SSL Trust Pitfalls Prof Ravi Sandhu THE CERTIFICATE



- Slides: 25

SSL Trust Pitfalls Prof. Ravi Sandhu

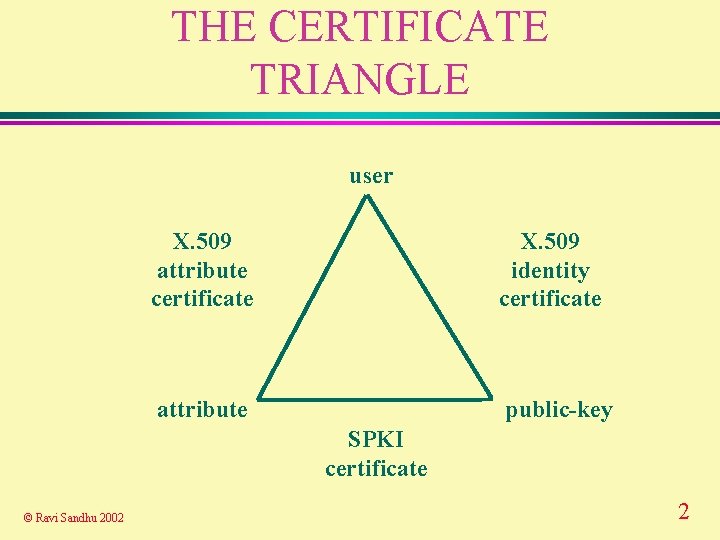
THE CERTIFICATE TRIANGLE user X. 509 attribute certificate X. 509 identity certificate attribute public-key SPKI certificate © Ravi Sandhu 2002 2

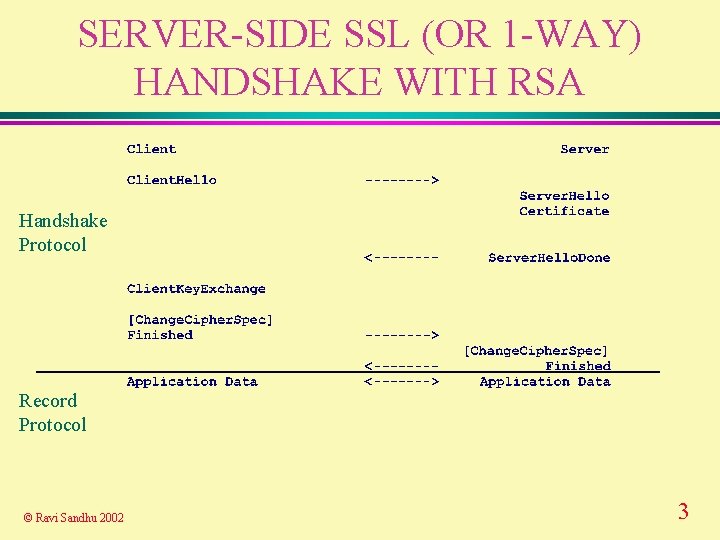
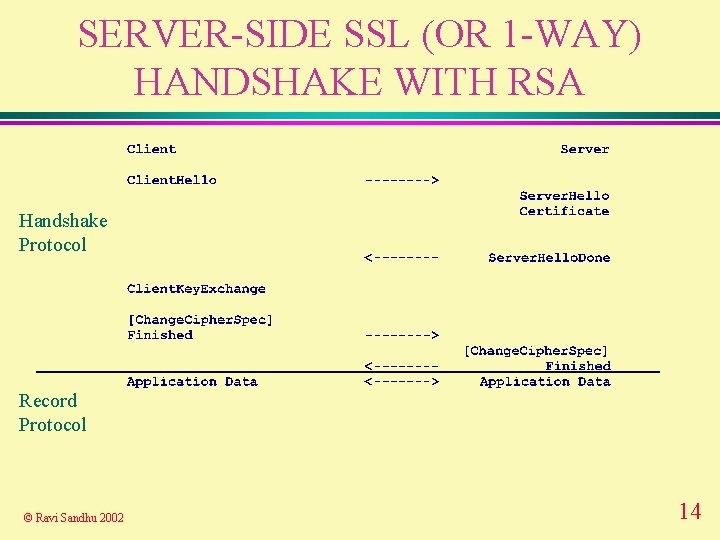
SERVER-SIDE SSL (OR 1 -WAY) HANDSHAKE WITH RSA Handshake Protocol Record Protocol © Ravi Sandhu 2002 3

