Security of Authentication Protocols Alexander Potapov Outline Authentication

















- Slides: 35

Security of Authentication Protocols Alexander Potapov

Outline � Authentication definition � Protocol architectures � Cryptographic properties � Freshness � Types of attack on protocols � Two-way authentication protocol attack � The Diffie-Hellman key exchange attack � Authentication protocol using a KDC

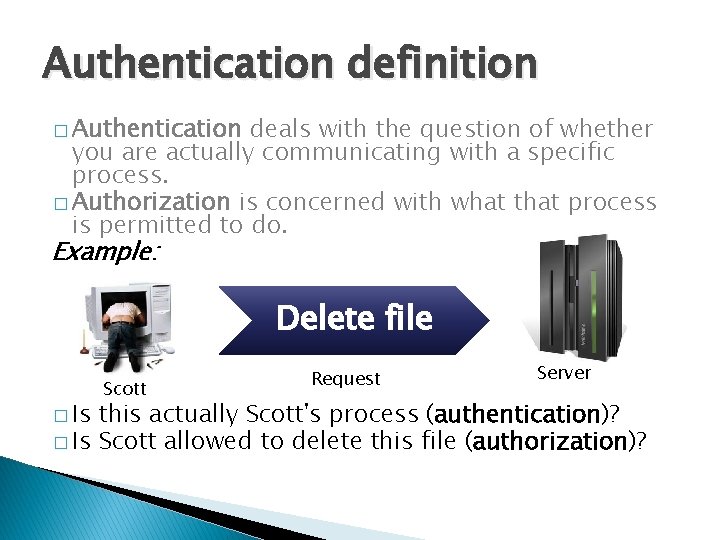
Authentication definition � Authentication deals with the question of whether you are actually communicating with a specific process. � Authorization is concerned with what that process is permitted to do.

Authentication definition � Authentication deals with the question of whether you are actually communicating with a specific process. � Authorization is concerned with what that process is permitted to do. Example: Delete file � Is Scott Request Server this actually Scott's process (authentication)? � Is Scott allowed to delete this file (authorization)?

Protocol architectures � Existing cryptographic keys � Method of session key generation

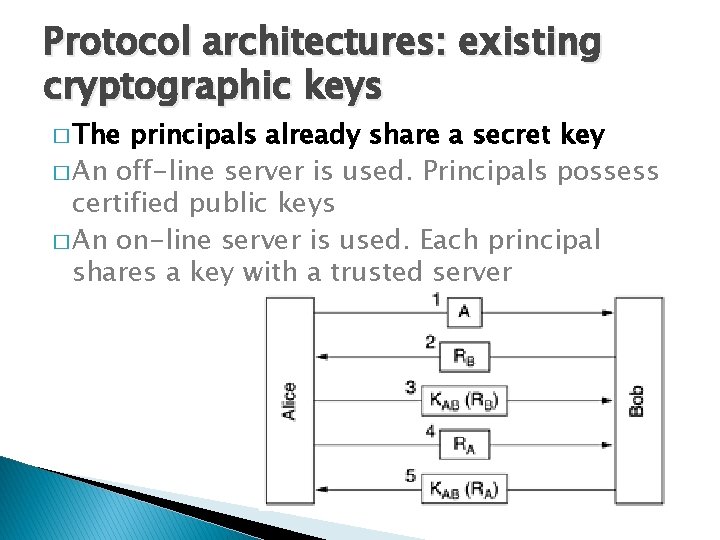
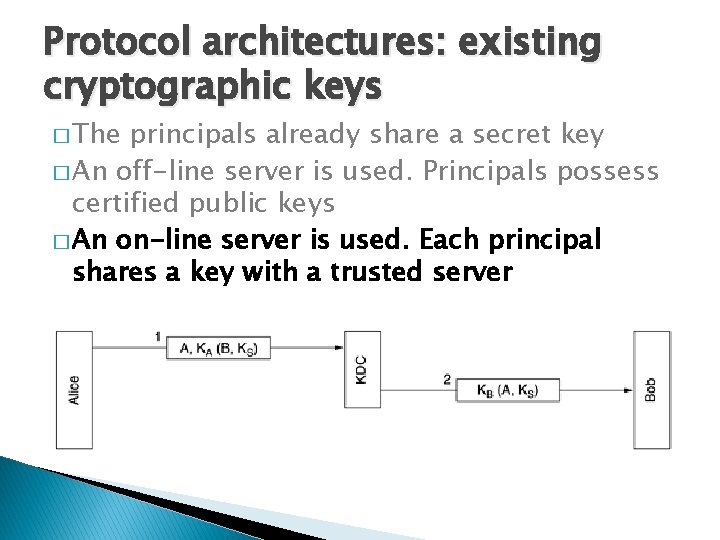
Protocol architectures: existing cryptographic keys � The principals already share a secret key � An off-line server is used. Principals possess certified public keys � An on-line server is used. Each principal shares a key with a trusted server

