SYNCHRONISATION 2 Prof Leonardo Mostarda University of Camerino










- Slides: 25

SYNCHRONISATION 2 Prof. Leonardo Mostarda University of Camerino Prof. Leonardo Mostarda-- Camerino, 1

Last lecture z Physical Clocks z Clock Synchronization Algorithms z Logical clocks 2

Outline z MUTUAL EXCLUSION y A Centralized Algorithm y A Distributed Algorithm y A Token Ring Algorithm z Leader election y The Bully Algorithm y A Ring Algorithm 3

MUTUAL EXCLUSION z In many cases processes will need to simultaneously access the same resources. z To prevent that such concurrent accesses corrupt the resource, or make it inconsistent, solutions are needed to grant mutual exclusive access by processes. z We take a look at some of the more important distributed algorithms that have been proposed. 4

MUTUAL EXCLUSION z Distributed mutual exclusion algorithms can be classified into two different categories. z Token-based solutions y easy to implement fairness y easy to avoid deadlock y when token is lost it is difficult to create exactly one new token. z Permission-based approach y source first requires the permission of other processes 5

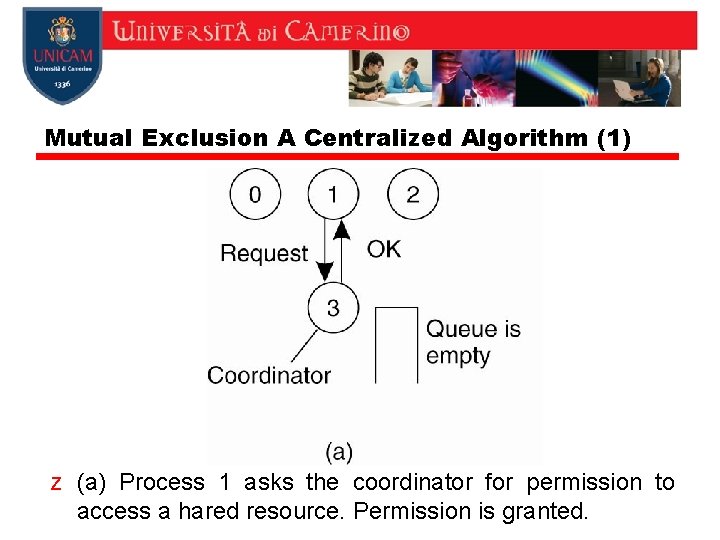
MUTUAL EXCLUSION z A Centralized Algorithm z The most straightforward way to achieve mutual exclusion in a distributed system is to simulate how it is done in a one-processor system. z One process is elected as the coordinator. z Whenever a process wants to access a shared resource, it sends a request message to the coordinator. y it is fair y it guarantees mutual exclusion 6

Mutual Exclusion A Centralized Algorithm (1) z (a) Process 1 asks the coordinator for permission to access a hared resource. Permission is granted.

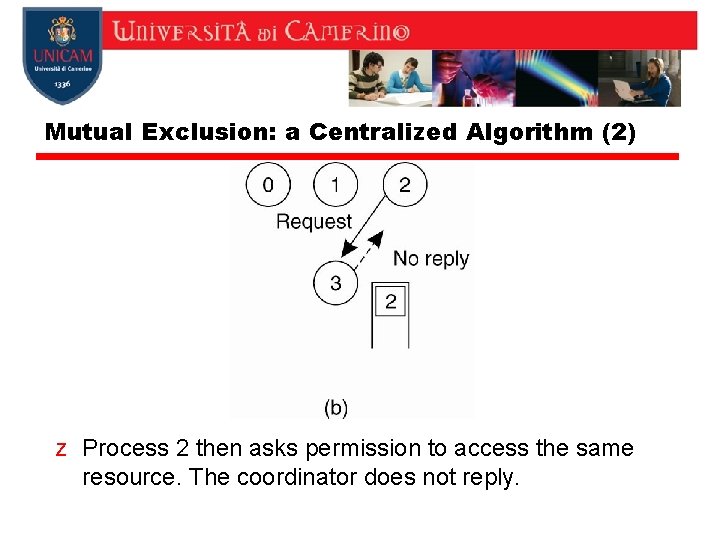
Mutual Exclusion: a Centralized Algorithm (2) z Process 2 then asks permission to access the same resource. The coordinator does not reply.

