William Stallings Data and Computer Communications Chapter 15






- Slides: 33

William Stallings Data and Computer Communications Chapter 15 Internetwork Protocols

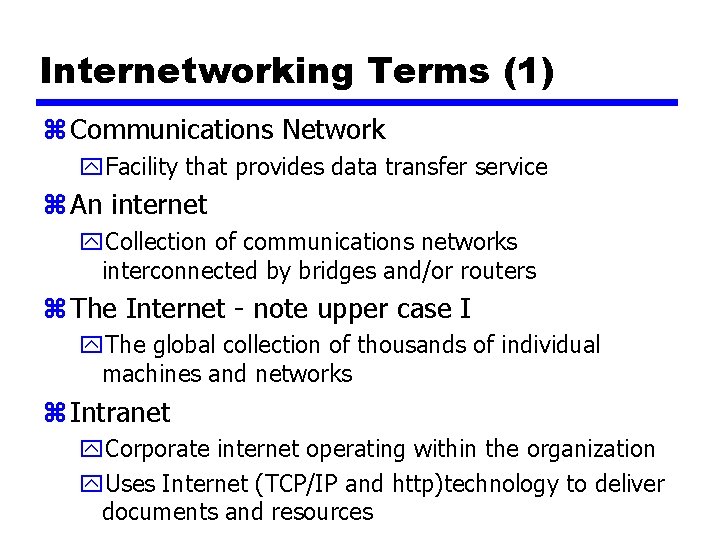
Internetworking Terms (1) z Communications Network y. Facility that provides data transfer service z An internet y. Collection of communications networks interconnected by bridges and/or routers z The Internet - note upper case I y. The global collection of thousands of individual machines and networks z Intranet y. Corporate internet operating within the organization y. Uses Internet (TCP/IP and http)technology to deliver documents and resources

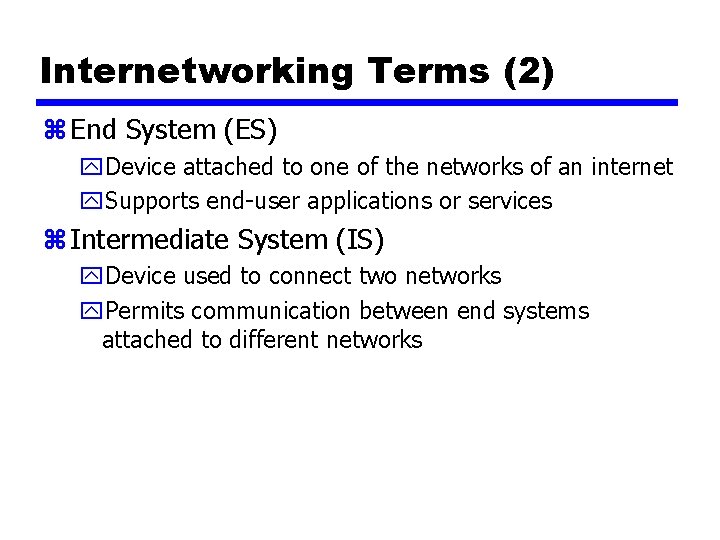
Internetworking Terms (2) z End System (ES) y. Device attached to one of the networks of an internet y. Supports end-user applications or services z Intermediate System (IS) y. Device used to connect two networks y. Permits communication between end systems attached to different networks

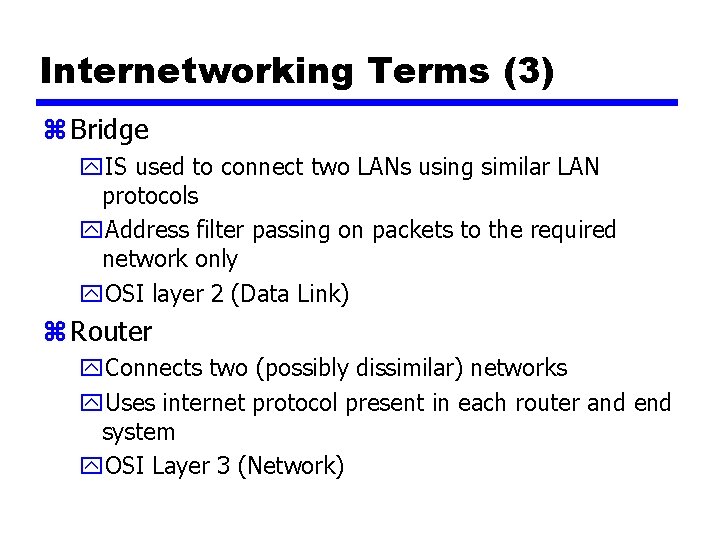
Internetworking Terms (3) z Bridge y. IS used to connect two LANs using similar LAN protocols y. Address filter passing on packets to the required network only y. OSI layer 2 (Data Link) z Router y. Connects two (possibly dissimilar) networks y. Uses internet protocol present in each router and end system y. OSI Layer 3 (Network)

