ROUTING TECHNIQUES IN WIRELESS SENSOR NETWORKS A SURVEY
















- Slides: 29

ROUTING TECHNIQUES IN WIRELESS SENSOR NETWORKS: A SURVEY

Outline Background Classification of Routing Protocols Data Centric Protocols � Flooding and Gossiping � SPIN � Directed Diffusion � Rumor Routing

Background Sensor nodes � Small, wireless, battery powered � Energy, bandwidth constrained � Data sensing, relaying, aggregating � No global addressing scheme Sink nodes � More powerful nodes � Usually gateway to wired networks � Data collecting and processing

Goal So at network layer, it is highly desirable to find methods for energy efficient route discovery and relaying of data from the sensor nodes to the BS so that the life time of the network is maximized.

Routing Protocols

Data-centric Protocols The ability to query a set of sensor nodes Attribute-based naming Data aggregation during relaying For example: � Flooding & Gossiping SPIN � Directed Diffusion � Rumor Routing �

Flooding & Gossiping In flooding, sensor broadcasts packets to all its neighbors till dst reached or packets' ttl == 0 In gossiping, sensor sends packets to a randomly selected neighbor which does the same

Flooding & Gossiping(cont. ) Pros � Simple � No routing, no state maintenance Cons � Implosion � Overlap Resource blindness � Delay in Gossiping �

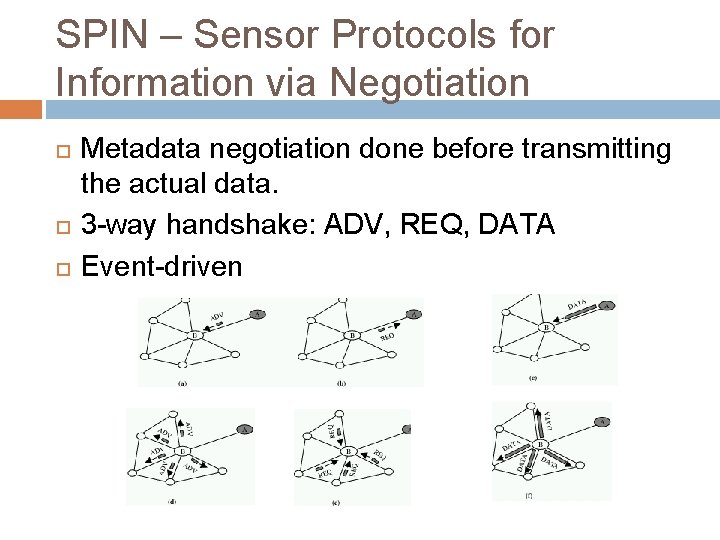
SPIN – Sensor Protocols for Information via Negotiation Metadata negotiation done before transmitting the actual data. 3 -way handshake: ADV, REQ, DATA Event-driven

SPIN(cont. ) Pros � Solve the classic problems � Topological changes are localized Cons � No guarantee on the delivery of data

Directed Diffusion Sink node floods named “interest” with larger update interval Sensor node sends back data via “gradients” Sink node then sends the same “interest” with smaller update interval Query-driven

Directed Diffusion (cont) Pros � On demand route setup � Each node does aggregation and caching, thus good energy efficiency and low delay Cons � Query-driven, not a good choice for continuous data delivery � Extra overhead for data matching and queries

Rumor Routing A trade-off between Query & Event flooding An agent, a long-lived packet, is generated when events happen The agent propagate the event to distant nodes

Rumor Routing (cont) Pros � Avoid query flooding Cons � Performs well only when # of events is small � Overhead to maintain agents and event-tables

Hierarchical Routing Protocols Ø When sensor density increases single tier networks cause Gateway overloading Increased latency Large energy consumption Clustered Network allow coverage of large area of interest and additional load without degrading the performance

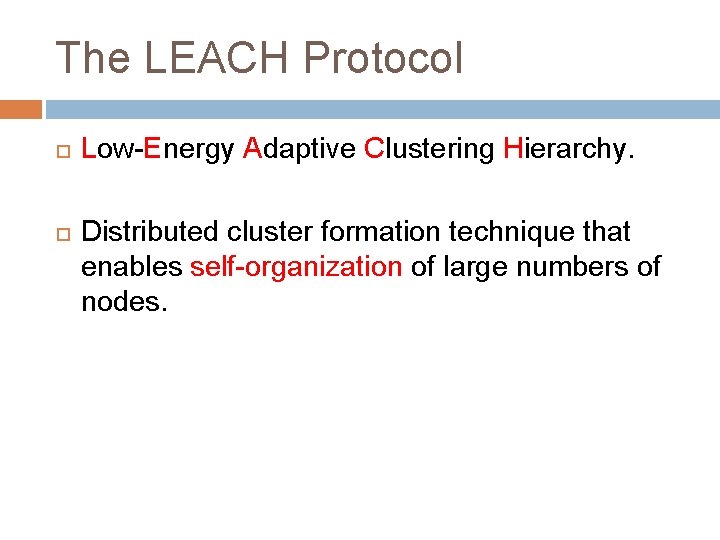
Hierarchical Routing Protocols Idea Ø Ø Partition the entire network into regions or clusters. Select one or more nodes as the cluster head. The routing is nodes -> cluster head A -> cluster head B -> cluster head C -> nodes The routing between cluster heads and the routing within a cluster may follow different protocols (EGPBGP and IGP-OSPF). Issues resolved: Energy wasted in collision, collision avoidance, idle-listening Achieves Ø Ø Better scalability Removes the load to less powerful nodes

