T C P Also called IPng IP next




- Slides: 32

T C P Also called , IPng – “IP next generation” Next Generation: IPv 6 and ICMPv 6 / I P Recall IPv 4 provides host-to-host or hop-to -hop communication Recall UDP/TCP provide end-to-end or process-to-process communication Dr. Clincy 1

T Why IPv 6 ? 3 major reasons C Recall that (1) subnetting, (2) classless addressing, (3) DHCP P (dynamic address allocation) and (4) NAT all contributed to better / I P utilization of the 32 -bit address space - despite these solutions, address depletion is still an issue There are numerous applications on the rise that require streaming real-time audio and video – and real-time transmission requires minimum delay and reservation-of-resources strategies – and IPv 4 isn’t designed for these strategies Over the last few years, there has been a much greater demand for security and for the Internet to accommodate encryption and authentication of data for some applications – and IPv 4 doesn’t provide encryption or authentication Dr. Clincy 2

T Why IPv 6 ? C IPv 6 was proposed in overcoming IPv 4’s deficiencies P / I P IPv 6 has these advantages over IPv 4: 1. larger address space – 128 bits 2. better header format – options can be inserted or not 3. new options – additional functionalities 4. allowance for extension – protocol can be extended for newer technologies 5. support for resource allocation – enables the Tx to request special handling 6. support for more security – provides encryption and authentication Related protocols were either modified or dropped for IPv 6 - ICMP was modified (ICMPv 6) - ARP and IGMP in version 4 were combined in ICMPv 6 - RARP was dropped - RIP and OSPF were slightly modified Dr. Clincy 3

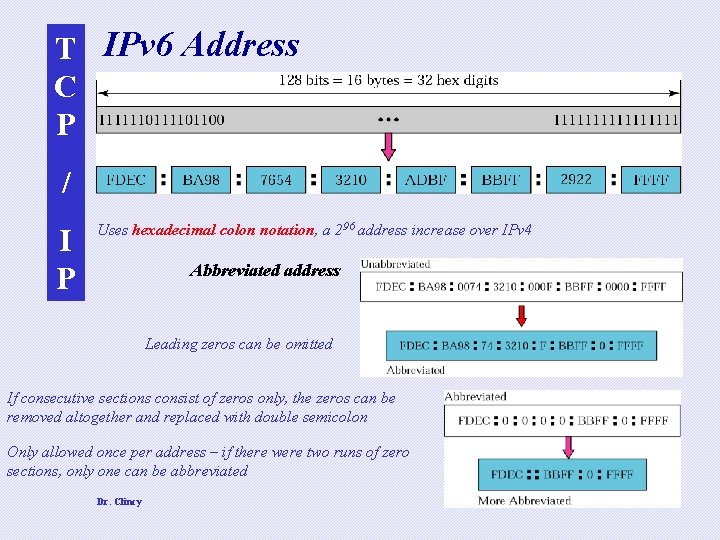
T IPv 6 Address C P / I P Uses hexadecimal colon notation, a 296 address increase over IPv 4 Abbreviated address Leading zeros can be omitted If consecutive sections consist of zeros only, the zeros can be removed altogether and replaced with double semicolon Only allowed once per address – if there were two runs of zero sections, only one can be abbreviated Dr. Clincy 4

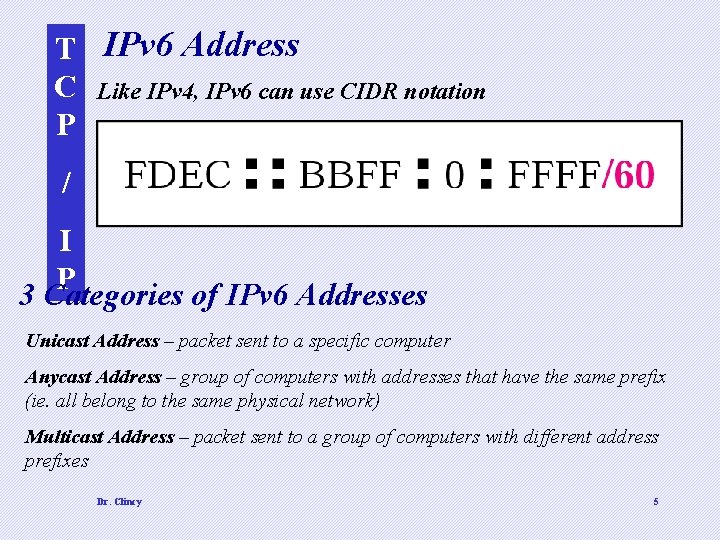
T IPv 6 Address C Like IPv 4, IPv 6 can use CIDR notation P / I P 3 Categories of IPv 6 Addresses Unicast Address – packet sent to a specific computer Anycast Address – group of computers with addresses that have the same prefix (ie. all belong to the same physical network) Multicast Address – packet sent to a group of computers with different address prefixes Dr. Clincy 5

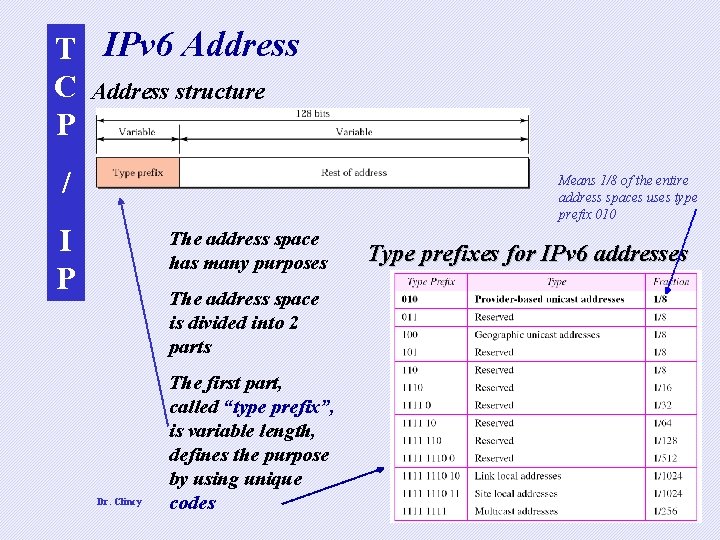
T IPv 6 Address C Address structure P / Means 1/8 of the entire address spaces uses type prefix 010 I P The address space has many purposes Type prefixes for IPv 6 addresses The address space is divided into 2 parts Dr. Clincy The first part, called “type prefix”, is variable length, defines the purpose by using unique codes 6