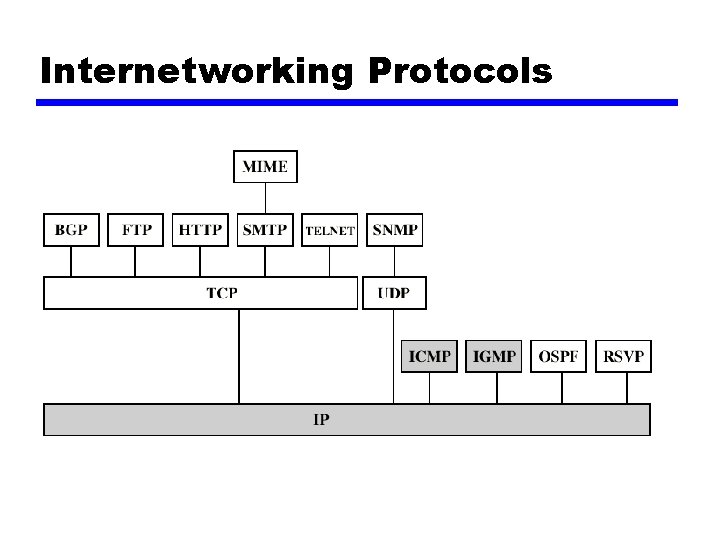
Internetworking Protocols

Network Architecture Features z Addressing z Packet size z Access mechanism z Timeouts z Error recovery z Status reporting z Routing z User access control z Connection based or connectionless

Connectionless Internetworking z Advantages y. Flexibility y. Robust y. No unnecessary overhead z Unreliable y. Not guaranteed delivery y. Not guaranteed order of delivery x. Packets can take different routes y. Reliability is responsibility of next layer up (e. g. TCP)

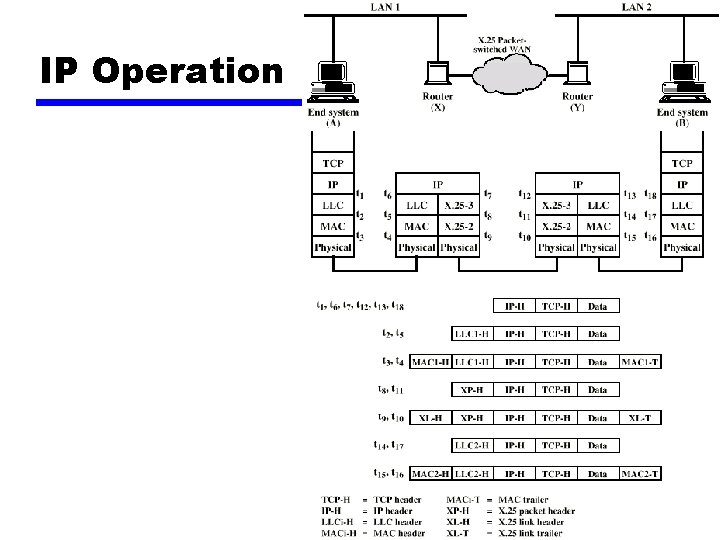
IP Operation

Design Issues z Routing z Datagram lifetime z Fragmentation and re-assembly z Error control z Flow control

Routing z End systems and routers maintain routing tables y. Indicate next router to which datagram should be sent y. Static x. May contain alternative routes y. Dynamic x. Flexible response to congestion and errors z Source routing y. Source specifies route as sequential list of routers to be followed y. Security (Problem!) y. Priority z Route recording

Datagram Lifetime z Datagrams could loop indefinitely y. Consumes resources y. Transport protocol may need upper bound on datagram life z Datagram marked with lifetime y. Time To Live field in IP y. Once lifetime expires, datagram discarded (not forwarded) y. Hop count x. Decrement time to live on passing through a each router y. Time count x. Need to know how long since last router z (Aside: compare with Logan’s Run)

