Routing Techniques in Wireless Sensor Networks A Survey





























- Slides: 107

Routing Techniques in Wireless Sensor Networks: A Survey IEEE Wireless Communication Dec 2004 Jamal N. Al-Karaki, The Hashemite University Ahmed E. Kamal, Iowa State University presented by 曾勇誠 R 93725047

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

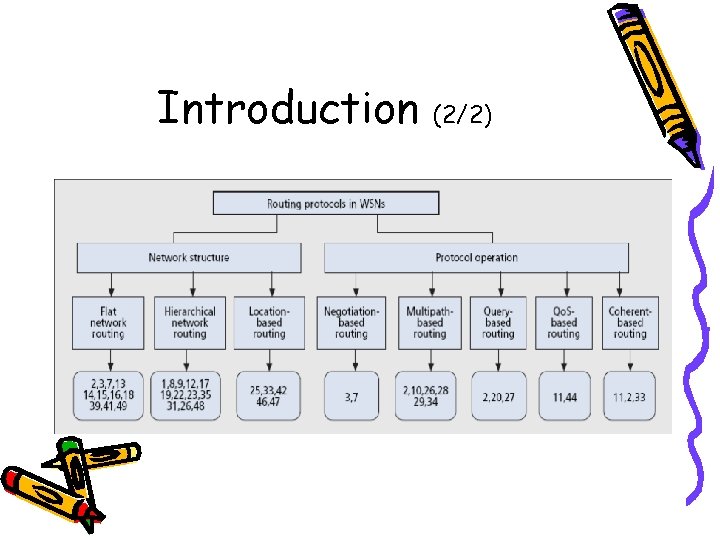
Introduction (1/2) • Routing protocols in WSNs Differ depending on the application and network architecture • Classified into three categories based on the underlying network structure: – Flat: Nodes are assigned equal roles – Hierarchical: Nodes will play different roles – Location-based: Nodes’ positions are exploited to route data • Classified into multipath-based, query-based, negotiationbased, Qo. S-based, and coherent-based depending on the protocol operation • Trade-offs between energy and communication overhead savings

Introduction (2/2)

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Challenges (1/2) • Due to the relatively large number of sensor nodes, it is not possible to build a global addressing scheme for the deployment of a large number of sensor nodes as the overhead of ID maintenance is high • Applications of sensor networks require the few of sensed data from multiple sources to a particular BS • Sensor nodes are tightly constrained in terms of energy, processing, and storage capacities

Challenges (2/2) • In most application scenarios, nodes in WSNs are generally stationary after deployment except for maybe a few mobile nodes. • Sensor networks are application-specific • Position awareness of sensor nodes is important since data collection is normally based on the location • Data collected based on common phenomena, so there is a high probability that this data has some redundancy

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

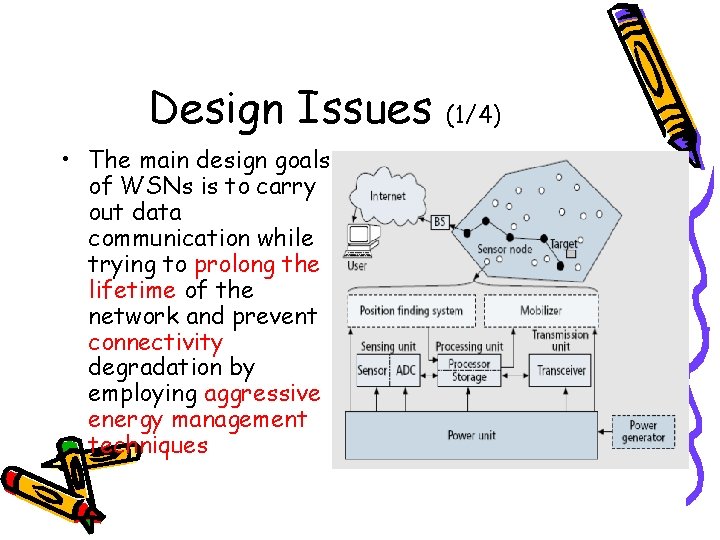
Design Issues • The main design goals of WSNs is to carry out data communication while trying to prolong the lifetime of the network and prevent connectivity degradation by employing aggressive energy management techniques (1/4)

Design Issues (2/4) • Node deployment: application-dependent • Energy consumption without losing accuracy • Data reporting method – Manual (deterministic): data is routed through predetermined paths – Randomized: nodes are scattered randomly, creating an ad hoc routing infrastructure – Distribution of nodes is not uniform, optimal clustering becomes necessary – Use up their limited supply of energy – The malfunctioning of some sensor nodes – – Time-driven: for application requiring periodic data monitoring Event-driven: react due to a certain event (time-critical ap) Query-driven: response to a query (time-critical ap) Hybrid

Design Issues • Node/link heterogeneity • Fault tolerance • Scalability • Network dynamics • Transmission media (3/4) – For example, hierarchical protocols designate a cluster head node – The failure of sensor nodes should not affect the overall task of the sensor network – Any routing scheme must be able to work with huge number of sensor nodes – Nodes can be mobile – The phenomenon can be mobile – The required bandwidth is low(1 -100 kb/s) – TDMA-based protocols conserve more energy than contention-based protocols (like CSMA)

Design Issues • Connectivity • Coverage • Data aggregation • Quality of service (4/4) – Density in sensor networks – Depends on the possibly random distribution of nodes – A sensor’s view of the environment is limited in both range and accuracy – Sensor nodes may generate significant redundant data – To reduce the number of transmissions – Network lifetime often is considered more important – Bounded latency for data delivery is a condition for time-constrained applications

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Flat Routing • • Each node plays the same role Data-centric routing • Protocols – Due to not feasible to assign a global id to each node – Save energy through data negotiation and elimination of redundant data – – – – – Sensor Protocols for Information via Negotiation (SPIN) Directed diffusion (DD) Rumor routing Minimum Cost Forwarding Algorithm (MCFA) Gradient-based routing (GBR) Information-driven sensor querying/Constrained anisotropic diffusion routing (IDSQ/CADR) COUGAR ACQUIRE Energy-Aware Routing protocols with random walks

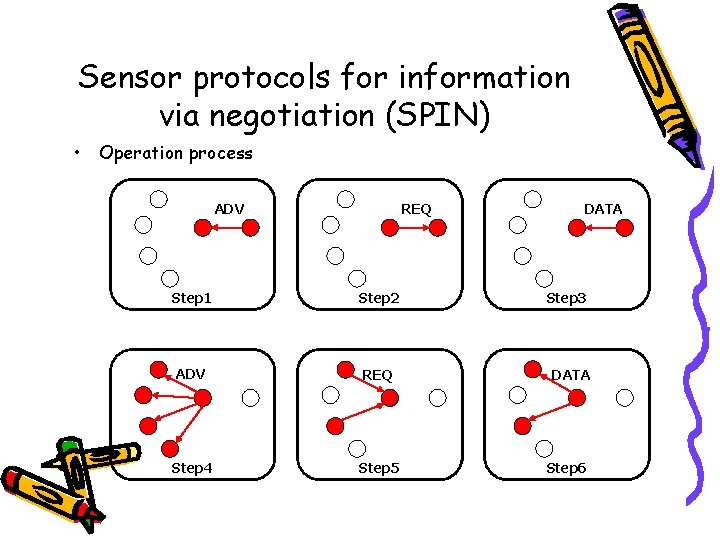
Sensor protocols for information via negotiation (SPIN) • Features – Negotiation • to operate efficiently and to conserve energy • using a meta-data – Resource adaptation • To extend the operating lifetime of the system • monitoring their own energy resources • SPIN Message – ADV – new data advertisement – REQ – request for ADV data – DATA – actual data message – ADV, REQ messages contain only meta-data

