Solucionar la GDPR con Microfocus Administracin de redes





- Slides: 21

Solucionar la GDPR con Microfocus

Administración de redes/ Data Protector COBOL 40 Años 30 Años

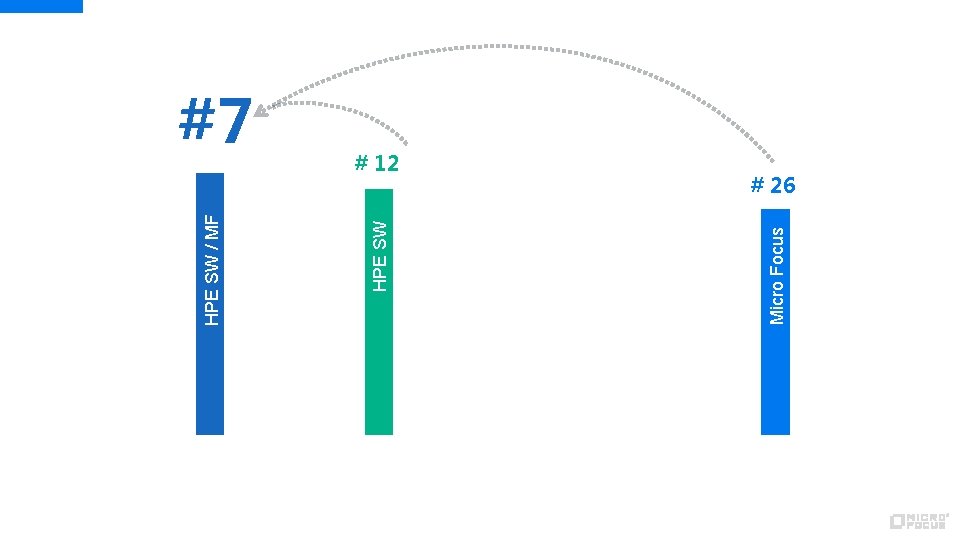
# 12 Micro Focus HPE SW / MF #7 # 26

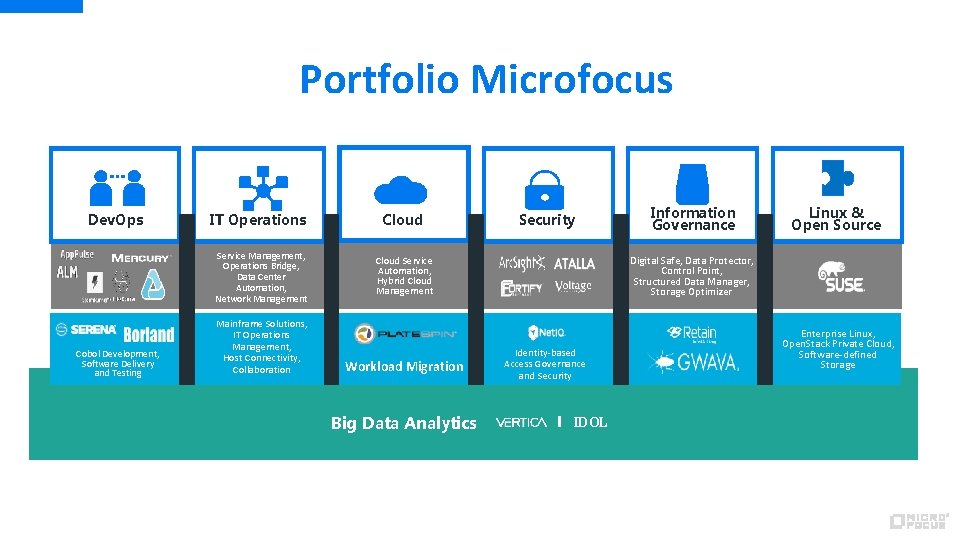
Portfolio Microfocus Dev. Ops IT Operations Service Management, Operations Bridge, Data Center Automation, Network Management Cobol Development, Software Delivery and Testing Mainframe Solutions, IT Operations Management, Host Connectivity, Collaboration Cloud Security Big Data Analytics Linux & Open Source Digital Safe, Data Protector, Control Point, Structured Data Manager, Storage Optimizer Cloud Service Automation, Hybrid Cloud Management Workload Migration Information Governance Identity-based Access Governance and Security IDOL Enterprise Linux, Open. Stack Private Cloud, Software-defined Storage

