The Compliance Game FISMA SP 800 53 HIPAA
- Slides: 13

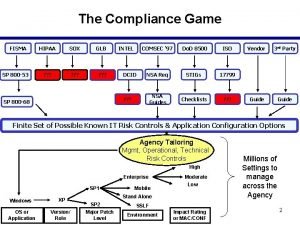
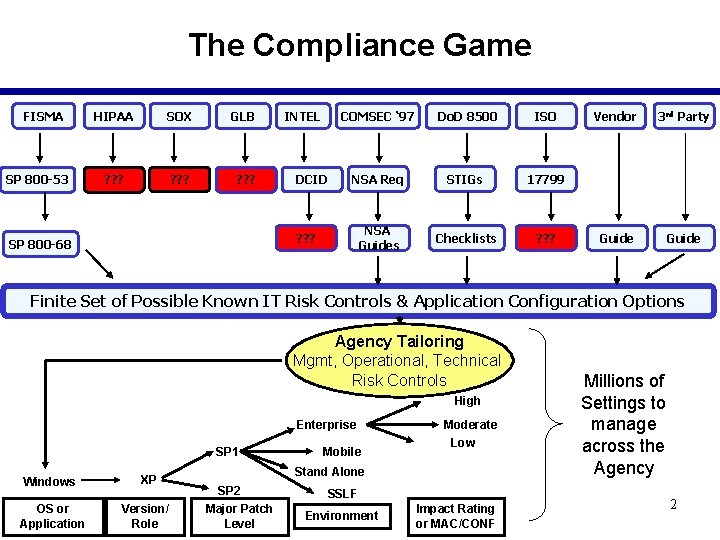
The Compliance Game FISMA SP 800 -53 HIPAA SOX GLB ? ? ? INTEL DCID COMSEC ‘ 97 Do. D 8500 ISO NSA Req STIGs 17799 NSA Guides Checklists ? ? ? SP 800 -68 Vendor 3 rd Party Guide Finite Set of Possible Known IT Risk Controls & Application Configuration Options Agency Tailoring Mgmt, Operational, Technical Risk Controls High Enterprise SP 1 Windows OS or Application XP Version/ Role Mobile Moderate Low Stand Alone SP 2 Major Patch Level SSLF Environment Impact Rating or MAC/CONF Millions of Settings to manage across the Agency 2

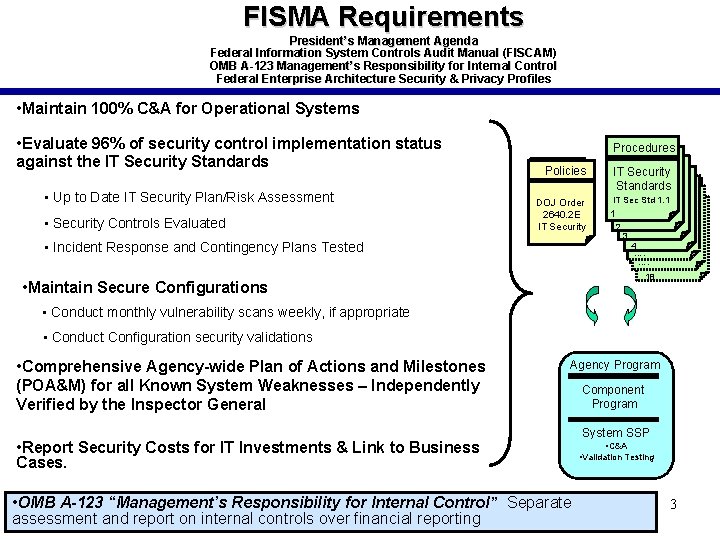
FISMA Requirements President’s Management Agenda Federal Information System Controls Audit Manual (FISCAM) OMB A-123 Management’s Responsibility for Internal Control Federal Enterprise Architecture Security & Privacy Profiles • Maintain 100% C&A for Operational Systems • Evaluate 96% of security control implementation status against the IT Security Standards • Up to Date IT Security Plan/Risk Assessment • Security Controls Evaluated Procedures Policies IT Security Standards DOJ Order 2640. 2 E IT Security IT Sec Std 1. 1 • Incident Response and Contingency Plans Tested 1 2 3 4 …. …. 18 • Maintain Secure Configurations • Conduct monthly vulnerability scans weekly, if appropriate • Conduct Configuration security validations • Comprehensive Agency-wide Plan of Actions and Milestones (POA&M) for all Known System Weaknesses – Independently Verified by the Inspector General Agency Program • Report Security Costs for IT Investments & Link to Business Cases. • OMB A-123 “Management’s Responsibility for Internal Control” Separate assessment and report on internal controls over financial reporting Component Program System SSP • C&A • Validation Testing 3