The LEACH Protocol Low-Energy Adaptive Clustering Hierarchy. Distributed cluster formation technique that enables self-organization of large numbers of nodes.

LEACH - Setup Set up phase Cluster Head (CH) selection (random + rotating) Ø ADV Ø Join REQ Ø TDMA SCH prepared by CH (no collisions and reduced energy consumption) Ø

LEACH - Steady State Broken into frames, where nodes send their data to the cluster head at most once per frame during their allocated transmission slot. Once the cluster head receives all the data, it performs data aggregation.

PEGASIS Power-Efficient GAthering in Sensor Information Systems. The key idea in PEGASIS is to form a chain among the sensor nodes so that each node will receive from and transmit to a close neighbor. Well, what was so bad in LEACH except for a bad name. . .

PEGASIS - Concept Be Greedy! Align with the one that has the max signal strength, form a near-optimal chain. Communicate with neighbors only. But who takes care of communicating to BS?

PEGASIS - Leader The main idea in PEGASIS is for each node to receive from and transmit to close neighbors and take turns being the leader for transmission to the BS. Nodes take turns transmitting to the BS (i mod N node in round i out of N nodes shall transmit to BS).

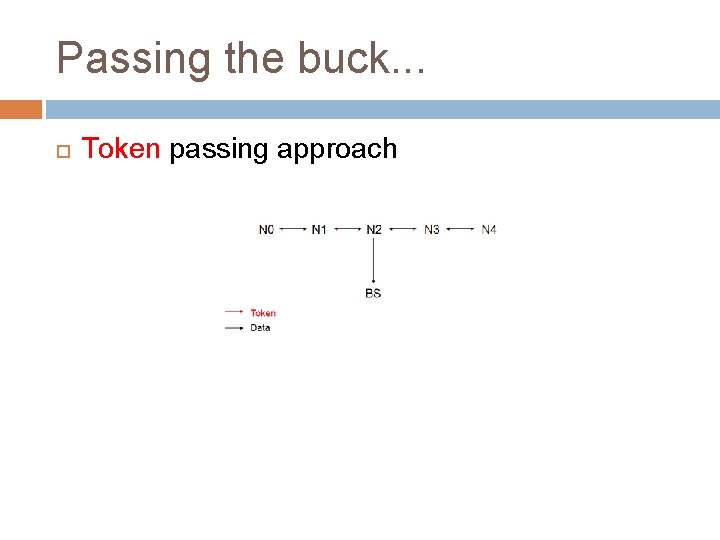
Passing the buck. . . Token passing approach

The TEEN Protocol Threshold sensitive Energy Efficient sensor Network protocol. Proactive Protocols (LEACH) � The nodes in this network periodically switch on their sensors and transmitters, sense the environment and transmit the data of interest. Reactive Protocols (TEEN) � The nodes react immediately to sudden and drastic changes in the value of a sensed attribute.

TEEN - Functioning At every cluster change time, the cluster-head broadcasts to its members � Hard This is a threshold value for the sensed attribute. It is the absolute value of the attribute beyond which, the node sensing this value must switch on its transmitter and report to its cluster head. � Soft Threshold (HT) Threshold (ST) This is a small change in the value of the sensed attribute which triggers the node to switch on its transmitter and transmit.

TEEN - Hard Threshold The first time a parameter from the attribute set reaches its hard threshold value, the node switches on its transmitter and sends the sensed data. The sensed value is stored in an internal variable in the node, called the sensed value (SV).

TEEN - Soft Threshold The nodes will next transmit data in the current cluster period, only when both the following conditions are true: � The current value of the sensed attribute is greater than the hard threshold. � The current value of the sensed attribute differs from SV by an amount equal to or greater than the soft threshold.

TEEN - Drawback If the thresholds are not reached, the user will not get any data from the network at all and will not come to know even if all the nodes die. Adaptive Periodic TEEN This scheme practical implementation would have to ensure that there are no collisions in the cluster.

Thank you