www. gdprandbeyond. com

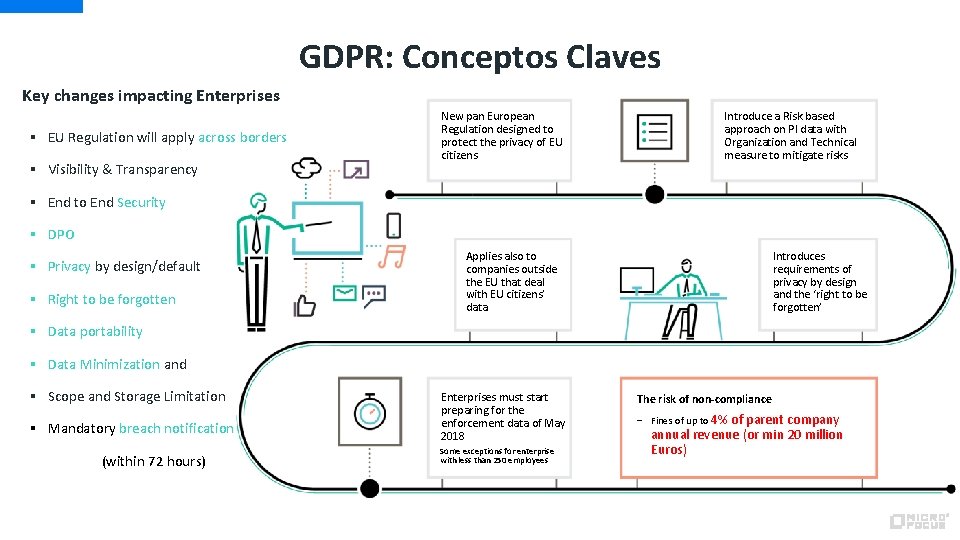
GDPR: Conceptos Claves Key changes impacting Enterprises § EU Regulation will apply across borders § Visibility & Transparency New pan European Regulation designed to protect the privacy of EU citizens Introduce a Risk based approach on PI data with Organization and Technical measure to mitigate risks § End to End Security § DPO § Privacy by design/default § Right to be forgotten Applies also to companies outside the EU that deal with EU citizens’ data Introduces requirements of privacy by design and the ‘right to be forgotten’ § Data portability § Data Minimization and § Scope and Storage Limitation § Mandatory breach notification (within 72 hours) Enterprises must start preparing for the enforcement data of May 2018 Some exceptions for enterprise with less than 250 employees The risk of non-compliance − Fines of up to 4% of parent company annual revenue (or min 20 million Euros)

• ¿Qué datos quedan bajo el alcance de la GDPR? ¿Dónde se encuentran? • ¿De qué manera aplico las políticas en el ciclo de vida de la información? GDPR - Gestion del Dato • ¿De qué manera pueda responder de manera eficiente y rápida a cualquier cuestión legal relacionada con la información que manejo, como por ejemplo el “derecho al olvido”? • ¿Cómo aseguro que los datos sensibles estén protegidos y almacenados y archivados de manera segura? 7

• Cómo sé que he tenido una fuga de información? ¿En cuánto tiempo la puedo detectar? (breach notification) GDPR - Seguridad • ¿Cómo neutralizo el impacto de una fuga de datos, incluyendo la obligación de su notificación? Artículo 34: Si los datos estan cifrados, la notificación no es necesaria 8