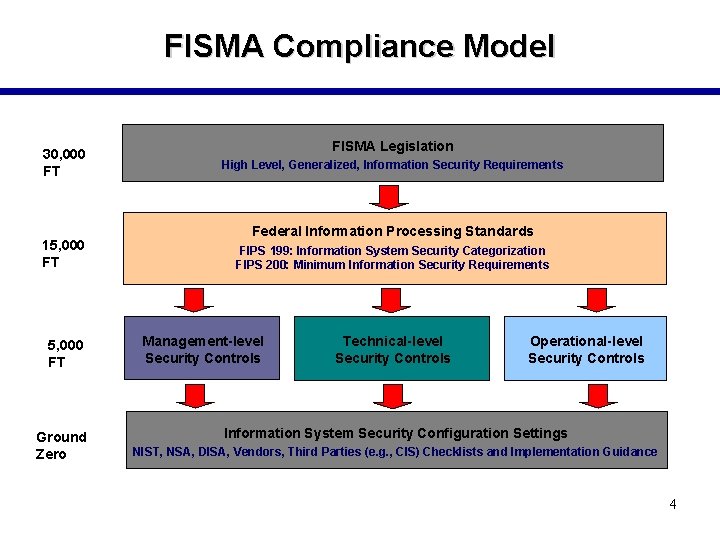
FISMA Compliance Model 30, 000 FT 15, 000 FT Ground Zero FISMA Legislation High Level, Generalized, Information Security Requirements Federal Information Processing Standards FIPS 199: Information System Security Categorization FIPS 200: Minimum Information Security Requirements Management-level Security Controls Technical-level Security Controls Operational-level Security Controls Information System Security Configuration Settings NIST, NSA, DISA, Vendors, Third Parties (e. g. , CIS) Checklists and Implementation Guidance 4