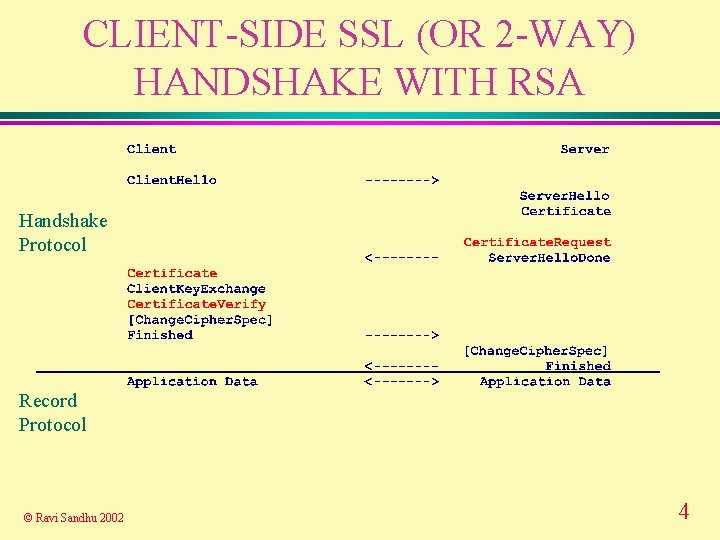
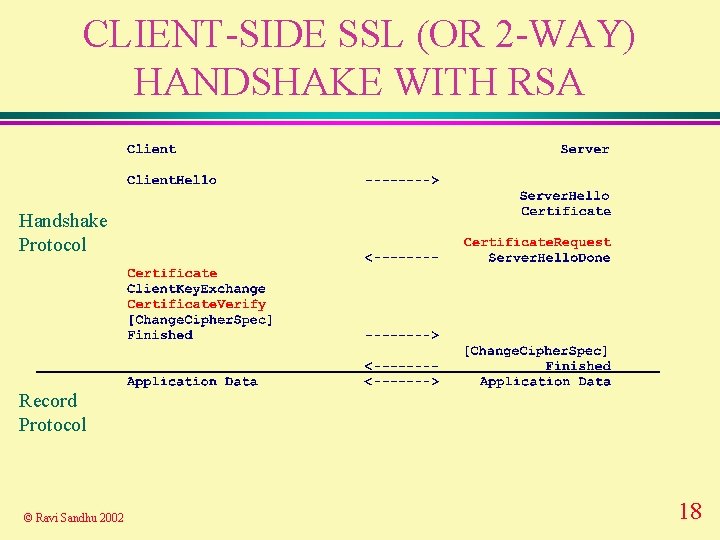
CLIENT-SIDE SSL (OR 2 -WAY) HANDSHAKE WITH RSA Handshake Protocol Record Protocol © Ravi Sandhu 2002 4

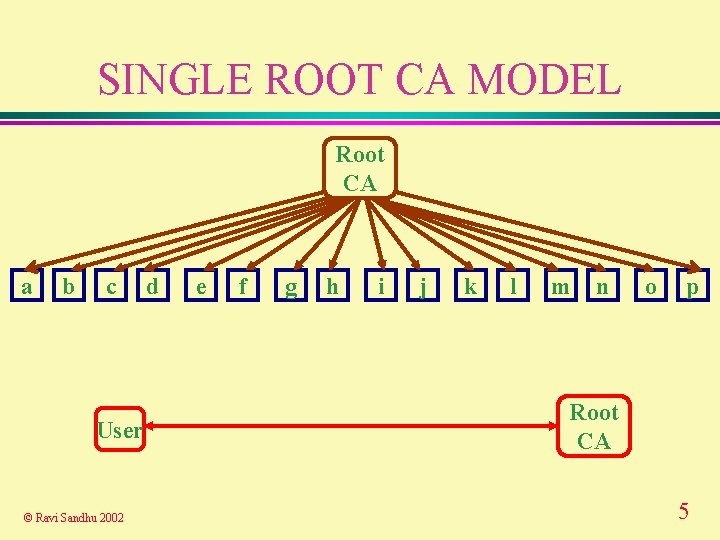
SINGLE ROOT CA MODEL Root CA a b c User © Ravi Sandhu 2002 d e f g h i j k l m n o p Root CA 5

