Security Outline Encryption Algorithms Authentication Protocols Message Integrity



- Slides: 15

Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls 4/598 N: Computer Networks

Risk analysis • Important to understand threat and perform risk analysis – No system is “secure”, systems usually trade security for performance, ease of use etc. – If information is worth x and it costs y to break into system and if (x < y), then not worth encryption – Wasteful to build a system that is more secure than is necessary • Network data is transient (unlike stored data) 4/598 N: Computer Networks

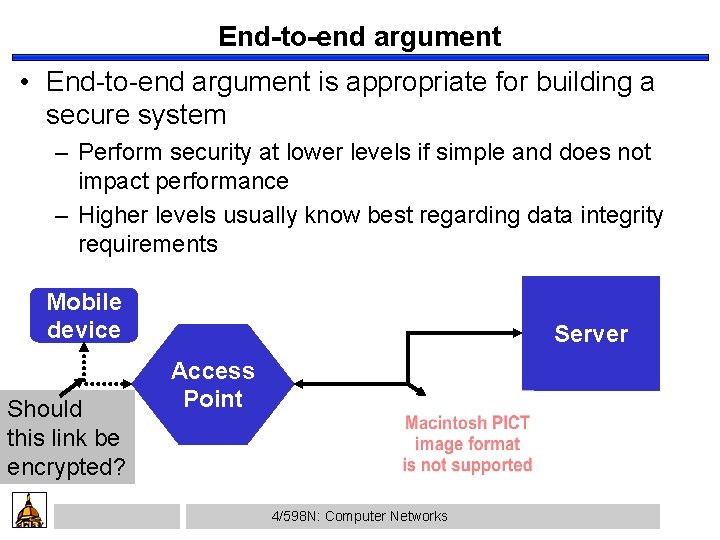
End-to-end argument • End-to-end argument is appropriate for building a secure system – Perform security at lower levels if simple and does not impact performance – Higher levels usually know best regarding data integrity requirements Mobile device Should this link be encrypted? Server Access Point 4/598 N: Computer Networks

Security Attacks • Social engineering attacks – Preys on people gullibility (good nature), hardest to defend • E. g. I once got an unlisted number from a telephone operator because I sounded desperate (I was, but that was not the point) • E. g. Anna kour*va virus • E. g. If I walk in with coupla heavy looking boxes into the elevator to go to Boyd 5 th floor (at night) would you let me in? You can go into “secure” companies by looking like you “belong” there • Denial of service attacks – Network flooding, Distributed DOS, holding resources, viruses 4/598 N: Computer Networks

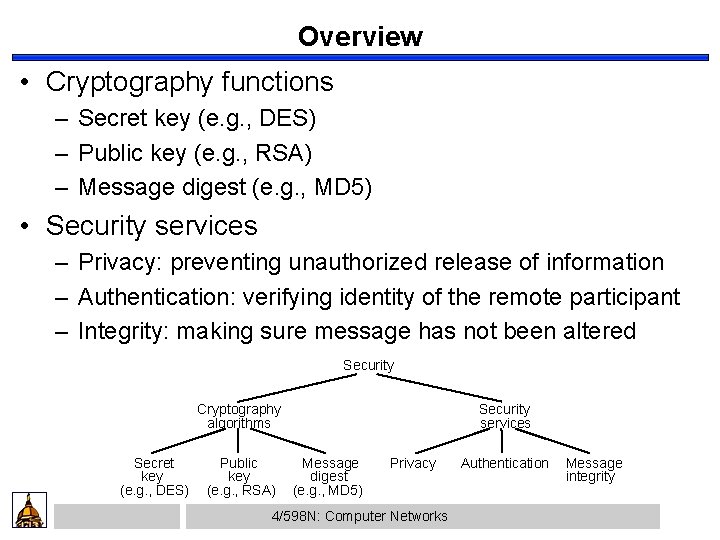
Overview • Cryptography functions – Secret key (e. g. , DES) – Public key (e. g. , RSA) – Message digest (e. g. , MD 5) • Security services – Privacy: preventing unauthorized release of information – Authentication: verifying identity of the remote participant – Integrity: making sure message has not been altered Security Cryptography algorithms Secret key (e. g. , DES) Public key (e. g. , RSA) Security services Message digest (e. g. , MD 5) Privacy 4/598 N: Computer Networks Authentication Message integrity