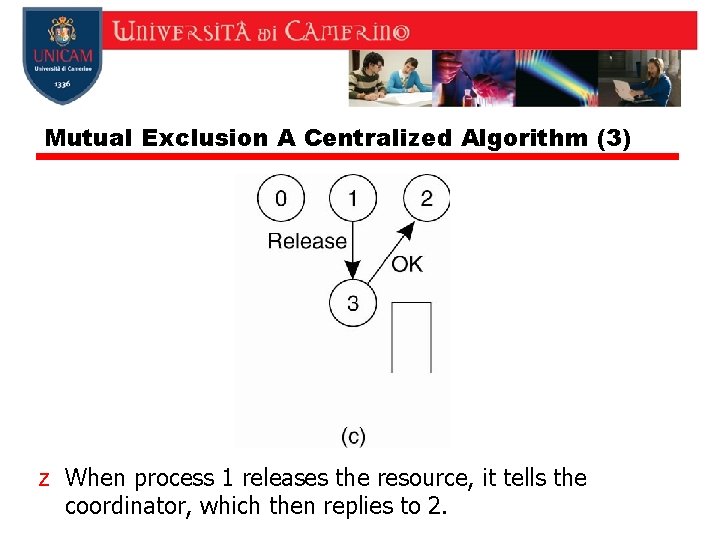
Mutual Exclusion A Centralized Algorithm (3) z When process 1 releases the resource, it tells the coordinator, which then replies to 2.

MUTUAL EXCLUSION z Problems? The coordinator is a single point of failure. Scalability 10

Ricart and Agrawala z A Distributed Algorithm y Ricart and Agrawala's algorithm requires that there be a total ordering of all events in the system. y Lamport's algorithm presented in Sec. 6. 2. 1 is one way to achieve this ordering and can be used to provide time-stamps for distributed mutual exclusion. 11

Ricart and Agrawala z When a process wants to access a shared resource, it sends a message containing the name of the resource, its process number, and the current (logical) time to all processes. z When a process receives a request message, the action it takes depends on its own state with respect to the resource named in the message. z Three different cases have to be clearly distinguished: 12

A Distributed Algorithm (1) z Three different cases: 1. If the receiver is not accessing the resource and does not want to access it, it sends back an OK message to the sender. 2. If the receiver already has access to the resource, it simply does not reply. Instead, it queues the request. 3. If the receiver wants to access the resource as well but has not yet done so, it compares the timestamp of the incoming message with the one contained in the message that it has sent everyone. The lowest one wins.

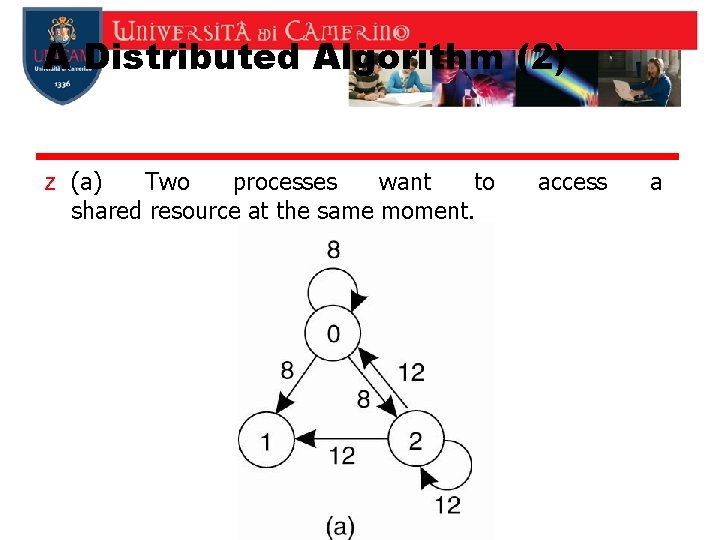
A Distributed Algorithm (2) z (a) Two processes want to shared resource at the same moment. access a