Fragmentation and Re-assembly z Different packet sizes z When to re-assemble y. At destination x. Results in packets getting smaller as data traverses internet y. Intermediate re-assembly x. Need large buffers at routers x. Buffers may fill with fragments x. All fragments must go through same router • Inhibits dynamic routing

IP Fragmentation (1) z IP re-assembles at destination only z Uses fields in header y. Data Unit Identifier (ID) x. Identifies end system originated datagram • Source and destination address • Protocol layer generating data (e. g. TCP) • Identification supplied by that layer y. Data length x. Length of user data in octets

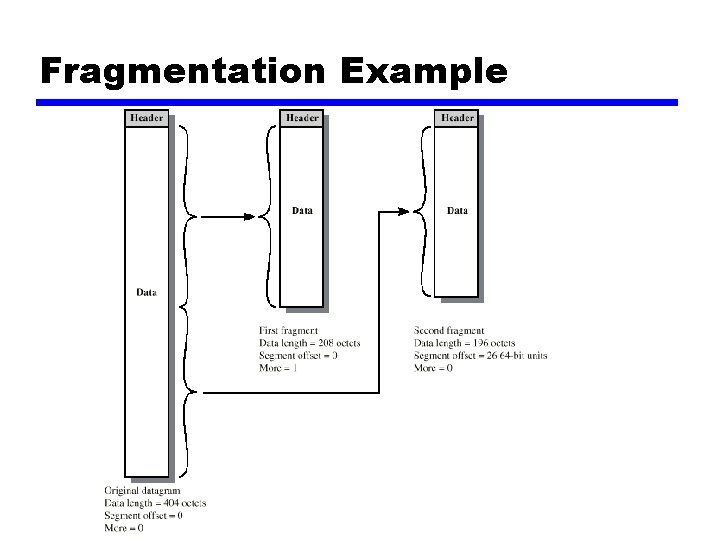
IP Fragmentation (2) y. Offset x. Position of fragment of user data in original datagram x. In multiples of 64 bits (8 octets) y. More flag x. Indicates that this is not the last fragment

Fragmentation Example

Dealing with Failure z Re-assembly may fail if some fragments get lost z Need to detect failure z Re-assembly time out y. Assigned to first fragment to arrive y. If timeout expires before all fragments arrive, discard partial data z Use packet lifetime (time to live in IP) y. If time to live runs out, kill partial data

Internet Protocol (IP) z Part of TCP/IP y. Used by the Internet z Specifies interface with higher layer ye. g. TCP z Specifies protocol format and mechanisms

Parameters (1) z Source address z Destination address z Protocol y. Recipient e. g. TCP z Type of Service y. Specify treatment of data unit during transmission through networks z Identification y. Source, destination address and user protocol y. Uniquely identifies PDU y. Needed for re-assembly and error reporting y. Send only

Parameters (2) z Don’t fragment indicator y. Can IP fragment data y. If not, may not be possible to deliver y. Send only z Time to live y. Send onl z Data length z Option data z User data

Options z Security z Source routing z Route recording z Stream identification z Timestamping

