What You Need to Know for Project One










- Slides: 30

What You Need to Know for Project One Joey Echeverria Friday, August 29, 2003 15 -410 Fall 2003 Carnegie Mellon University

Overview 1. 2. 3. Introduction Project One Motivation and Demo Mundane Details in x 86 PIC and hardware interrupts, software interrupts and exceptions, the IDT, privilege levels, segmentation 4. 5. Writing a Device Driver Installing and Using Simics Carnegie Mellon University 2

A Little Bit About Myself 1. 2. 3. 4. My name is Joey I’m a senior in ECE (sort-of) I took OS with Greg Kesden last fall I, like the rest of the staff, am Here to Help™ Carnegie Mellon University 3

Project 1 Motivation What are our hopes for project 1? 1. a) b) c) d) introduction to kernel programming a better understanding of the x 86 arch hands-on experience with hardware interrupts and device drivers get acquainted with the simulator (Simics) and development tools Carnegie Mellon University 4

Project 1 Demo 1. Project 1 consists of using the console, keyboard and timer to create a simple game 2. Demo… Carnegie Mellon University 5

Mundane Details in x 86 1. 2. 3. 4. 5. Kernels work closely with hardware This means you need to know about hardware Some knowledge (registers, stack conventions) is assumed from 15 -213 You will learn more x 86 details as the semester goes on Use the Intel PDF files as reference (http: //www. cs. cmu. edu/~410/projects. html) Carnegie Mellon University 6

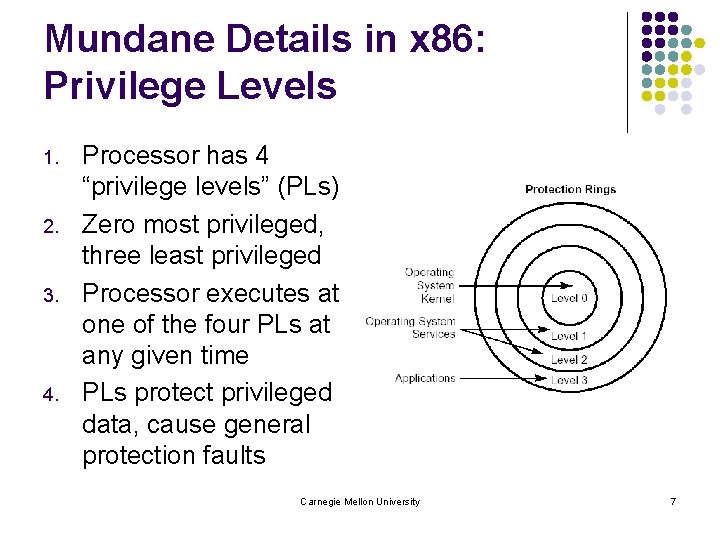
Mundane Details in x 86: Privilege Levels 1. 2. 3. 4. Processor has 4 “privilege levels” (PLs) Zero most privileged, three least privileged Processor executes at one of the four PLs at any given time PLs protect privileged data, cause general protection faults Carnegie Mellon University 7

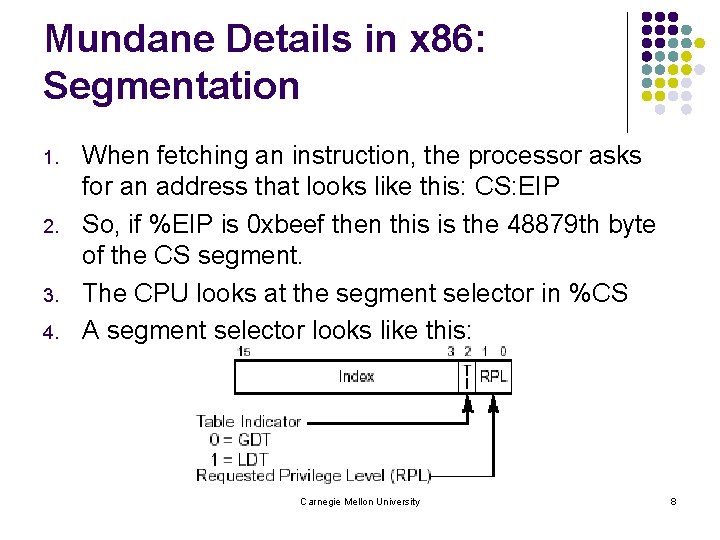
Mundane Details in x 86: Segmentation 1. 2. 3. 4. When fetching an instruction, the processor asks for an address that looks like this: CS: EIP So, if %EIP is 0 xbeef then this is the 48879 th byte of the CS segment. The CPU looks at the segment selector in %CS A segment selector looks like this: Carnegie Mellon University 8