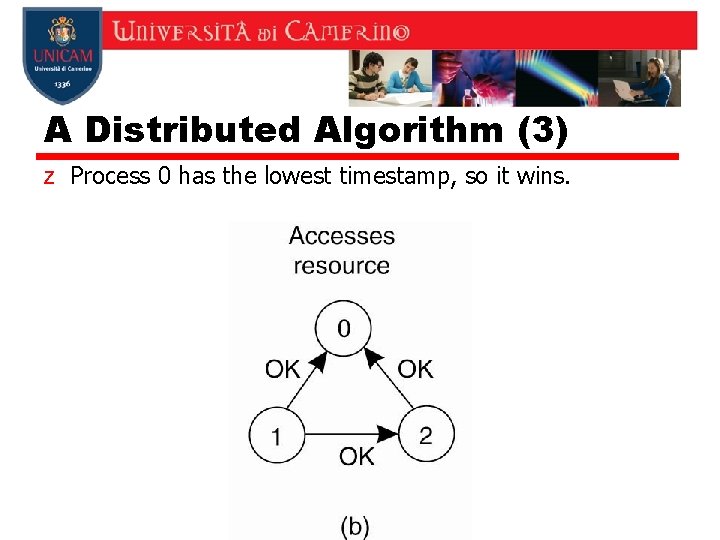
A Distributed Algorithm (3) z Process 0 has the lowest timestamp, so it wins.

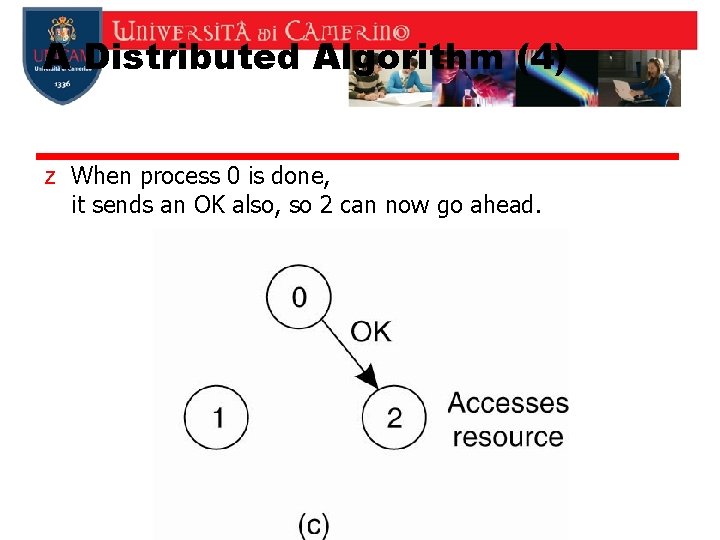
A Distributed Algorithm (4) z When process 0 is done, it sends an OK also, so 2 can now go ahead.

MUTUAL EXCLUSION z Problems? We have introduced n points of failure. If any process crashes, it will fail to respond to requests. This silence will be interpreted (incorrectly) as denial of permission, thus blocking all subsequent attempts by all processes to enter all critical regions. Solution? NACK 17

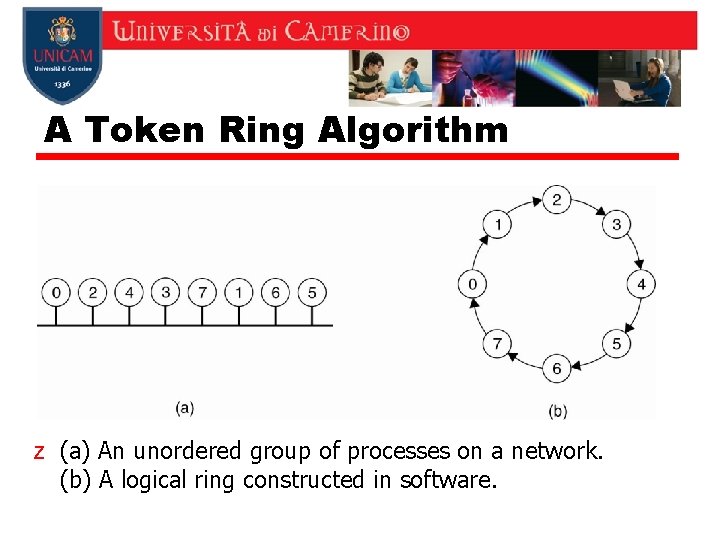
A Token Ring Algorithm z (a) An unordered group of processes on a network. (b) A logical ring constructed in software.

