SSH Operation The Swiss Army Knife of encryption
















- Slides: 22

SSH Operation The Swiss Army Knife of encryption tools… Firewalls, Perimeter Protection, and VPNs - SANS © 2001 1

SSH Features • Command line terminal connection tool • Replacement for rsh, rcp, telnet, and others • All traffic encrypted • Both ends authenticate themselves to the other end • Ability to carry and encrypt non-terminal traffic Firewalls, Perimeter Protection, and VPNs - SANS © 2001 2

Brief History • SSH. com’s SSH 1, originally completely free with source code, then license changed with version 1. 2. 13 • SSH. com’s SSH 2, originally only commercial, but now free for some uses. • Open. SSH team took the last free SSH 1 release, refixed bugs, added features, and added support for the SSH 2 protocol. Firewalls, Perimeter Protection, and VPNs - SANS © 2001 3

Installation • Open. SSH is included with a number of Linux distributions, and available for a large number of Unices • On RPM-based linuxes: – “rpm –Uvh openssh*. rpm” Firewalls, Perimeter Protection, and VPNs - SANS © 2001 4

Basic use • • ssh Ssh. Server. Name ssh –l User. Name Ssh. Server. Name ssh Ssh. Server. Name Command. To. Run ssh –v Ssh. Server. Name Server Host Key checks Uses same login password And if we need to encrypt other traffic? Firewalls, Perimeter Protection, and VPNs - SANS © 2001 5

Port Forwarding – real server on remote machine • I want to listen on port 5110 on this machine; all packets arriving here get sent to mailserver, port 110: – ssh –L 5110: mailserver: 110 mailserver Firewalls, Perimeter Protection, and VPNs - SANS © 2001 6

Port Forwarding – real server on this machine • All web traffic to my firewall should be redirected to the web server running on port 8000 on my machine instead: – ssh –R 80: My. Machine: 8000 firewall Firewalls, Perimeter Protection, and VPNs - SANS © 2001 7

X Windows forwarding • No setup – already done! • Run the X Windows application in the terminal window: – xclock & – The screen display shows up on your computer, and any keystrokes and mouse movements are sent back, all encrypted. Firewalls, Perimeter Protection, and VPNs - SANS © 2001 8

Securely copying files • scp –p localfile remotemachine: /remotepath/file • Prompts for authentication if needed • All traffic encrypted • Replaces ftp, rcp, file sharing Firewalls, Perimeter Protection, and VPNs - SANS © 2001 9

SSH key background • Old way: password stored on server, user supplied password compared to stored version • New way: private key kept on client, public key stored on server. Firewalls, Perimeter Protection, and VPNs - SANS © 2001 10

SSH key creation • General command: – ssh-keygen –b 1024 –c “Comment” –f ~/. ssh/identity_file • Different forms for each of the SSH flavors • Assign a hard-to-guess passphrase to the private key during creation. • Key can be used for multiple servers Firewalls, Perimeter Protection, and VPNs - SANS © 2001 11

SSH key installation • 3 versions of ssh: interoperability is good, but poorly documented • ssh-keyinstall utility automates the creation and installation – “ssh-keyinstall –s Ssh. Server. Name” creates keys, if needed, and installs them on the remote server – Need password during key install only Firewalls, Perimeter Protection, and VPNs - SANS © 2001 12

Using SSH keys • ssh Ssh. Server. Name • Ssh –l User. Name Ssh. Server. Name • ssh Ssh. Server. Name Command. To. Run • Ssh –v Ssh. Server. Name Firewalls, Perimeter Protection, and VPNs - SANS © 2001 13

ssh-agent • Remembers your private key(s) • Other applications can ask ssh-agent to authenticate you automatically. • Unattended remote sessions. • ssh-agent bash • ssh-agent startx • eval `ssh-agent` #Less preferred • ssh-add [Key. Name] Firewalls, Perimeter Protection, and VPNs - SANS © 2001 14

Fanout • Runs command on multiple machines by opening separate ssh session to each • fanout “machine 1 machine 2 user@machine 3” “command params” • Gives organized output from each machine Firewalls, Perimeter Protection, and VPNs - SANS © 2001 15

File synchronization - Rsync • Rsync copies a tree of files from a master out to a copy on another machine. • Can use ssh as its transport. • rsync –azv –e ssh /home/wstearns/webtree/ mirror. stearns. org/home/web/ Firewalls, Perimeter Protection, and VPNs - SANS © 2001 16

Rsync-backup • Rsync-backup automates the process of backing up machines with rsync and ssh. • Features: – Only changed data shipped – All permissions preserved – All communication encrypted – Unlimited snapshots – Use <= 2 X-4 X combined client capacity Firewalls, Perimeter Protection, and VPNs - SANS © 2001 17

Rsync-backup client install • Install ssh, rsync, and rsync-backup -client rpms (see http: //www. stearns. org • Install ssh-keyinstall on client to create a backup key with – ssh-keyinstall –s backupserver –u root –c /usr/sbin/rsync-backup-server Firewalls, Perimeter Protection, and VPNs - SANS © 2001 18

Rsync-backup server install • Install ssh, freedups, rsync-static, and rsync-backup-server rpms • Turn off password authentication in /etc/sshd_config Firewalls, Perimeter Protection, and VPNs - SANS © 2001 19

Rsync-backup examples • Examples of backup commands: – rsync-backup-client / root@backupserver: / – rsync-backup-client /usr /home/gbk root@backupserver: / Firewalls, Perimeter Protection, and VPNs - SANS © 2001 20

Links and references • http: //www. ssh. com • http: //www. openssh. org • SSH, The Secure Shell, The Definitive Guide • ssh-keyinstall, fanout, rsyncbackup, freedups and other apps at http: //www. stearns. org/ Firewalls, Perimeter Protection, and VPNs - SANS © 2001 21

More links • Docs at http: //www. stearns. org/doc/ • http: //www. employees. org/~satch/ ssh/faq/ssh-faq. html • http: //rsync. samba. org • William Stearns wstearns@pobox. com Firewalls, Perimeter Protection, and VPNs - SANS © 2001 22
 Geocaching swiss army knife
Geocaching swiss army knife Swiss knife vs radio
Swiss knife vs radio Us army chaplain center and school
Us army chaplain center and school Secure remote login ssh
Secure remote login ssh Oracle zero downtime migration
Oracle zero downtime migration Rfc sftp
Rfc sftp Linux ln 명령어
Linux ln 명령어 Gobbles exploit
Gobbles exploit Ssh communications security
Ssh communications security Java ssh framework
Java ssh framework Mutable infrastructure
Mutable infrastructure Praktikmål ssa
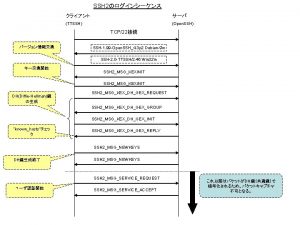
Praktikmål ssa Ssh シーケンス
Ssh シーケンス Ssh works
Ssh works Ssh protocol stack
Ssh protocol stack High performance ssh
High performance ssh Ssh ssl tls
Ssh ssl tls Contoh asb dan ssh
Contoh asb dan ssh Ssh secure shell client
Ssh secure shell client Secure remote login ssh
Secure remote login ssh 익스트림 스위치 ssh 설정
익스트림 스위치 ssh 설정 Ssh heartbleed
Ssh heartbleed Ssh secure shell wiki
Ssh secure shell wiki