Encryption methods • Symmetric cryptography – Sender and receiver know the secret key (apriori ) • Fast encryption, but key exchange should happen outside the system • Asymmetric cryptography – Each person maintains two keys, public and private • M Private. Key(Public. Key(M)) • M Public. Key (Private. Key(M)) – Public part is available to anyone, private part is only known to the sender – E. g. Pretty Good Privacy (PGP), RSA 4/598 N: Computer Networks

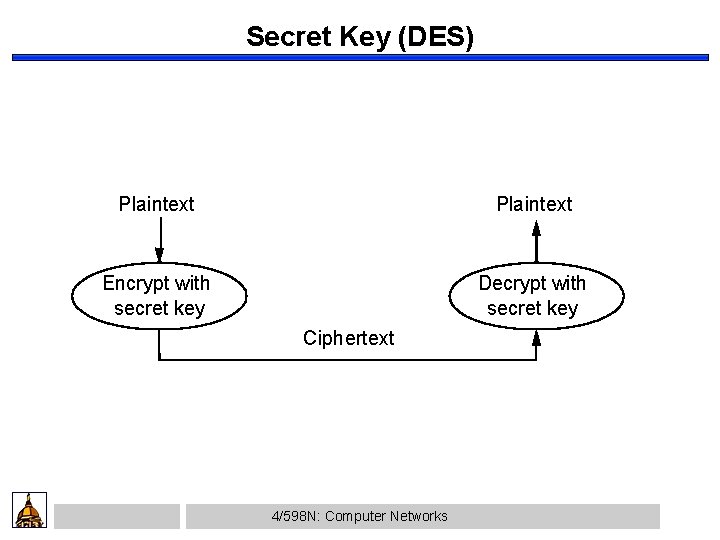
Secret Key (DES) Plaintext Encrypt with secret key Decrypt with secret key Ciphertext 4/598 N: Computer Networks

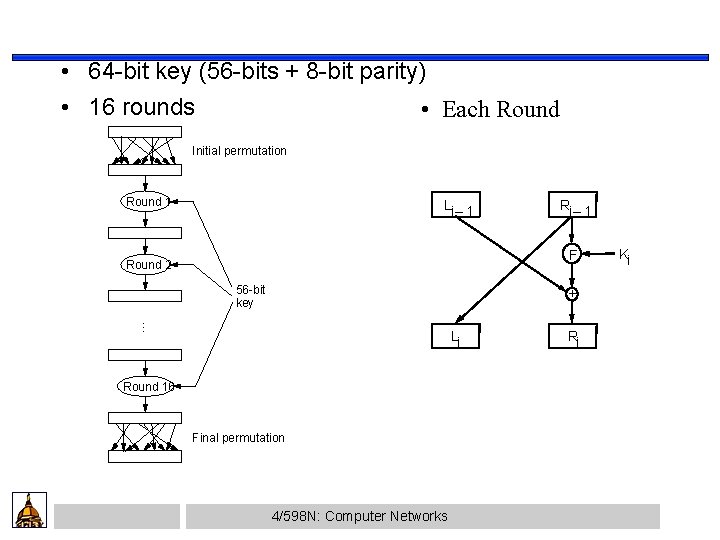
• 64 -bit key (56 -bits + 8 -bit parity) • 16 rounds • Each Round Initial permutation Round 1 Li – 1 Ri – 1 F Round 2 56 -bit key … + Li Round 16 Final permutation 4/598 N: Computer Networks Ri Ki