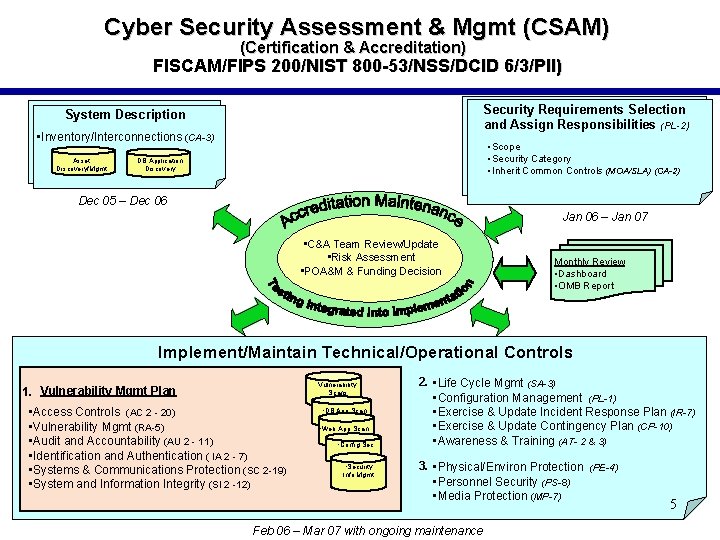
Cyber Security Assessment & Mgmt (CSAM) (Certification & Accreditation) FISCAM/FIPS 200/NIST 800 -53/NSS/DCID 6/3/PII) Security Requirements Selection and Assign Responsibilities (PL-2) System Description • Inventory/Interconnections (CA-3) Asset Discovery/Mgmt • Scope • Security Category • Inherit Common Controls (MOA/SLA) (CA-2) DB Application Discovery Dec 05 – Dec 06 Jan 06 – Jan 07 • C&A Team Review/Update • Risk Assessment • POA&M & Funding Decision Monthly Review • Dashboard • OMB Report Implement/Maintain Technical/Operational Controls Vulnerability Scans 1. Vulnerability Mgmt Plan • Access Controls (AC 2 - 20) • Vulnerability Mgmt (RA-5) • Audit and Accountability (AU 2 - 11) • Identification and Authentication ( IA 2 - 7) • Systems & Communications Protection (SC 2 -19) • System and Information Integrity (SI 2 -12) • DB App Scan • Web App Scan • Config Sec • Security Info Mgmt 2. • Life Cycle Mgmt (SA-3) • Configuration Management (PL-1) • Exercise & Update Incident Response Plan (IR-7) • Exercise & Update Contingency Plan (CP-10) • Awareness & Training (AT- 2 & 3) 3. • Physical/Environ Protection (PE-4) • Personnel Security (PS-8) • Media Protection (MP-7) Feb 06 – Mar 07 with ongoing maintenance 5

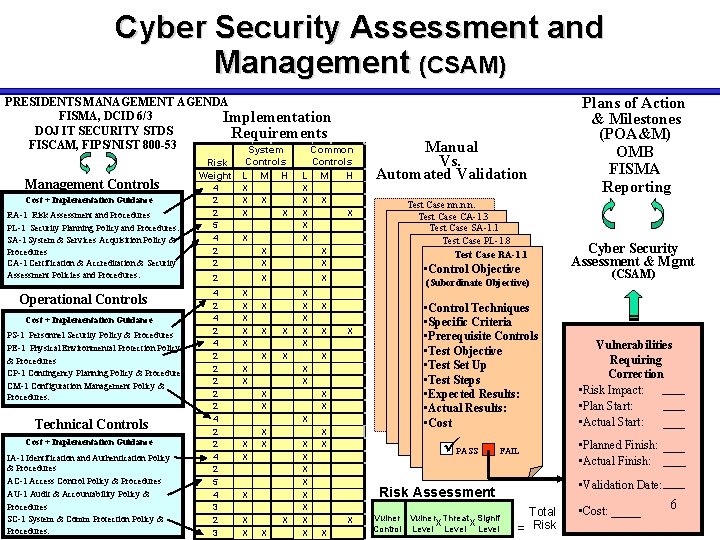
Cyber Security Assessment and Management (CSAM) PRESIDENTS MANAGEMENT AGENDA FISMA, DCID 6/3 Implementation DOJ IT SECURITY STDS Requirements FISCAM, FIPS/NIST 800 -53 System Common Management Controls Cost + Implementation Guidance RA-1 Risk Assessment and Procedures PL-1 Security Planning Policy and Procedures. SA-1 System & Services Acquisition Policy & Procedures CA-1 Certification & Accreditation & Security Assessment Policies and Procedures. Operational Controls Cost + Implementation Guidance PS-1 Personnel Security Policy & Procedures PE-1 Physical Environmental Protection Policy & Procedures CP-1 Contingency Planning Policy & Procedures CM-1 Configuration Management Policy & Procedures. Technical Controls Cost + Implementation Guidance IA-1 Identification and Authentication Policy & Procedures AC-1 Access Control Policy & Procedures AU-1 Audit & Accountability Policy & Procedures SC-1 System & Comm Protection Policy & Procedures. Controls Risk Weight L M H 4 2 2 5 4 2 2 X X X 2 4 2 4 2 2 2 4 2 5 4 3 2 3 X X X Controls L M H X X X X X X X (Subordinate Objective) X X X X X X X Test Case nn. n. n. Test Case CA-1. 3 Test Case SA-1. 1 Test Case PL-1. 8 Test Case RA-1. 1 • Control Objective X X Manual Vs. Automated Validation X X • Control Techniques • Specific Criteria • Prerequisite Controls • Test Objective • Test Set Up • Test Steps • Expected Results: • Actual Results: • Cost ü PASS FAIL X Vulner Threat Signif X X Control Level Cyber Security Assessment & Mgmt (CSAM) Vulnerabilities Requiring Correction • Risk Impact: • Plan Start: • Actual Start: • Planned Finish: • Actual Finish: • Validation Date: Risk Assessment X Plans of Action & Milestones (POA&M) OMB FISMA Reporting Total = Risk • Cost: _____ 6

