VPN M Akram Mujahid Slide 1 Virtual Private






- Slides: 22

VPN M Akram Mujahid Slide 1

Virtual Private Network (VPN) • A virtual private network (VPN) is a secure network that uses public telecommunication infrastructures, such as the Internet, to connect remote sites or users together. M Akram Mujahid Slide 2

Types of VPNs • • • Remote access VPN Intranet VPN Extranet VPN M Akram Mujahid Slide 3

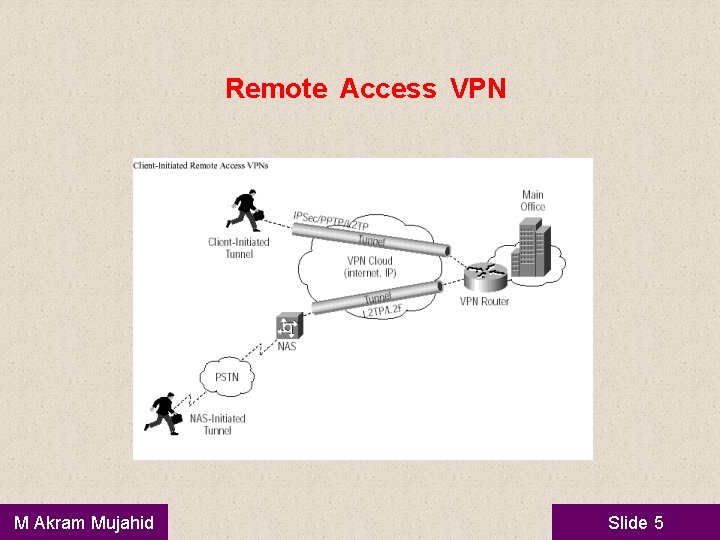
Remote-Access VPN • • A remote-access VPN allows individual users to establish secure connections with a remote computer network. An example of a company that needs a remoteaccess VPN is a large firm with hundreds of salespeople in the field. Another name for this type of VPN is virtual private dial-up network (VPDN M Akram Mujahid Slide 4

Remote Access VPN M Akram Mujahid Slide 5

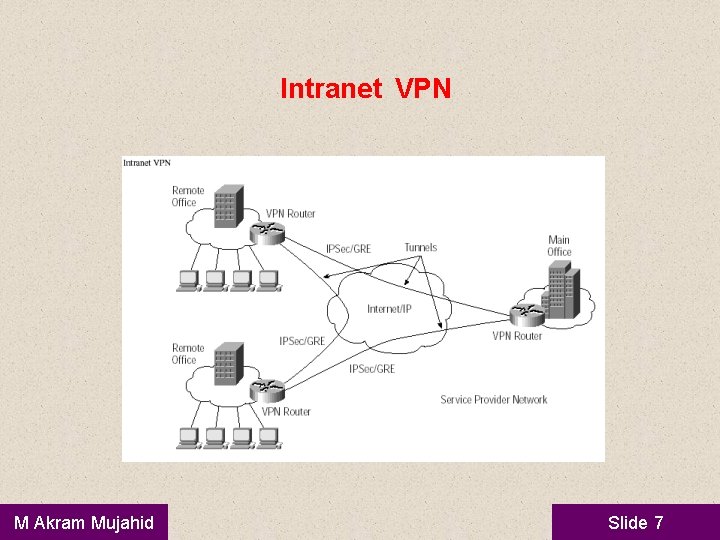
Intranet VPN • Intranet-based -- If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN to connect each separate LAN to a single WAN. M Akram Mujahid Slide 6

Intranet VPN M Akram Mujahid Slide 7

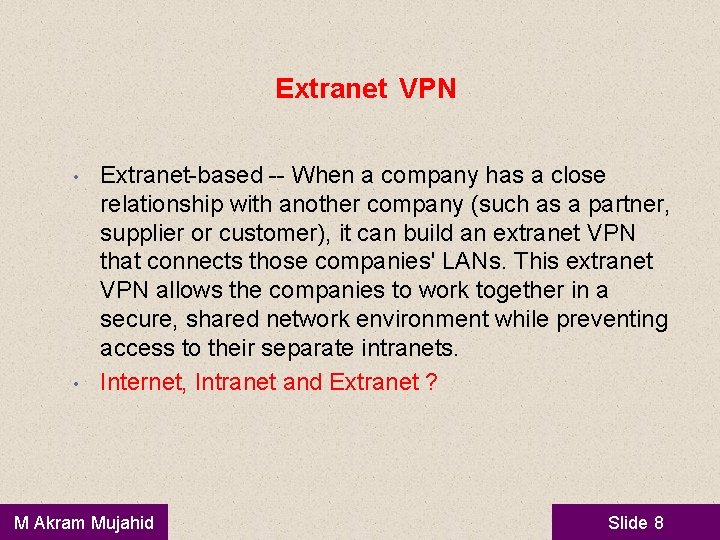
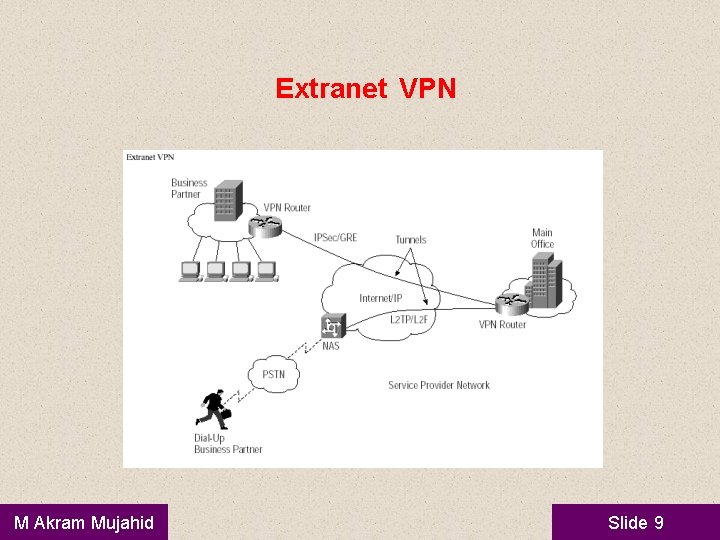
Extranet VPN • • Extranet-based -- When a company has a close relationship with another company (such as a partner, supplier or customer), it can build an extranet VPN that connects those companies' LANs. This extranet VPN allows the companies to work together in a secure, shared network environment while preventing access to their separate intranets. Internet, Intranet and Extranet ? M Akram Mujahid Slide 8