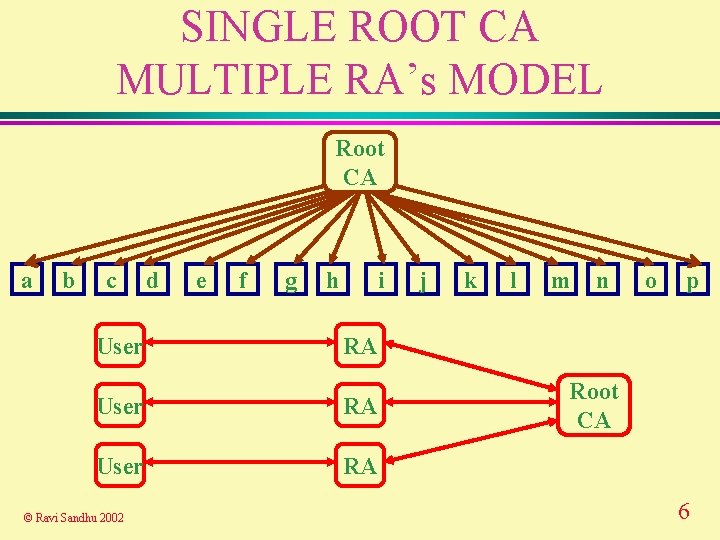
SINGLE ROOT CA MULTIPLE RA’s MODEL Root CA a b c User d e f g h i k l m n o p RA User RA © Ravi Sandhu 2002 j Root CA 6

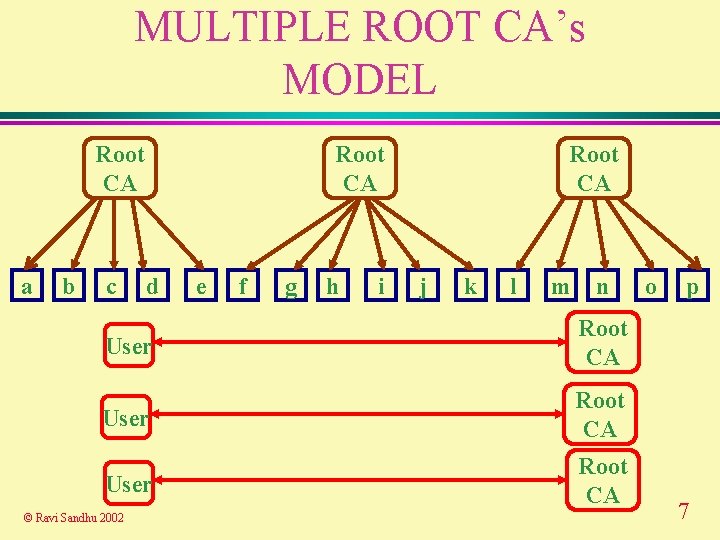
MULTIPLE ROOT CA’s MODEL Root CA a b c Root CA d e f g h i Root CA j k l m n User Root CA © Ravi Sandhu 2002 o p 7

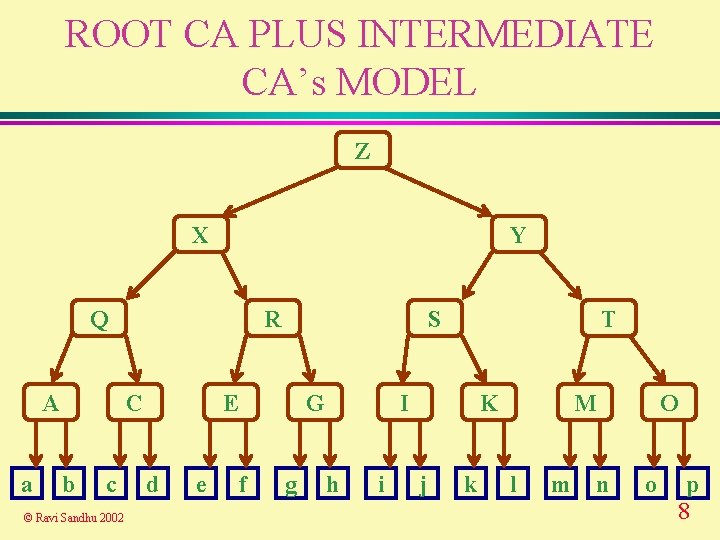
ROOT CA PLUS INTERMEDIATE CA’s MODEL Z X Y Q A a R C b c © Ravi Sandhu 2002 S E d e G f g T I h i K j k M l m O n o p 8