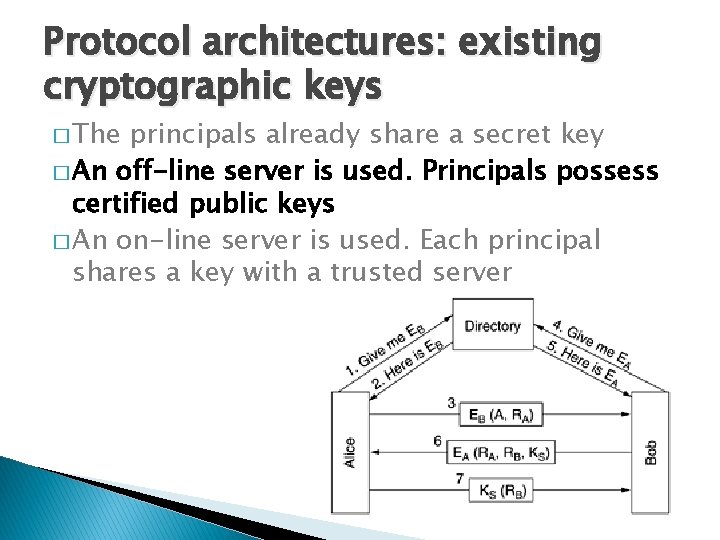
Protocol architectures: existing cryptographic keys � The principals already share a secret key � An off-line server is used. Principals possess certified public keys � An on-line server is used. Each principal shares a key with a trusted server

Protocol architectures: existing cryptographic keys � The principals already share a secret key � An off-line server is used. Principals possess certified public keys � An on-line server is used. Each principal shares a key with a trusted server

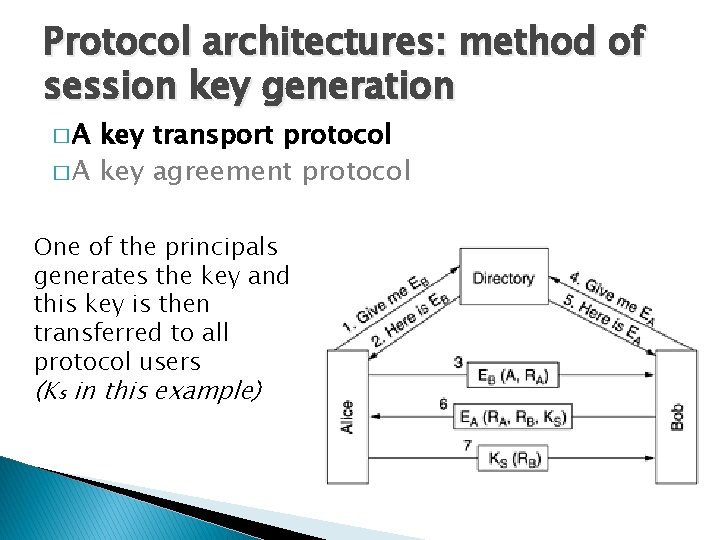
Protocol architectures: method of session key generation �A key transport protocol � A key agreement protocol One of the principals generates the key and this key is then transferred to all protocol users (Ks in this example)

