Topology Control and Its Effects in Wireless Networks


- Slides: 24

Topology Control and Its Effects in Wireless Networks Ning Li, Jennifer Hou, and Lui Sha Department of Computer Science University of Illinois at Urbana-Champaign {nli, jhou, lrs}@cs. uiuc. edu Ning Li, CS, UIUC

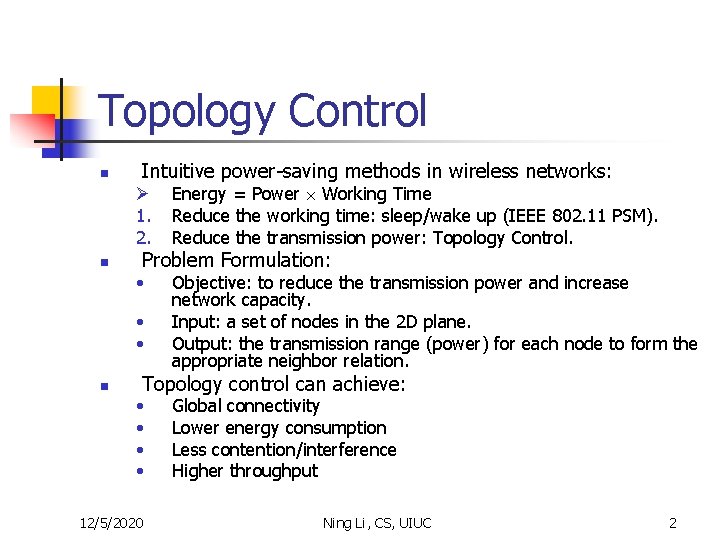
Topology Control n n Intuitive power-saving methods in wireless networks: Ø 1. 2. Energy = Power Working Time Reduce the working time: sleep/wake up (IEEE 802. 11 PSM). Reduce the transmission power: Topology Control. • Objective: to reduce the transmission power and increase network capacity. Input: a set of nodes in the 2 D plane. Output: the transmission range (power) for each node to form the appropriate neighbor relation. Problem Formulation: • • n Topology control can achieve: • • 12/5/2020 Global connectivity Lower energy consumption Less contention/interference Higher throughput Ning Li, CS, UIUC 2

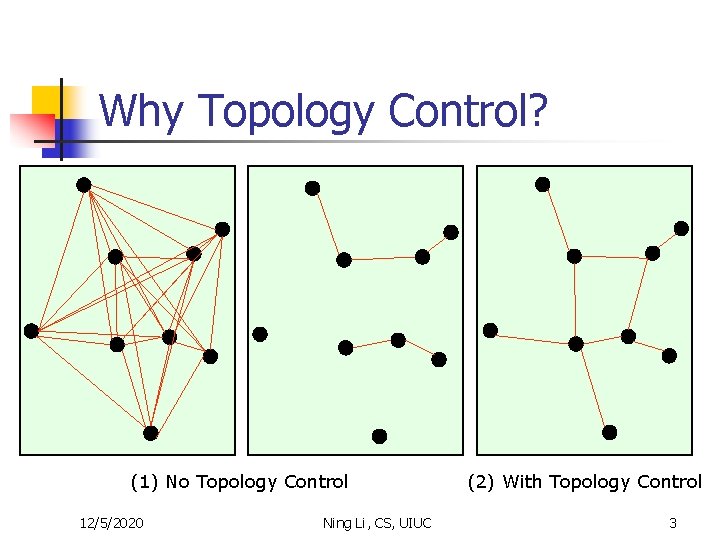
Why Topology Control? (1) No Topology Control 12/5/2020 Ning Li, CS, UIUC (2) With Topology Control 3