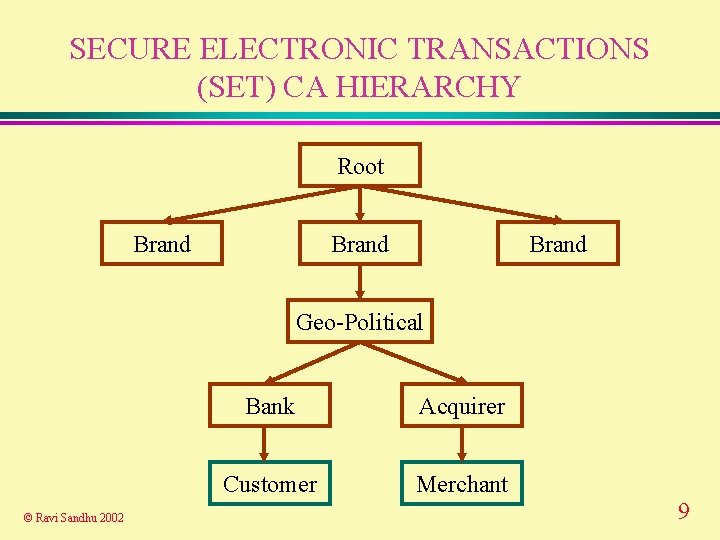
SECURE ELECTRONIC TRANSACTIONS (SET) CA HIERARCHY Root Brand Geo-Political © Ravi Sandhu 2002 Bank Acquirer Customer Merchant 9

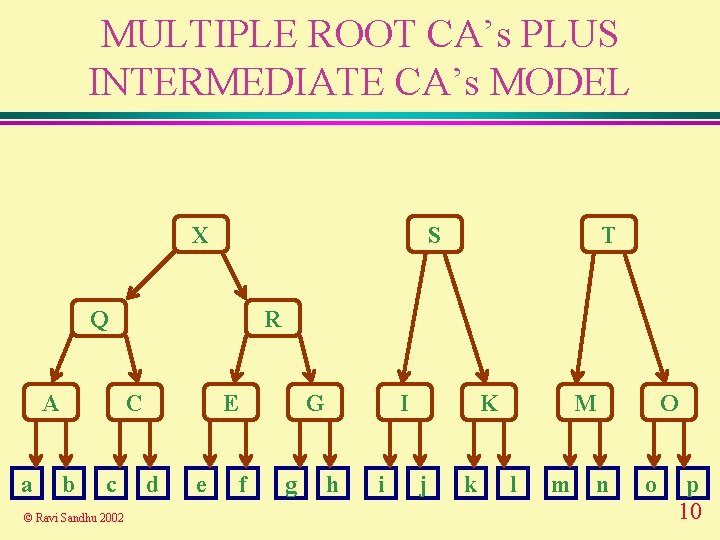
MULTIPLE ROOT CA’s PLUS INTERMEDIATE CA’s MODEL X S Q A a R C b c © Ravi Sandhu 2002 T E d e G f g I h i K j k M l m O n o p 10