tiv era e nc lia mp Op Co cia n cie Efi GDPR a Imagen Corporativa

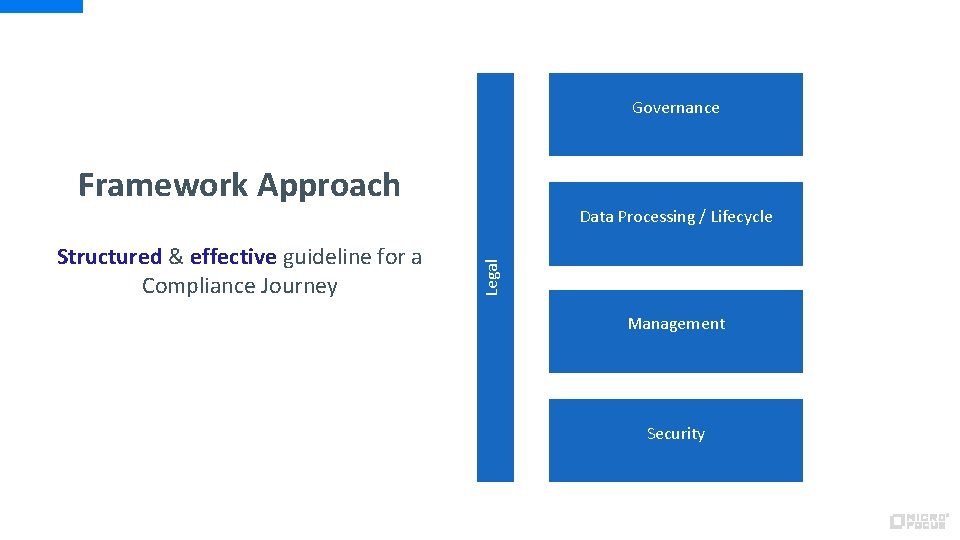
Governance Framework Approach Legal Structured & effective guideline for a Compliance Journey Data Processing / Lifecycle Management Security

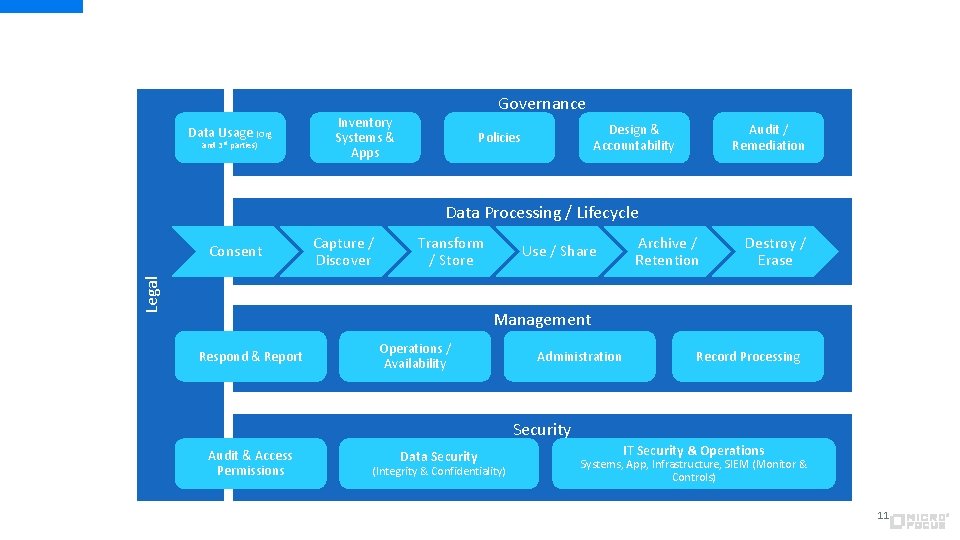
Data Usage (Org and 3 rd parties) Governance Inventory Systems & Apps Design & Accountability Policies Audit / Remediation Data Processing / Lifecycle Capture / Discover Transform / Store Legal Consent Use / Share Archive / Retention Destroy / Erase Management Respond & Report Operations / Availability Administration Record Processing Security Audit & Access Permissions Data Security (Integrity & Confidentiality) IT Security & Operations Systems, App, Infrastructure, SIEM (Monitor & Controls) 11