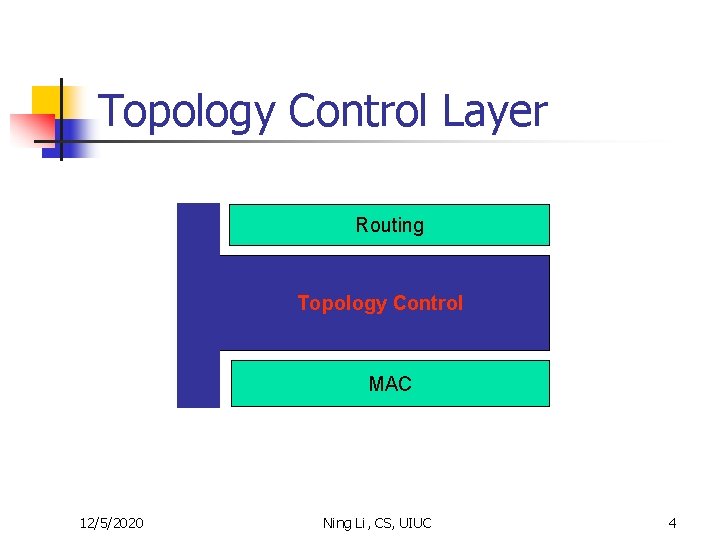
Topology Control Layer Routing Topology Control MAC 12/5/2020 Ning Li, CS, UIUC 4

Design Guidelines for Topology Control Algorithms n n n The network connectivity should be preserved, especially for static wireless networks. Algorithms should be distributed, i. e. , each node should make decisions on its own. To be more resistant to the impact of mobility, the algorithm should depend only on local information, e. g. , information collected within one hop. Bi-directional links are preferred, so as to facilitate link level acknowledgments and the medium access control mechanisms such as RTS/CTS in IEEE 802. 11. It is also desirable that the node degree in the topology derived under the algorithm is small. 12/5/2020 Ning Li, CS, UIUC 5

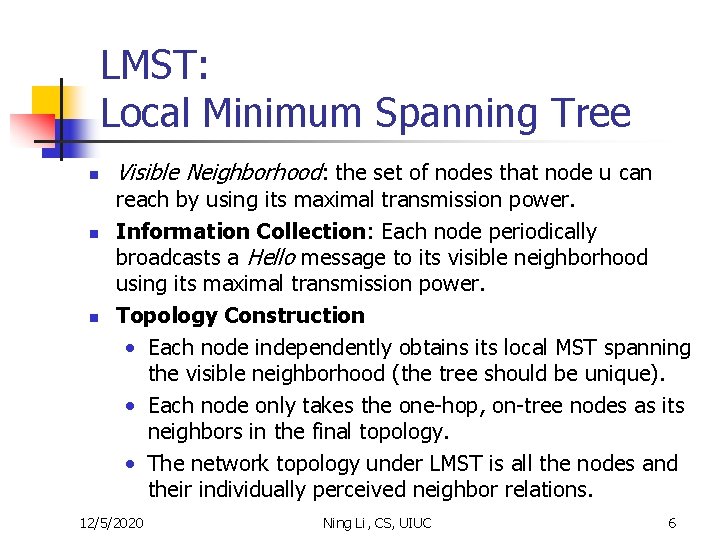
LMST: Local Minimum Spanning Tree n n n Visible Neighborhood: the set of nodes that node u can reach by using its maximal transmission power. Information Collection: Each node periodically broadcasts a Hello message to its visible neighborhood using its maximal transmission power. Topology Construction • Each node independently obtains its local MST spanning the visible neighborhood (the tree should be unique). • Each node only takes the one-hop, on-tree nodes as its neighbors in the final topology. • The network topology under LMST is all the nodes and their individually perceived neighbor relations. 12/5/2020 Ning Li, CS, UIUC 6

