TKIP Temporal Key Integrity Protocol TKIP A cipher






- Slides: 18

TKIP

Temporal Key Integrity Protocol (TKIP) • A cipher suite based on old hardware (RC 4 cipher) – A transmitter calculates a keyed cryptographic message integrity code (MIC). TKIP appends the computed MIC. The receiver discards any frames with invalid MIC in TKIP is not perfect due to hardware constraints. Has a timeout countermeasure. – Uses a transmit sequence counter (TSC) for every frame. Defend replay attack. – Uses a key-mixing function to combine the temporal key, the transmitter address (TA), and the TSC into the seed (IV, key) for the RC 4 stream cipher

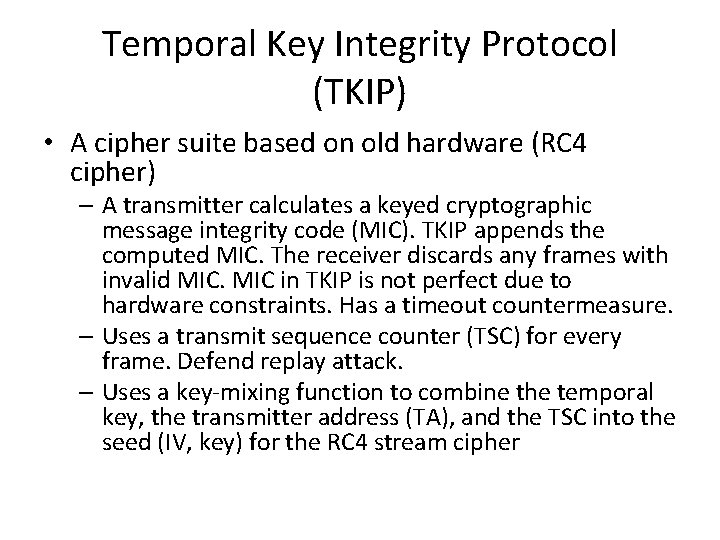
TKIP Encapsulation The figures are from http: //standards. ieee. org/getieee 802/download/802. 11 i-2004. pdf