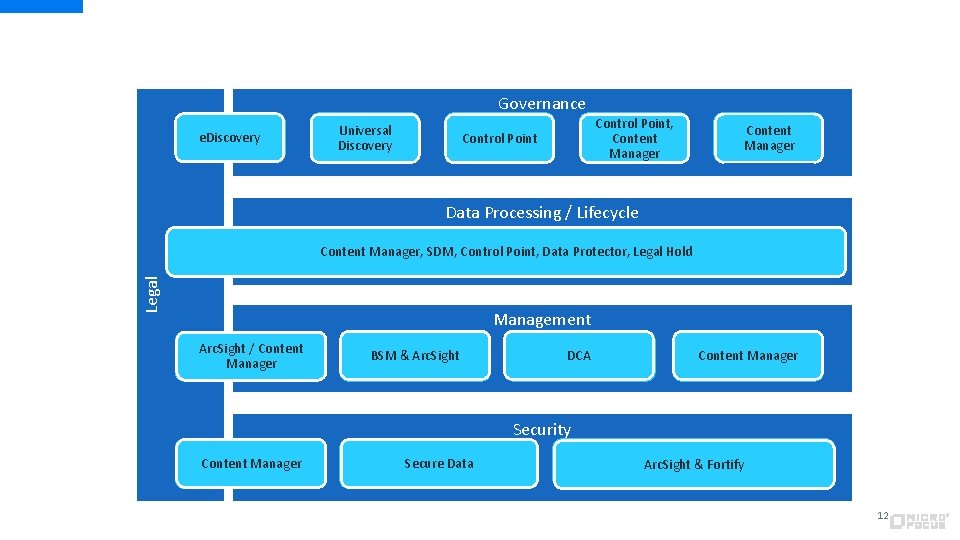
Data Usage (Org e. Discovery and 3 rd parties) Governance Inventory Universal& Systems Discovery Apps Control Design. Point, & Content Accountability Manager Policies Control Point Audit / Content Remediation Manager Data Processing / Lifecycle Capture / Transform Archive / Content Manager, SDM, Control Point, Protector, Legal Hold Use. Data / Share Discover / Store Retention Legal Consent Destroy / Erase Management Arc. Sight / Content Respond & Report Manager Operations / BSM & Arc. Sight Availability DCA Administration Content. Processing Manager Record Security Audit & Access Content Manager Permissions Data Security Secure Data (Integrity & Confidentiality) IT Security & Operations Systems, App, Arc. Sight Infrastructure, SIEM (Monitor & & Fortify Controls) 12

A recent Pw. C white paper on GDPR… Five critical technology capabilities Eight GDPR compliance scenarios 1 2 3 4 5 6 7 8

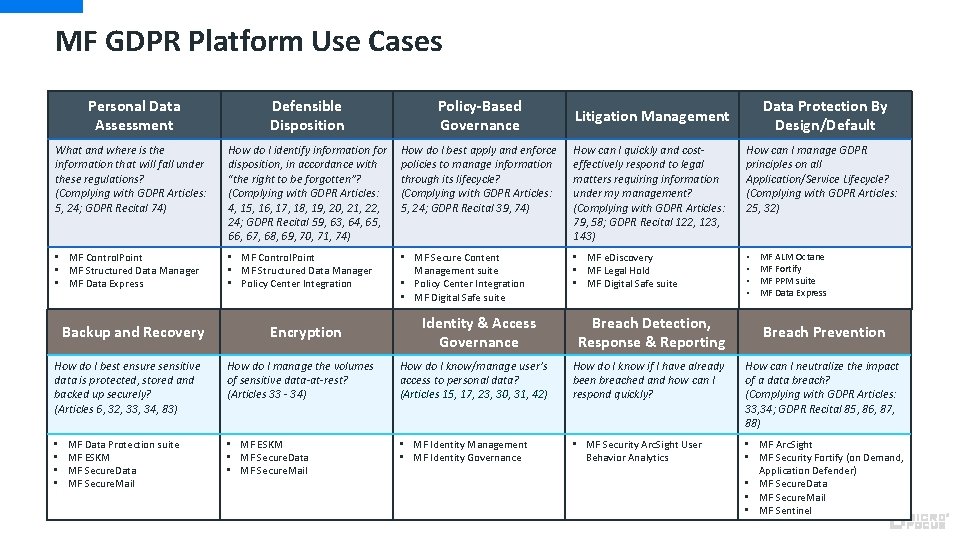
MF GDPR Platform Use Cases Personal Data Assessment Defensible Disposition Policy-Based Governance What and where is the information that will fall under these regulations? (Complying with GDPR Articles: 5, 24; GDPR Recital 74) How do I identify information for disposition, in accordance with “the right to be forgotten”? (Complying with GDPR Articles: 4, 15, 16, 17, 18, 19, 20, 21, 22, 24; GDPR Recital 59, 63, 64, 65, 66, 67, 68, 69, 70, 71, 74) How do I best apply and enforce policies to manage information through its lifecycle? (Complying with GDPR Articles: 5, 24; GDPR Recital 39, 74) How can I quickly and costeffectively respond to legal matters requiring information under my management? (Complying with GDPR Articles: 79, 58; GDPR Recital 122, 123, 143) How can I manage GDPR principles on all Application/Service Lifecycle? (Complying with GDPR Articles: 25, 32) • MF Control. Point • MF Structured Data Manager • MF Data Express • MF Control. Point • MF Structured Data Manager • Policy Center Integration • MF Secure Content Management suite • Policy Center Integration • MF Digital Safe suite • MF e. Discovery • MF Legal Hold • MF Digital Safe suite • • Backup and Recovery How do I best ensure sensitive data is protected, stored and backed up securely? (Articles 6, 32, 33, 34, 83) • • MF Data Protection suite MF ESKM MF Secure. Data MF Secure. Mail Encryption Identity & Access Governance Data Protection By Design/Default Litigation Management Breach Detection, Response & Reporting MF ALM Octane MF Fortify MF PPM suite MF Data Express Breach Prevention How do I manage the volumes of sensitive data-at-rest? (Articles 33 - 34) How do I know/manage user’s access to personal data? (Articles 15, 17, 23, 30, 31, 42) How do I know if I have already been breached and how can I respond quickly? How can I neutralize the impact of a data breach? (Complying with GDPR Articles: 33, 34; GDPR Recital 85, 86, 87, 88) • MF ESKM • MF Secure. Data • MF Secure. Mail • MF Identity Management • MF Identity Governance • MF Security Arc. Sight User Behavior Analytics • MF Arc. Sight • MF Security Fortify (on Demand, Application Defender) • MF Secure. Data • MF Secure. Mail • MF Sentinel