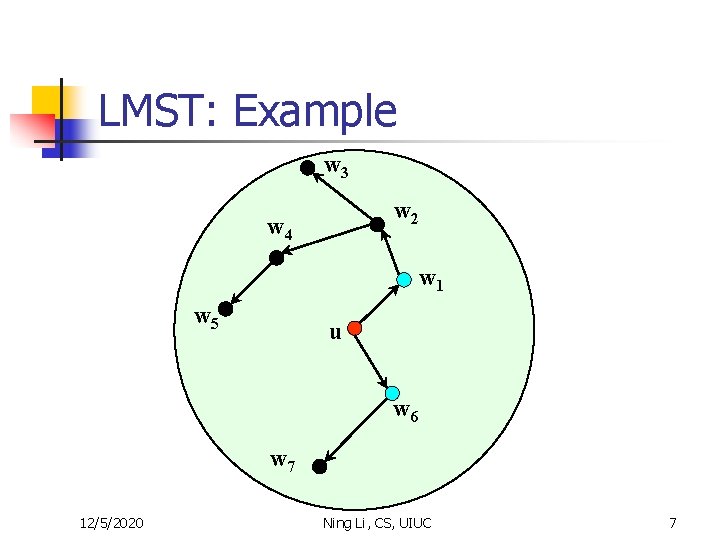
LMST: Example w 3 w 2 w 4 w 1 w 5 u w 6 w 7 12/5/2020 Ning Li, CS, UIUC 7

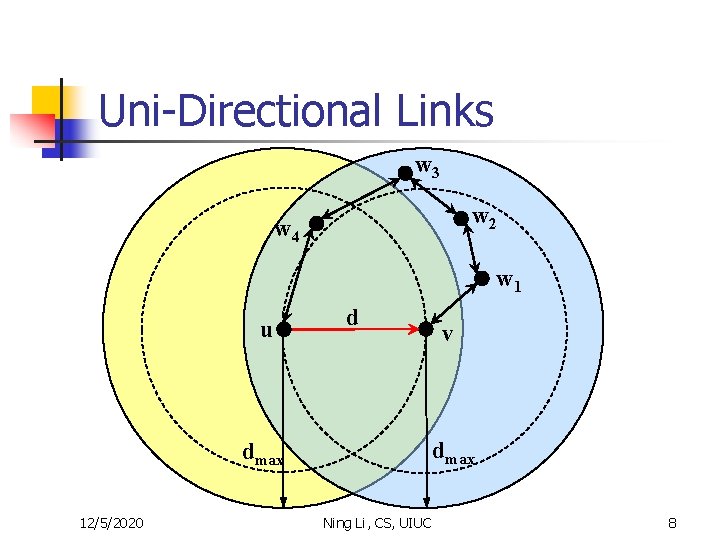
Uni-Directional Links w 3 w 2 w 4 w 1 u d dmax 12/5/2020 v Ning Li, CS, UIUC 8

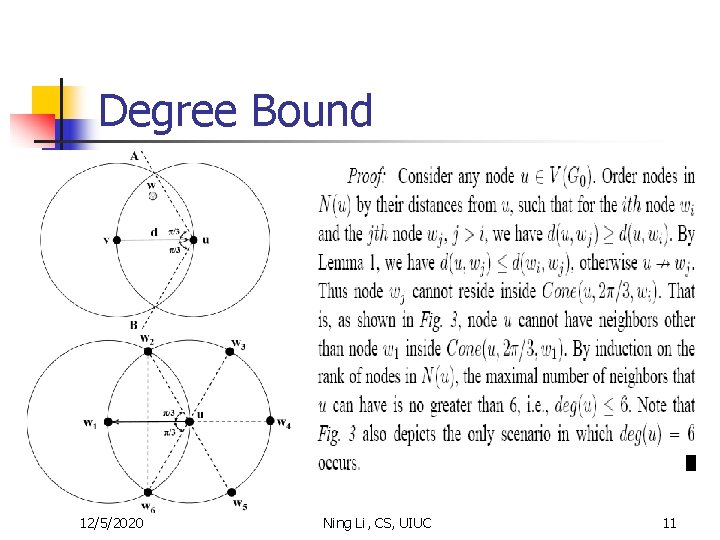
LMST Properties n n The final topology G 0 is a connected graph (with some links being uni-directional). To make the topology bi-directional, we can apply • Addition: add extra links into G 0 so that all uni-directional links become bi-directional • Removal: delete all uni-directional links in G 0. n n Both approaches result in connected graphs with bidirectional links. LMST Properties • The resulting topology preserves the connectivity. • After removal of asymmetric links, all links are bi-directional and the connectivity is still preserved. • The degree of any node is bounded by 6. 12/5/2020 Ning Li, CS, UIUC 9