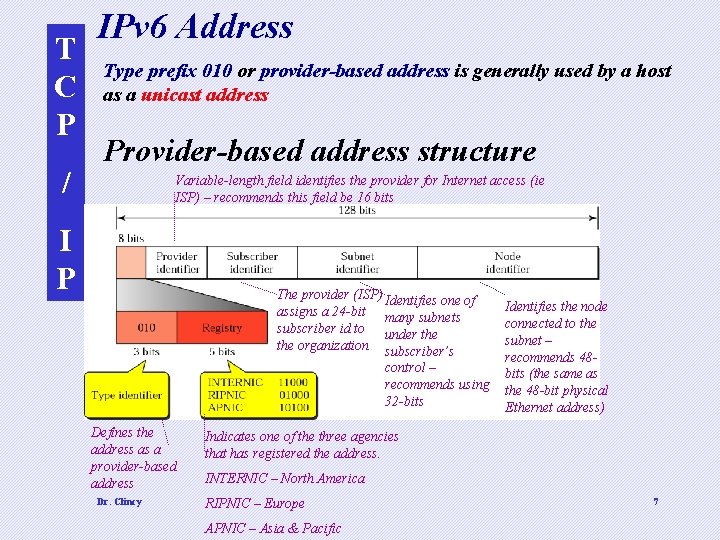
T C P / IPv 6 Address Type prefix 010 or provider-based address is generally used by a host as a unicast address Provider-based address structure Variable-length field identifies the provider for Internet access (ie ISP) – recommends this field be 16 bits I P The provider (ISP) Identifies one of assigns a 24 -bit many subnets subscriber id to under the organization subscriber’s control – recommends using 32 -bits Defines the address as a provider-based address Dr. Clincy Identifies the node connected to the subnet – recommends 48 bits (the same as the 48 -bit physical Ethernet address) Indicates one of the three agencies that has registered the address. INTERNIC – North America RIPNIC – Europe APNIC – Asia & Pacific 7

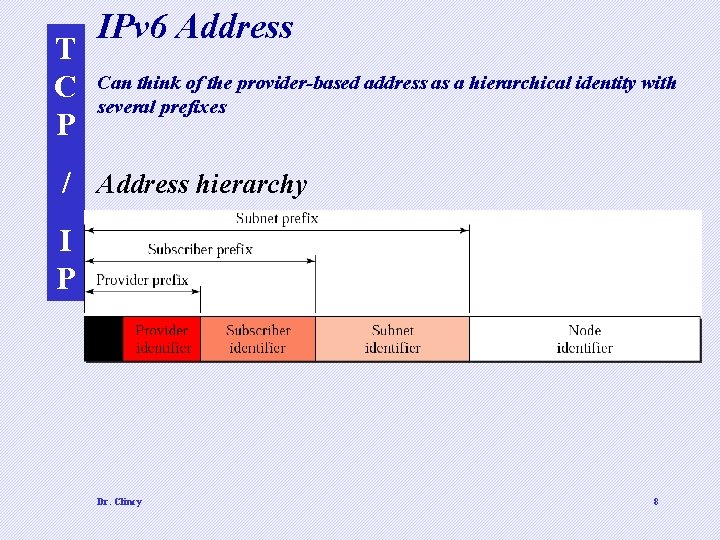
T C P IPv 6 Address Can think of the provider-based address as a hierarchical identity with several prefixes / Address hierarchy I P Dr. Clincy 8

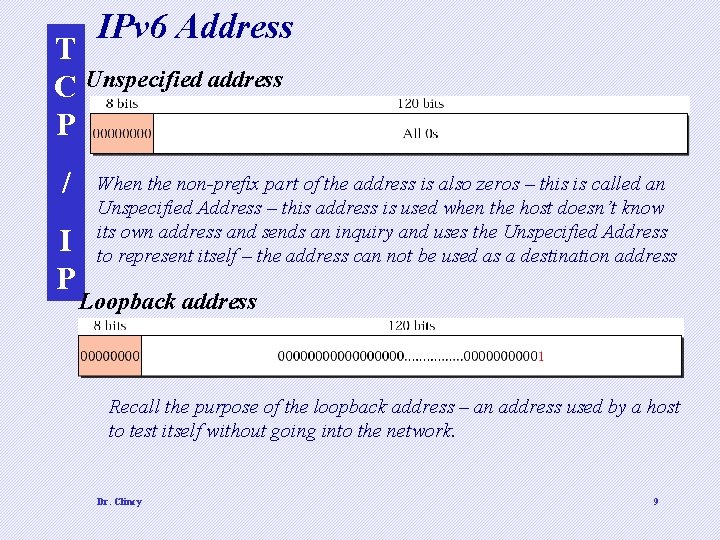
IPv 6 Address T C Unspecified address P / I P When the non-prefix part of the address is also zeros – this is called an Unspecified Address – this address is used when the host doesn’t know its own address and sends an inquiry and uses the Unspecified Address to represent itself – the address can not be used as a destination address Loopback address Recall the purpose of the loopback address – an address used by a host to test itself without going into the network. Dr. Clincy 9