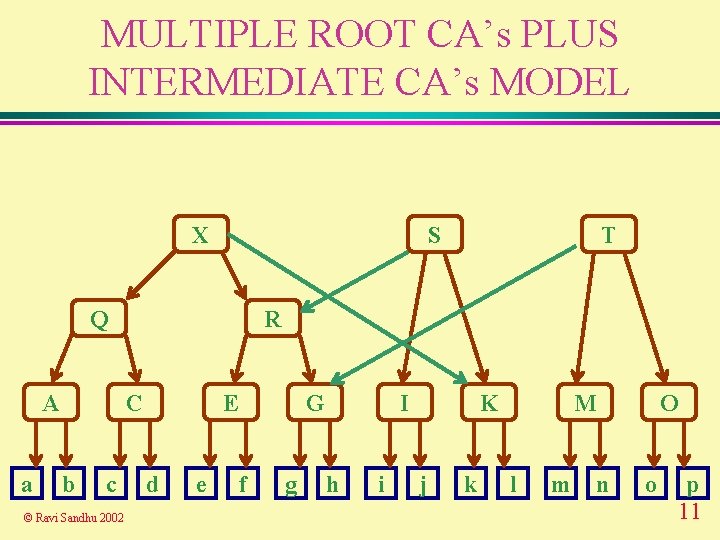
MULTIPLE ROOT CA’s PLUS INTERMEDIATE CA’s MODEL X S Q A a R C b c © Ravi Sandhu 2002 T E d e G f g I h i K j k M l m O n o p 11

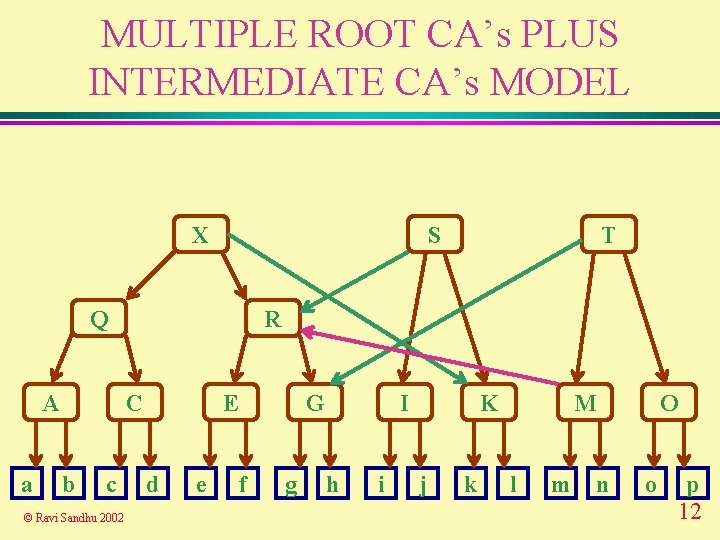
MULTIPLE ROOT CA’s PLUS INTERMEDIATE CA’s MODEL X S Q A a R C b c © Ravi Sandhu 2002 T E d e G f g I h i K j k M l m O n o p 12

MULTIPLE ROOT CA’s PLUS INTERMEDIATE CA’s MODEL v Essentially the model on the web today v Deployed in server-side SSL mode v Client-side SSL mode yet to happen © Ravi Sandhu 2002 13

SERVER-SIDE SSL (OR 1 -WAY) HANDSHAKE WITH RSA Handshake Protocol Record Protocol © Ravi Sandhu 2002 14

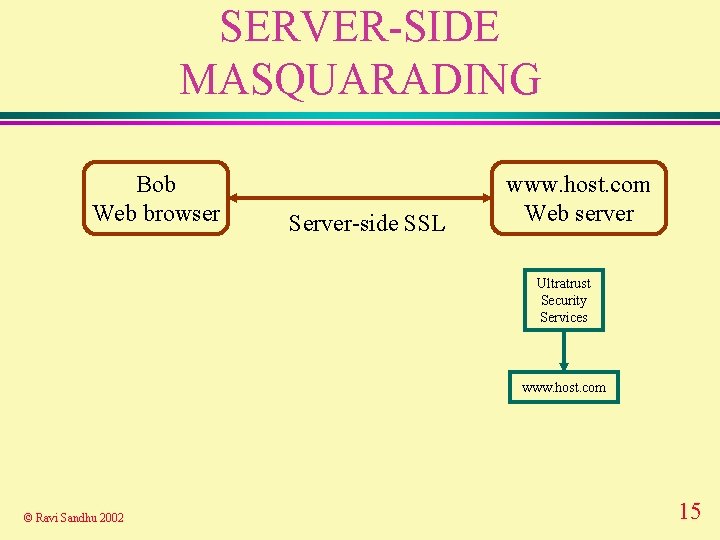
SERVER-SIDE MASQUARADING Bob Web browser Server-side SSL www. host. com Web server Ultratrust Security Services www. host. com © Ravi Sandhu 2002 15