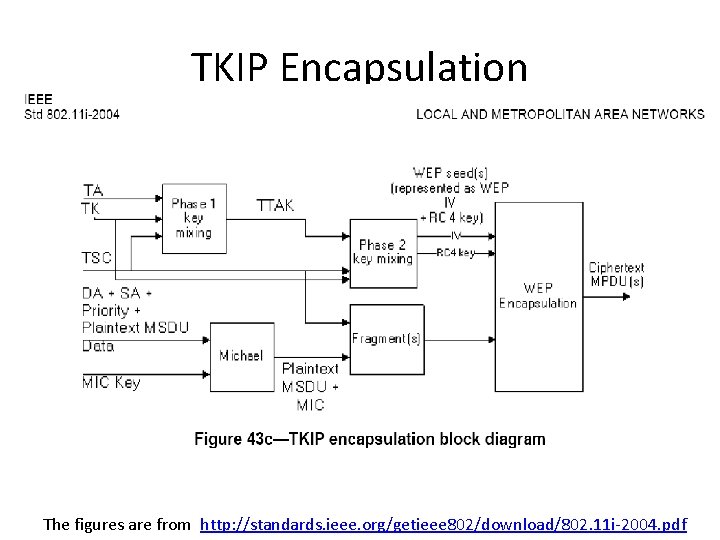
Decpsulation

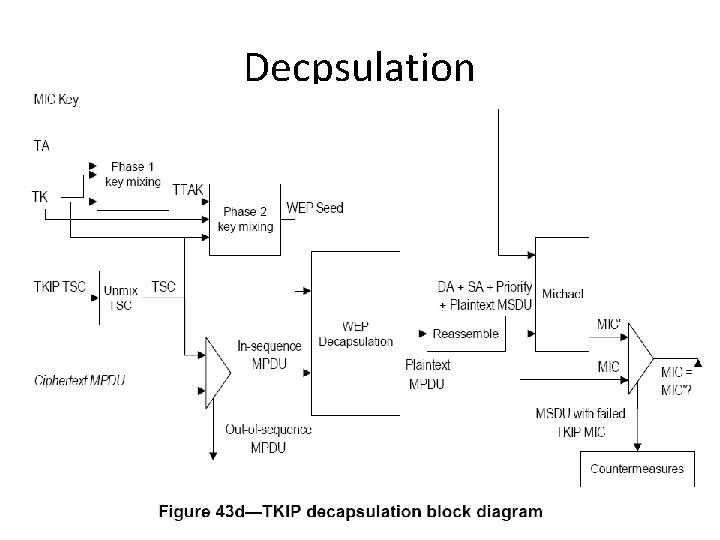
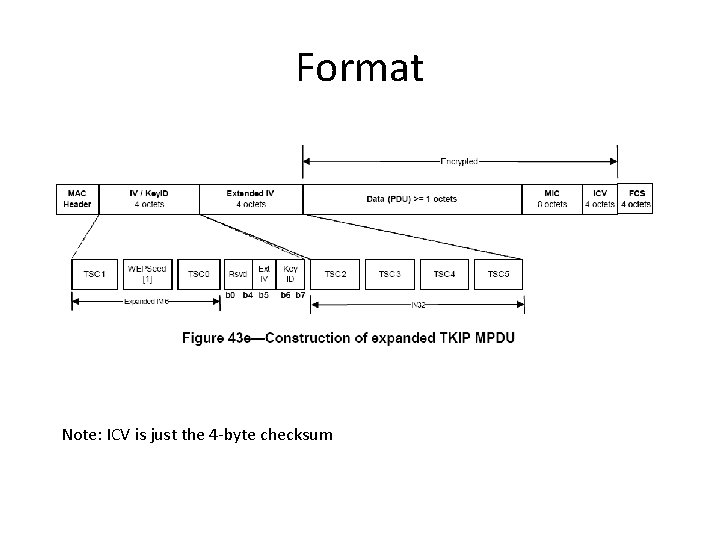
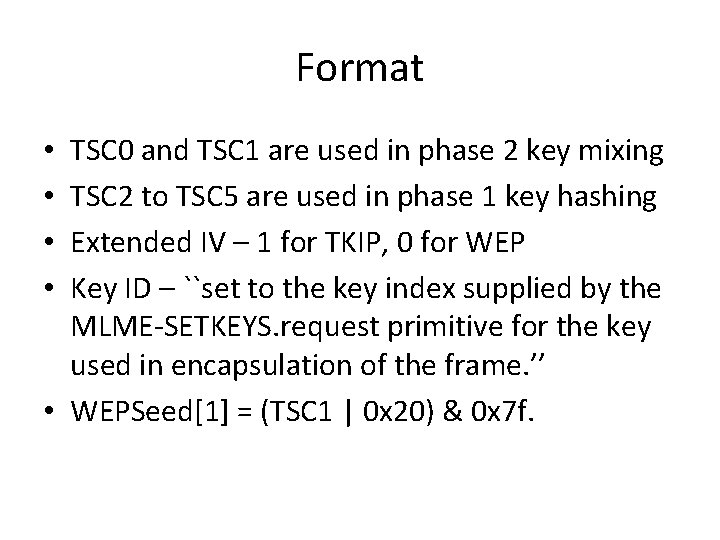
Format Note: ICV is just the 4 -byte checksum

Format TSC 0 and TSC 1 are used in phase 2 key mixing TSC 2 to TSC 5 are used in phase 1 key hashing Extended IV – 1 for TKIP, 0 for WEP Key ID – ``set to the key index supplied by the MLME-SETKEYS. request primitive for the key used in encapsulation of the frame. ’’ • WEPSeed[1] = (TSC 1 | 0 x 20) & 0 x 7 f. • •

MIC • WEP design allows the packet forgery. Attacks: – Bit-flipping attacks – Data (payload) truncation, concatenation, and splicing – Fragmentation attacks – Iterative guessing attacks against the key – Redirection by modifying the MPDU DA or RA field – Impersonation attacks by modifying the MPDU SA or TA field