Sensor protocols for information via negotiation (SPIN) • Operation process ADV REQ Step 1 Step 2 ADV REQ Step 4 Step 5 DATA Step 3 DATA Step 6

Sensor protocols for information via negotiation (SPIN) • Resource adaptive algorithm – When energy is plentiful • Communicate using the 3 -stage handshake protocol – When energy is approaching a low-energy threshold • • If a node receives ADV, it does not send out REQ • Energy is reserved to sensing the event Advantage – Simplicity • Each node performs little decision making when it receives new data • Need not forwarding table • – Robust to topology change Drawback – Large overhead • Data broadcasting

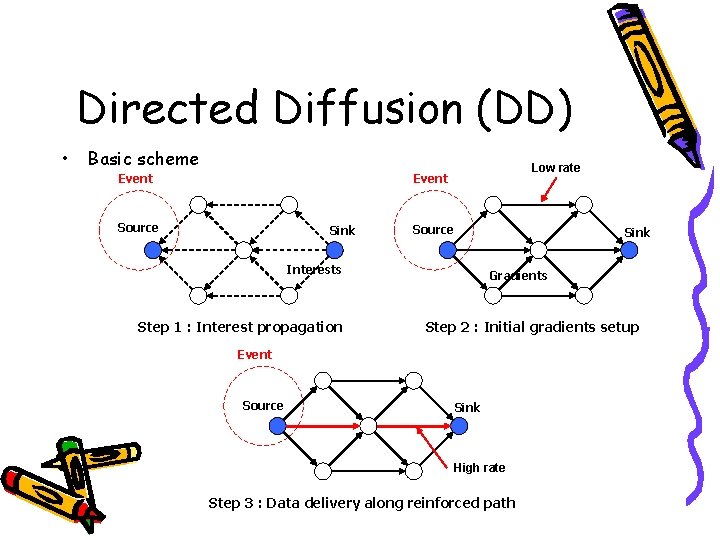
Directed Diffusion (DD) • Feature • Four elements – – – Data-centric routing protocol A path is established between sink node and source node Localized interactions • The propagation and aggregation procedures are all based on local information – Interest • A task description which is named by a list of attribute-value pairs that describe a task – Gradient • Path direction, data transmission rate – Data message – Reinforcement • To select a single path from multiple paths

Directed Diffusion (DD) • Basic scheme Low rate Event Source Sink Interests Step 1 : Interest propagation Gradients Step 2 : Initial gradients setup Event Source Sink High rate Step 3 : Data delivery along reinforced path

Directed Diffusion (DD) • Advantage – Small delay • Always transmit the data through shortest path – Robust to failed path • Drawback – Imbalance of node lifetime • The energy of node on shortest path is drained faster than another – Time synchronization technique • To implement data aggregation • Not easy to realize in a sensor network – The overhead involved in recording information • Increasing the cost of a sensor node

Rumor Routing • Feature – Combine query flooding and event flooding – Discovering arbitrary paths instead of the shortest path – Rumor routing is attractive only when • The number of queries is larger than a threshold • The number of events is smaller than another threshold • Assumption – The network is composed of densely distributed nodes – Only short distance transmissions – Immobile nodes

Rumor Routing • Basic scheme – Each node maintain • A lists of neighbors • An event table – When a node detects an event • Generate an agent • Let it travel on a random path • The visited node form a gradient to the event – When a sink needs an event • Transmit a query • The query meets some node which lies on the gradient – Route establishment

Rumor Routing • The node sensing an event probabilistically generates an agent. The probability of generating an agent is an algorithm parameter… • In order to propagate directions to the event as far as possible in the network, a straightening algorithm is used – The agent maintains a list of recently seen nodes. – When picking its next hop, it will first try nodes not in the list.

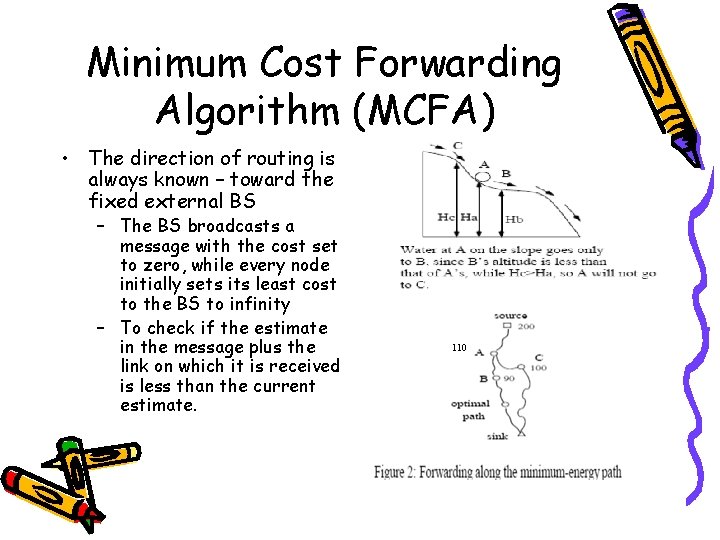
Minimum Cost Forwarding Algorithm (MCFA) • Objective – Establish the cost field – Transmit the data through the minimum-cost path • Feature – Optimality • Minimum cost path criteria : hop count, energy consumption, delay etc. – Simplicity • Need not to maintain forwarding table • Need not to know an ID for a neighbor node

Minimum Cost Forwarding Algorithm (MCFA) • Operation process – Each node stores its cost to the sink – The sink broadcasts an ADV message • containing its own cost (0 initially) – Each node receiving the message transmits neighbor node • Add the cost in ADV message to its own cost – The cost field is set up • after the ADV message propagates through the network – The source transmits an information through cost field • Drawback – Limited network size • The time to set the cost field is directly proportional to the size of the network – Load is not balanced

Minimum Cost Forwarding Algorithm (MCFA) • The direction of routing is always known – toward the fixed external BS – The BS broadcasts a message with the cost set to zero, while every node initially sets its least cost to the BS to infinity – To check if the estimate in the message plus the link on which it is received is less than the current estimate. 110

Gradient-based routing • Memorize the number of hops when the interest is diffused • Minimum the number of hops to reach the BS • To obtain balanced traffic and prolong lifetime: – A stochastic scheme – An energy-based – A stream-based scheme

