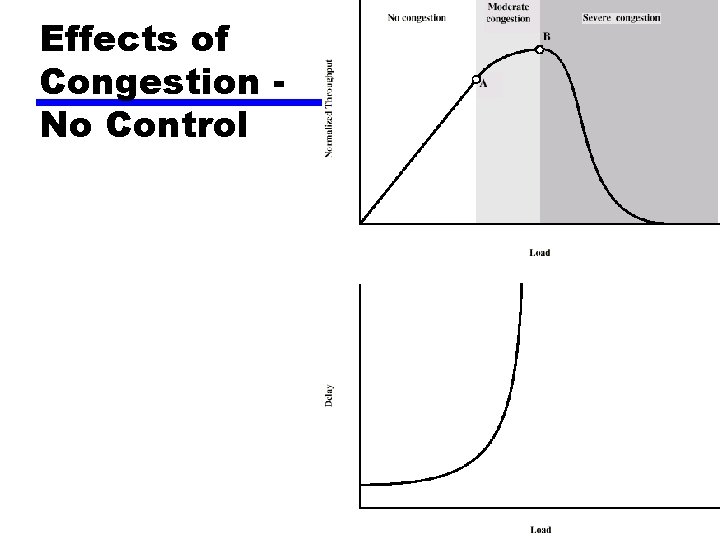
Effects of Congestion z Packets arriving are stored at input buffers z Routing decision made z Packet moves to output buffer z Packets queued for output transmitted as fast as possible y. Statistical time division multiplexing z If packets arrive to fast to be routed, or to be output, buffers will fill z Can discard packets z Can use flow control y. Can propagate congestion through network

Interaction of Queues

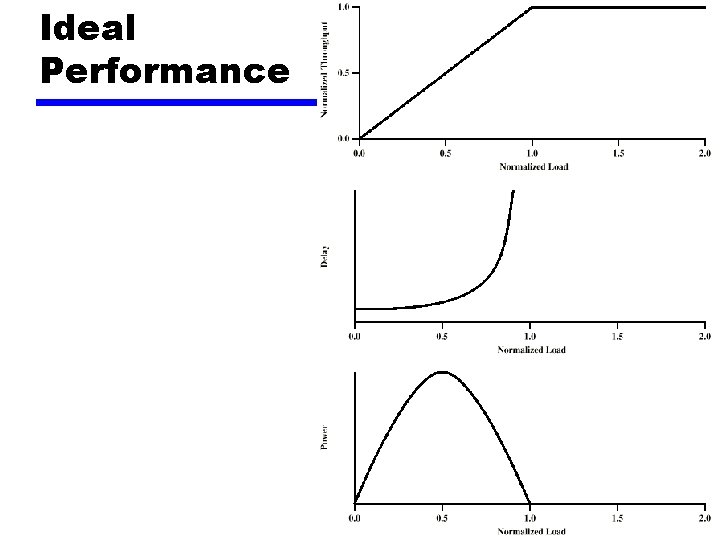
Ideal Performance

Practical Performance z Ideal assumes infinite buffers and no overhead z Buffers are finite z Overheads occur in exchanging congestion control messages

Effects of Congestion No Control

Factors that Cause Congestion z Packet arrival rate exceeds the outgoing link capacity. z Insufficient memory to store arriving packets z Bursty traffic z Slow processor 10

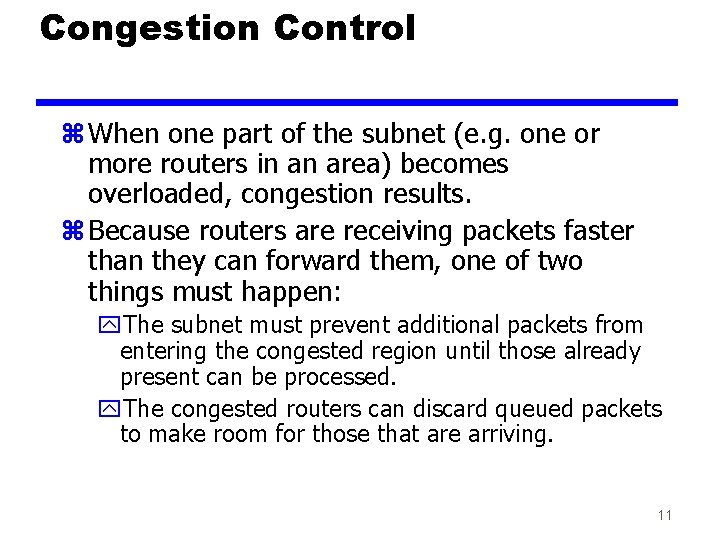
Congestion Control z When one part of the subnet (e. g. one or more routers in an area) becomes overloaded, congestion results. z Because routers are receiving packets faster than they can forward them, one of two things must happen: y. The subnet must prevent additional packets from entering the congested region until those already present can be processed. y. The congested routers can discard queued packets to make room for those that are arriving. 11