Mundane Details in x 86: Segmentation 1. 2. 3. 4. 5. 6. The segment selector has a segment number, table selector, and requested privilege level (RPL) The segment number is an index into a segment descriptor table The table select flag selects a descriptor table There are two tables: global descriptor table and a local descriptor table The RPL’s meaning differs with the segment register the selector is in For %CS, RPL sets the processor privilege level Carnegie Mellon University 9

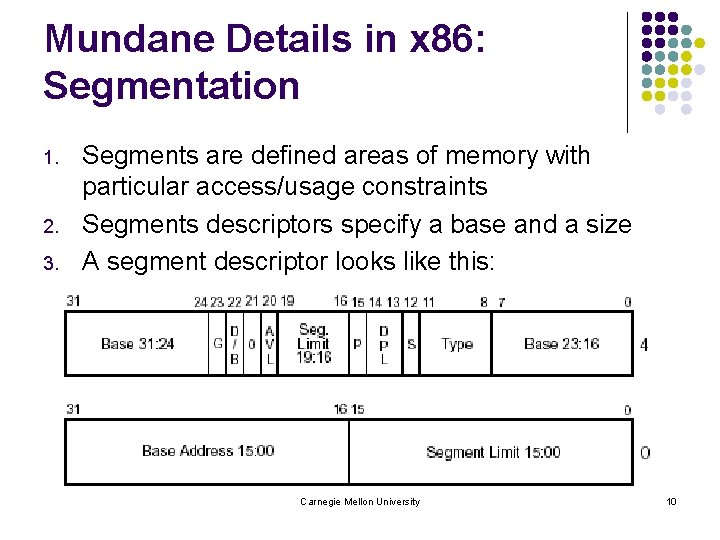
Mundane Details in x 86: Segmentation 1. 2. 3. Segments are defined areas of memory with particular access/usage constraints Segments descriptors specify a base and a size A segment descriptor looks like this: Carnegie Mellon University 10

Mundane Details in x 86: Segmentation 1. 2. 3. For our example, if the segment descriptor indexed by the segment selector in %CS specified a base address of 0 xdead 0000 Then assuming 0 xbeef is smaller than the size of the segment, the address CS: EIP represents the linear virtual address 0 xdeadbeef This is fed into the page-directory/page-table system which will be important in project 3 Carnegie Mellon University 11

Mundane Details in x 86: Segmentation 1. 2. 3. CS is the segment register for code SS is the segment register for the stack segment DS is the default segment register for data read/writes, but ES, FS, and GS can also be used Carnegie Mellon University 12