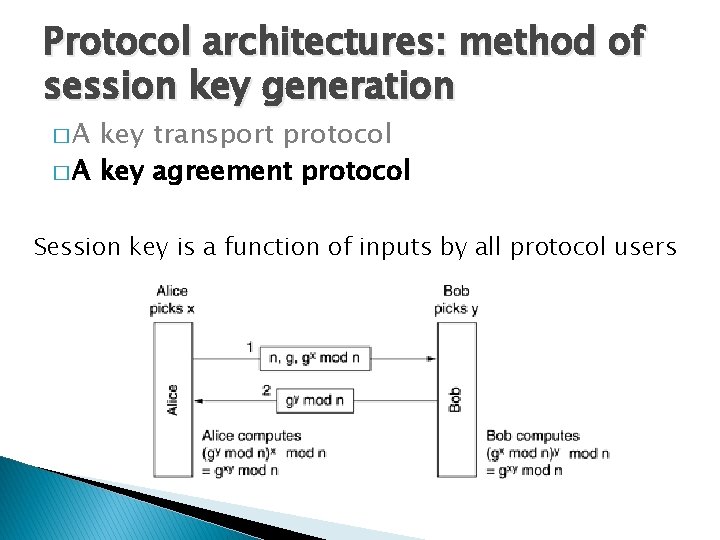
Protocol architectures: method of session key generation �A key transport protocol � A key agreement protocol Session key is a function of inputs by all protocol users

Cryptographic properties � Confidentiality � Data integrity � Data origin authentication � Non-repudiation Ensures that data is only available to those authorised to obtain it. Usually achieved through encryption/decryption.

Cryptographic properties � Confidentiality � Data integrity � Data origin authentication � Non-repudiation Ensures that data has not been altered by unauthorised entities. Usually achieved: • Use of hash functions in combination with encryption • Use of message authentication code to create a separate check field

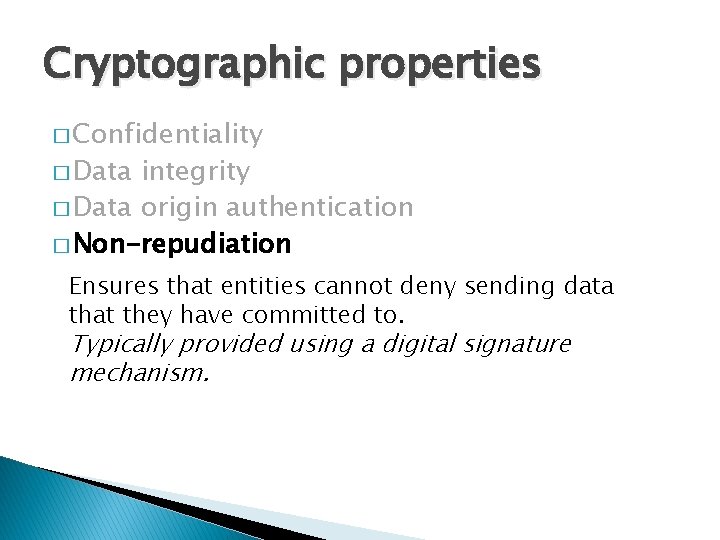
Cryptographic properties � Confidentiality � Data integrity � Data origin authentication � Non-repudiation Guarantees the origin of data. Normally achieved by the same mechanisms like we have in data integrity.

Cryptographic properties � Confidentiality � Data integrity � Data origin authentication � Non-repudiation Ensures that entities cannot deny sending data that they have committed to. Typically provided using a digital signature mechanism.

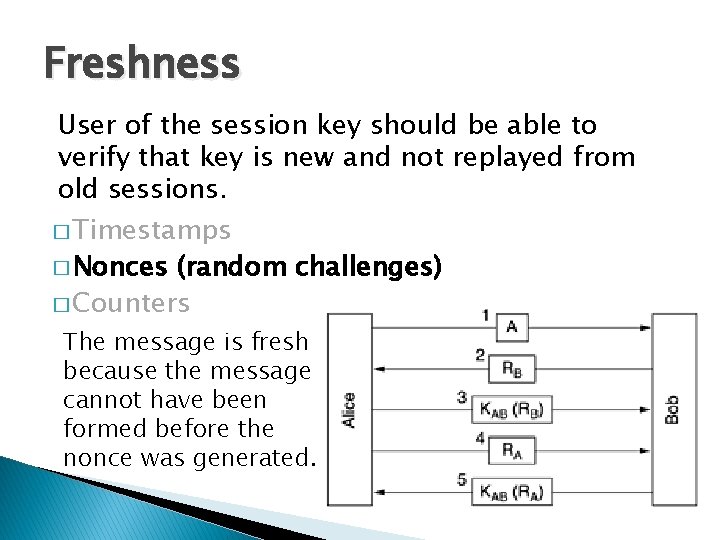
Freshness User of the session key should be able to verify that key is new and not replayed from old sessions. � Timestamps � Nonces (random challenges) � Counters On recipients side if message is within an acceptable window of the current time then the message is regarded as fresh.