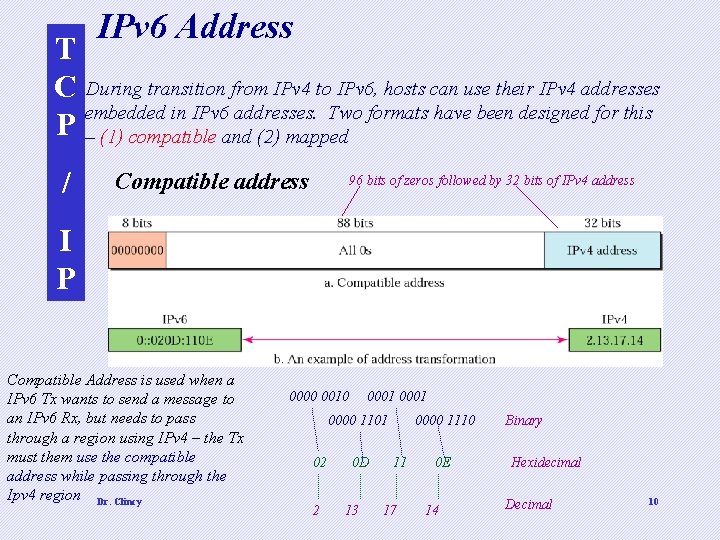
IPv 6 Address T C During transition from IPv 4 to IPv 6, hosts can use their IPv 4 addresses embedded in IPv 6 addresses. Two formats have been designed for this P – (1) compatible and (2) mapped / Compatible address 96 bits of zeros followed by 32 bits of IPv 4 address I P Compatible Address is used when a IPv 6 Tx wants to send a message to an IPv 6 Rx, but needs to pass through a region using IPv 4 – the Tx must them use the compatible address while passing through the Ipv 4 region Dr. Clincy 0000 0010 0001 0000 1101 02 2 0 D 13 0000 1110 11 17 0 E 14 Binary Hexidecimal Decimal 10

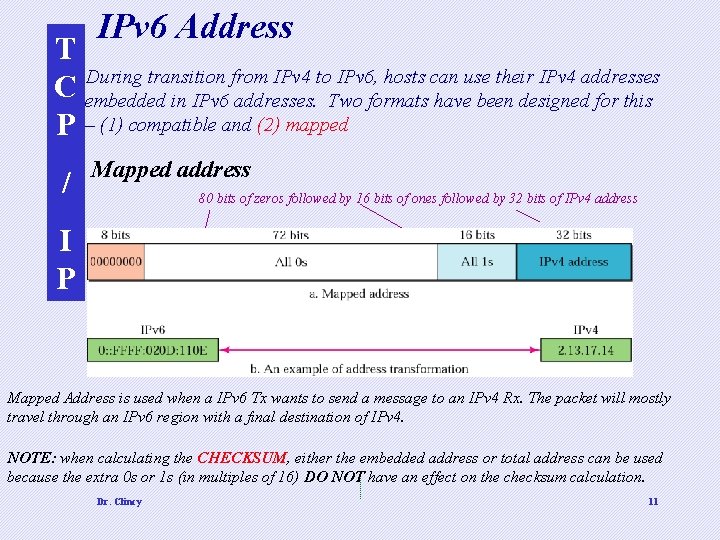
IPv 6 Address T During transition from IPv 4 to IPv 6, hosts can use their IPv 4 addresses C embedded in IPv 6 addresses. Two formats have been designed for this P – (1) compatible and (2) mapped / Mapped address 80 bits of zeros followed by 16 bits of ones followed by 32 bits of IPv 4 address I P Mapped Address is used when a IPv 6 Tx wants to send a message to an IPv 4 Rx. The packet will mostly travel through an IPv 6 region with a final destination of IPv 4. NOTE: when calculating the CHECKSUM, either the embedded address or total address can be used because the extra 0 s or 1 s (in multiples of 16) DO NOT have an effect on the checksum calculation. Dr. Clincy 11

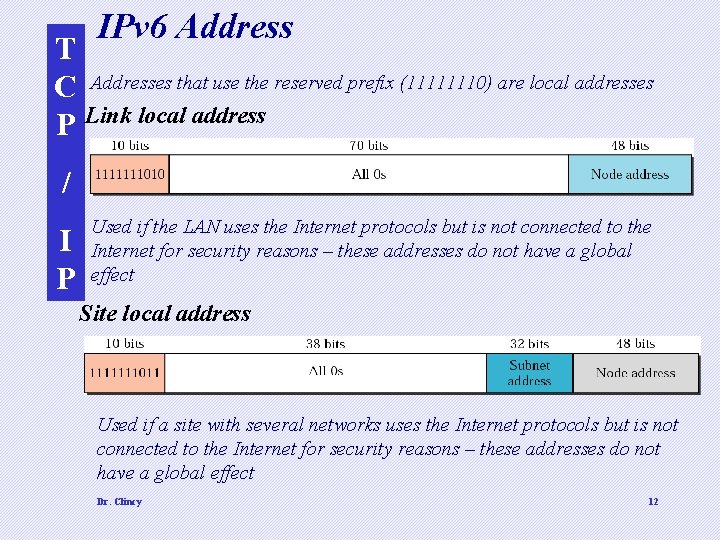
IPv 6 Address T C Addresses that use the reserved prefix (11111110) are local addresses P Link local address / I P Used if the LAN uses the Internet protocols but is not connected to the Internet for security reasons – these addresses do not have a global effect Site local address Used if a site with several networks uses the Internet protocols but is not connected to the Internet for security reasons – these addresses do not have a global effect Dr. Clincy 12