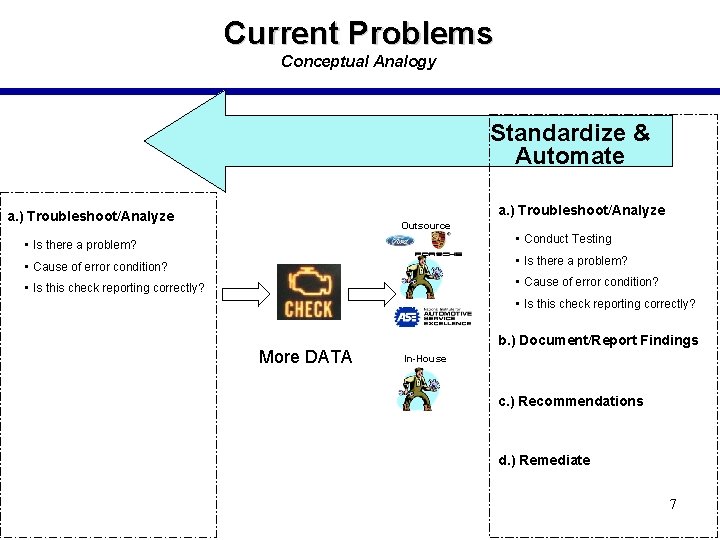
Current Problems Conceptual Analogy Standardize & Automate a. ) Troubleshoot/Analyze Outsource • Is there a problem? • Conduct Testing • Cause of error condition? • Is there a problem? • Is this check reporting correctly? • Cause of error condition? • Is this check reporting correctly? More DATA b. ) Document/Report Findings In-House c. ) Recommendations d. ) Remediate 7

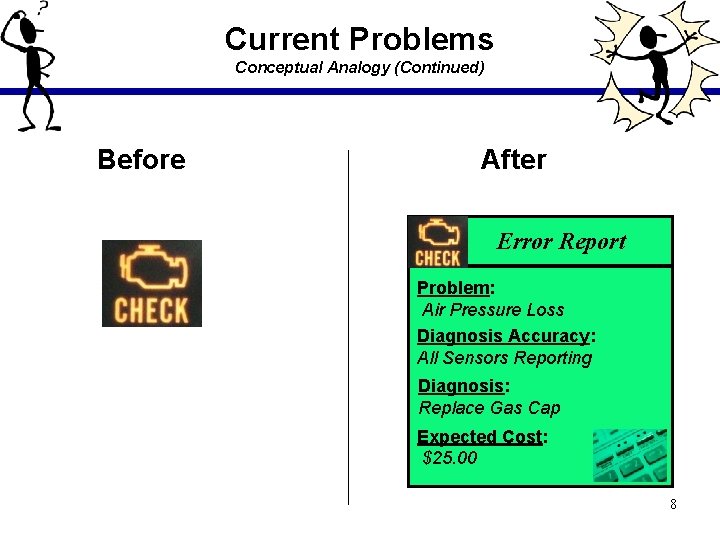
Current Problems Conceptual Analogy (Continued) Before After Error Report Problem: Air Pressure Loss Diagnosis Accuracy: All Sensors Reporting Diagnosis: Replace Gas Cap Expected Cost: $25. 00 8