Congestion Control, cont. z Congestion Control is concerned with efficiently using a network at high load. z Several techniques can be employed. These include: y. Warning bit y. Choke packets y. Load shedding y. Random early discard y. Traffic shaping z The first 3 deal with congestion detection and recovery. The last 2 deal with congestion avoidance. 12

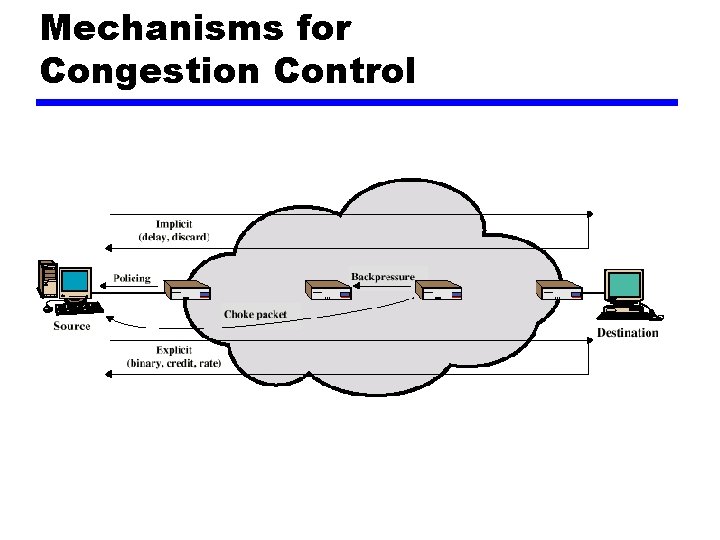
Mechanisms for Congestion Control

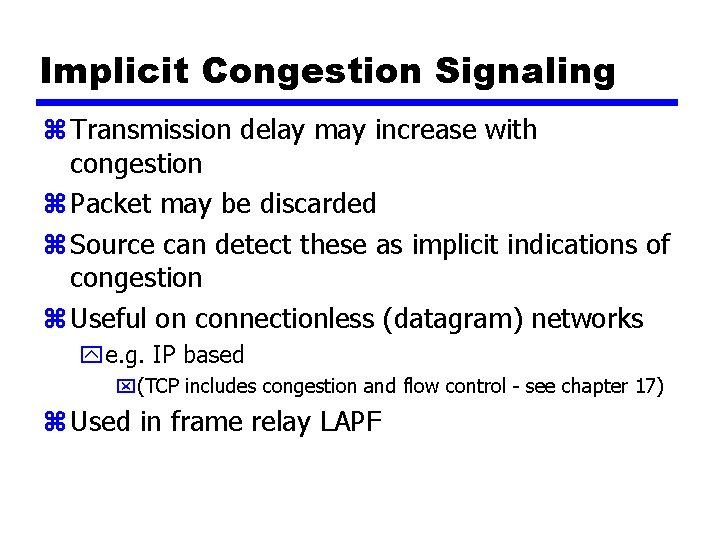
Implicit Congestion Signaling z Transmission delay may increase with congestion z Packet may be discarded z Source can detect these as implicit indications of congestion z Useful on connectionless (datagram) networks ye. g. IP based x(TCP includes congestion and flow control - see chapter 17) z Used in frame relay LAPF

Explicit Congestion Signaling z Network alerts end systems of increasing congestion z End systems take steps to reduce offered load z Backwards y. Congestion avoidance in opposite direction to packet required z Forwards y. Congestion avoidance in same direction as packet required