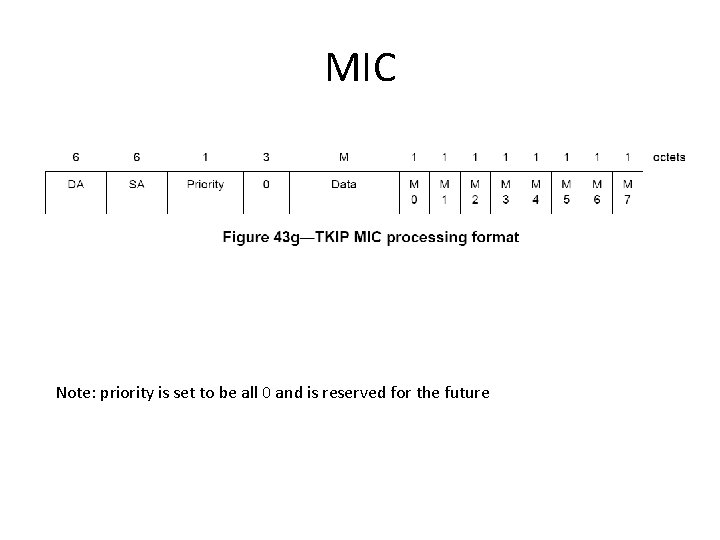
MIC Note: priority is set to be all 0 and is reserved for the future

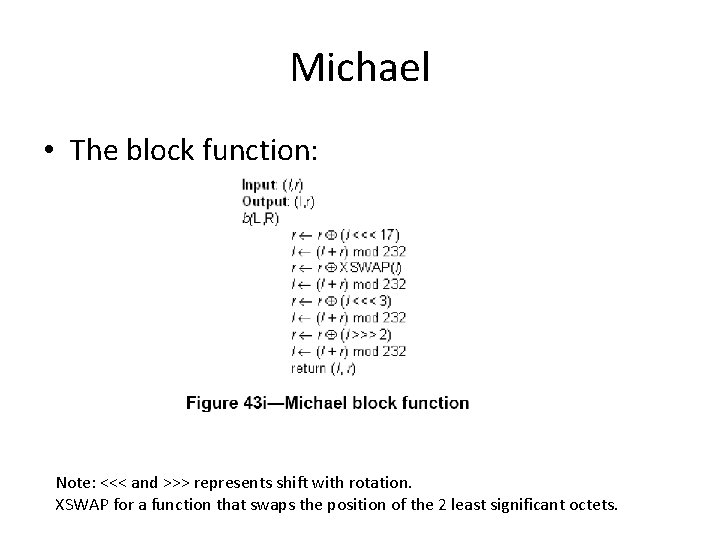
Michael • TKIP uses a customized algorithm, called Michael, to compute the 8 -byte MIC. – The message is appended by 0 x 5 a at the end, then 4 -7 0 x 00. Divided into a 32 -bit words: M 0 to Mn-1. – Then, iteratively does the following:

Michael • The block function: Note: <<< and >>> represents shift with rotation. XSWAP for a function that swaps the position of the 2 least significant octets.

MIC • TKIP MIC is not very strong. So, among other things, – TKIP MIC failure events should be logged. – ``The rate of MIC failures must be kept below two per minute. This implies that STAs and APs detecting two MIC failure events within 60 s must disable all receptions using TKIP for a period of 60 s. The slowdown makes it difficult for an attacker to make a large number of forgery attempts in a short time. ’’ – Also defined procedures in case of MIC failure.

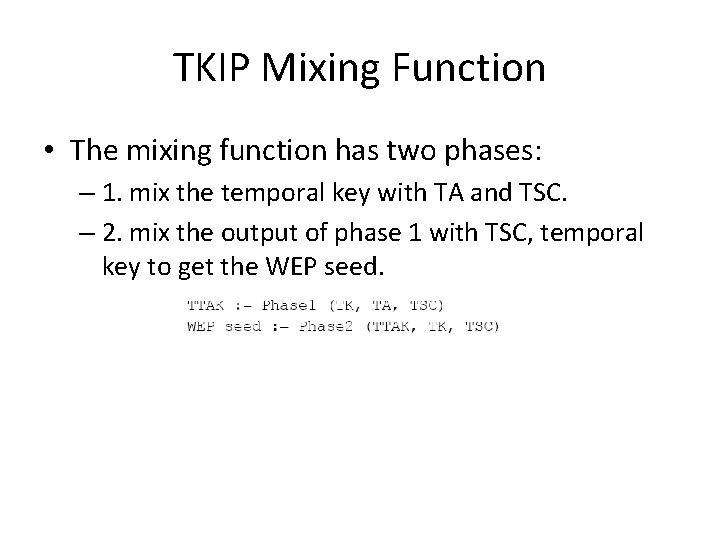
TKIP Mixing Function • The mixing function has two phases: – 1. mix the temporal key with TA and TSC. – 2. mix the output of phase 1 with TSC, temporal key to get the WEP seed.