Information-driven sensor querying and constrained anisotropic diffusion routing (IDSQ/CADR) • Key idea – Routing data in a network so that information gain is maximized while power and bandwidth consumption is minimized • CADR: – Aims to be a general form of directed diffusion – Diffuses queries by using a set of information criteria to select which sensors can get the data • IDSQ: – Does not specifically define how the query and information are routed – The querying node can determine which node can provide the most useful information with the additional advantage of balancing the energy cost

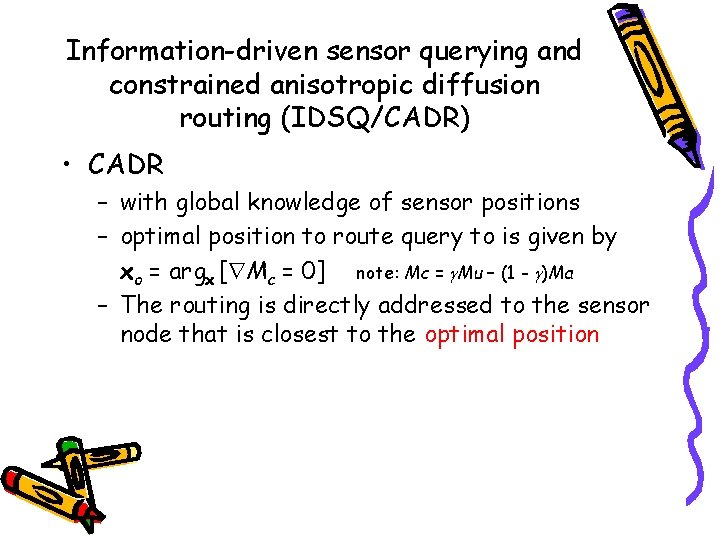
Information-driven sensor querying and constrained anisotropic diffusion routing (IDSQ/CADR) • CADR – with global knowledge of sensor positions – optimal position to route query to is given by xo = argx [ Mc = 0] note: Mc = Mu – (1 - )Ma – The routing is directly addressed to the sensor node that is closest to the optimal position

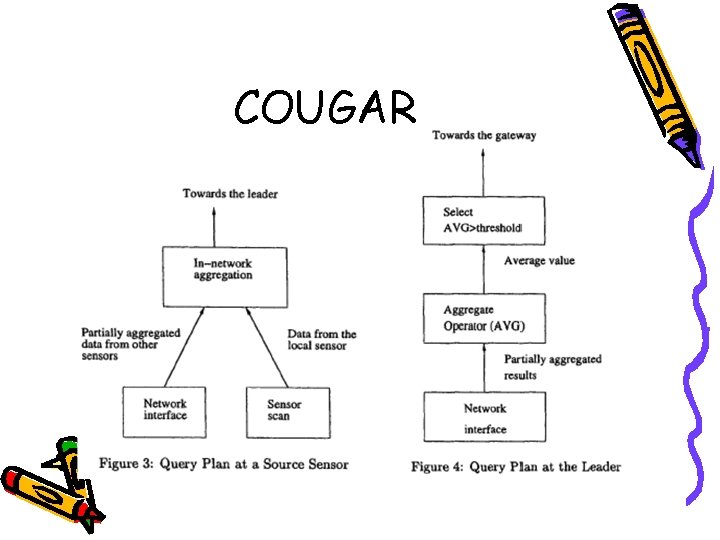
COUGAR • View the network as a huge distributed database system • Use declarative queries • Abstract query processing from the network layer • Disadvantages – May add extra overhead – query layer – Synchronization – Leader nodes maintenance

COUGAR

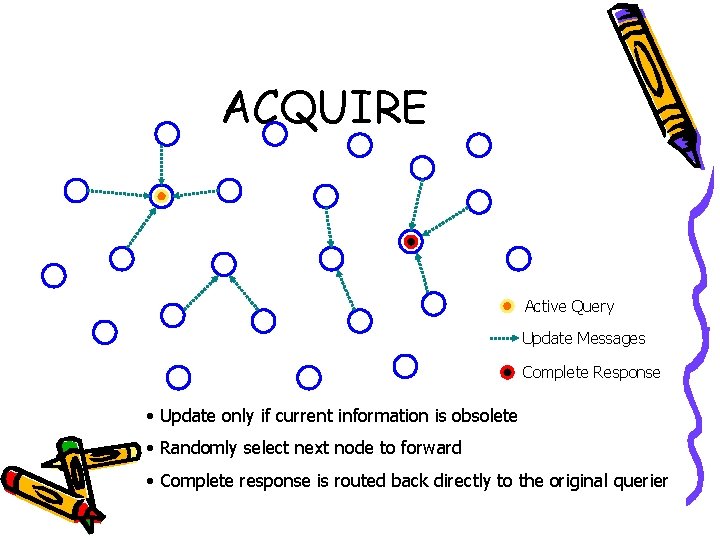
ACQUIRE • Views the network as a distributed DB where complex queries can be divided into several subqueries • The BS sends a query, which is then forwarded by each node receiving the query • Each node tries to respond to the query partially bye using its precached information • Triggered update obtaining information from all neighborhood within a look-ahead of d hops • Query is returned back to the querying node as a completed response

ACQUIRE Active Query Update Messages Complete Response • Update only if current information is obsolete • Randomly select next node to forward • Complete response is routed back directly to the original querier

Energy-Aware Routing • A destination-initiated reactive protocol • It maintains a set of paths • Choosing paths by means of certain probability depending on how low the energy consumption is

Energy-Aware Routing • Setup Phase Local Rule Directional flooding Sensor p 1 = 0. 75 Controller p 2 = 0. 25 10 n. J 30 n. J

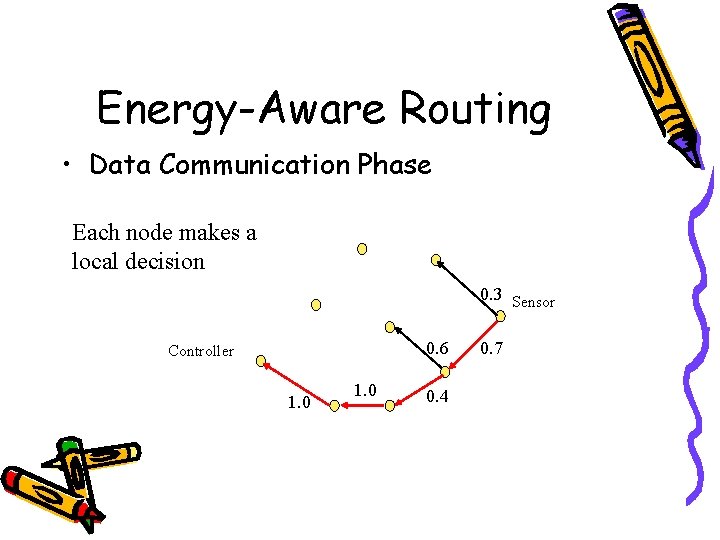
Energy-Aware Routing • Data Communication Phase Each node makes a local decision 0. 3 Sensor 0. 6 Controller 1. 0 0. 4 0. 7