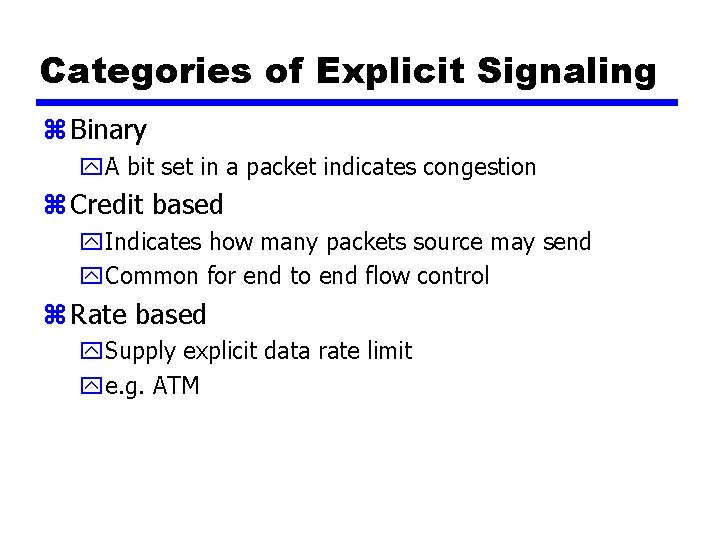
Categories of Explicit Signaling z Binary y. A bit set in a packet indicates congestion z Credit based y. Indicates how many packets source may send y. Common for end to end flow control z Rate based y. Supply explicit data rate limit ye. g. ATM

Warning Bit z A special bit in the packet header is set by the router to warn the source when congestion is detected. z The bit is copied and piggy-backed on the ACK and sent to the sender. z The sender monitors the number of ACK packets it receives with the warning bit set and adjusts its transmission rate accordingly. 17

Choke Packets z A more direct way of telling the source to slow down. z A choke packet is a control packet generated at a congested node and transmitted to restrict traffic flow. z The source, on receiving the choke packet must reduce its transmission rate by a certain percentage. z An example of a choke packet is the ICMP Source Quench Packet. 18

Hop-by-Hop Choke Packets z Over long distances or at high speeds choke packets are not very effective. z A more efficient method is to send to choke packets hop-by-hop. z This requires each hop to reduce its transmission even before the choke packet arrive at the source. 19

Traffic Management z Fairness z Quality of service y. May want different treatment for different connections z Reservations ye. g. ATM y. Traffic contract between user and network

Load Shedding z When buffers become full, routers simply discard packets. z Which packet is chosen to be the victim depends on the application and on the error strategy used in the data link layer. z For a file transfer, for, e. g. cannot discard older packets since this will cause a gap in the received data. z For real-time voice or video it is probably better to throw away old data and keep new packets. z Get the application to mark packets with discard priority. 21

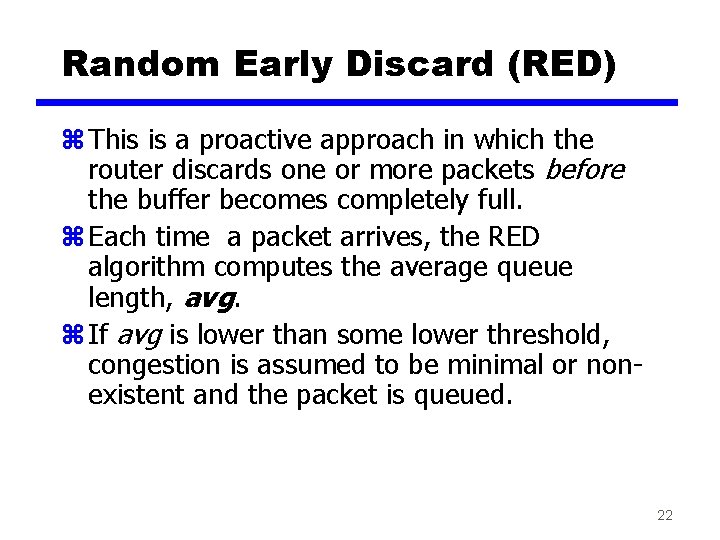
Random Early Discard (RED) z This is a proactive approach in which the router discards one or more packets before the buffer becomes completely full. z Each time a packet arrives, the RED algorithm computes the average queue length, avg. z If avg is lower than some lower threshold, congestion is assumed to be minimal or nonexistent and the packet is queued. 22

RED, cont. z If avg is greater than some upper threshold, congestion is assumed to be serious and the packet is discarded. z If avg is between the two thresholds, this might indicate the onset of congestion. The probability of congestion is then calculated. 23

WRED z Weighted Random Early Detect z Traffic can be prioritized and put in different queues z Each queue will have a different weight in the discard method, less for high priority, more for low priority