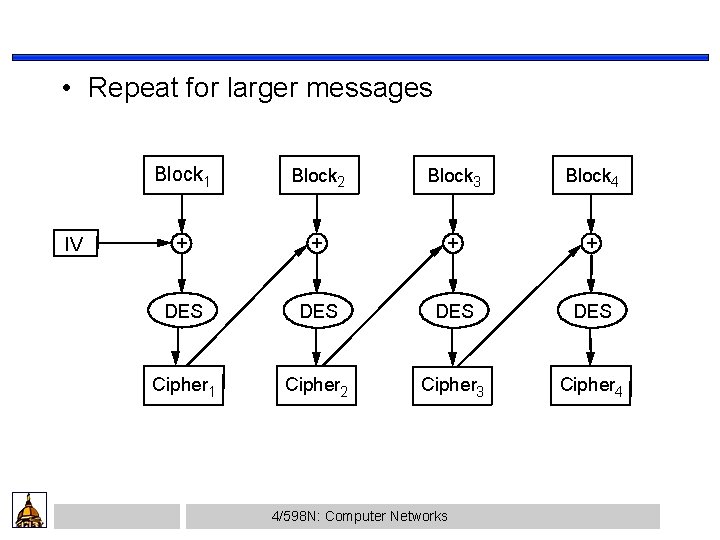
• Repeat for larger messages IV Block 1 Block 2 Block 3 Block 4 + + DES DES Cipher 1 Cipher 2 Cipher 3 Cipher 4 4/598 N: Computer Networks

RSA • Named after Rivest, Shamir and Adleman – Only receiver receives message: • Encode message using receivers public key – Only sender could’ve sent the message • Encode message using sender’s private key – Only sender could’ve sent the message and only receiver can read the message • Encode message using receivers public key and then encode using our private key 4/598 N: Computer Networks

Strength • Strength of crypto system depends on the strengths of the keys • Computers get faster – keys have to become harder to keep up • If it takes more effort to break a code than is worth, it is okay – Transferring money from my bank to my credit card and Citibank transferring billions of dollars with another bank should not have the same key strength 4/598 N: Computer Networks

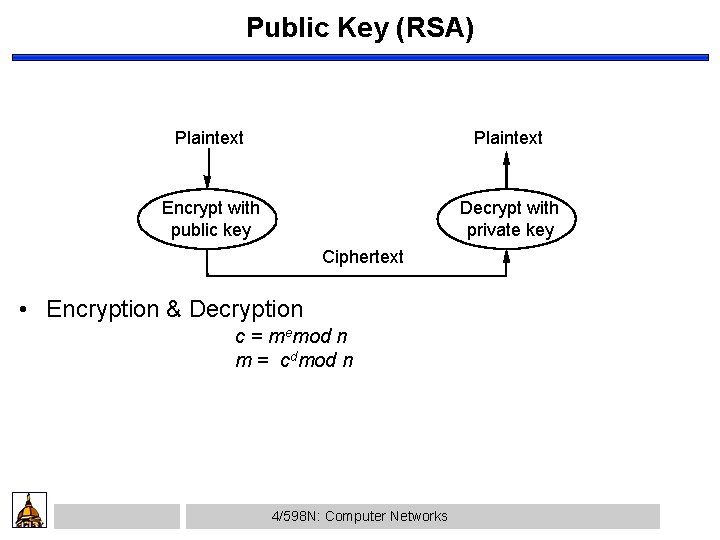
Public Key (RSA) Plaintext Encrypt with public key Decrypt with private key Ciphertext • Encryption & Decryption c = memod n m = cdmod n 4/598 N: Computer Networks

• • • RSA (cont) Choose two large prime numbers p and q (each 256 bits) Multiply p and q together to get n Choose the encryption key e, such that e and (p - 1) x (q - 1) are relatively prime. Two numbers are relatively prime if they have no common factor greater than one Compute decryption key d such that – d = e-1 mod ((p - 1) x (q - 1)) • Construct public key as (e, n) • Construct public key as (d, n) • Discard (do not disclose) original primes p and q 4/598 N: Computer Networks