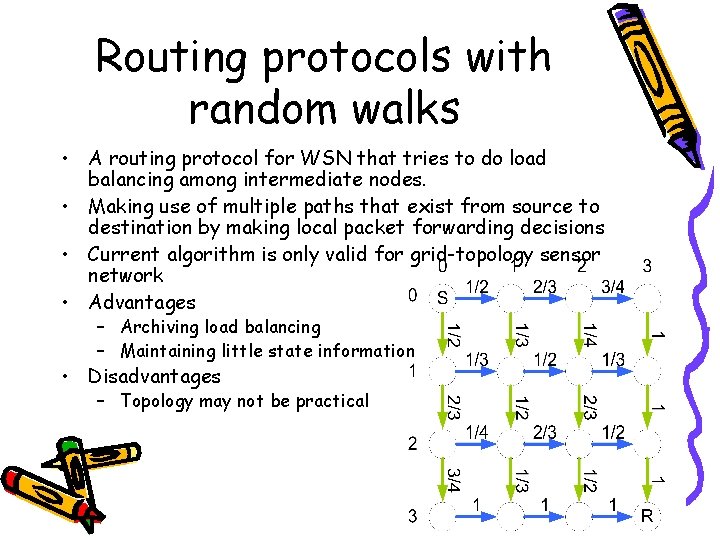
Routing protocols with random walks • A routing protocol for WSN that tries to do load balancing among intermediate nodes. • Making use of multiple paths that exist from source to destination by making local packet forwarding decisions • Current algorithm is only valid for grid-topology sensor network • Advantages – Archiving load balancing – Maintaining little state information • Disadvantages – Topology may not be practical

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Hierarchical Routing • • • Nodes will play different roles Advantages related to scalability and efficient communication Mainly two-layer routing • Protocols – Select cluster heads – Routing – – – – Low Energy Adaptive Clustering Hierarchy (LEACH) Power-Efficient Gathering in Sensor Information Systems (PEGASIS) Threshold-Sensitive Energy Efficient Protocols Small Minimum energy communication network (MECN) Self-organizing protocol (SOP) Virtual grid architecture routing Hierarchical power-aware routing Two –Tier Data Dissemination (TTDD)

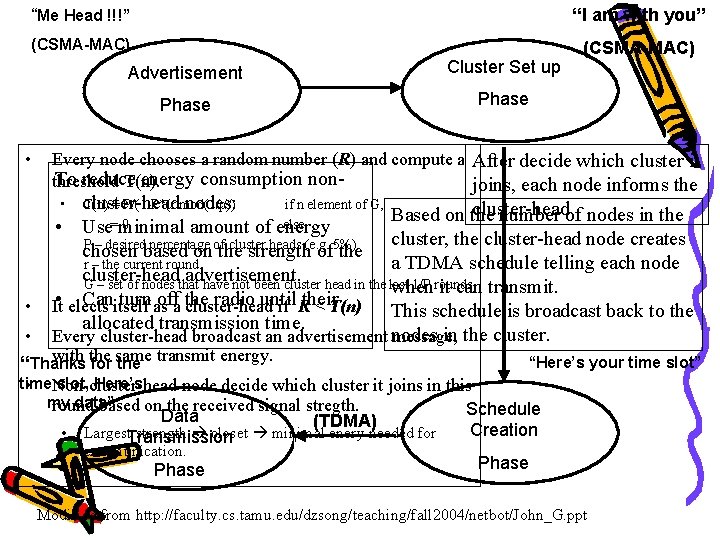
Low-energy adaptive clustering hierarchy (LEACH) • Randomly select sensor nodes as cluster-heads, so the high energy dissipation in communicating with the base station is spread to all sensor nodes in the sensor network. • Set-up phase – each sensor node chooses a random number between 0 and 1 – If this random number is less than the threshold T(n), the sensor node is a cluster-head.

Low-energy adaptive clustering hierarchy (LEACH) – Set-up phase • The cluster-heads advertise to all sensor nodes in the network • The sensor nodes inform the appropriate cluster-heads that they will be a member of the cluster. (base on signal strength) • Afterwards, the cluster-heads assign the time on which the sensor nodes can send data to the cluster-heads based on a TDMA approach.

Low-energy adaptive clustering hierarchy (LEACH) – Steady phase • the sensor nodes can begin sensing and transmitting data to the cluster-heads. • The cluster-heads also aggregate data from the nodes in their cluster before sending these data to the base station. – After a certain period of time spent on the steady phase, the network • goes into the set-up phase again and • enters into another round of selecting the clusterheads.

“Me Head !!!” “I am with you” (CSMA-MAC) • Advertisement Cluster Set up Phase Every node chooses a random number (R) and compute a After decide which cluster it To reduce energy consumption nonthreshold T(n). joins, each node informs the T(n) = P/(1 -P*(r mod(1/p)) if n element of G, cluster-head nodes: cluster-head Based on the number of nodes in the 0 else • Use=minimal amount of energy cluster, the cluster-head node creates P – desired percentage of cluster heads (e. g. 5%) chosen based on the strength of the a TDMA schedule telling each node r – the current round cluster-head advertisement. G – set of nodes that have not been cluster head in the last 1/P rounds when it can transmit. • It elects Canitself turn as offa the radio until their cluster-head if R < T(n) This schedule is broadcast back to the allocated transmission time. in the cluster. Every cluster-head broadcast an advertisement nodes message, • • • with the “Here’s your time slot” “Thanks for same the transmit energy. time slot, Here’s • Non-cluster-head node decide which cluster it joins in this my data” round based on the received signal stregth. Schedule Data (TDMA) Creation • Largest. Transmission strength closet minimal enery needed for communication. Phase Modified from http: //faculty. cs. tamu. edu/dzsong/teaching/fall 2004/netbot/John_G. ppt

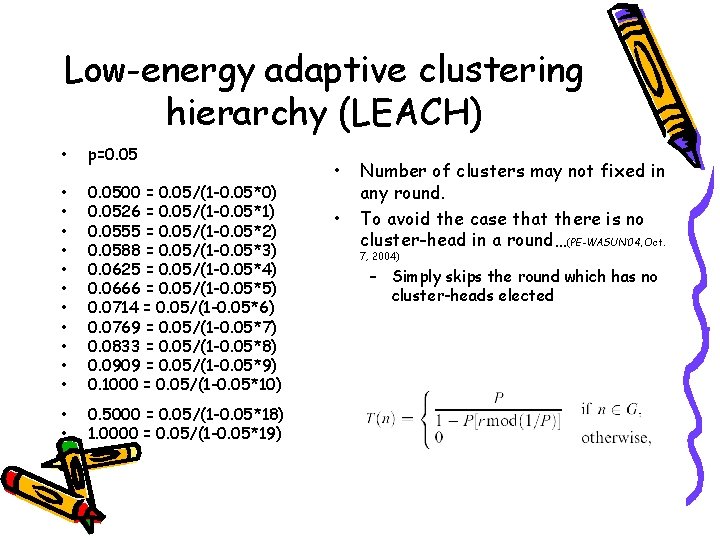
Low-energy adaptive clustering hierarchy (LEACH) • p=0. 05 • • • 0. 0500 = 0. 05/(1 -0. 05*0) 0. 0526 = 0. 05/(1 -0. 05*1) 0. 0555 = 0. 05/(1 -0. 05*2) 0. 0588 = 0. 05/(1 -0. 05*3) 0. 0625 = 0. 05/(1 -0. 05*4) 0. 0666 = 0. 05/(1 -0. 05*5) 0. 0714 = 0. 05/(1 -0. 05*6) 0. 0769 = 0. 05/(1 -0. 05*7) 0. 0833 = 0. 05/(1 -0. 05*8) 0. 0909 = 0. 05/(1 -0. 05*9) 0. 1000 = 0. 05/(1 -0. 05*10) • • 0. 5000 = 0. 05/(1 -0. 05*18) 1. 0000 = 0. 05/(1 -0. 05*19) • • Number of clusters may not fixed in any round. To avoid the case that there is no cluster-head in a round…(PE-WASUN’ 04, Oct. 7, 2004) – Simply skips the round which has no cluster-heads elected