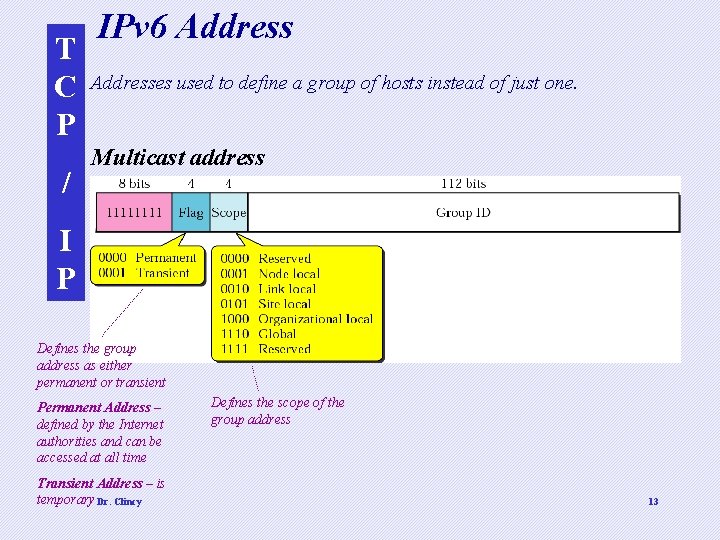
T C P / IPv 6 Addresses used to define a group of hosts instead of just one. Multicast address I P Defines the group address as either permanent or transient Permanent Address – defined by the Internet authorities and can be accessed at all time Transient Address – is temporary Dr. Clincy Defines the scope of the group address 13

T C P Next Generation: IPv 6 and ICMPv 6 / I P . . Continuing … Dr. Clincy 14

T C P IPv 6 Packet / I P Dr. Clincy 15

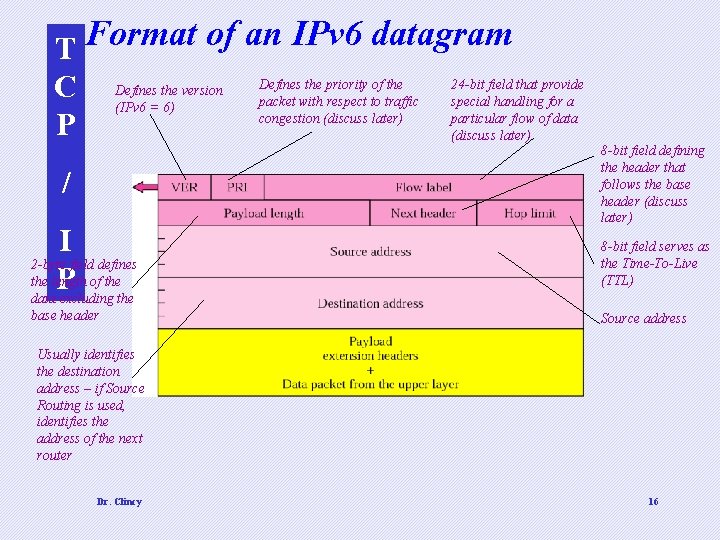
T Format of an IPv 6 datagram Defines the priority of the 24 -bit field that provide the version C Defines packet with respect to traffic special handling for a (IPv 6 = 6) congestion (discuss later) particular flow of data P (discuss later) / I 2 -byte field defines the length of the P data excluding the base header 8 -bit field defining the header that follows the base header (discuss later) 8 -bit field serves as the Time-To-Live (TTL) Source address Usually identifies the destination address – if Source Routing is used, identifies the address of the next router Dr. Clincy 16

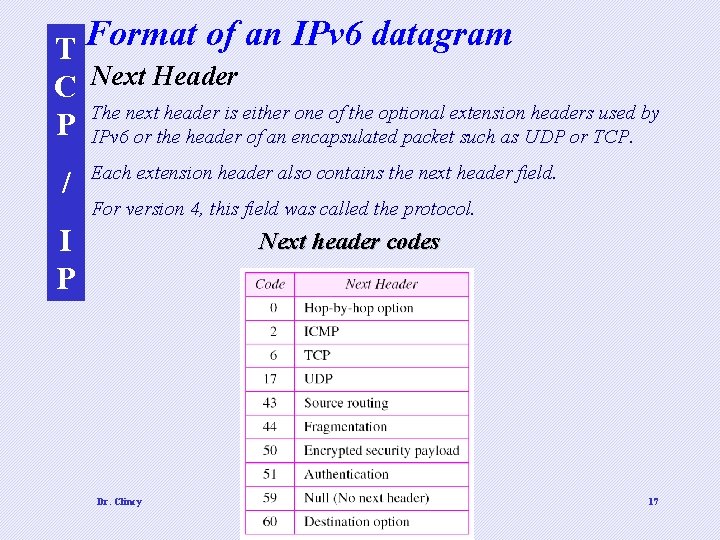
T Format of an IPv 6 datagram C Next Header The next header is either one of the optional extension headers used by P IPv 6 or the header of an encapsulated packet such as UDP or TCP. / Each extension header also contains the next header field. For version 4, this field was called the protocol. I P Next header codes Dr. Clincy 17