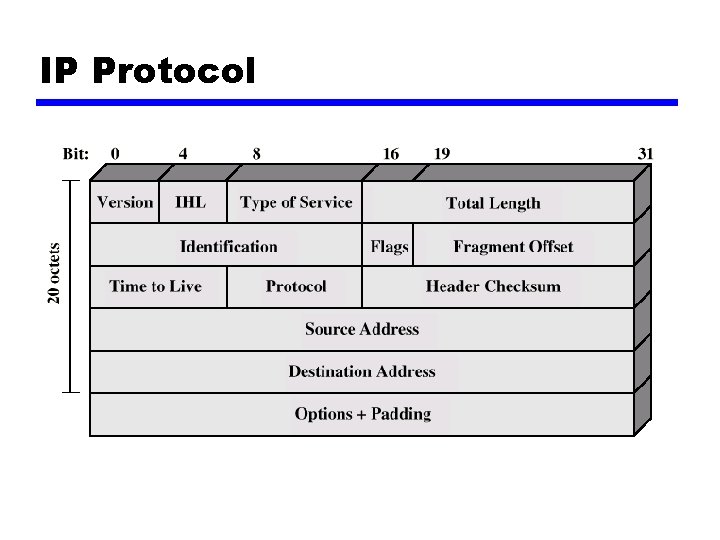
IP Protocol

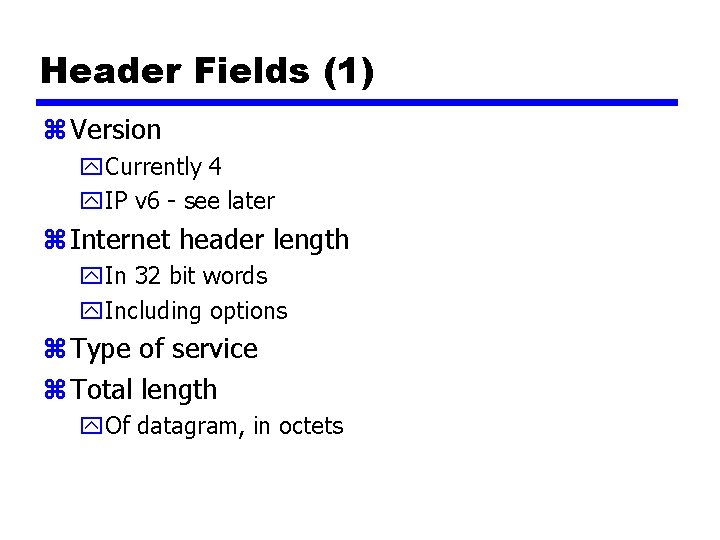
Header Fields (1) z Version y. Currently 4 y. IP v 6 - see later z Internet header length y. In 32 bit words y. Including options z Type of service z Total length y. Of datagram, in octets

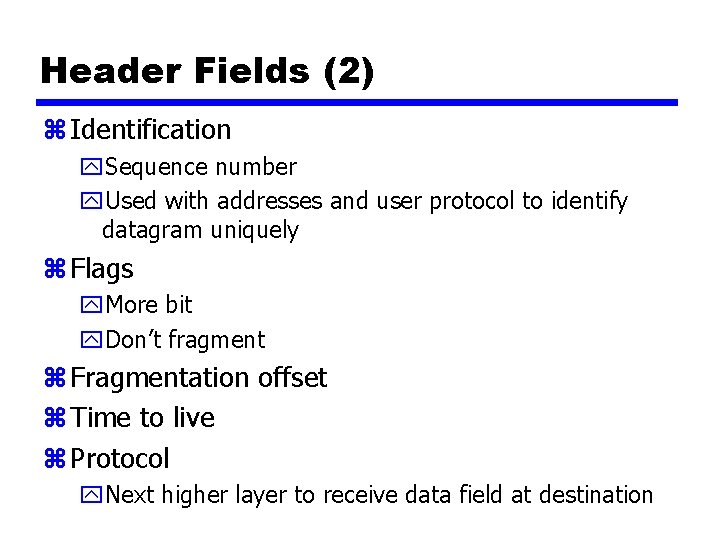
Header Fields (2) z Identification y. Sequence number y. Used with addresses and user protocol to identify datagram uniquely z Flags y. More bit y. Don’t fragment z Fragmentation offset z Time to live z Protocol y. Next higher layer to receive data field at destination

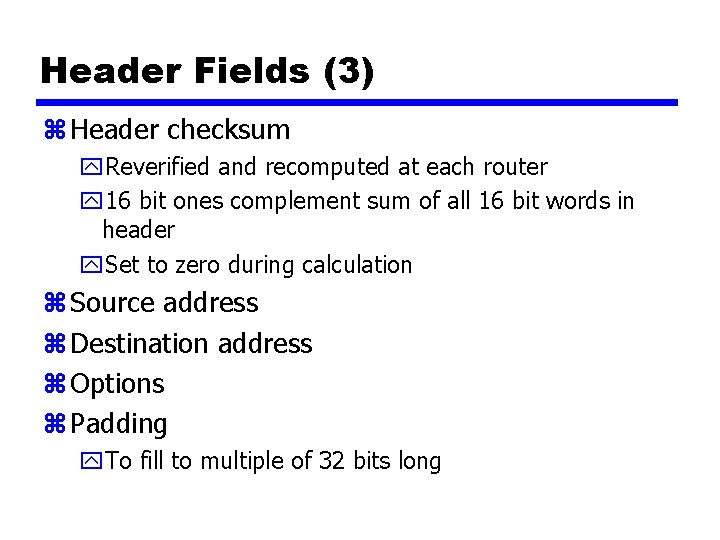
Header Fields (3) z Header checksum y. Reverified and recomputed at each router y 16 bit ones complement sum of all 16 bit words in header y. Set to zero during calculation z Source address z Destination address z Options z Padding y. To fill to multiple of 32 bits long