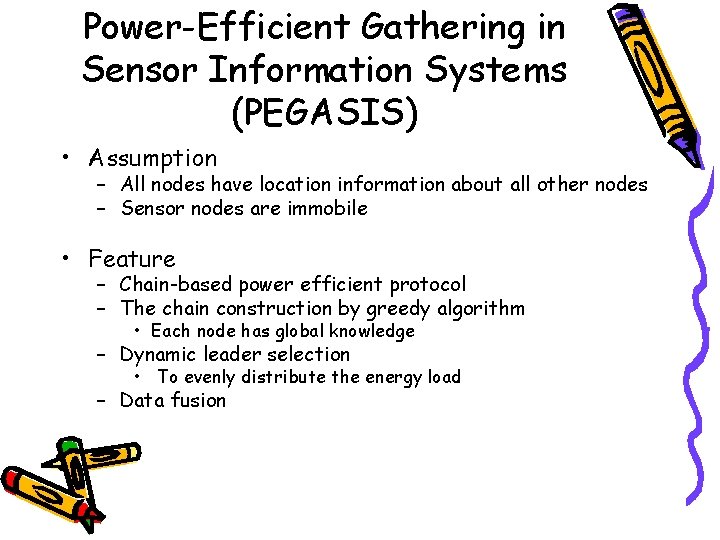
Power-Efficient Gathering in Sensor Information Systems (PEGASIS) • Assumption – All nodes have location information about all other nodes – Sensor nodes are immobile • Feature – Chain-based power efficient protocol – The chain construction by greedy algorithm • Each node has global knowledge – Dynamic leader selection • To evenly distribute the energy load – Data fusion

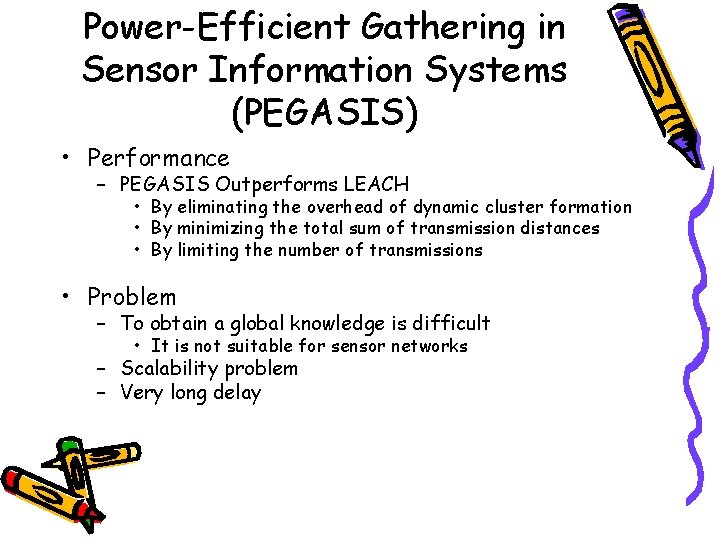
Power-Efficient Gathering in Sensor Information Systems (PEGASIS) • Performance – PEGASIS Outperforms LEACH • By eliminating the overhead of dynamic cluster formation • By minimizing the total sum of transmission distances • By limiting the number of transmissions • Problem – To obtain a global knowledge is difficult • It is not suitable for sensor networks – Scalability problem – Very long delay

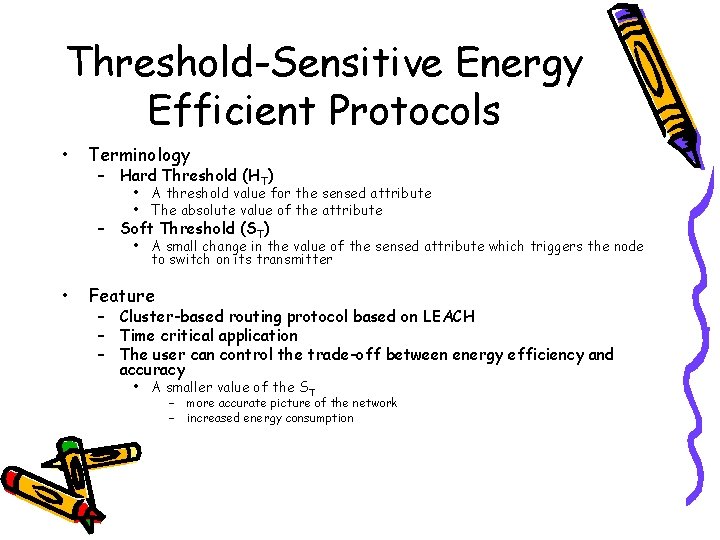
Threshold-Sensitive Energy Efficient Protocols • Terminology – Hard Threshold (HT) • A threshold value for the sensed attribute • The absolute value of the attribute – Soft Threshold (ST) • A small change in the value of the sensed attribute which triggers the node to switch on its transmitter • Feature – Cluster-based routing protocol based on LEACH – Time critical application – The user can control the trade-off between energy efficiency and accuracy • A smaller value of the ST – more accurate picture of the network – increased energy consumption

Threshold-Sensitive Energy Efficient Protocols • Basic scheme – A gain of sensing value – Decision whether to report it or not • Based on the values of HT and ST – Data are reported only • When the sensed value exceeds HT • When the value’s change is bigger than ST • Drawback – Cannot allocate the time slot • Each node turn on its transmitter all the time – Cannot distinguish a node which does not sense a “big” change from a dead or failed node – Collision occurrence in the cluster