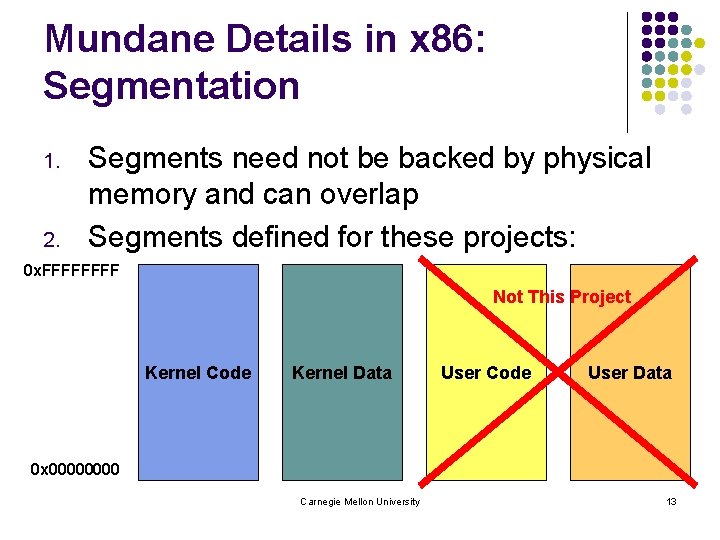
Mundane Details in x 86: Segmentation 1. 2. Segments need not be backed by physical memory and can overlap Segments defined for these projects: 0 x. FFFF Not This Project Kernel Code Kernel Data User Code User Data 0 x 0000 Carnegie Mellon University 13

Mundane Details in x 86: Segmentation 1. 2. 3. 4. 5. Why so many? You can’t specify a segment that is readable, writable and executable. Therefore one for readable/executable code Another for readable/writable data Need user and kernel segments in project 3 for protection Carnegie Mellon University 14

Mundane Details in x 86: Segmentation 1. 2. Don’t need to be concerned with the mundane details of segments in this class For more information you can read the intel docs or our documentation at: http: //www. cs. cmu. edu/~410/doc/segments. html Carnegie Mellon University 15

Mundane Details in x 86: Getting into Kernel Mode How do we get from user mode (PL 3) to kernel mode (PL 0)? 1. a) Exception (divide by zero, etc) b) Software Interrupt (int n instruction) c) Hardware Interrupt (keyboard, timer, etc) Carnegie Mellon University 16

Mundane Details in x 86: Exceptions 1. 2. 3. 4. 5. Sometimes user processes do stupid things int gorganzola = 128/0; char* idiot_ptr = NULL; *idiot_ptr = 0; These cause a handler routine to be executed at PL 0 Examples include divide by zero, general protection fault, page fault Carnegie Mellon University 17

Mundane Details in x 86: Software Interrupts 1. 2. 3. 4. A device gets the kernel’s attention by raising an interrupt User processes get the kernel’s attention by raising a software interrupt x 86 instruction int n (more info on page 346 of intel-isr. pdf) Executes handler routine at PL 0 Carnegie Mellon University 18

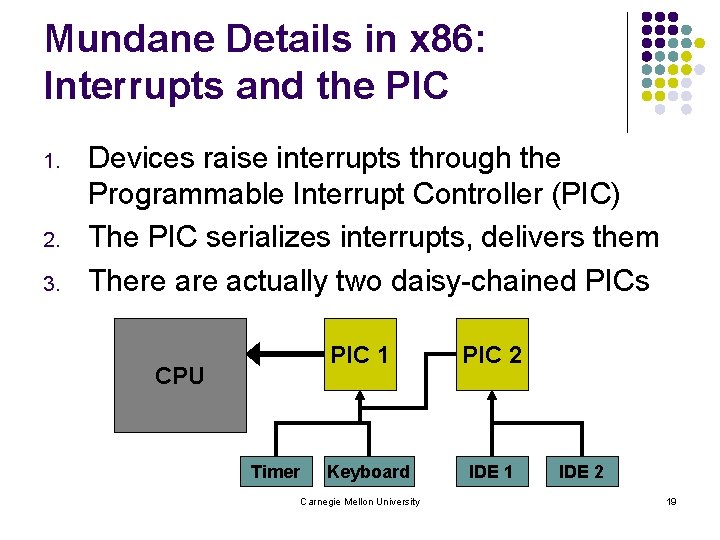
Mundane Details in x 86: Interrupts and the PIC 1. 2. 3. Devices raise interrupts through the Programmable Interrupt Controller (PIC) The PIC serializes interrupts, delivers them There actually two daisy-chained PICs PIC 1 CPU Timer Keyboard Carnegie Mellon University PIC 2 IDE 1 IDE 2 19