ELECTION ALGORITHMS z Many distributed algorithms require one process to act as coordinator; z If all processes are exactly the same, with no distinguishing characteristics, there is no way to select one of them to be special; z We will assume that each process has a unique number, for example, its network address; z Election algorithms attempt to locate the process with the highest process number and designate it as coordinator. z The algorithms differ in the way they do the location. 19

ELECTION ALGORITHMS z We assume that every process knows the process number of every other process. z What the processes do not know is which ones are currently up and which ones are currently down. z The goal of an election algorithm is to ensure that when an election starts, it concludes with all processes agreeing on who the new coordinator is to be. 20

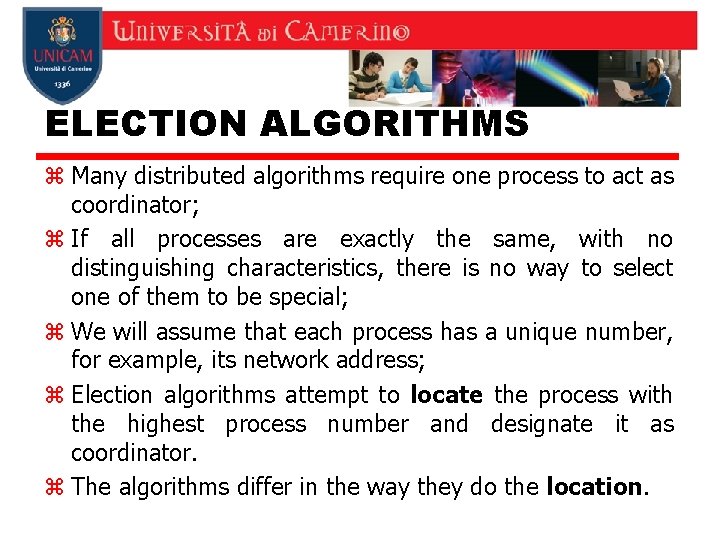
Election Algorithms z The Bully Algorithm 1. P sends an ELECTION message to all processes with higher numbers. 2. If no one responds, P wins the election and becomes coordinator. 3. If one of the higher-ups answers, it takes over. P’s job is done.

The Bully Algorithm (1) z The bully election algorithm. y (a) Process 4 holds an election. y (b) Processes 5 and 6 respond, telling 4 to stop. y (c) Now 5 and 6 each hold an election.

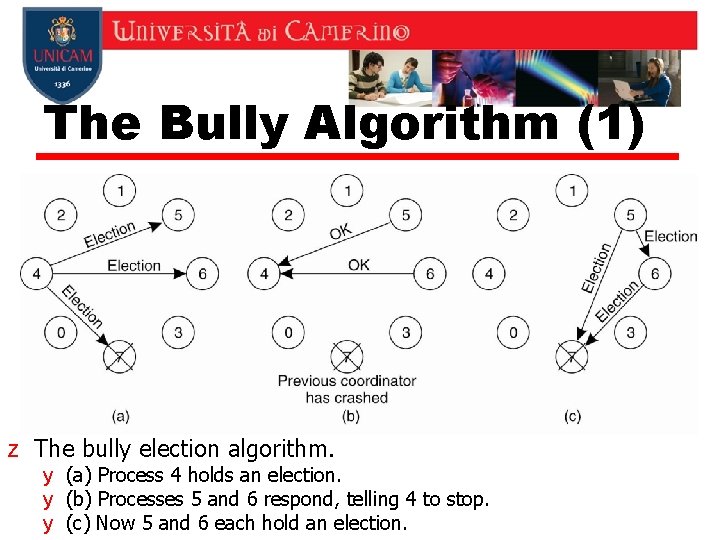
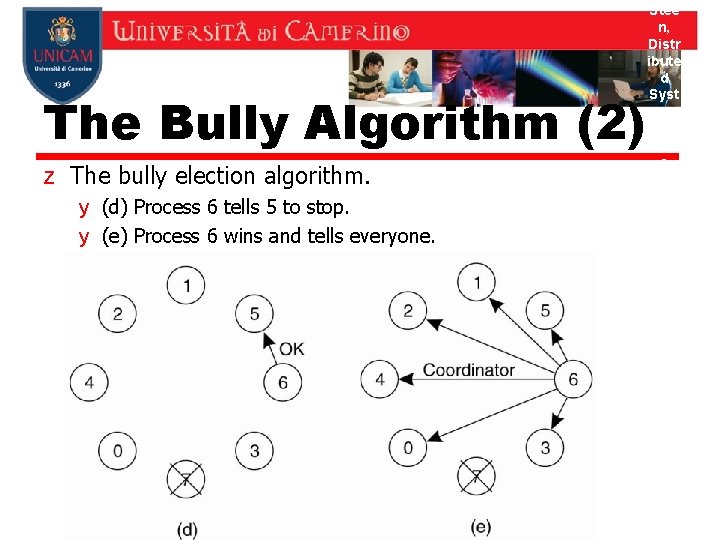
The Bully Algorithm (2) z The bully election algorithm. y (d) Process 6 tells 5 to stop. y (e) Process 6 wins and tells everyone. Stee n, Distr ibute d Syst ems: Prin ciple s and Para digm s, 2 e, (c) 2007 Pren tice. Hall, Inc. All right s rese rved. 0 -132392 27 -5