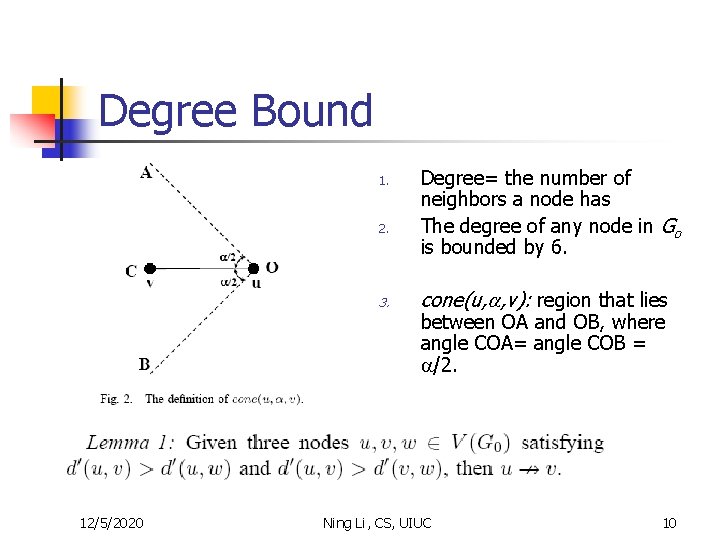
Degree Bound 1. 2. 3. 12/5/2020 Degree= the number of neighbors a node has The degree of any node in Go is bounded by 6. cone(u, a, v): region that lies between OA and OB, where angle COA= angle COB = a/2. Ning Li, CS, UIUC 10

Degree Bound 12/5/2020 Ning Li, CS, UIUC 11

Proof of Connectivity 1. 2. Define a weight function such that each edge has a distinct weight. Prove by induction that any pair of nodes of distance at most r are connected: • • 3. Basis: the pair of nodes on the shortest edge are connected. Induction on the node pairs in an ascending order of the weight. It can be proved that any pair of nodes are connected by shorter edges from the topology by LMST. Prove that any pair of nodes in the topology by LMST are connected. 12/5/2020 Ning Li, CS, UIUC 12

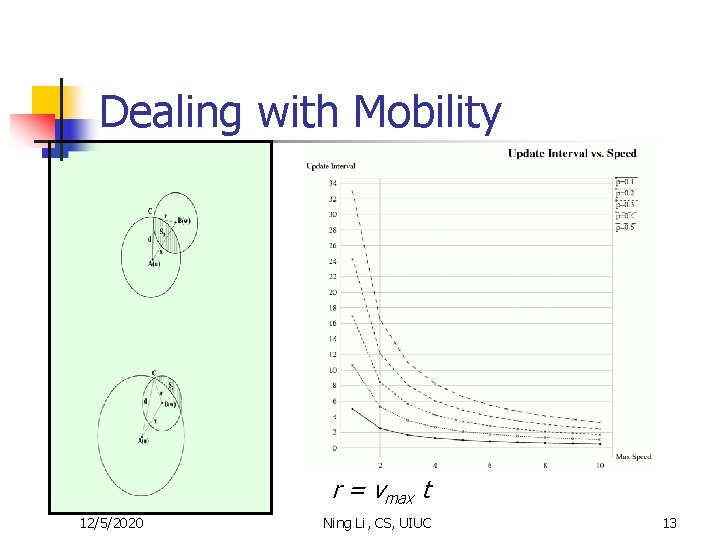
Dealing with Mobility r = vmax t 12/5/2020 Ning Li, CS, UIUC 13

Performance Evaluation n Traffic Independent Metrics • Average node degree • Average link length • Average radius n Traffic Dependent Metrics • Transmissions per packet • Energy efficiency 12/5/2020 Ning Li, CS, UIUC 14