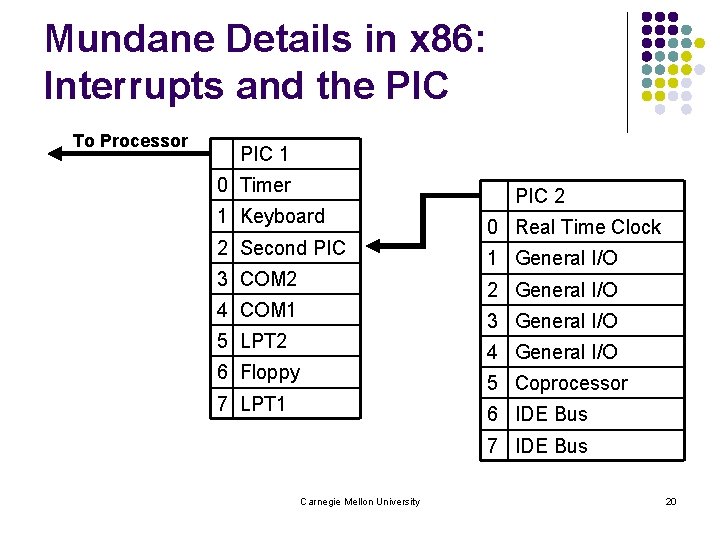
Mundane Details in x 86: Interrupts and the PIC To Processor PIC 1 0 Timer 1 Keyboard 2 Second PIC 3 COM 2 PIC 2 0 Real Time Clock 1 General I/O 2 General I/O 4 COM 1 3 General I/O 5 LPT 2 4 General I/O 6 Floppy 5 Coprocessor 7 LPT 1 6 IDE Bus 7 IDE Bus Carnegie Mellon University 20

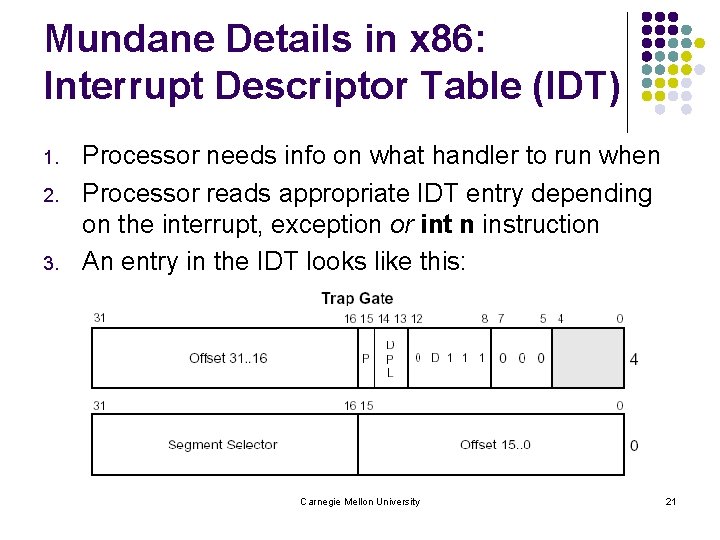
Mundane Details in x 86: Interrupt Descriptor Table (IDT) 1. 2. 3. Processor needs info on what handler to run when Processor reads appropriate IDT entry depending on the interrupt, exception or int n instruction An entry in the IDT looks like this: Carnegie Mellon University 21

