Autokey Ciphers History The Autokey Cipher is almost







- Slides: 18

Autokey Ciphers

History • The Autokey Cipher is almost identical to the Vigenère Cipher – only it’s more secure • It was first invented by Girolamo Cardano and was made more secure by Vigenère

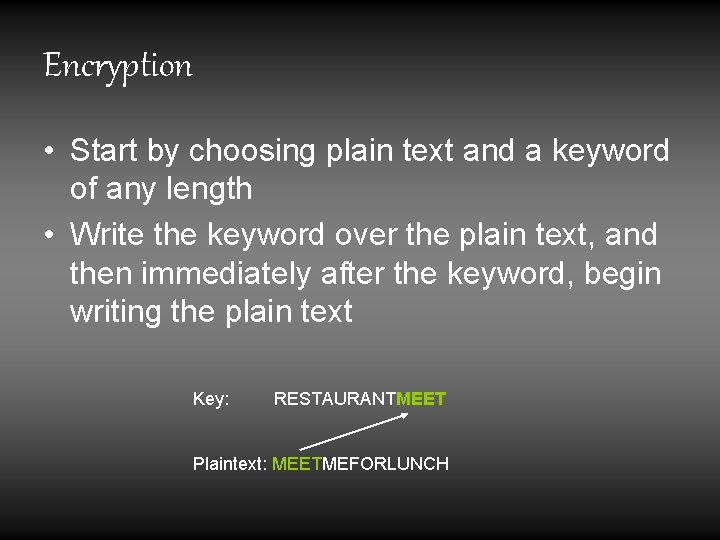
Encryption • Start by choosing plain text and a keyword of any length • Write the keyword over the plain text, and then immediately after the keyword, begin writing the plain text Key: RESTAURANTMEET Plaintext: MEETMEFORLUNCH

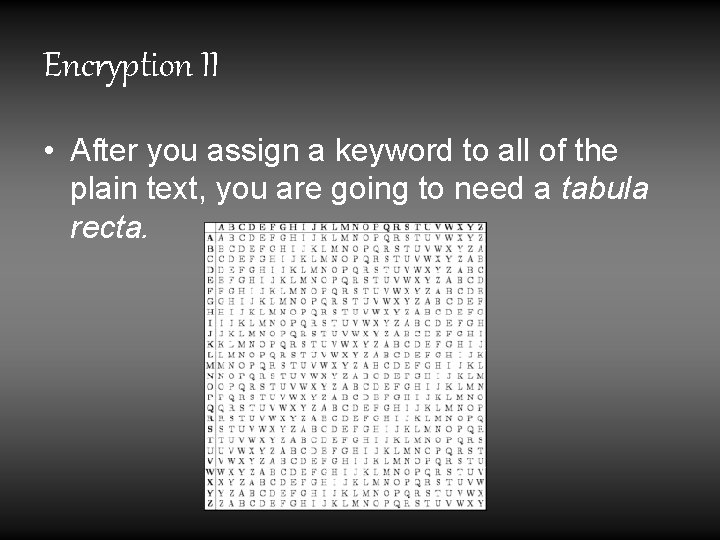
Encryption II • After you assign a keyword to all of the plain text, you are going to need a tabula recta.

Encryption III • In order to encrypt plain text, you locate the row with the first letter to be encrypted, and the column with the first letter of the key. The letter where the line and column cross is the ciphertext letter

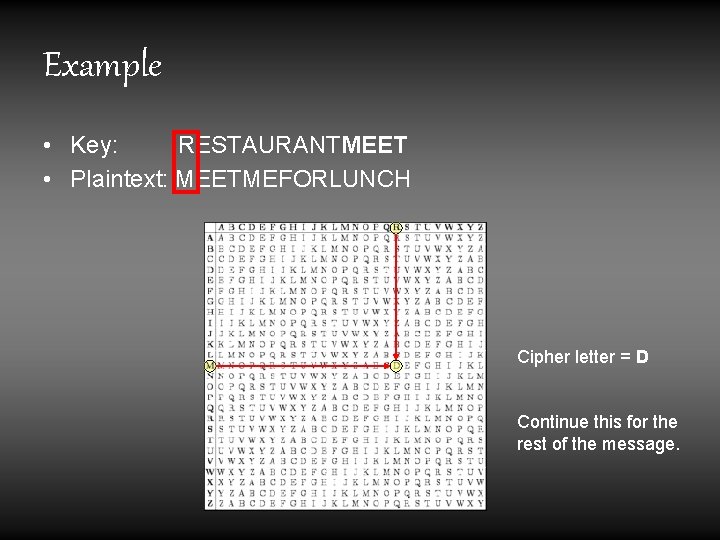
Example • Key: RESTAURANTMEET • Plaintext: MEETMEFORLUNCH Cipher letter = D Continue this for the rest of the message.