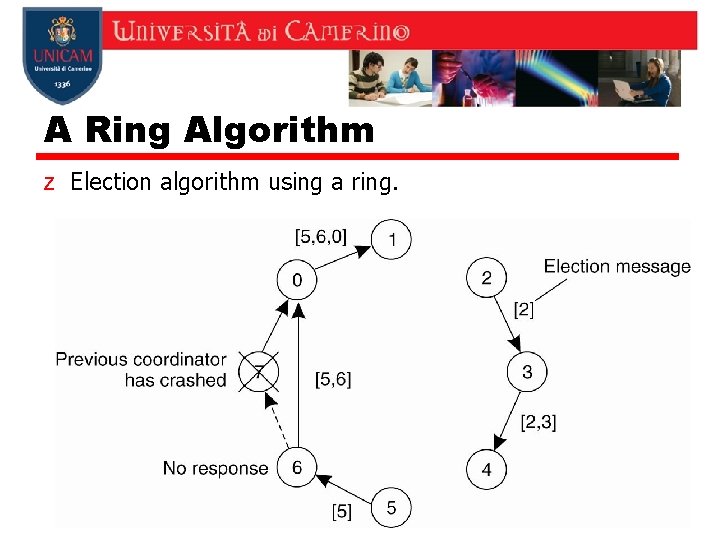
A Ring Algorithm z Election algorithm using a ring.

Summary z MUTUAL EXCLUSION y A Centralized Algorithm y A Distributed Algorithm y A Token Ring Algorithm z Leader election y The Bully Algorithm y A Ring Algorithm 25
 Leonardo mostarda
Leonardo mostarda Leonardo mostarda
Leonardo mostarda Leonardo mostarda
Leonardo mostarda Hotmail synchronisation automatique
Hotmail synchronisation automatique Classical problems of synchronization
Classical problems of synchronization Betti camerino
Betti camerino Mostarda di quinacrina
Mostarda di quinacrina Vetrino
Vetrino Leonardo fibonacci leonardo pisano (fibonacci)
Leonardo fibonacci leonardo pisano (fibonacci) 詹景裕
詹景裕 Romano cycle pump
Romano cycle pump Gabriel farcia marquez
Gabriel farcia marquez Versatile personality meaning
Versatile personality meaning Uncinectomia
Uncinectomia Turbulence leonardo da vinci
Turbulence leonardo da vinci Leonardo's robot
Leonardo's robot Tahun 1225 leonardo da pisa mencari akar persamaan
Tahun 1225 leonardo da pisa mencari akar persamaan Leonardo vinci 1452 mazara del vallo
Leonardo vinci 1452 mazara del vallo San giovanni battista leonardo
San giovanni battista leonardo Leonardo casali
Leonardo casali Programme leonardo da vinci
Programme leonardo da vinci Leonardo rigutini
Leonardo rigutini Sasha leonardo
Sasha leonardo Leonardo da vinci giuliomo ser piero
Leonardo da vinci giuliomo ser piero Italian guilds
Italian guilds Contamination lab pisa
Contamination lab pisa