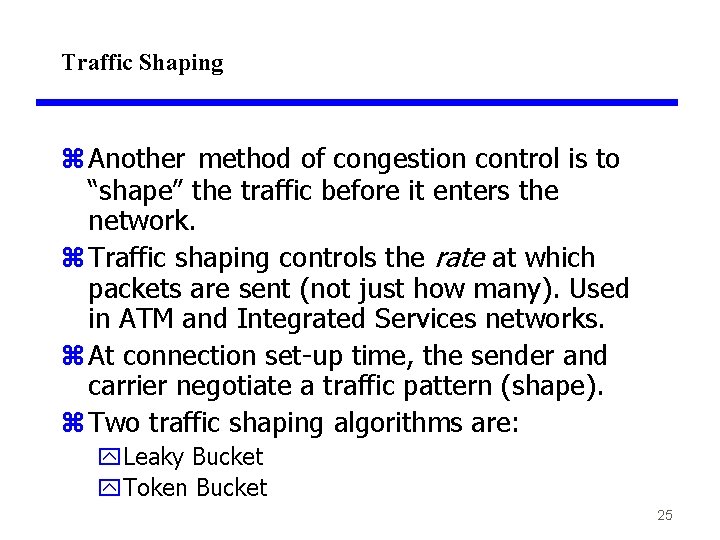
Traffic Shaping z Another method of congestion control is to “shape” the traffic before it enters the network. z Traffic shaping controls the rate at which packets are sent (not just how many). Used in ATM and Integrated Services networks. z At connection set-up time, the sender and carrier negotiate a traffic pattern (shape). z Two traffic shaping algorithms are: y. Leaky Bucket y. Token Bucket 25

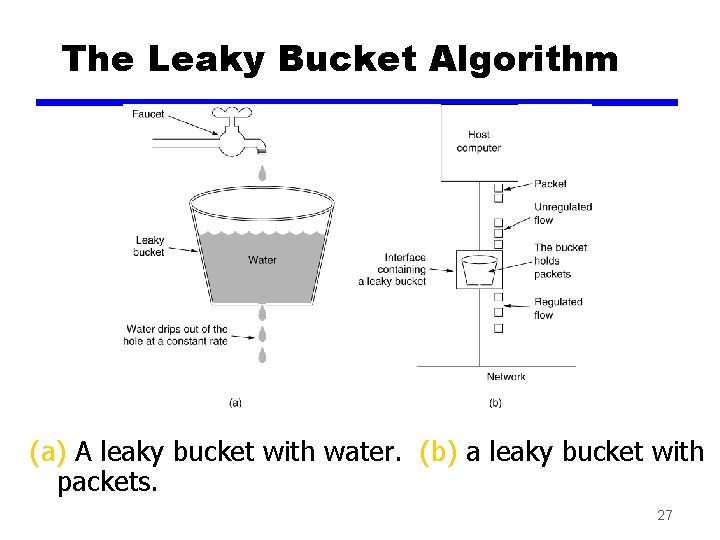
The Leaky Bucket Algorithm z The Leaky Bucket Algorithm used to control rate in a network. It is implemented as a singleserver queue with constant service time. If the bucket (buffer) overflows then packets are discarded. 26

The Leaky Bucket Algorithm (a) A leaky bucket with water. (b) a leaky bucket with packets. 27

Leaky Bucket Algorithm, cont. z The leaky bucket enforces a constant output rate (average rate) regardless of the burstiness of the input. Does nothing when input is idle. z The host injects one packet per clock tick onto the network. This results in a uniform flow of packets, smoothing out bursts and reducing congestion. z When packets are the same size (as in ATM cells), the one packet per tick is okay. For variable length packets though, it is better to allow a fixed number of bytes per tick. E. g. 1024 bytes per tick will allow one 1024 -byte packet or two 512 -byte packets or four 256 byte packets on 1 tick. 28