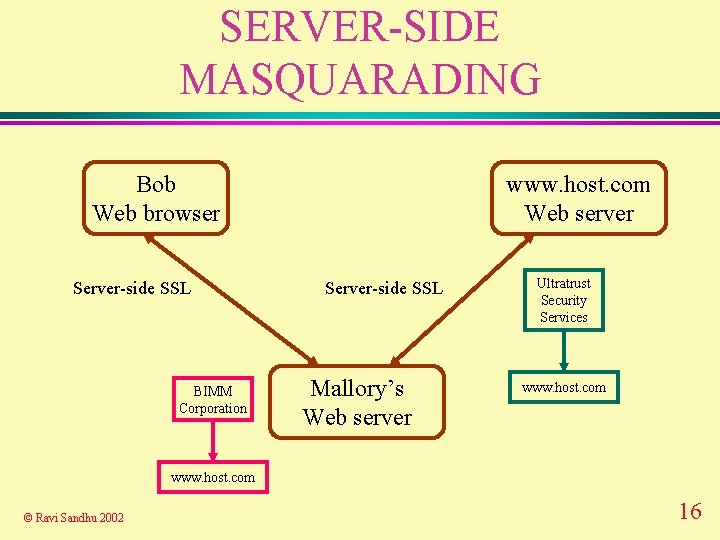
SERVER-SIDE MASQUARADING Bob Web browser Server-side SSL BIMM Corporation www. host. com Web server Server-side SSL Mallory’s Web server Ultratrust Security Services www. host. com © Ravi Sandhu 2002 16

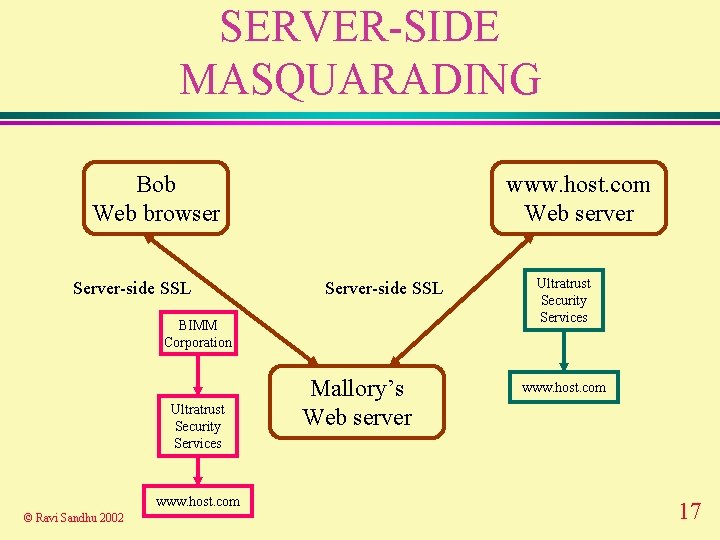
SERVER-SIDE MASQUARADING Bob Web browser Server-side SSL www. host. com Web server Server-side SSL BIMM Corporation Ultratrust Security Services www. host. com © Ravi Sandhu 2002 Mallory’s Web server Ultratrust Security Services www. host. com 17

CLIENT-SIDE SSL (OR 2 -WAY) HANDSHAKE WITH RSA Handshake Protocol Record Protocol © Ravi Sandhu 2002 18