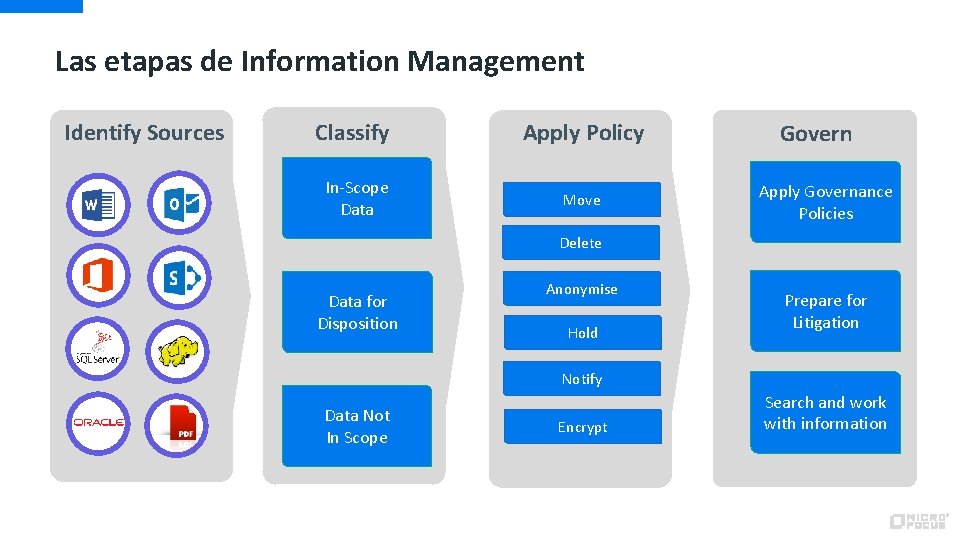
Las etapas de Information Management Identify Sources Classify Apply Policy In-Scope Data Move Govern Apply Governance Policies Delete Data for Disposition Anonymise Hold Prepare for Litigation Notify Data Not In Scope Encrypt Search and work with information