My Public Key -----BEGIN PGP PUBLIC KEY BLOCK----Version: PGPfreeware 7. 0. 3 for non-commercial use <http: //www. pgp. com> m. QGi. BDqt. LPw. RBADn. G 0+9 Ik. Dv. I 8 t/3 wd. L 3 CSO 4 Dyt. EH 0 Njr. Nw. AYYIaewp 3 Mklsxk. P p 6 i. Vblwii. CH 4 T 4 Nqkaru+ka. EQ 1 h. STa 7 E/F 9 y. QCWN 5 J 0 u 1 U 7 mtg. TKFyt 7 VG 0 tx. AVx t. V 7 Tuyx. Nog. Jkpm 2 Bqo. Kqq. Ud. Cdbm+Gur. X/G 2 ynb. INj. EOvhcy 0 i 1 ttxgy. Drw. Cg/8 HZ t. M 0 i 06 VVNc. R/QCm. A+Jd. HGw. MEAIj. XLVV 97 hu. Etpu. WDiq 4 J 53 ec. V 3 HXQm 6 Xo. UZq 4 Sc n+nsv. Xe 4 UD+6 ldub/ri. Oq. By 22 f. BBAKh. Us. M 3 l. GFgr 7 h 19 X 3 RGdw/y. BVox+BLajp. W+ F+ddj. JAVSFe. Tv. Nanhn. XL 9 a 3 nw. CThb 4 a. EUTd. D 61 kgo. UWJl 2 Bns. K 1 DUSo 2 X 6 As. ZYo+ Gkn. OA/92 d. UNYUzsp. PLk. Xv. Pj. Oo+u. JEr. ZA 4 a. N+UYs. Jw. D 3 Al. Yug. VLkc 3 n. QBQy. SO 4 b. AR Xitjn. N 0 DA 6 Kz/j 6 e+cq. Re. Cy. Eu. Bn. Pta. Y/Nn/d. An 1 lg. Ul. J/Et. KQ 9 J 4 kr. I 3+Rx. Rmlp. Y Ut. Wy. Taak. V/QCXk. B/y. B 9 i 6 i. Afs. Cprlc. RSpm. ZAGu. NXr+p. HTHB 0 ILQm. U 3 Vy. ZW 5 k. YXIg Q 2 hhbm. Ry. YSA 8 c 3 Vy. ZW 5 k. YXJAY 3 Mud. Wdh. Lm. Vkd. T 6 JAFg. EEBECABg. FAjqt. LPw. ICw. MJ CAc. CAQo. CGQEFGw. MAAAAACgk. Ql. U 7 d. FVWfeisq. TACf. Xx. U 9 a 1 mbou. W 2 nb. Wdx 6 MHat. Q 6 TOg. Ao. M 9 W 1 PBRW 8 Iz 3 BIgcn. Ss. Z 2 UPNJHDu. QINBDqt. LPw. QCAD 2 Qle 3 CH 8 IF 3 Kiutap Qv. MF 6 Pl. TETl. Ptv. Fuu. Us 4 INo. Bp 1 aj. FOm. PQFXz 0 Af. Gy 0 Opl. K 33 TGSGSfg. Mg 71 l 6 Rf. U od. NQ+PVZX 9 x 2 Uk 89 PY 3 bzpnh. V 5 JZzf 24 rn. RPxfx 2 v. IPFRz. Bhznz. JZv 8 V+bv 9 k. V 7 H Aar. TW 56 No. KVy. Ot. Qa 8 L 9 GAFgr 5 f. SI/Vh. OSdv. NILSd 5 JEHNmszb. Dg. NRR 0 Pf. Iiz. HHxb LY 7288 kjw. EPwp. Vs. Yj. Y 67 VYy 4 XTj. TNP 18 F 1 d. Dox 0 Yb. N 4 z. ISy 1 Kv 884 b. Ep. QBg. Rj. Xy. E pwpy 1 ob. EAxn. IByl 6 yp. UM 2 Zafq 9 AKUJs. CRt. MIPWak. XUGfn. Hy 9 i. Usi. GSa 6 q 6 Jew 1 Xp Mgs 7 AAICCACLx. NC 3 Vth 553 Y 90 JCVy. M 9 m. PWzvrkjf. EGf. Bi. CFDZ 0 HONW 81 yw. Uy. V 6 j. T O/1 s. Usg. R 7 j. GB 26 XBsn. IY 96 a 9 WTp. Uo. I+20 Yst. FLRj 8 s. XOVXua. P/YTmg. SLv 82 O 6 SWd Bze 1 S 0 YJc. U 31/zd. Cftsz 67 UWT 8 vg 39 ye. Gy. Q 5 KQP 83 p 9 DKpi 4 Z 5 K 4 M 29 p 8 e. Ct 9 BY+ kid 94 h 9+16 ZT 8 JLF 0 i. Ew. Gap. Zvpa. Tuc. CNo. C 8 t 6 CKPto 0 d. Gpk. Yp 7 u. BYo. Sz. Lg. Nv. Uh 2 n Bj. GVEm. Luioabqb. Oaom. DEr. ITY 2 i. Nc. W 3 CCgjj. Yvgg/Hnu 7 HB 2 x. Kzu. VUN 1 NTGogcu. NI Yx 88 mi+d/Hx. TY 6 YNr 9 x. NW 0 f 0 p. Wk. ZDVB 0 i. QBMBBg. RAg. AMBQI 6 r. Sz 8 BRs. MAAAAAAo. J EJVO 3 RVVn 3 or. Yh. IAo. IQPx. Gv. Hm. X 8 c 6 ka. AZqko 1 z. YCeixc. AJ 9 tp 5 h/KQZr. IN/Bpy. TW 9 Xgv 4 qx. KEA== =Pv 5 O -----END PGP PUBLIC KEY BLOCK----- 4/598 N: Computer Networks