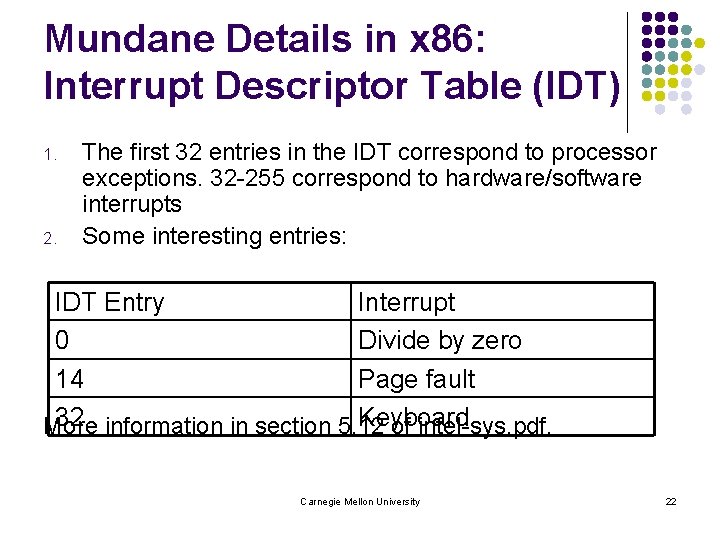
Mundane Details in x 86: Interrupt Descriptor Table (IDT) 1. 2. The first 32 entries in the IDT correspond to processor exceptions. 32 -255 correspond to hardware/software interrupts Some interesting entries: IDT Entry Interrupt 0 Divide by zero 14 Page fault 32 information in section 5. 12 Keyboard More of intel-sys. pdf. Carnegie Mellon University 22

Mundane Details in x 86: Communicating with Devices I/O Ports 1. a) b) use instructions like inb, outb use separate address space Memory-Mapped I/O 2. a) b) magic areas of memory tied to devices console is one of them Carnegie Mellon University 23

Writing a Device Driver Traditionally consist of two separate halves 1. a) b) 2. 3. named “top” and “bottom” halves BSD and Linux use these names differently One half is interrupt driven, executes quickly, queues work The other half processes queued work at a more convenient time Carnegie Mellon University 24

Writing a Device Driver For this project, your keyboard driver will likely have a top and bottom half Bottom half: 1. 2. a) Responds to keyboard interrupts and enqueue scan codes Top half: 3. a) In readchar(), read from the queue and processes scan codes into characters Carnegie Mellon University 25

Installing and Using Simics is an instruction set simulator Makes testing kernels MUCH easier Runs on both x 86 and Solaris 1. 2. 3. a) If you want to run from Solaris, we can try and accommodate, but the tarball only has linux support Carnegie Mellon University 26

Installing and Using Simics: Running on AFS We use mtools to copy to disk image files Proj 1 Makefile sets up config file for you You must exec simics in your project dir The proj 1. tar. gz includes: 1. 2. 3. 4. a) Only simics-linux. sh right now, can provide simics-solaris. sh if you are really interested Carnegie Mellon University 27

Installing and Using Simics: Running on AFS 1. 2. We give you some volume space It is located here: /afs/cs. cmu. edu/academic/class/15410 -f 03/usr/<user-id> 3. 4. 5. You should use this volume This way, if you have a problem the staff will have permission to look at your code This will help speed up answers to your questions Carnegie Mellon University 28

Installing and Using Simics: Running on Personal PC 1. 2. 3. 4. 5. Runs under Linux or Solaris (we will try to support this) As of now you need a 128. 2. *. * IP or a node locked license (takes a day or two to get this) Download simics-linux. tar. gz (real soon™) Install mtools RPM (pointer on course www) Tweak Makefile Carnegie Mellon University 29

Installing and Using Simics: Debugging Run simulation with r, stop with ctl-c Magic instruction 1. 2. a) Memory access breakpoints 3. a) break 0 x 2000 –x OR break (sym init_timer) Symbolic debugging 4. a) 5. xchg %bx, %bx (wrapper in interrupts. h) psym foo OR print (sym foo) Demo Carnegie Mellon University 30