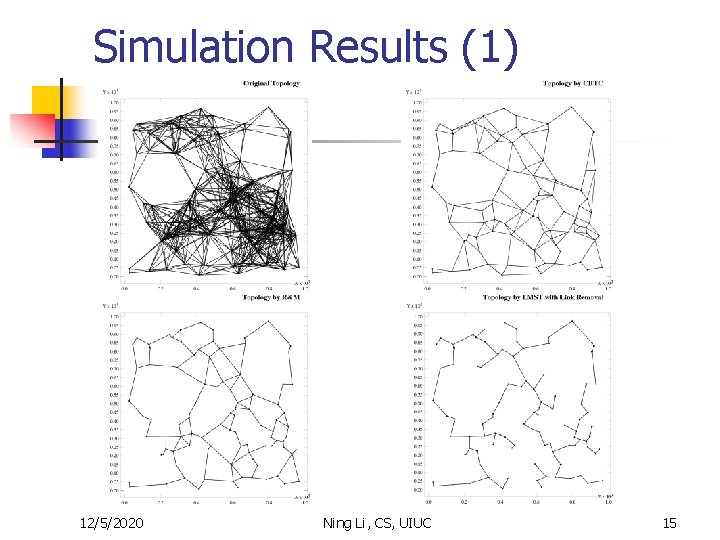
Simulation Results (1) 12/5/2020 Ning Li, CS, UIUC 15

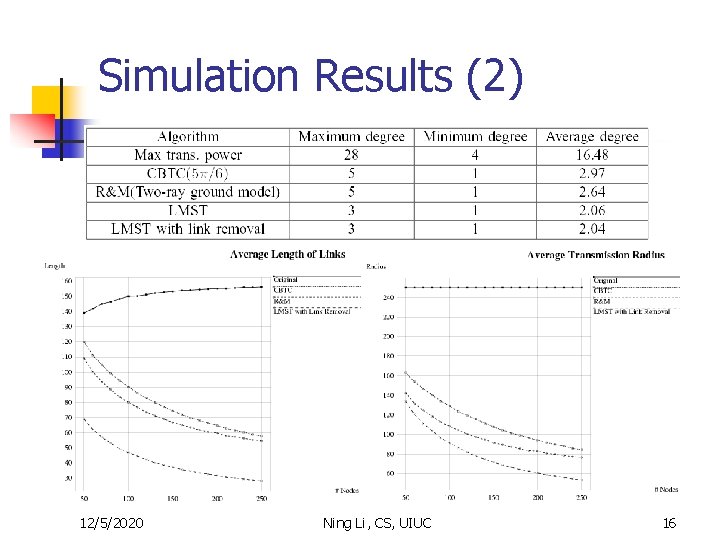
Simulation Results (2) 12/5/2020 Ning Li, CS, UIUC 16

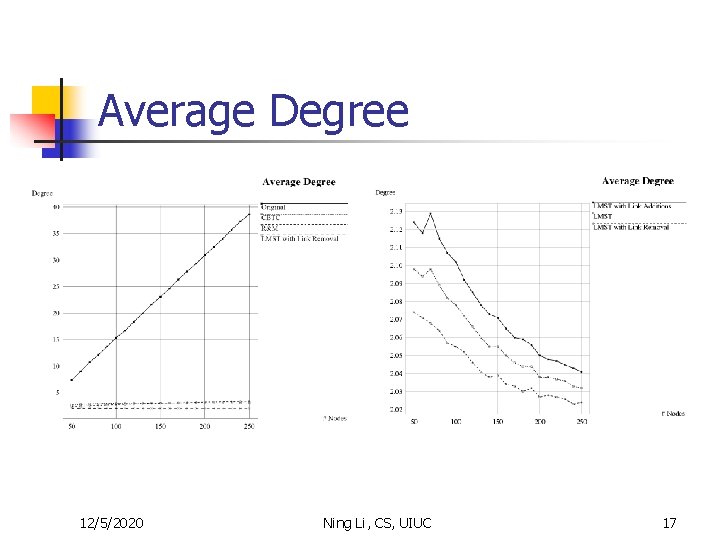
Average Degree 12/5/2020 Ning Li, CS, UIUC 17