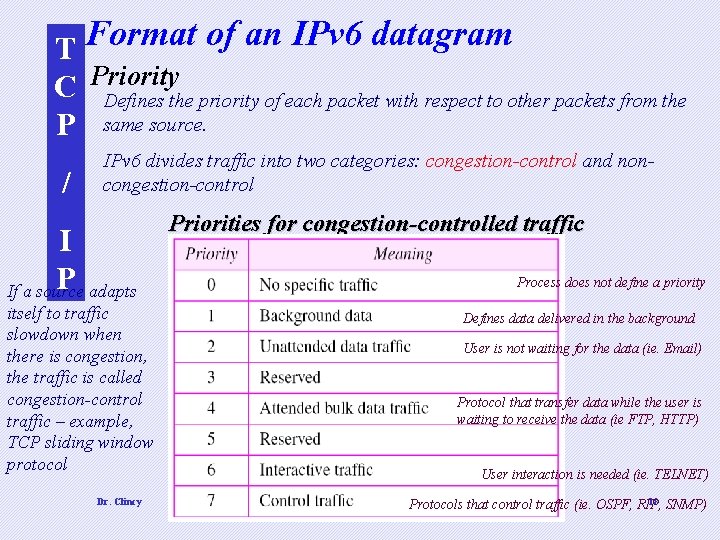
T Format of an IPv 6 datagram C Priority Defines the priority of each packet with respect to other packets from the P same source. / IPv 6 divides traffic into two categories: congestion-control and noncongestion-control I P adapts If a source itself to traffic slowdown when there is congestion, the traffic is called congestion-control traffic – example, TCP sliding window protocol Dr. Clincy Priorities for congestion-controlled traffic Process does not define a priority Defines data delivered in the background User is not waiting for the data (ie. Email) Protocol that transfer data while the user is waiting to receive the data (ie FTP, HTTP) User interaction is needed (ie. TELNET) 18 SNMP) Protocols that control traffic (ie. OSPF, RIP,

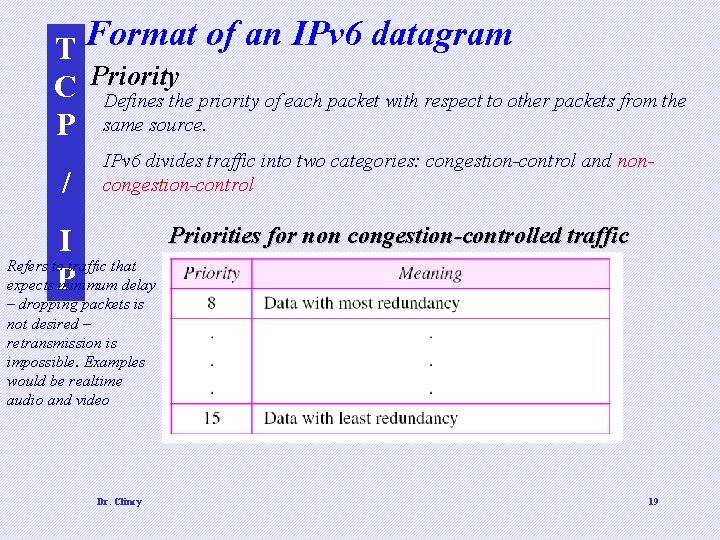
T Format of an IPv 6 datagram C Priority Defines the priority of each packet with respect to other packets from the P same source. / IPv 6 divides traffic into two categories: congestion-control and noncongestion-control I Refers to traffic that expects P minimum delay Priorities for non congestion-controlled traffic – dropping packets is not desired – retransmission is impossible. Examples would be realtime audio and video Dr. Clincy 19

IPv 6 Packet T Flow Label C • Recall how a routing-algorithm table lookup is performed for a packet using a P router. / I P • Sequence of packets sent from a Tx to Rx needing “special handling” is called a flow • Combo of the Tx address and a flow label uniquely identifies a flow of packets • The flow label is assigned to the packet by the Tx – randomly generated number • From a router perspective, a flow is a sequence of packets sharing the characteristics (using same resources, same security, , etc) • If the packet has a flow number, the router consults it flow label table for the next hop • This speeds up the process – much faster than going through the routing algorithm approach • Flow label approach is good for apps needing to reserve bandwidth and buffer space beforehand in minimizing delays (ie. realtime audio and video) Dr. Clincy 20

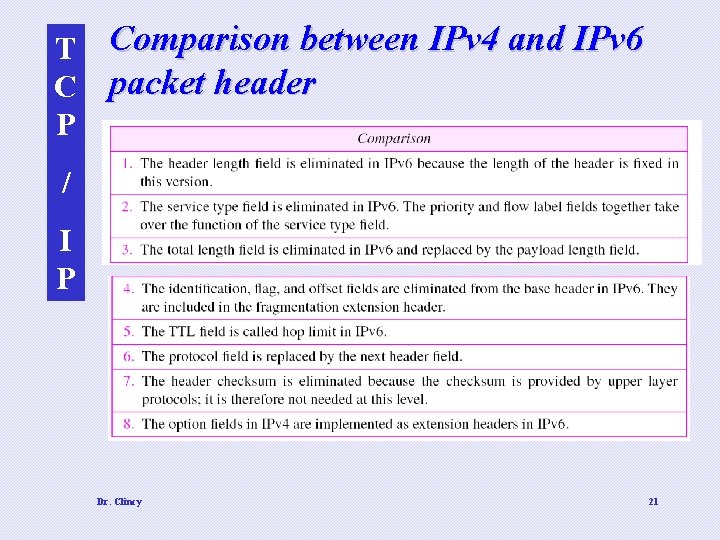
T Comparison between IPv 4 and IPv 6 C packet header P / I P Dr. Clincy 21