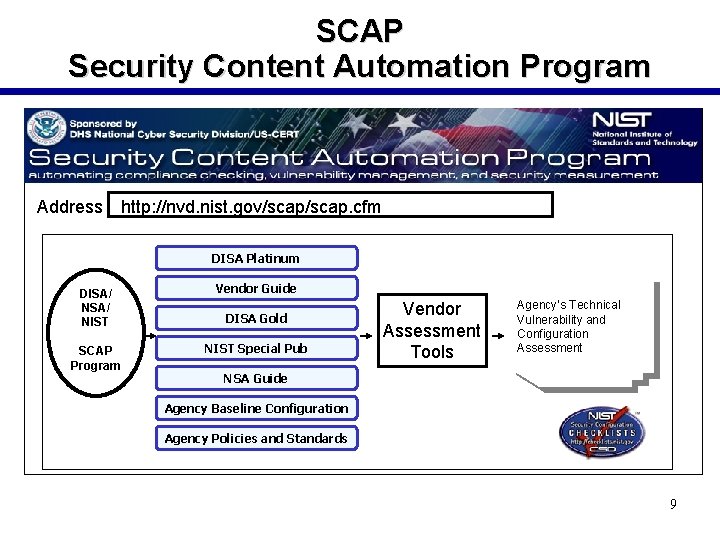
SCAP Security Content Automation Program Address http: //nvd. nist. gov/scap. cfm DISA Platinum DISA/ NIST SCAP Program Vendor Guide DISA Gold NIST Special Pub Vendor Assessment Tools Agency’s Technical Vulnerability and Configuration Assessment NSA Guide Agency Baseline Configuration Agency Policies and Standards 9

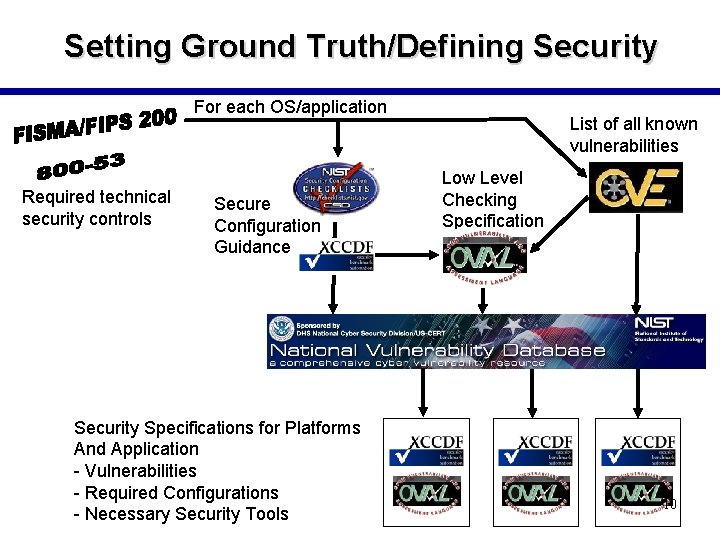
Setting Ground Truth/Defining Security For each OS/application Required technical security controls Secure Configuration Guidance Security Specifications for Platforms And Application - Vulnerabilities - Required Configurations - Necessary Security Tools List of all known vulnerabilities Low Level Checking Specification 10