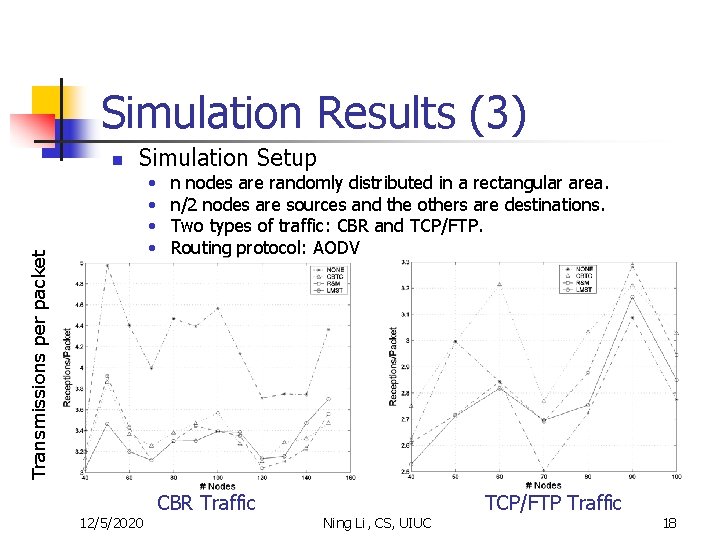
Simulation Results (3) n Simulation Setup Transmissions per packet • • 12/5/2020 n nodes are randomly distributed in a rectangular area. n/2 nodes are sources and the others are destinations. Two types of traffic: CBR and TCP/FTP. Routing protocol: AODV CBR Traffic Ning Li, CS, UIUC TCP/FTP Traffic 18

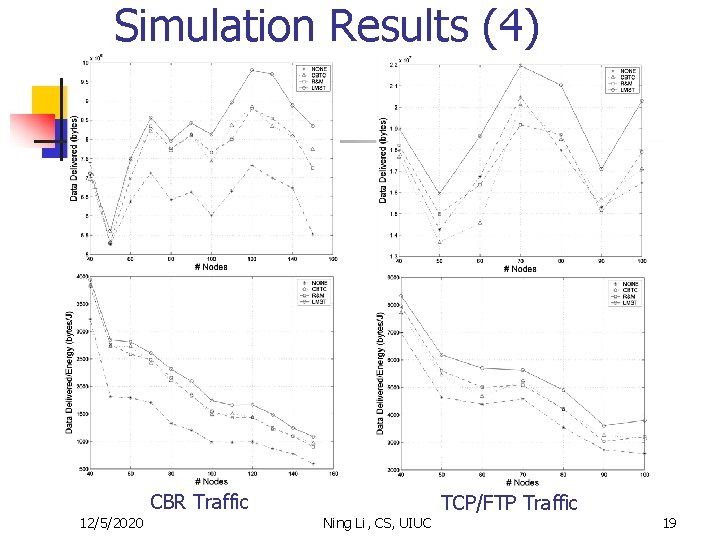
Simulation Results (4) CBR Traffic 12/5/2020 Ning Li, CS, UIUC TCP/FTP Traffic 19

LMST Summary n A localized topology control algorithm for wireless multihop networks which • • 12/5/2020 Preserves global connectivity; Ensures bi-directional links; Has a bounded number of neighbors; Provides higher capacity and energy efficiency. Ning Li, CS, UIUC 20

Existing Work n Assumptions: • Static multi-hop wireless network. • Homogeneous Network: the maximal transmission power (transmission range) for each node is the same. • Transmission power can be adjusted. • The area that the transmission of a node u can cover is a disk centered at u. • Each node is able to determine its own position via GPS or other positioning techniques. n Existing Work: • • RM: Relay-Region Based Approach, 1999 CBTC: Cone-Based Topology Control, 2000 RNG, 2002 COMPOW/CLUSTERPOW, 2002/2003 12/5/2020 Ning Li, CS, UIUC 21