Extranet VPN M Akram Mujahid Slide 9

Advantages of VPN – – – – Greater scalability Easy to add/remove users Reduced long-distance telecommunications costs Mobility Security Extends geographic connectivity Boosts employee productivity M Akram Mujahid Slide 10

Disadvantages of VPN – – Lack of standards Understanding of security issues Unpredictable Internet traffic Difficult to accommodate products from different vendors M Akram Mujahid Slide 11

What is needed? • • • Existing hardware (Servers, workstations, …) Internet connection VPN - Router/Switch Software to create and manage tunnels Security Device such as firewall M Akram Mujahid Slide 12

How it works • • Operates at layer 2 or 3 of OSI model • Layer 2 frame – Ethernet • Layer 3 packet – IP Tunneling • allows senders to encapsulate their data in IP packets that hide the routing and switching infrastructure of the Internet • to ensure data security against unwanted viewers, or hackers. M Akram Mujahid Slide 13

VPN Components • • • Protocols Security Appliances M Akram Mujahid Slide 14

Protocols • • Tunneling requires three different protocols: Carrier protocol - The protocol used by the network that the information is traveling over Encapsulating protocol - The protocol (GRE, IPSec, L 2 F, PPTP, L 2 TP) that is wrapped around the original data Passenger protocol - The original data (IPX, Net. Beui, IP) being carried M Akram Mujahid Slide 15

VPN Components: Protocols • • • IP Security (IPSec) • Transport mode • Tunnel mode Point-to-Point Tunneling Protocol (PPTP) • Voluntary tunneling method • Uses PPP (Point-to-Point Protocol) Layer 2 Tunneling Protocol (L 2 TP) • Exists at the data link layer of OSI • Composed from PPTP and L 2 F (Layer 2 Forwarding) • Compulsory tunneling method M Akram Mujahid Slide 16

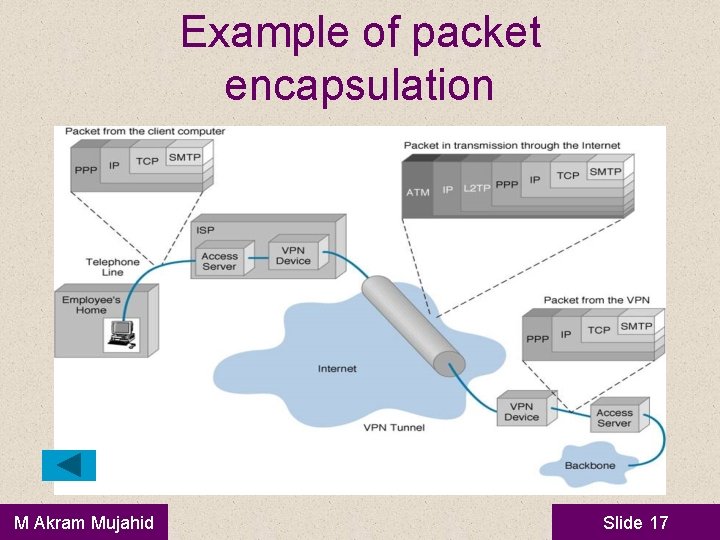
Example of packet encapsulation M Akram Mujahid Slide 17

VPN Components: Security • Encryption • Technique for scrambling and unscrambling information • Unscramble – called clear-text • Scrambled information – cipher-text M Akram Mujahid Slide 18

VPN Components: Security • Keys • Secret code that the encryption algorithm uses to create a unique version of cipher-text • 8 -bits keys = 256 combinations or two to the eighth power • 16 -bits keys = 65, 536 combinations or two to the 16 th power • 56 -bits keys = 72, 057, 594, 037, 927, 900 or two to the 56 th power • 168 -bits keys … M Akram Mujahid Slide 19

VPN Components: Security • Authentication • Determine if the sender is the authorized person and if the data has been redirect or corrupted • User/System Authentication • Data Authentication M Akram Mujahid Slide 20

VPN Components: Appliances • Intrusion detection firewalls • Monitors traffic crossing network parameters and protects enterprises from unauthorized access • Packet-level firewall checks source and destination • Application-level firewall acts as a host computer between the organization’s network and the Internet M Akram Mujahid Slide 21

Questions M Akram Mujahid Slide 22