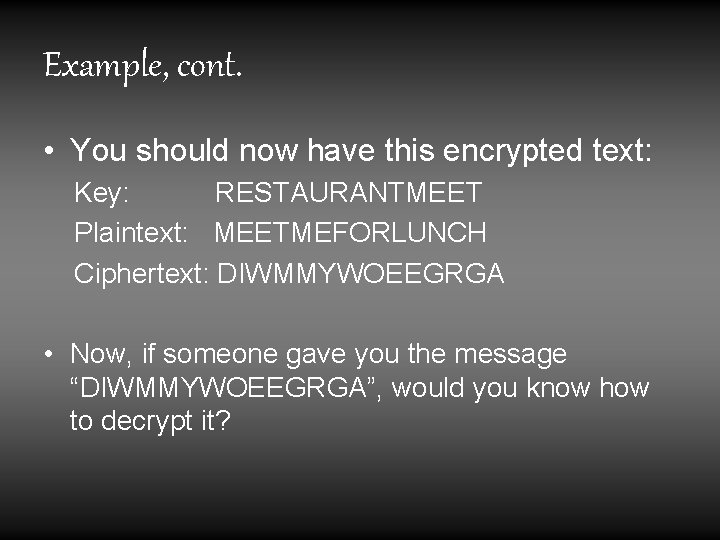
Example, cont. • You should now have this encrypted text: Key: RESTAURANTMEET Plaintext: MEETMEFORLUNCH Ciphertext: DIWMMYWOEEGRGA • Now, if someone gave you the message “DIWMMYWOEEGRGA”, would you know how to decrypt it?

Decryption • Assuming the buddy who sent you the secret message likes you, he probably message sent you the keyword, too. • With a key of RESTAURANT and ciphertext DIWMMYWOEEGRGA, find the key characters in the top-column header and the ciphertext characters in the table

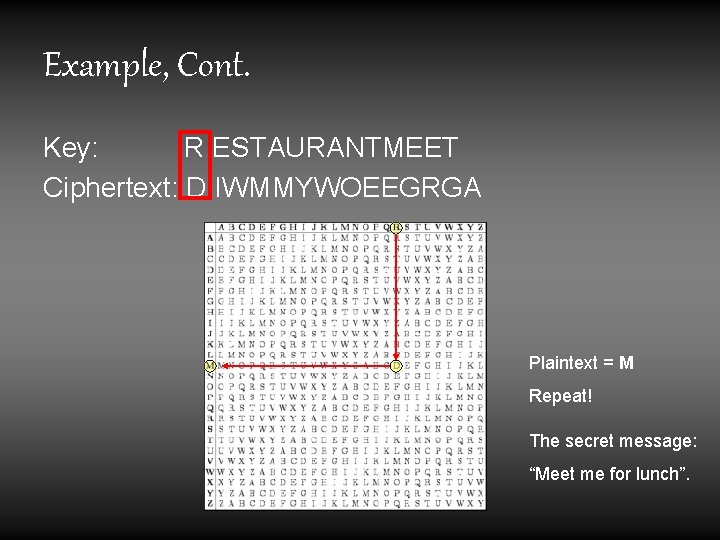
Example, Cont. Key: R ESTAURANTMEET Ciphertext: D IWMMYWOEEGRGA Plaintext = M Repeat! The secret message: “Meet me for lunch”.

Cryptanalysis • Now, say your buddy sent you the secret message, but didn’t give you the secret message password - you now have a wonderful problem!

How to solve it • Choose common trigrams or bigrams in all possible positions for the key. • Here, we use “the”. • Try it in all possible positions for the key