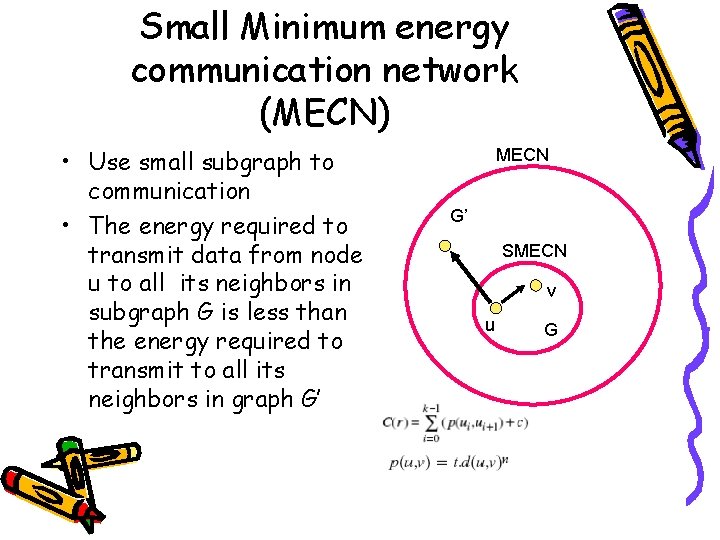
Small Minimum energy communication network (MECN) • Use small subgraph to communication • The energy required to transmit data from node u to all its neighbors in subgraph G is less than the energy required to transmit to all its neighbors in graph G’ MECN G’ SMECN v u G

Self-organizing protocol (SOP) • To build architecture to support heterogeneous sensor • SOP – Discovery Phase: discovery neighbors – Organization Phase: organize a hierarchy which is height balanced – Maintenance Phase: keep track alive and routing table – Self-Reorganization Phase: when group partitions or node failures

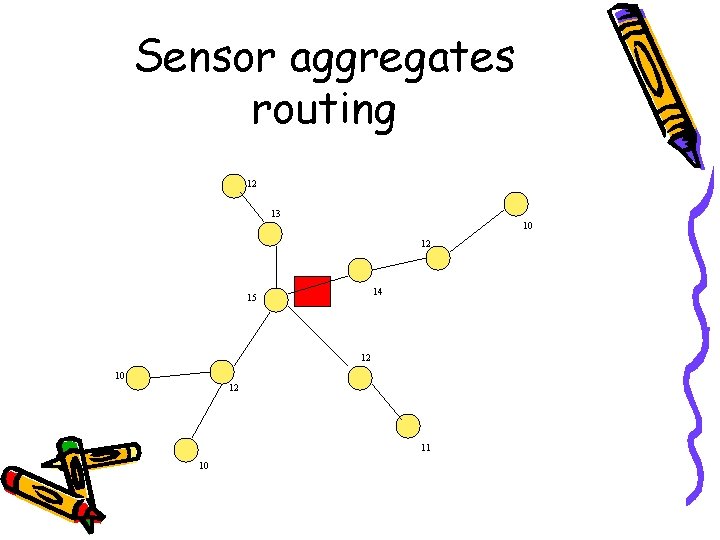
Sensor aggregates routing • The objective: – To collectively monitor target activity in a certain environment (target tracking applications) • Sensors are divided into clusters according to their sensed signal strength – To elect a leader, information exchanges between neighboring sensors • Three algs: DAM, EBAM, EMLAM

Sensor aggregates routing

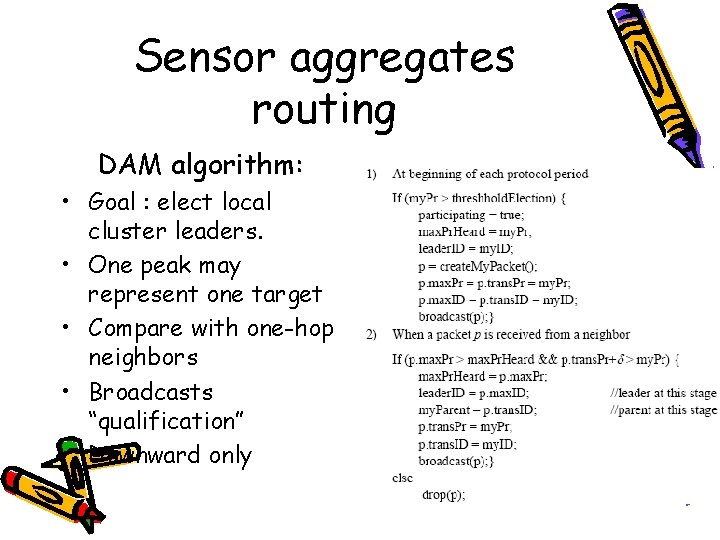
Sensor aggregates routing DAM algorithm: • Goal : elect local cluster leaders. • One peak may represent one target • Compare with one-hop neighbors • Broadcasts “qualification” • Downward only

Sensor aggregates routing 12 13 10 12 14 15 12 10 12 11 10

Sensor aggregates routing EBAM algorithm: • Provides a solution to count a targets within each sensor cluster • Consider the energy level of target signal sources • The energy level is estimated by computing the signal impact area, combining a weighted form of the detected target energy at each “impacted” sensor. • To convert the energy level into the corresponding target density: – assume roughly constant source energy output for the targets.

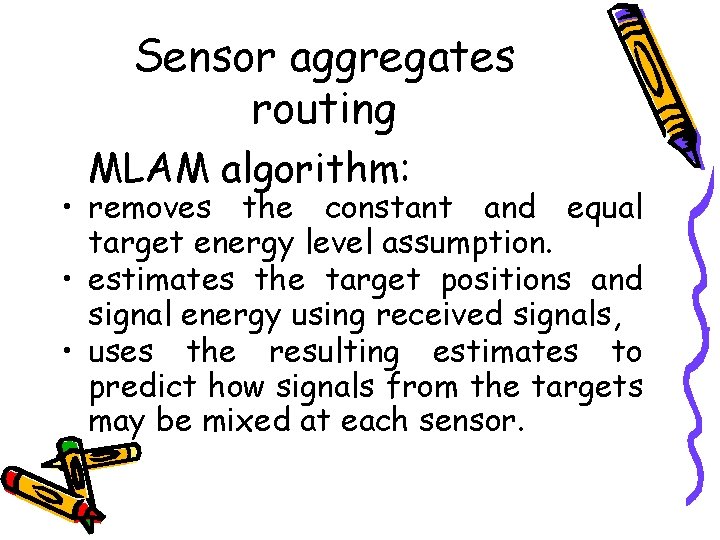
Sensor aggregates routing MLAM algorithm: • removes the constant and equal target energy level assumption. • estimates the target positions and signal energy using received signals, • uses the resulting estimates to predict how signals from the targets may be mixed at each sensor.