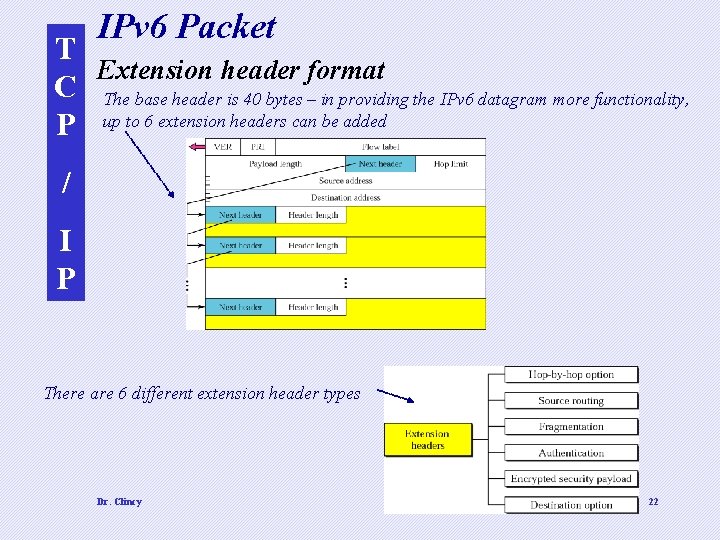
IPv 6 Packet T Extension header format C The base header is 40 bytes – in providing the IPv 6 datagram more functionality, P up to 6 extension headers can be added / I P There are 6 different extension header types Dr. Clincy 22

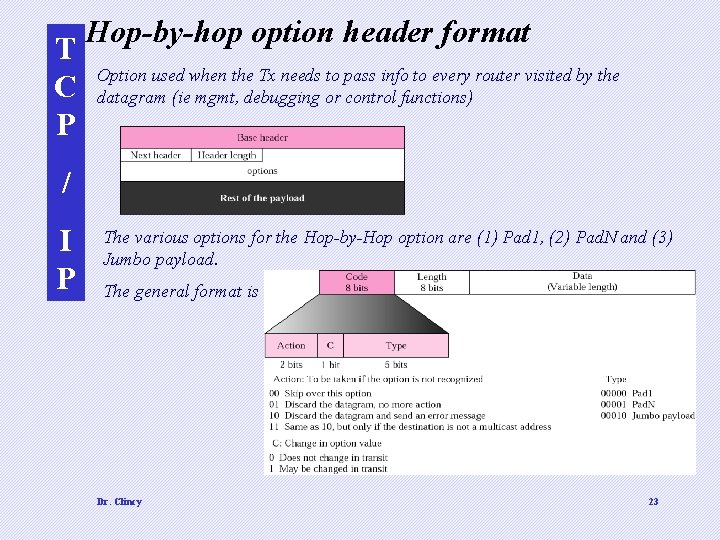
T C P Hop-by-hop option header format Option used when the Tx needs to pass info to every router visited by the datagram (ie mgmt, debugging or control functions) / I P The various options for the Hop-by-Hop option are (1) Pad 1, (2) Pad. N and (3) Jumbo payload. The general format is Dr. Clincy 23

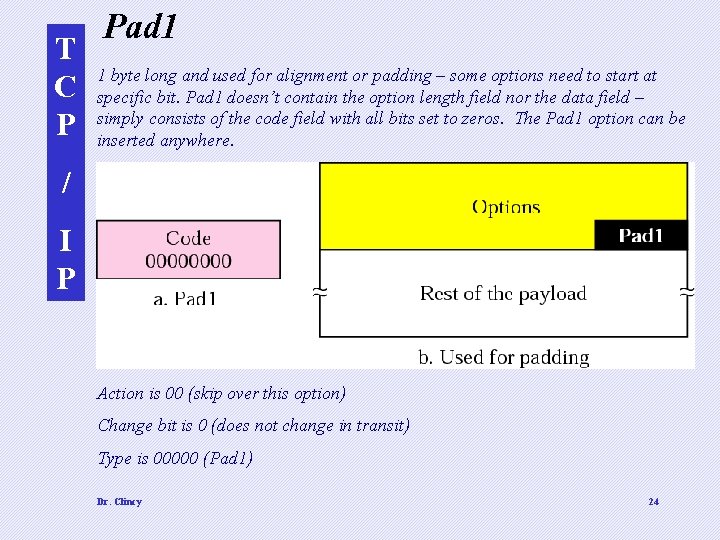
T C P Pad 1 1 byte long and used for alignment or padding – some options need to start at specific bit. Pad 1 doesn’t contain the option length field nor the data field – simply consists of the code field with all bits set to zeros. The Pad 1 option can be inserted anywhere. / I P Action is 00 (skip over this option) Change bit is 0 (does not change in transit) Type is 00000 (Pad 1) Dr. Clincy 24

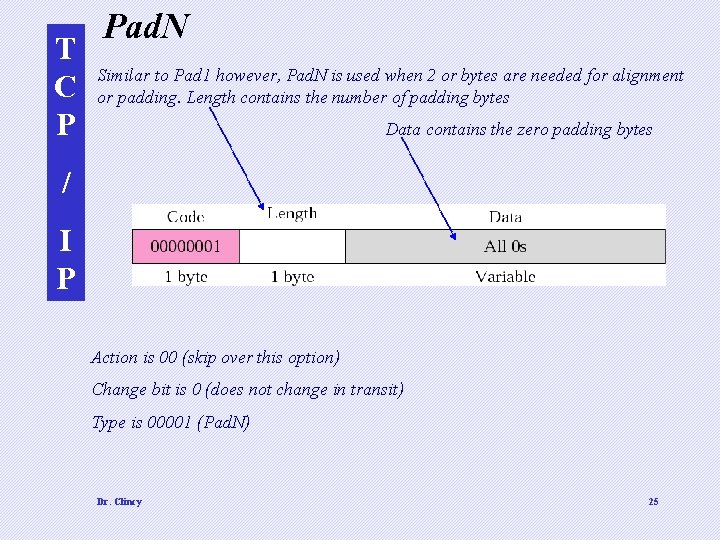
T C P Pad. N Similar to Pad 1 however, Pad. N is used when 2 or bytes are needed for alignment or padding. Length contains the number of padding bytes Data contains the zero padding bytes / I P Action is 00 (skip over this option) Change bit is 0 (does not change in transit) Type is 00001 (Pad. N) Dr. Clincy 25