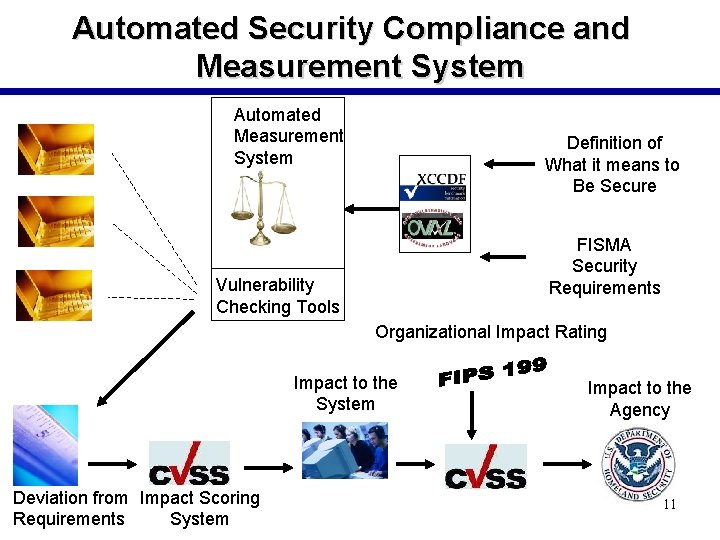
Automated Security Compliance and Measurement System Automated Measurement System Definition of What it means to Be Secure FISMA Security Requirements Vulnerability Checking Tools Organizational Impact Rating Impact to the System Deviation from Impact Scoring Requirements System Impact to the Agency 11

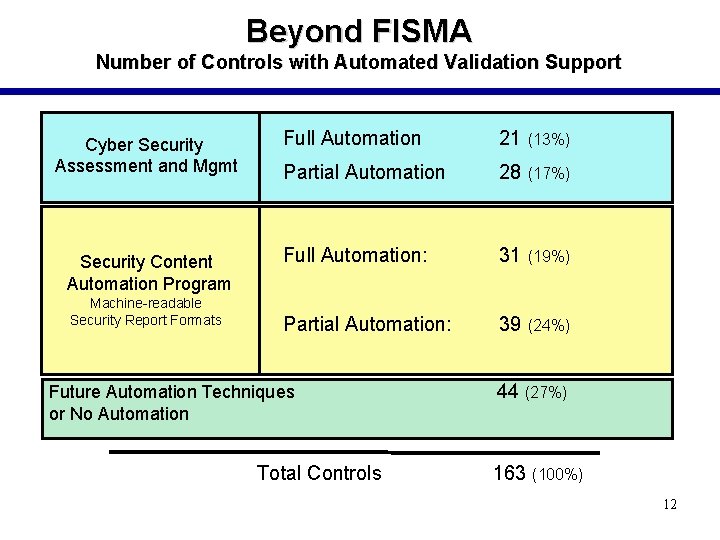
Beyond FISMA Number of Controls with Automated Validation Support Cyber Security Assessment and Mgmt Full Automation 21 (13%) Partial Automation 28 (17%) Security Content Automation Program Full Automation: 31 (19%) Partial Automation: 39 (24%) Machine-readable Security Report Formats Future Automation Techniques or No Automation Total Controls 44 (27%) 163 (100%) 12