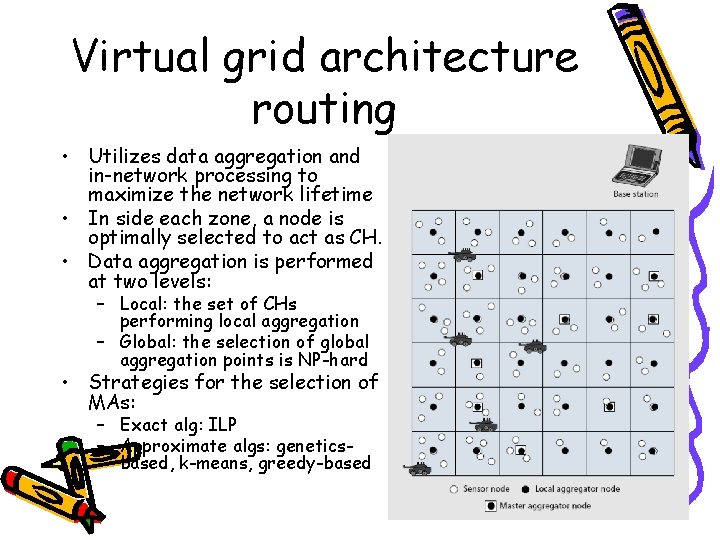
Virtual grid architecture routing • Utilizes data aggregation and in-network processing to maximize the network lifetime • In side each zone, a node is optimally selected to act as CH. • Data aggregation is performed at two levels: – Local: the set of CHs performing local aggregation – Global: the selection of global aggregation points is NP-hard • Strategies for the selection of MAs: – Exact alg: ILP – Approximate algs: geneticsbased, k-means, greedy-based

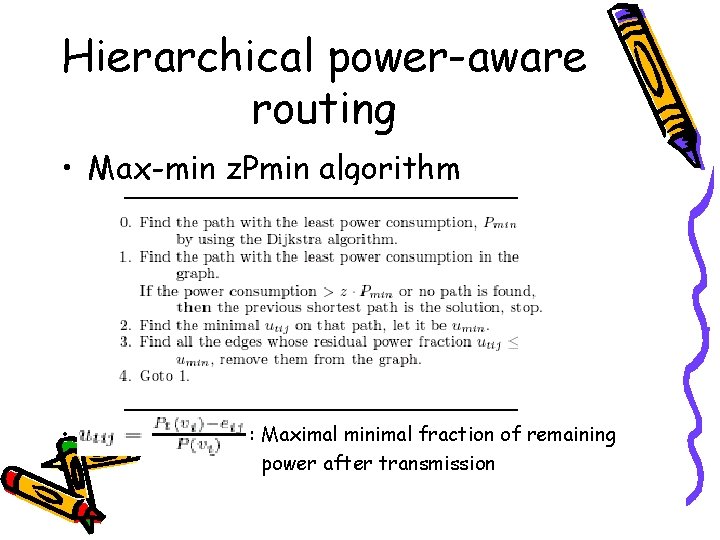
Hierarchical power-aware routing • Goal – To optimize the lifetime of the network. We develop an approximation algorithm called max-min z. Pmin. – To ensure scalability, we introduce a hierarchical algorithm, which is called zone-based routing

Hierarchical power-aware routing • Max-min z. Pmin algorithm • • : Maximal minimal fraction of remaining power after transmission

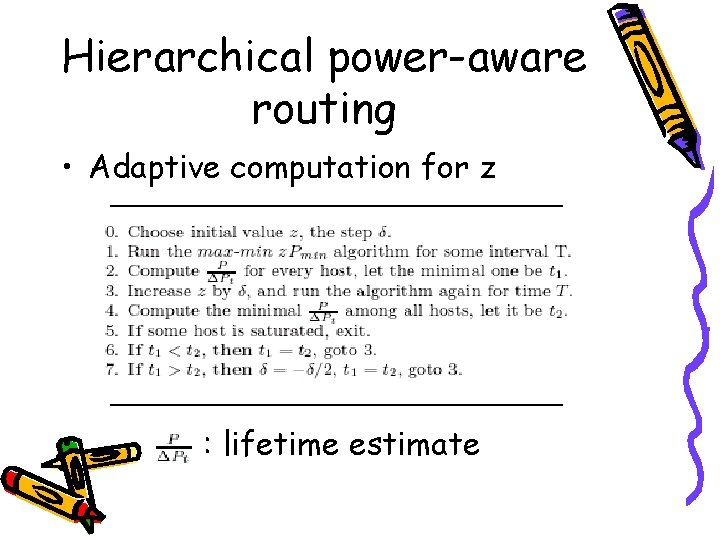
Hierarchical power-aware routing • Adaptive computation for z • : lifetime estimate

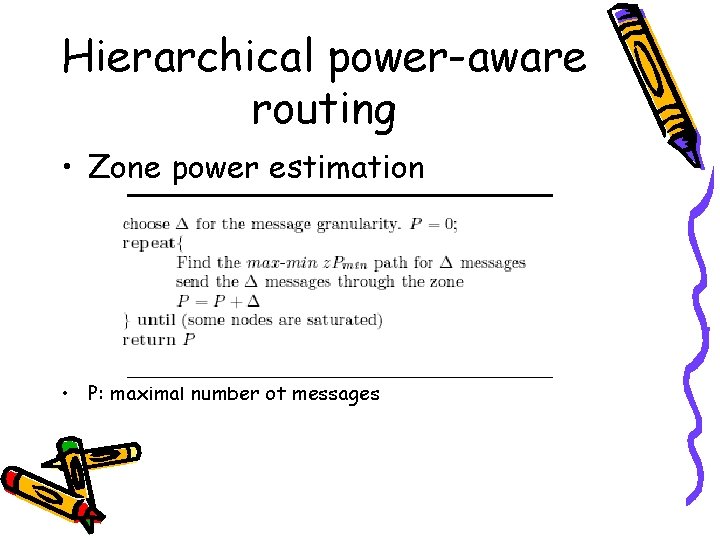
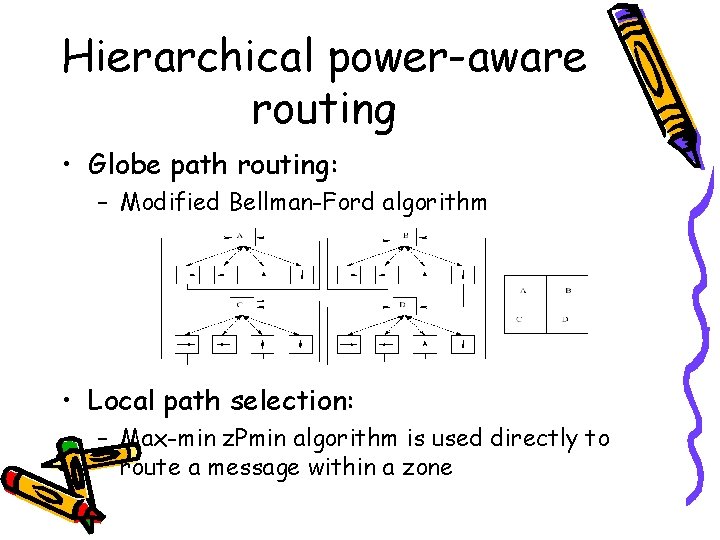
Hierarchical power-aware routing • Max-min z. Pmin: requires accurate power level information for all nodes • Zone-based: a hierarchical approach – Zone power estimation – Routing across zones (Globe path routing) – Routing within each zone (local path selection)

Hierarchical power-aware routing • Zone power estimation • P: maximal number of messages

Hierarchical power-aware routing • Globe path routing: – Modified Bellman-Ford algorithm • Local path selection: – Max-min z. Pmin algorithm is used directly to route a message within a zone