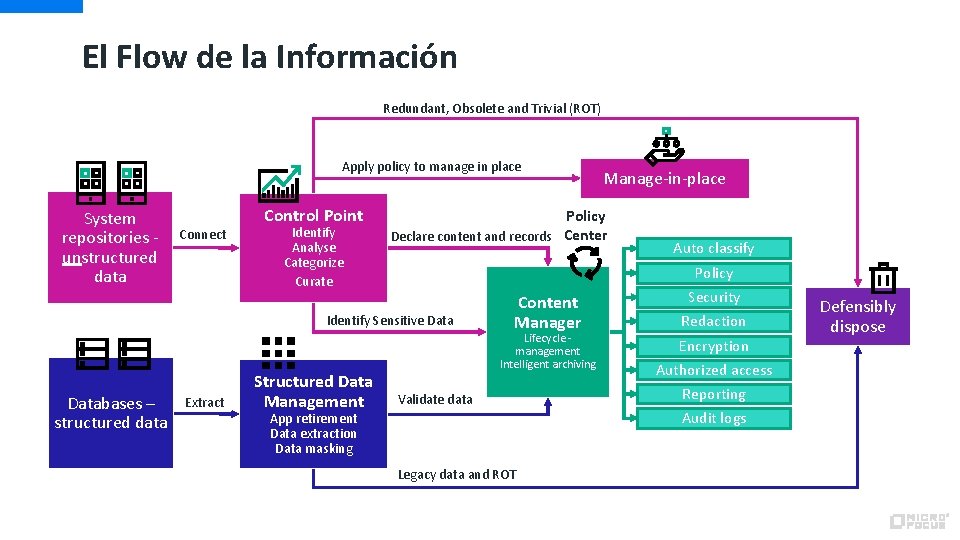
El Flow de la Información Redundant, Obsolete and Trivial (ROT) Apply policy to manage in place System repositories unstructured data Connect Control Point Identify Analyse Categorize Curate Policy Declare content and records Center Databases – structured data Extract Auto classify Policy Identify Sensitive Data Structured Data Management Manage-in-place Content Manager Lifecycle management Intelligent archiving Validate data App retirement Data extraction Data masking Legacy data and ROT Security Redaction Encryption Authorized access Reporting Audit logs Defensibly dispose

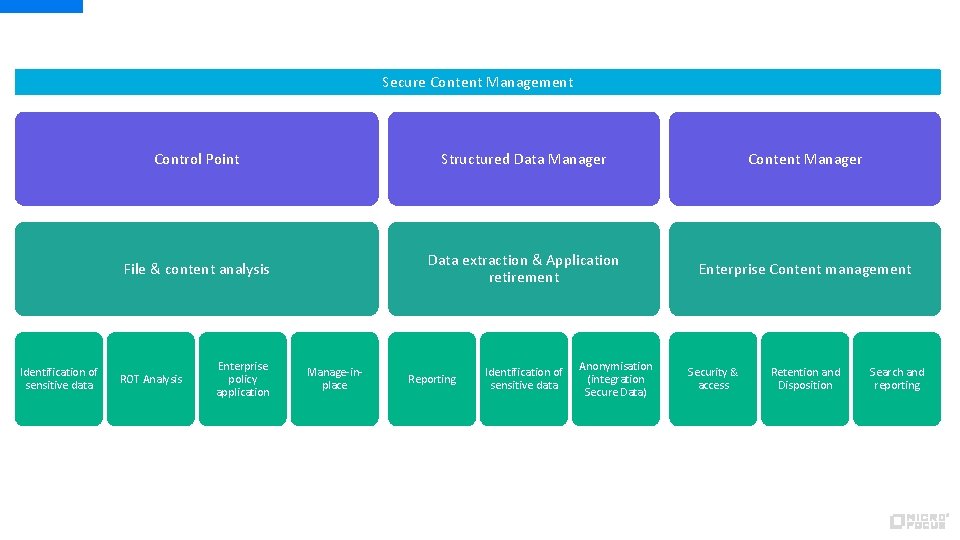
Secure Content Management Identification of sensitive data Control Point Structured Data Manager Content Manager File & content analysis Data extraction & Application retirement Enterprise Content management ROT Analysis Enterprise policy application Manage-inplace Reporting Identification of sensitive data Anonymisation (integration Secure Data) Security & access Retention and Disposition Search and reporting