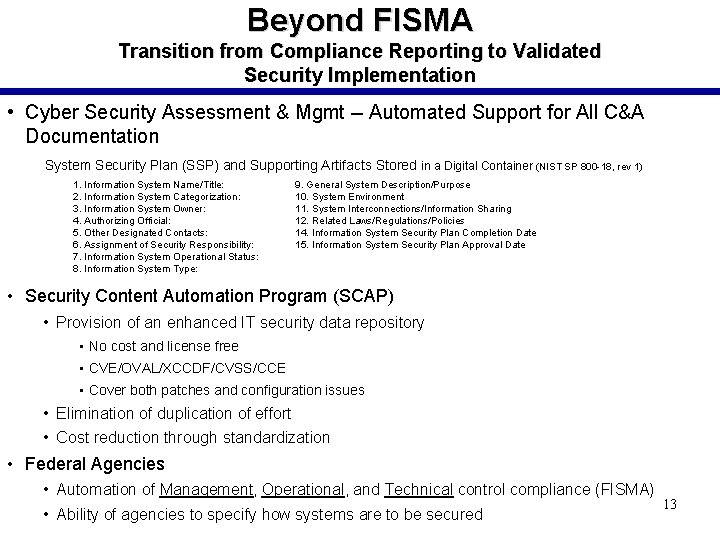
Beyond FISMA Transition from Compliance Reporting to Validated Security Implementation • Cyber Security Assessment & Mgmt -- Automated Support for All C&A Documentation System Security Plan (SSP) and Supporting Artifacts Stored in a Digital Container (NIST SP 800 -18, rev 1) 1. Information System Name/Title: 2. Information System Categorization: 3. Information System Owner: 4. Authorizing Official: 5. Other Designated Contacts: 6. Assignment of Security Responsibility: 7. Information System Operational Status: 8. Information System Type: 9. General System Description/Purpose 10. System Environment 11. System Interconnections/Information Sharing 12. Related Laws/Regulations/Policies 14. Information System Security Plan Completion Date 15. Information System Security Plan Approval Date • Security Content Automation Program (SCAP) • Provision of an enhanced IT security data repository • No cost and license free • CVE/OVAL/XCCDF/CVSS/CCE • Cover both patches and configuration issues • Elimination of duplication of effort • Cost reduction through standardization • Federal Agencies • Automation of Management, Operational, and Technical control compliance (FISMA) 13 • Ability of agencies to specify how systems are to be secured

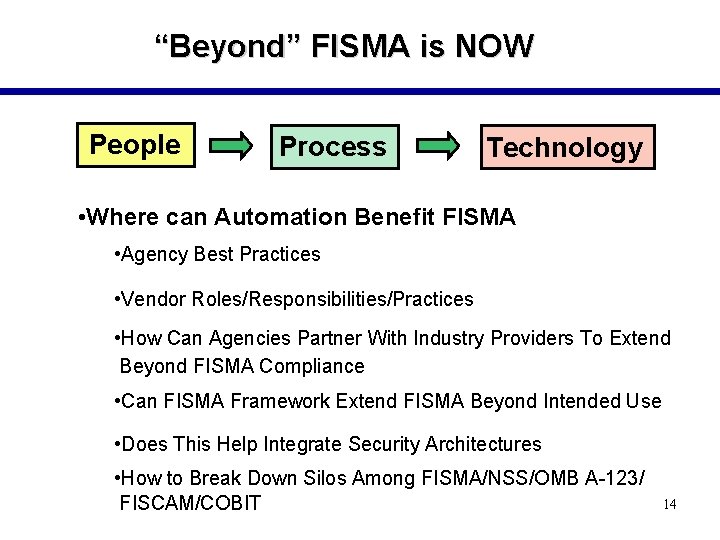
“Beyond” FISMA is NOW People Process Technology • Where can Automation Benefit FISMA • Agency Best Practices • Vendor Roles/Responsibilities/Practices • How Can Agencies Partner With Industry Providers To Extend Beyond FISMA Compliance • Can FISMA Framework Extend FISMA Beyond Intended Use • Does This Help Integrate Security Architectures • How to Break Down Silos Among FISMA/NSS/OMB A-123/ FISCAM/COBIT 14
 Joint commission and hipaa compliance
Joint commission and hipaa compliance Ada hipaa compliance kit
Ada hipaa compliance kit 200 + 200 = 400
200 + 200 = 400 Fmi moodle
Fmi moodle Fisma overview
Fisma overview Fiscam vs fisma
Fiscam vs fisma Ig maturity model
Ig maturity model Fisma reporting requirements
Fisma reporting requirements Becoming hipaa compliant
Becoming hipaa compliant Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs Louisiana hipaa laws
Louisiana hipaa laws What does tpo stand for in hipaa
What does tpo stand for in hipaa Hippa cow
Hippa cow Hipaa principles
Hipaa principles