Data Field z Carries user data from next layer up z Integer multiple of 8 bits long (octet) z Max length of datagram (header plus data) 65, 535 octets

IP Addresses - Class A z 32 bit global internet address z Network part and host part z Class A y. Start with binary 0 y. All 0 reserved y 01111111 (127) reserved for loopback y. Range 1. x. x. x to 126. x. x. x y. All allocated

IP Addresses - Class B z Start 10 z Range 128. x. x. x to 191. x. x. x z Second Octet also included in network address z 214 = 16, 384 class B addresses z All allocated

IP Addresses - Class C z Start 110 z Range 192. x. x. x to 223. x. x. x z Second and third octet also part of network address z 221 = 2, 097, 152 addresses z Nearly allocated y. See IPv 6

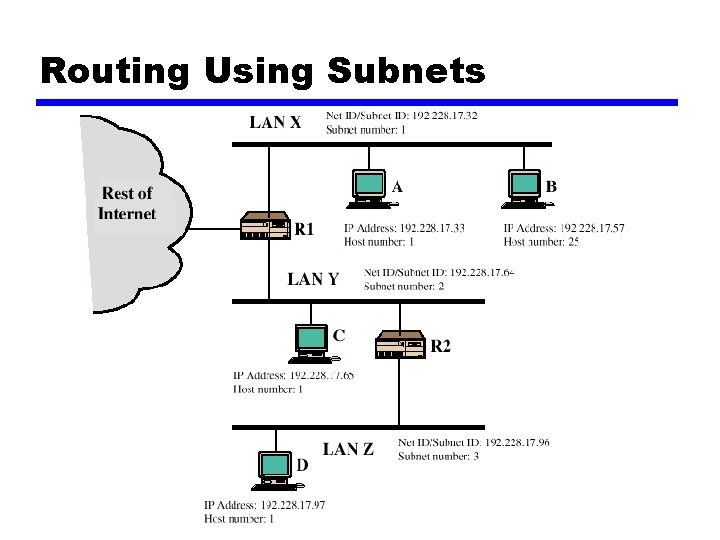
Subnets and Subnet Masks z Allow arbitrary complexity of internetworked LANs within organization z Insulate overall internet from growth of network numbers and routing complexity z Site looks to rest of internet like single network z Each LAN assigned subnet number z Host portion of address partitioned into subnet number and host number z Local routers route within subnetted network z Subnet mask indicates which bits are subnet number and which are host number

Routing Using Subnets

Why Change IP? z Address space exhaustion y. Two level addressing (network and host) wastes space y. Network addresses used even if not connected to Internet y. Growth of networks and the Internet y. Extended use of TCP/IP y. Single address per host z Requirements for new types of service

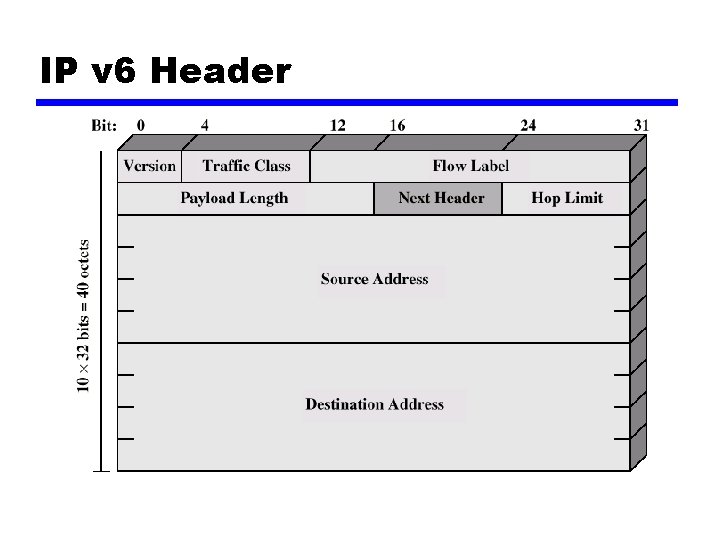
IP v 6 Header

Required Reading z Stallings chapter 15 z Comer, S. Internetworking with TCP/IP, volume 1, Prentice-Hall z All RFCs mentioned plus any others connected with these topics z Loads of Web sites on TCP/IP and IP version 6.