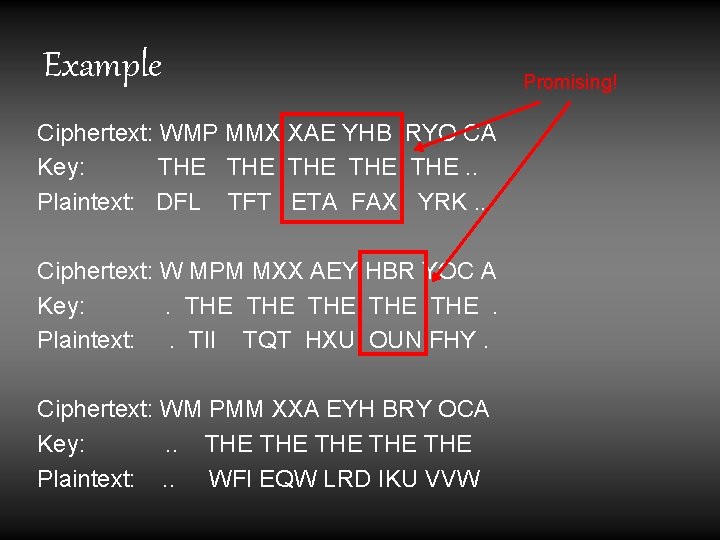
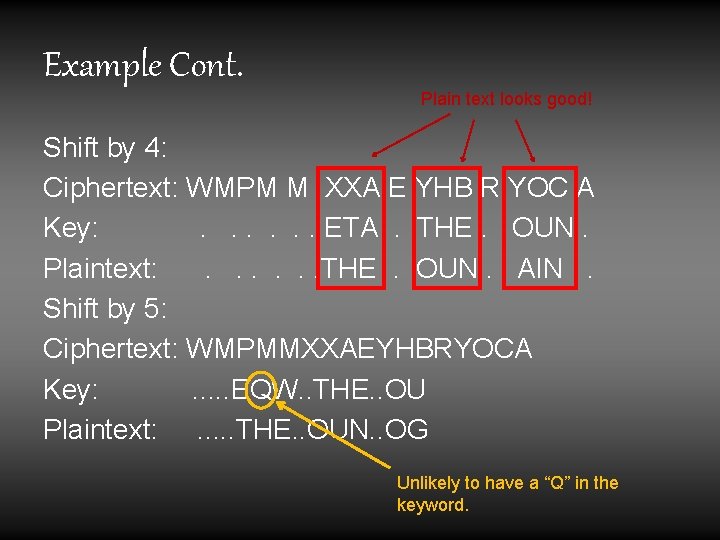
Example Ciphertext: WMP MMX XAE YHB RYO CA Key: THE THE THE. . Plaintext: DFL TFT ETA FAX YRK. . Ciphertext: W MPM MXX AEY HBR YOC A Key: . THE THE THE . Plaintext: . TII TQT HXU OUN FHY. Ciphertext: WM PMM XXA EYH BRY OCA Key: . . THE THE THE Plaintext: . . WFI EQW LRD IKU VVW Promising!

Example Cont. • We also know that some of the plain text is also in the key, to the right of the keyword • In the previous slide, we marked the possible plain text fragments “ETA”, “OUN” and “FAX” as promising • Now we will use these, plus “THE” to try and guess the keyword length

Example Cont. Plain text looks good! Shift by 4: Ciphertext: WMPM M XXA E YHB R YOC A Key: . . . . ETA . THE. OUN. Plaintext: . . . . THE . OUN. AIN . Shift by 5: Ciphertext: WMPMMXXAEYHBRYOCA Key: . . . EQW. . THE. . OU Plaintext: . . . THE. . OUN. . OG Unlikely to have a “Q” in the keyword.

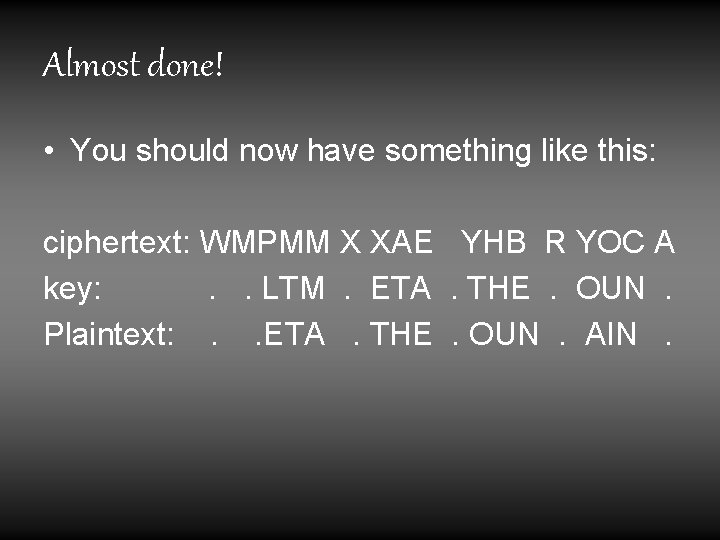
Example Cont. • Now we have to use our brains • The four letter shift looks good, so we can guess that the keyword is probably about 4 characters long • Through the “guess-and-check” method, we can fill in some blanks

Almost done! • You should now have something like this: ciphertext: WMPMM X XAE YHB R YOC A key: . . LTM . ETA . THE . OUN . Plaintext: . . ETA . THE . OUN . AIN .

The secret message? • “Meet at the fountain”. • …and no, Mr. Evans, that wasn’t “relatively pain-free. ”

Sources • http: //realmoftwelve. kryptos. info/toolbox/au tokey. html • http: //en. wikipedia. org/wiki/Autokey_cipher