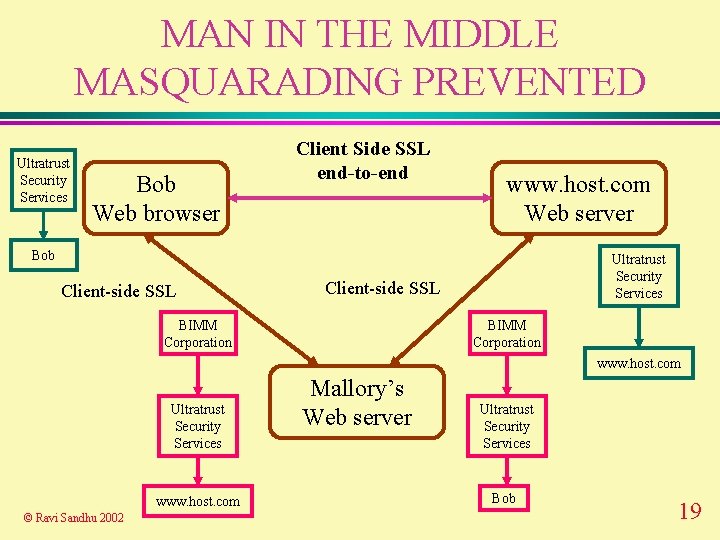
MAN IN THE MIDDLE MASQUARADING PREVENTED Ultratrust Security Services Bob Web browser Client Side SSL end-to-end www. host. com Web server Bob Client-side SSL Ultratrust Security Services Client-side SSL BIMM Corporation www. host. com Ultratrust Security Services www. host. com © Ravi Sandhu 2002 Mallory’s Web server Ultratrust Security Services Bob 19

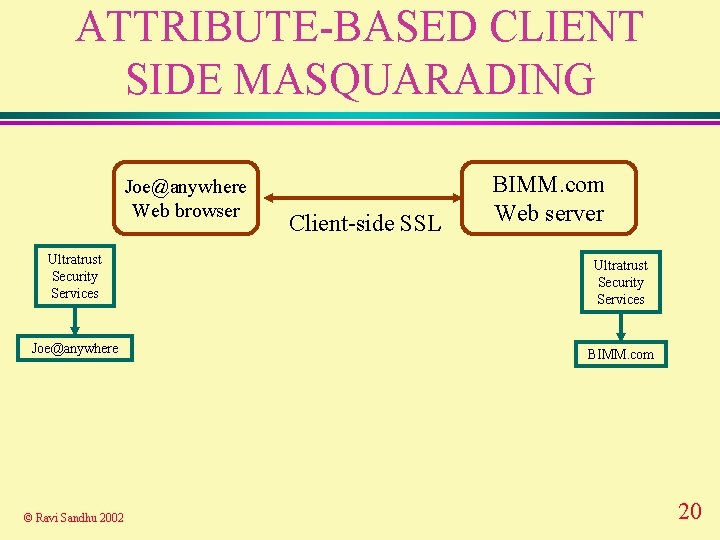
ATTRIBUTE-BASED CLIENT SIDE MASQUARADING Joe@anywhere Web browser Client-side SSL BIMM. com Web server Ultratrust Security Services Joe@anywhere BIMM. com © Ravi Sandhu 2002 20

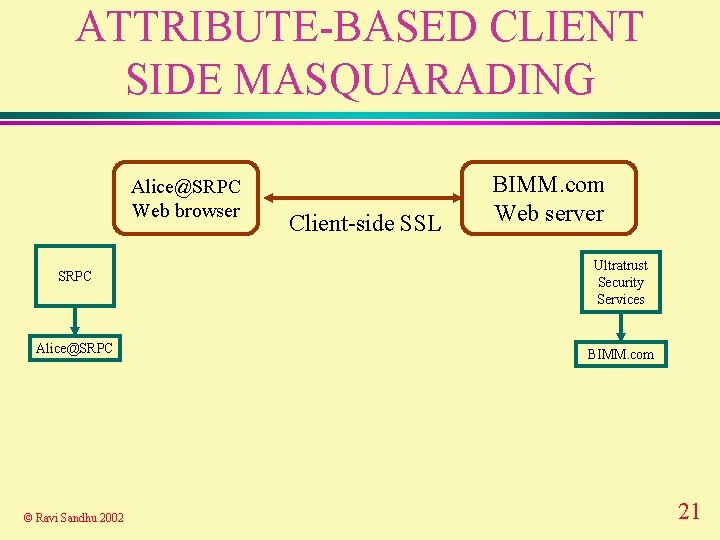
ATTRIBUTE-BASED CLIENT SIDE MASQUARADING Alice@SRPC Web browser Client-side SSL BIMM. com Web server SRPC Ultratrust Security Services Alice@SRPC BIMM. com © Ravi Sandhu 2002 21