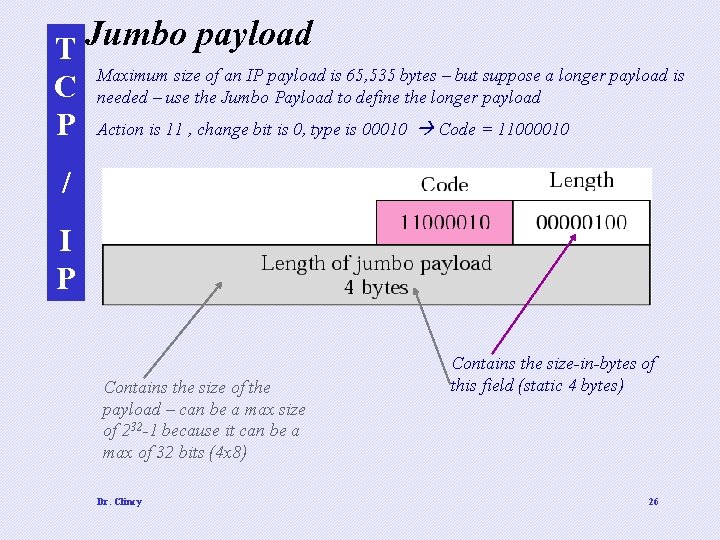
T Jumbo payload Maximum size of an IP payload is 65, 535 bytes – but suppose a longer payload is C needed – use the Jumbo Payload to define the longer payload P Action is 11 , change bit is 0, type is 00010 Code = 11000010 / I P Contains the size of the payload – can be a max size of 232 -1 because it can be a max of 32 bits (4 x 8) Dr. Clincy Contains the size-in-bytes of this field (static 4 bytes) 26

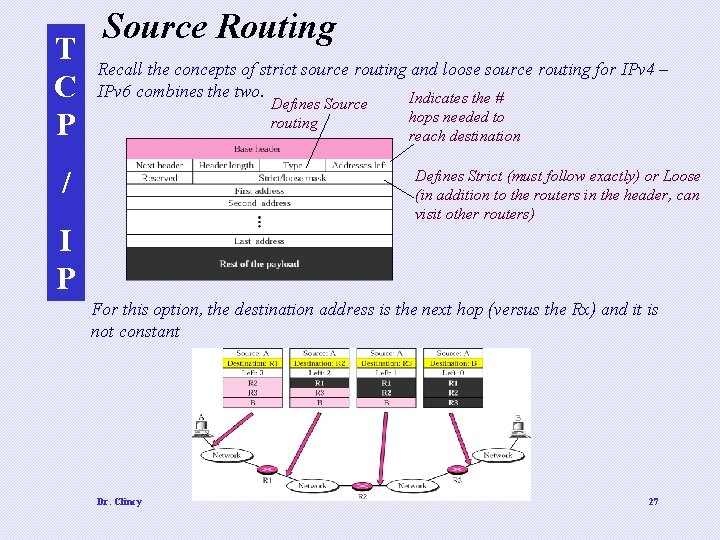
T C P Source Routing Recall the concepts of strict source routing and loose source routing for IPv 4 – IPv 6 combines the two. Indicates the # Defines Source routing / hops needed to reach destination Defines Strict (must follow exactly) or Loose (in addition to the routers in the header, can visit other routers) I P For this option, the destination address is the next hop (versus the Rx) and it is not constant Dr. Clincy 27

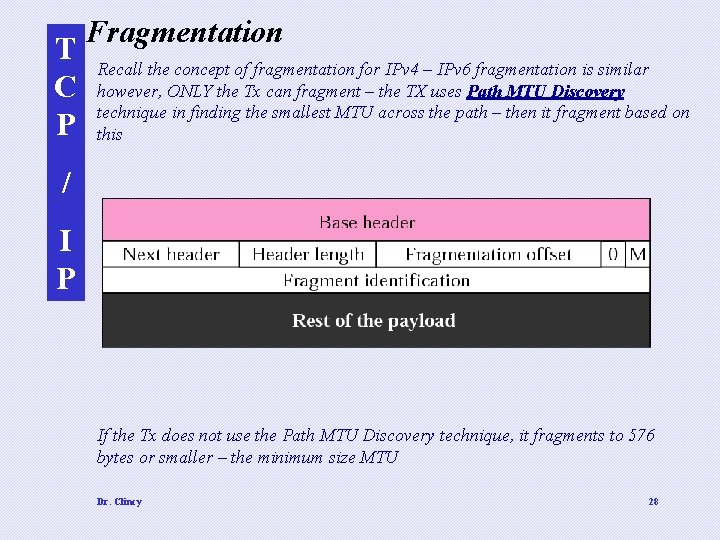
T C P Fragmentation Recall the concept of fragmentation for IPv 4 – IPv 6 fragmentation is similar however, ONLY the Tx can fragment – the TX uses Path MTU Discovery technique in finding the smallest MTU across the path – then it fragment based on this / I P If the Tx does not use the Path MTU Discovery technique, it fragments to 576 bytes or smaller – the minimum size MTU Dr. Clincy 28