Freshness User of the session key should be able to verify that key is new and not replayed from old sessions. � Timestamps � Nonces (random challenges) � Counters The message is fresh because the message cannot have been formed before the nonce was generated.

Freshness User of the session key should be able to verify that key is new and not replayed from old sessions. � Timestamps � Nonces (random challenges) � Counters The sender and recipient maintain a synchronized counter whose value is sent with the message and then incremented.

Types of attack on protocols Eavesdropping � Modification � Replay � Preplay � Reflection � Denial The adversary captures the information sent in the protocol of service � Typing attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping Modification � Replay � Preplay � Reflection � Denial The adversary alters the information sent in the protocol of service � Typing attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping The adversary records information seen in Replay � Replay the protocol and then � Preplay sends it to the same, or � Reflection a different, principal, � Denial of service possibly during a later � Typing attacks protocol run � Cryptanalysis � Certificate manipulation � Protocol interaction � Modification

Types of attack on protocols � Eavesdropping � Modification � Replay Preplay � Reflection � Denial The adversary engages in a run of the protocol prior to a run by the legitimate principals of service � Typing attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping � Modification � Replay � Preplay Reflection � Denial The adversary sends protocol message back to the principal who sent them of service � Typing attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping � Modification � Replay � Preplay � Reflection �Denialofofservice � Typing The adversary prevents or hinders legitimate principals from completing the protocol attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping � Modification � Replay � Preplay � Reflection � Denial The adversary replaces a protocol message field of one type with a message field of another type of service � Typing attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping � Modification � Replay � Preplay � Reflection � Denial The adversary gains some useful leverage from the protocol to help in cryptanalysis of service � Typing attacks � Cryptanalysis � Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping � Modification � Replay � Preplay � Reflection � Denial The adversary chooses or modifies certificate information to attack one or more protocol runs of service � Typing attacks � Cryptanalysis Certificate manipulation � Protocol interaction

Types of attack on protocols � Eavesdropping � Modification � Replay � Preplay � Reflection � Denial The adversary chooses a new protocol to interact with a known protocol of service � Typing attacks � Cryptanalysis � Certificate manipulation Protocol interaction � Protocol interaction

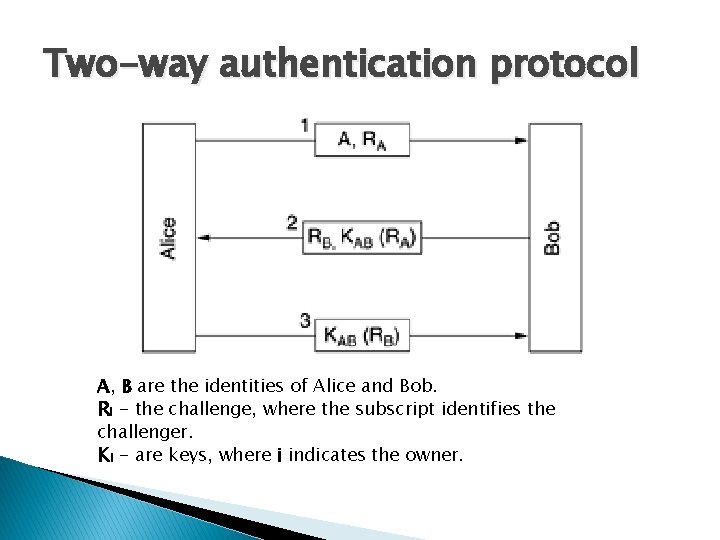
Two-way authentication protocol A, B are the identities of Alice and Bob. Ri - the challenge, where the subscript identifies the challenger. Ki - are keys, where i indicates the owner.