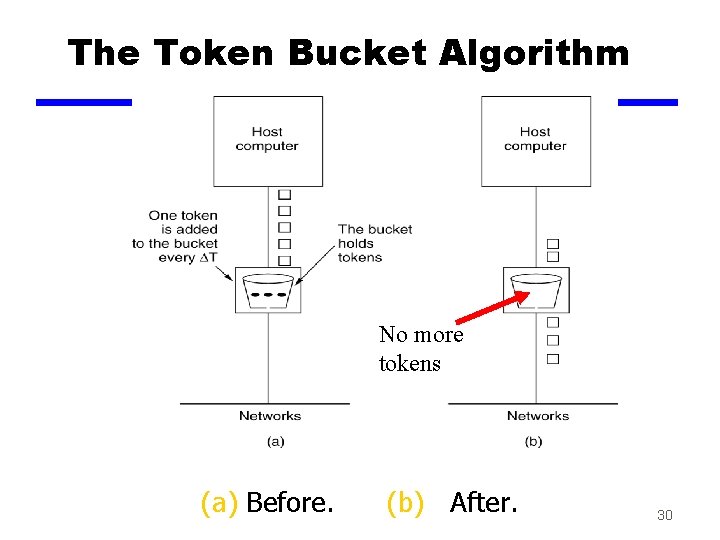
Token Bucket Algorithm z In contrast to the LB, the Token Bucket Algorithm, allows the output rate to vary, depending on the size of the burst. z In the TB algorithm, the bucket holds tokens. To transmit a packet, the host must capture and destroy one token. z Tokens are generated by a clock at the rate of one token every t sec. z Idle hosts can capture and save up tokens (up to the max. size of the bucket) in order to send larger bursts later. 29

The Token Bucket Algorithm 5 -34 No more tokens (a) Before. (b) After. 30

Leaky Bucket vs Token Bucket z LB discards packets; TB does not. TB discards tokens. z With TB, a packet can only be transmitted if there are enough tokens to cover its length in bytes. z LB sends packets at an average rate. TB allows for large bursts to be sent faster by speeding up the output. z TB allows saving up tokens (permissions) to send large bursts. LB does not allow saving. 31

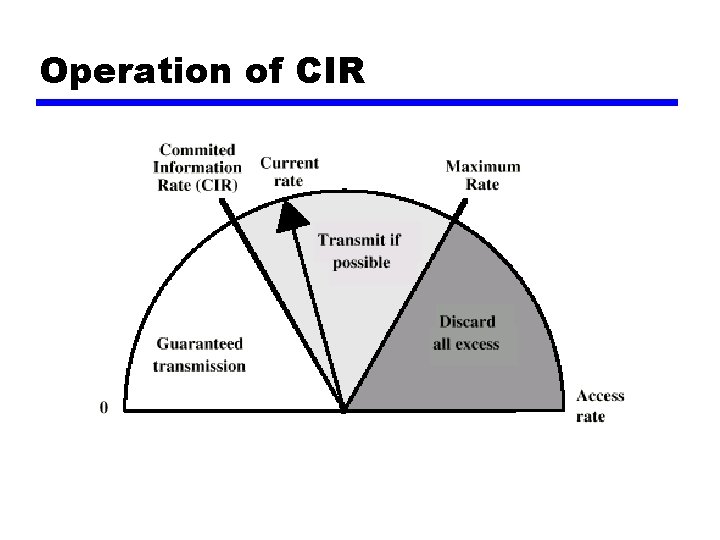
Operation of CIR

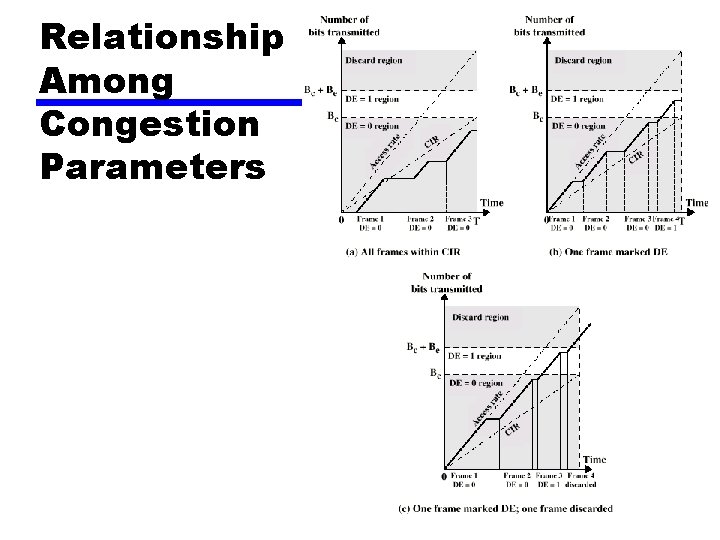
Relationship Among Congestion Parameters

Required Reading z Stallings chapter 12