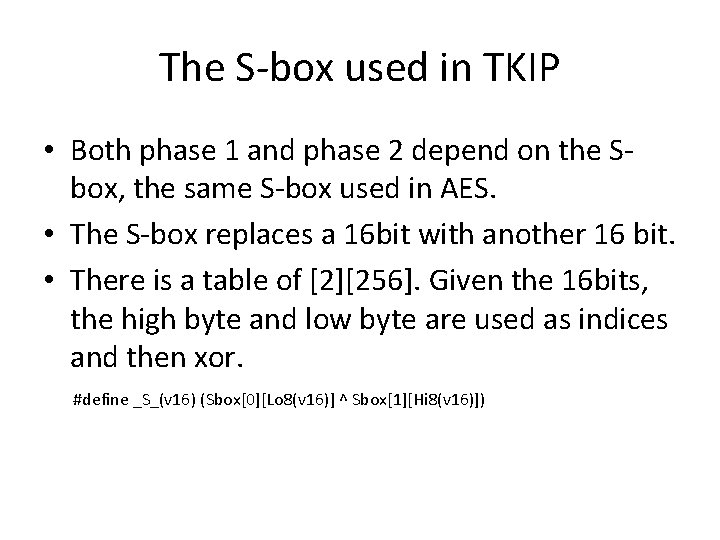
The S-box used in TKIP • Both phase 1 and phase 2 depend on the Sbox, the same S-box used in AES. • The S-box replaces a 16 bit with another 16 bit. • There is a table of [2][256]. Given the 16 bits, the high byte and low byte are used as indices and then xor. #define _S_(v 16) (Sbox[0][Lo 8(v 16)] ^ Sbox[1][Hi 8(v 16)])

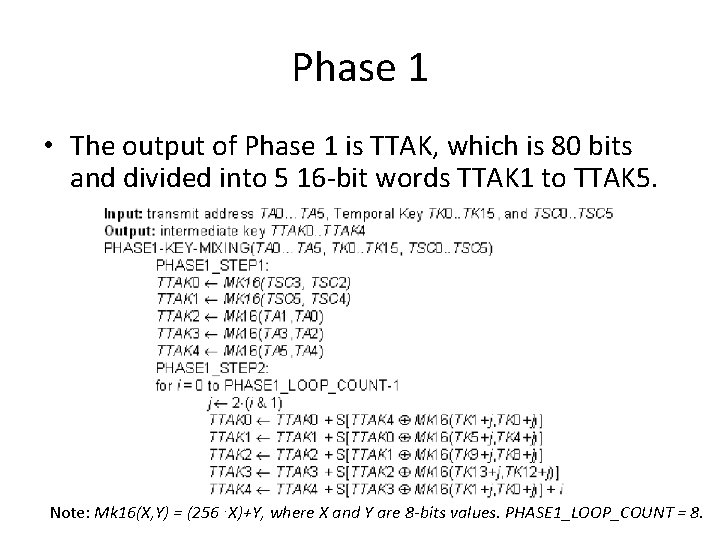
Phase 1 • The output of Phase 1 is TTAK, which is 80 bits and divided into 5 16 -bit words TTAK 1 to TTAK 5. Note: Mk 16(X, Y) = (256⋅X)+Y, where X and Y are 8 -bits values. PHASE 1_LOOP_COUNT = 8.

Phase 2 • Input: TTAK(80 bits), temporal key (128 bits), TSC( lower 16 bits). • Output: 128 bits (pre-frame key, WEP seed).

Phase 2 Note: PPK is a variable as 16 -bit array Note: Rot. R 1 is to rotate right by 1

Beyond TKIP • TKIP will become outdated. • The replacement is CTR with CBC-MAC Protocol (CCMP) which uses AES. • Page 57 -61.

Reading • http: //madwifi-project. org/browser/madwifi/trunk/net 80211/ieee 80211_crypto_tkip. c • Page 43 -57, http: //standards. ieee. org/getieee 802/download/802. 11 i-2004. pdf