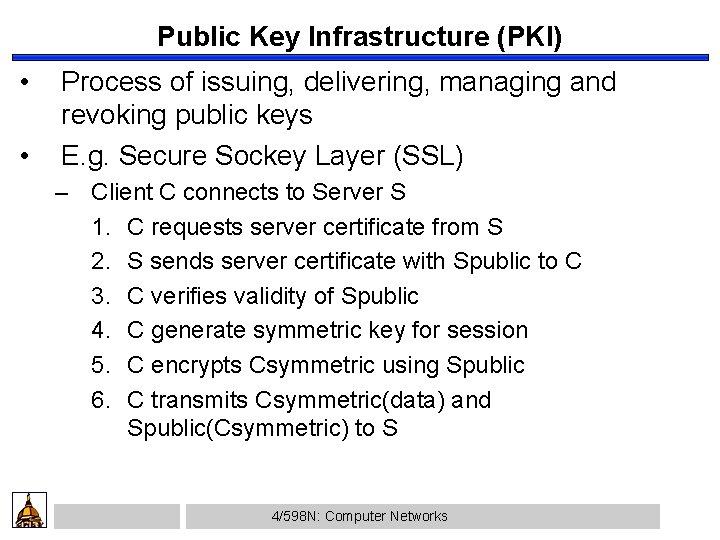
Public Key Infrastructure (PKI) • • Process of issuing, delivering, managing and revoking public keys E. g. Secure Sockey Layer (SSL) – Client C connects to Server S 1. C requests server certificate from S 2. S sends server certificate with Spublic to C 3. C verifies validity of Spublic 4. C generate symmetric key for session 5. C encrypts Csymmetric using Spublic 6. C transmits Csymmetric(data) and Spublic(Csymmetric) to S 4/598 N: Computer Networks