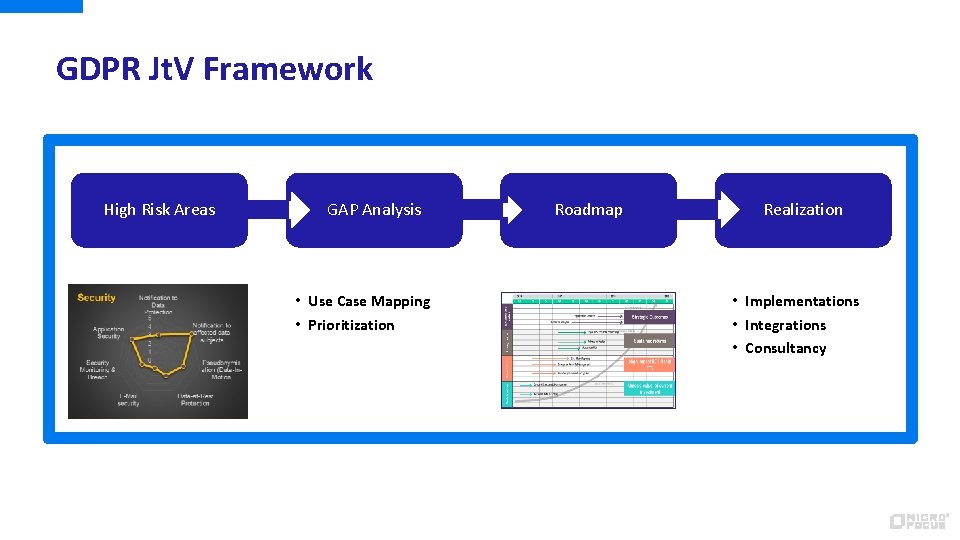
GDPR Jt. V Framework High Risk Areas GAP Analysis • Use Case Mapping • Prioritization Roadmap Realization • Implementations • Integrations • Consultancy

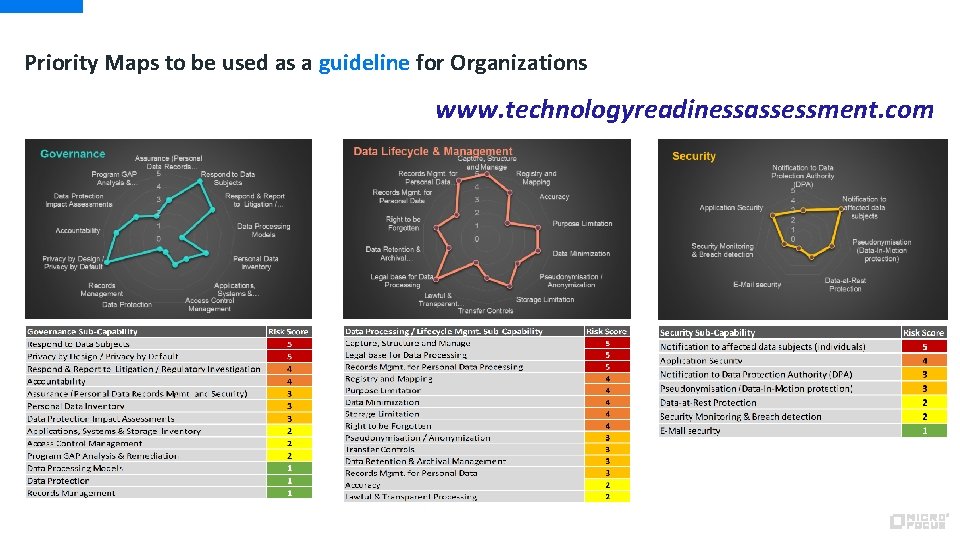
Priority Maps to be used as a guideline for Organizations www. technologyreadinessassessment. com

GDPR Technical Roadmap Design BUSINESS CHALLENGE… Being able to respond effectively to GDPR requires multiple changes to how data is managed without impacting on the business. • Where are the gaps in my current capabilities - people, skills and technologies? • Do I have effective control of my data throughout its lifecycle through to defensible disposal? • How can I implement change with minimum disruption to the business? MICRO FOCUS CAN HELP… • Identify gaps within your GDPR effectiveness and create a technology roadmap for change • Identify opportunities for increased business value and lower costs through information restructuring • Validate compliance options through targeted proof of concept/tooling • Provide the program, projects, priority and schedule to manage your information for compliance

www. microfocus. com