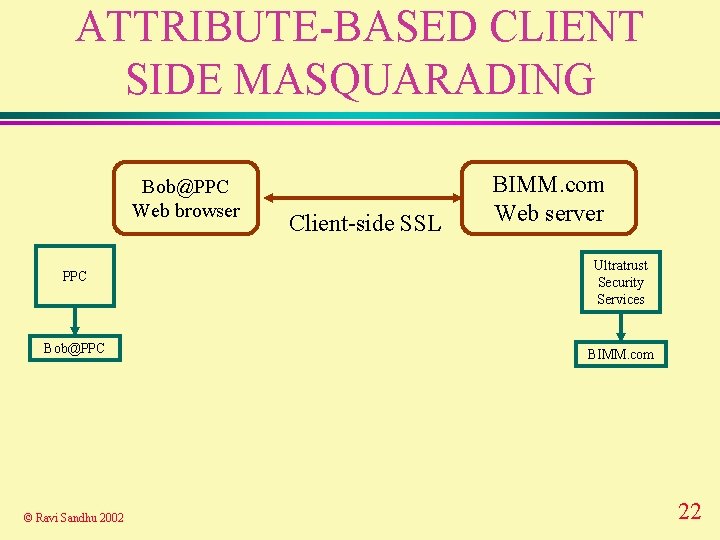
ATTRIBUTE-BASED CLIENT SIDE MASQUARADING Bob@PPC Web browser Client-side SSL BIMM. com Web server PPC Ultratrust Security Services Bob@PPC BIMM. com © Ravi Sandhu 2002 22

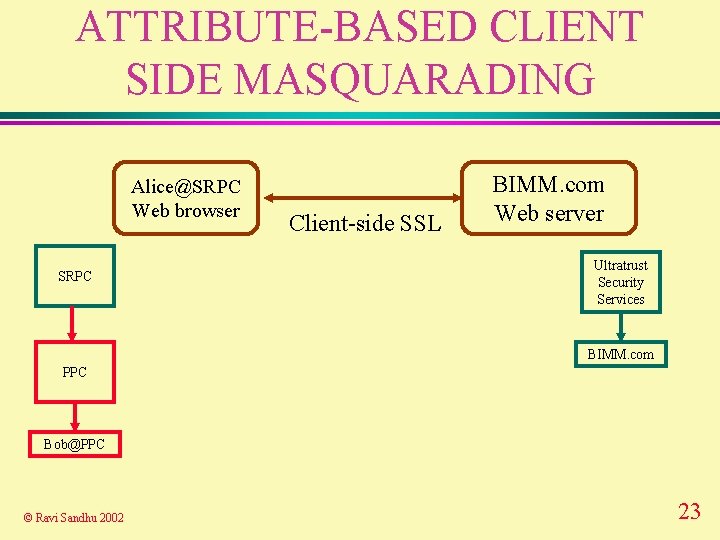
ATTRIBUTE-BASED CLIENT SIDE MASQUARADING Alice@SRPC Web browser SRPC Client-side SSL BIMM. com Web server Ultratrust Security Services BIMM. com PPC Bob@PPC © Ravi Sandhu 2002 23

PKI AND TRUST v Got to be very careful v Not a game for amateurs v Not many professionals as yet © Ravi Sandhu 2002 24

REFERENCES v v v "An overview of PKI trust models" by Perlman, R. IEEE Network, Volume: 13 Issue: 6 , Nov. -Dec. 1999 Page(s): 38 -43 "The problem with multiple roots in Web browsers-certificate masquerading" by Hayes, J. M. Proceedings Seventh IEEE International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprises, IEEE 1998. (WET ICE '98) 17 -19 June 1998 Page(s): 306 -311. "Restricting access with certificate attributes in multiple root environments - a recipe for certificate masquerading" by Hayes, J. M. Proc. 15 th Annual Computer Security Applications Conference, IEEE, 2001, Page(s): 386 -390. © Ravi Sandhu 2002 25