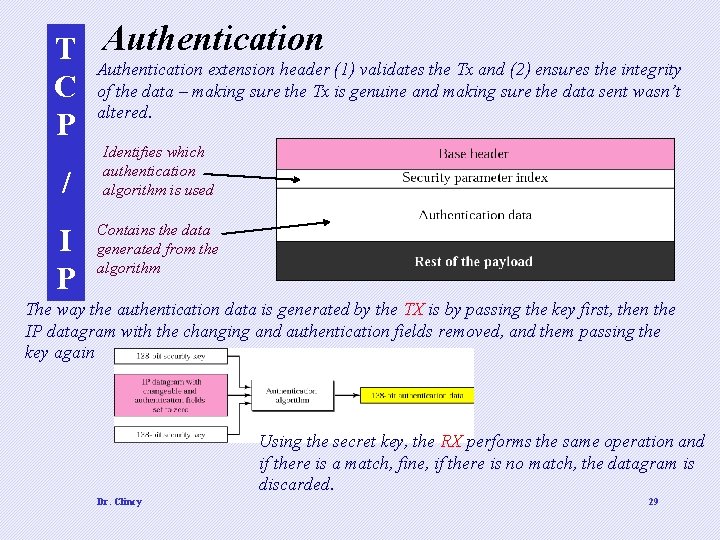
T Authentication extension header (1) validates the Tx and (2) ensures the integrity C of the data – making sure the Tx is genuine and making sure the data sent wasn’t altered. P / I P Identifies which authentication algorithm is used Contains the data generated from the algorithm The way the authentication data is generated by the TX is by passing the key first, then the IP datagram with the changing and authentication fields removed, and them passing the key again Using the secret key, the RX performs the same operation and if there is a match, fine, if there is no match, the datagram is discarded. Dr. Clincy 29

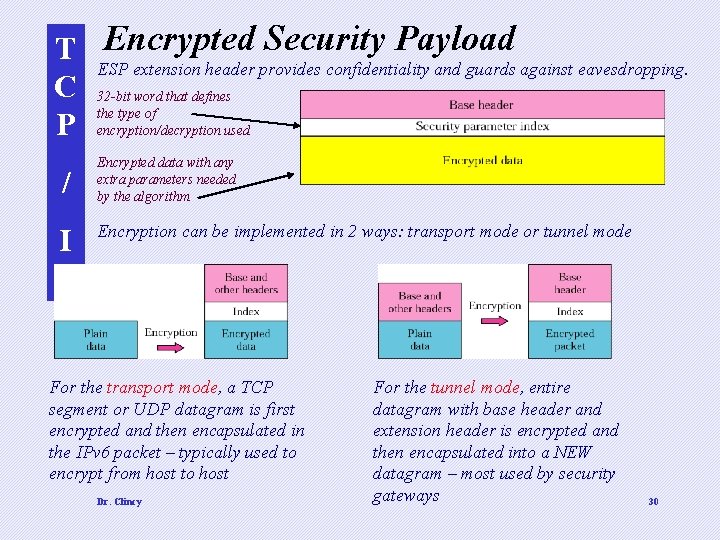
T Encrypted Security Payload ESP extension header provides confidentiality and guards against eavesdropping. C 32 -bit word that defines the type of P encryption/decryption used / I P Encrypted data with any extra parameters needed by the algorithm Encryption can be implemented in 2 ways: transport mode or tunnel mode For the transport mode, a TCP segment or UDP datagram is first encrypted and then encapsulated in the IPv 6 packet – typically used to encrypt from host to host Dr. Clincy For the tunnel mode, entire datagram with base header and extension header is encrypted and then encapsulated into a NEW datagram – most used by security gateways 30

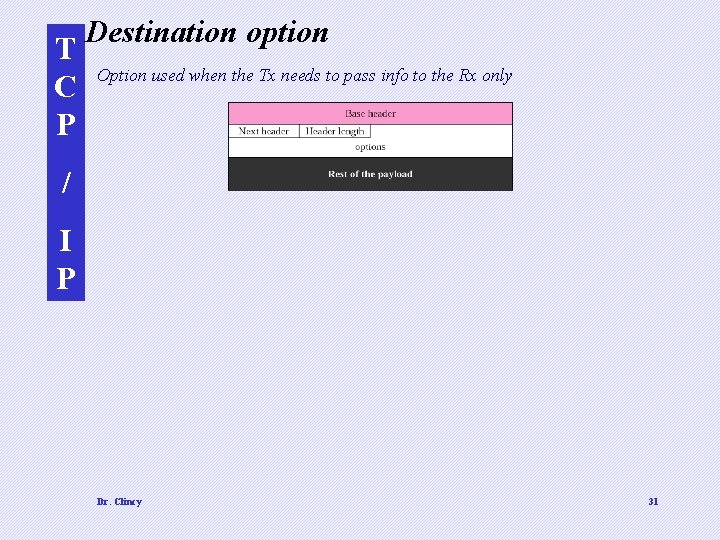
T C P Destination option Option used when the Tx needs to pass info to the Rx only / I P Dr. Clincy 31

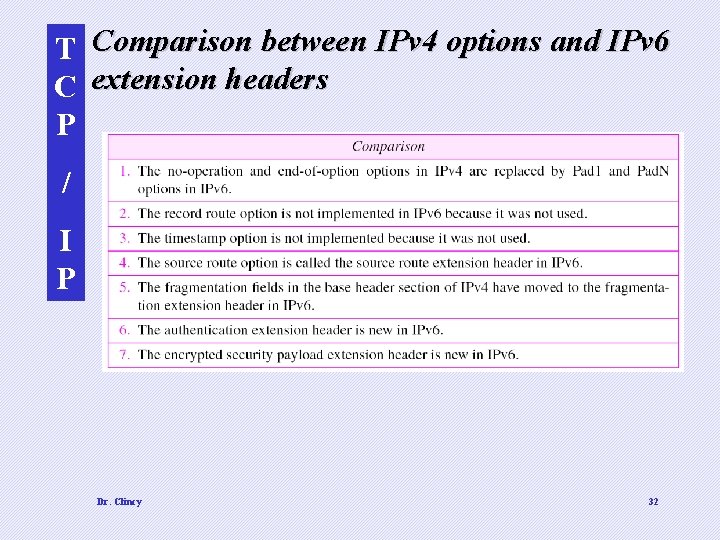
T Comparison between IPv 4 options and IPv 6 C extension headers P / I P Dr. Clincy 32