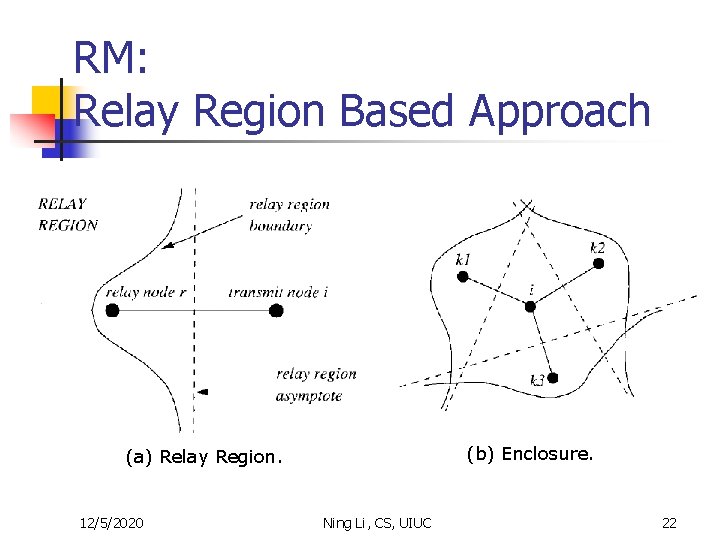
RM: Relay Region Based Approach (b) Enclosure. (a) Relay Region. 12/5/2020 Ning Li, CS, UIUC 22

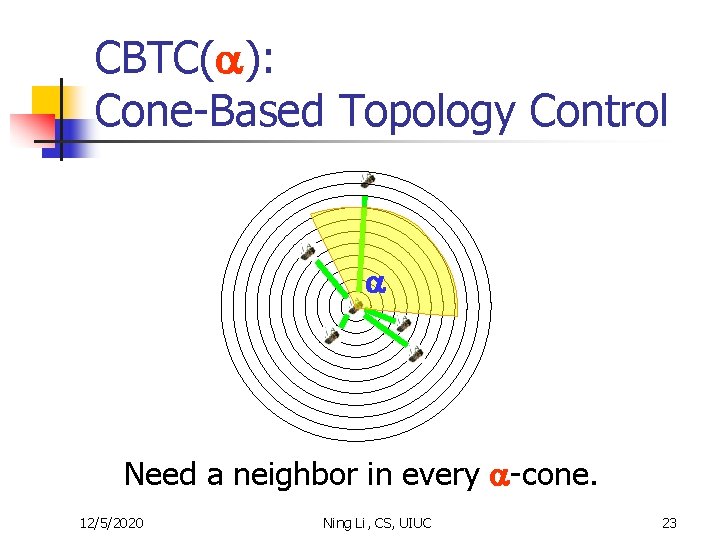
CBTC( ): Cone-Based Topology Control Need a neighbor in every -cone. 12/5/2020 Ning Li, CS, UIUC 23

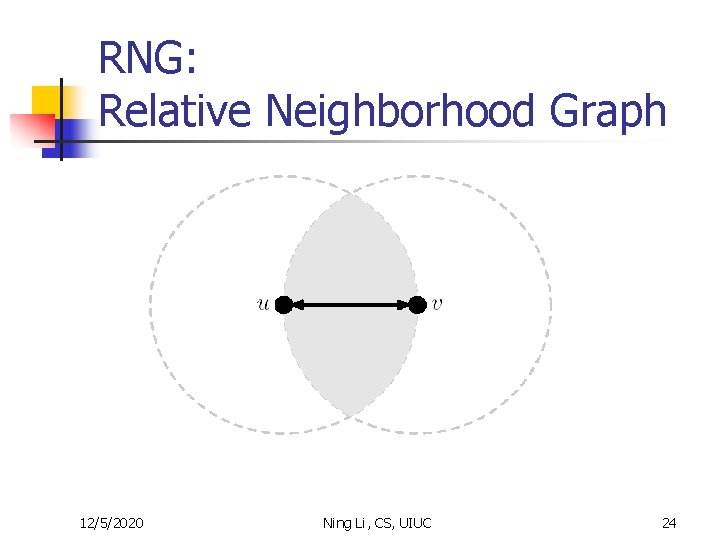
RNG: Relative Neighborhood Graph 12/5/2020 Ning Li, CS, UIUC 24