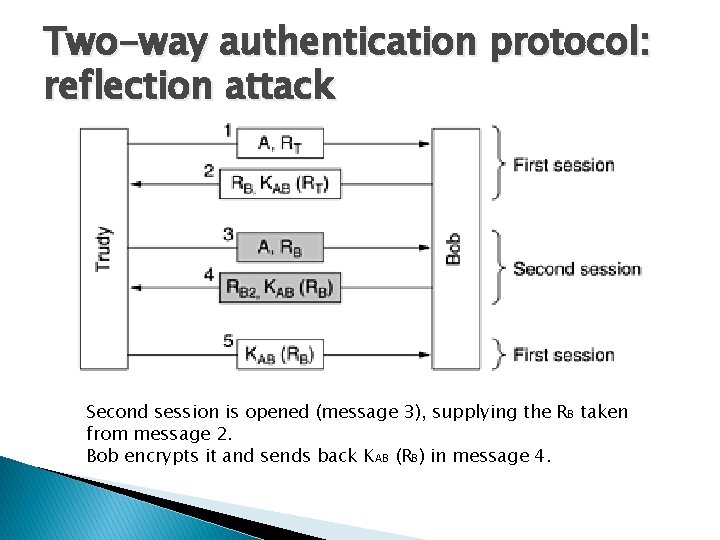
Two-way authentication protocol: reflection attack Second session is opened (message 3), supplying the RB taken from message 2. Bob encrypts it and sends back KAB (RB) in message 4.

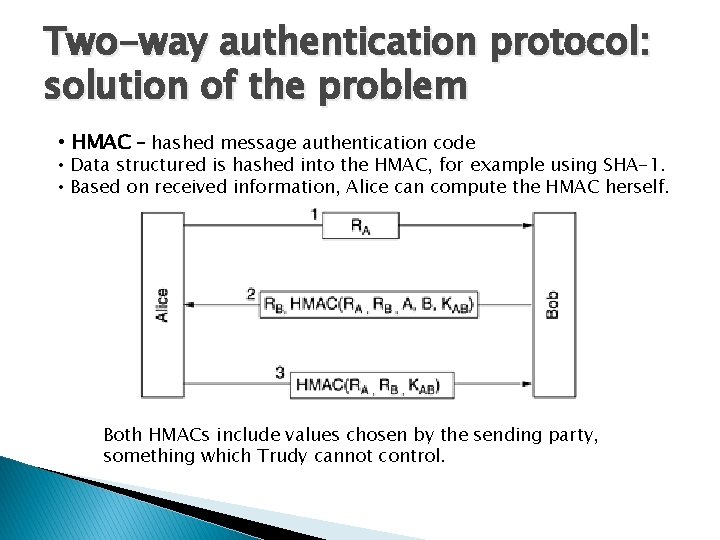
Two-way authentication protocol: solution of the problem • HMAC – hashed message authentication code • Data structured is hashed into the HMAC, for example using SHA-1. • Based on received information, Alice can compute the HMAC herself. Both HMACs include values chosen by the sending party, something which Trudy cannot control.

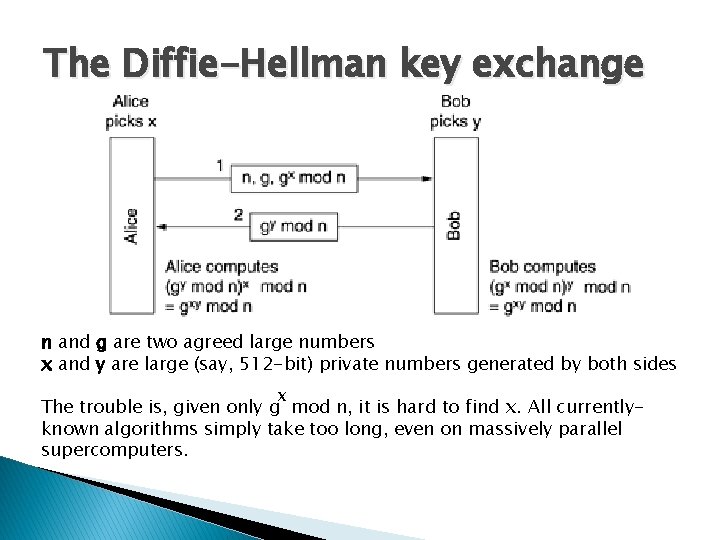
The Diffie-Hellman key exchange n and g are two agreed large numbers x and y are large (say, 512 -bit) private numbers generated by both sides x The trouble is, given only g mod n, it is hard to find x. All currentlyknown algorithms simply take too long, even on massively parallel supercomputers.

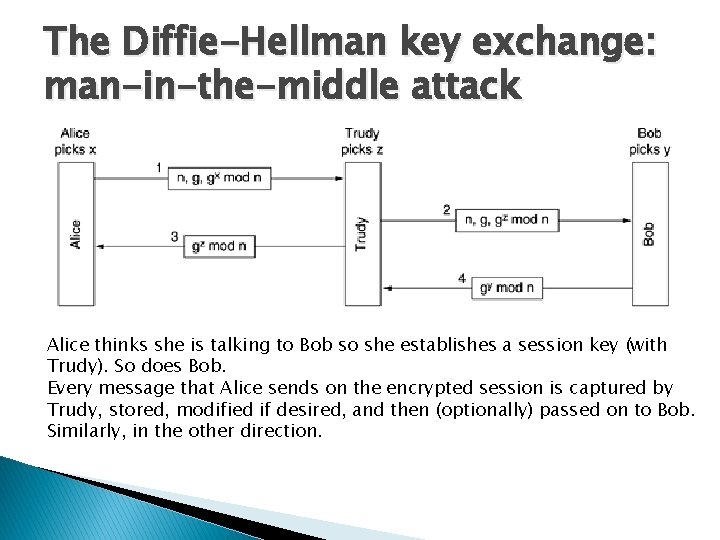
The Diffie-Hellman key exchange: man-in-the-middle attack Alice thinks she is talking to Bob so she establishes a session key (with Trudy). So does Bob. Every message that Alice sends on the encrypted session is captured by Trudy, stored, modified if desired, and then (optionally) passed on to Bob. Similarly, in the other direction.

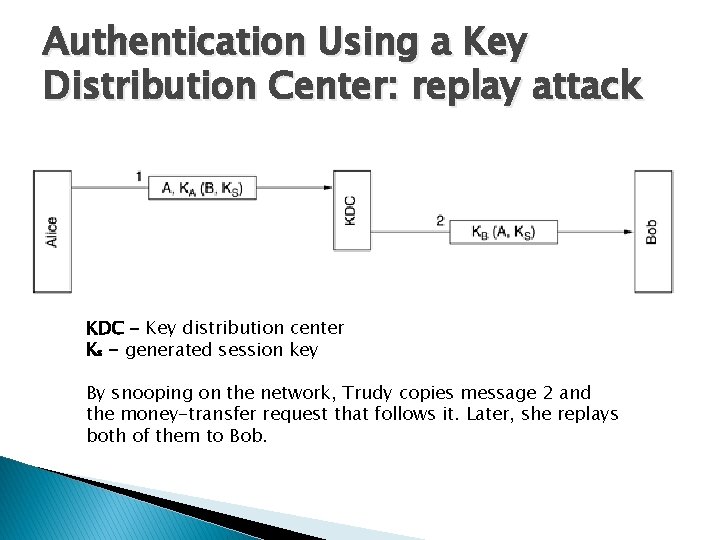
Authentication Using a Key Distribution Center: replay attack KDC - Key distribution center Ks - generated session key By snooping on the network, Trudy copies message 2 and the money-transfer request that follows it. Later, she replays both of them to Bob.

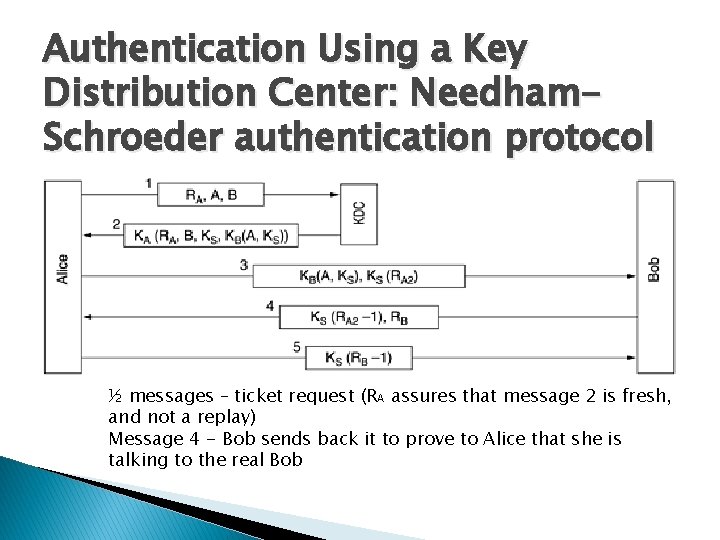
Authentication Using a Key Distribution Center: Needham. Schroeder authentication protocol ½ messages – ticket request (RA assures that message 2 is fresh, and not a replay) Message 4 - Bob sends back it to prove to Alice that she is talking to the real Bob

Reference Protocols for authentication and key establishment Colin Boyd, Anish Mathuria Computer networks Andrew S. Tanenbaum