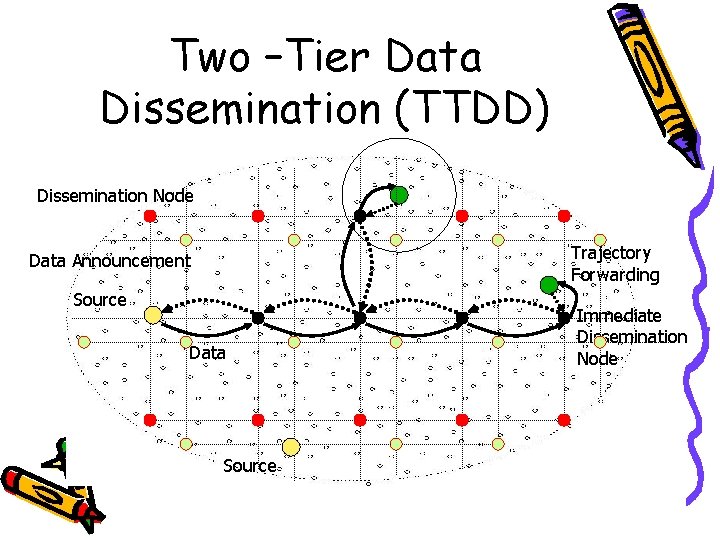
Two –Tier Data Dissemination (TTDD) Excessive Power Consumption Increased Wireless Transmission Collisions State Maintenance Overhead

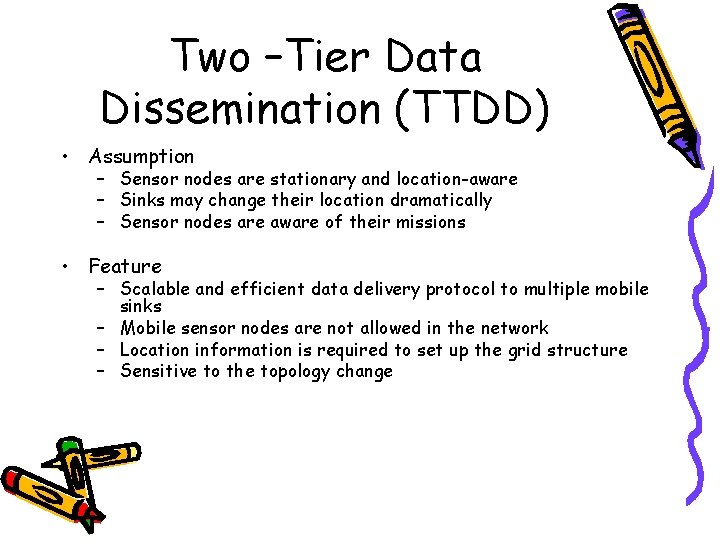
Two –Tier Data Dissemination (TTDD) • Assumption – Sensor nodes are stationary and location-aware – Sinks may change their location dramatically – Sensor nodes are aware of their missions • Feature – Scalable and efficient data delivery protocol to multiple mobile sinks – Mobile sensor nodes are not allowed in the network – Location information is required to set up the grid structure – Sensitive to the topology change

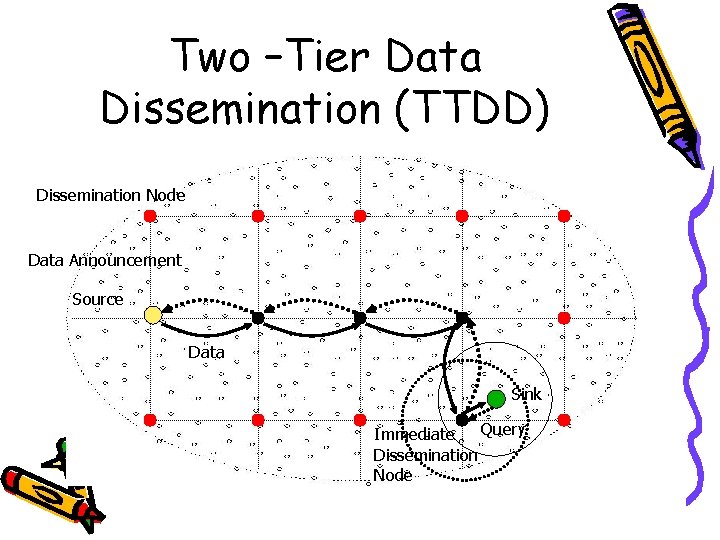
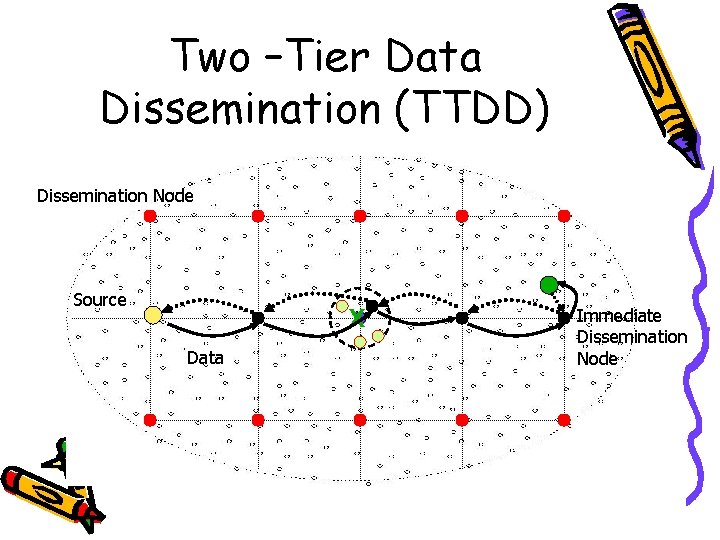
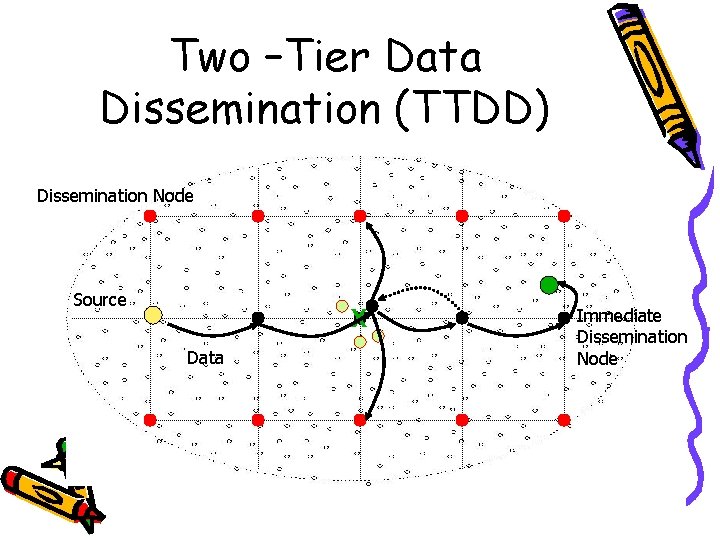
Two –Tier Data Dissemination (TTDD) Dissemination Node Data Announcement Source Data Sink Query Immediate Dissemination Node

Two –Tier Data Dissemination (TTDD) Dissemination Node Trajectory Forwarding Data Announcement Source Data Source Immediate Dissemination Node

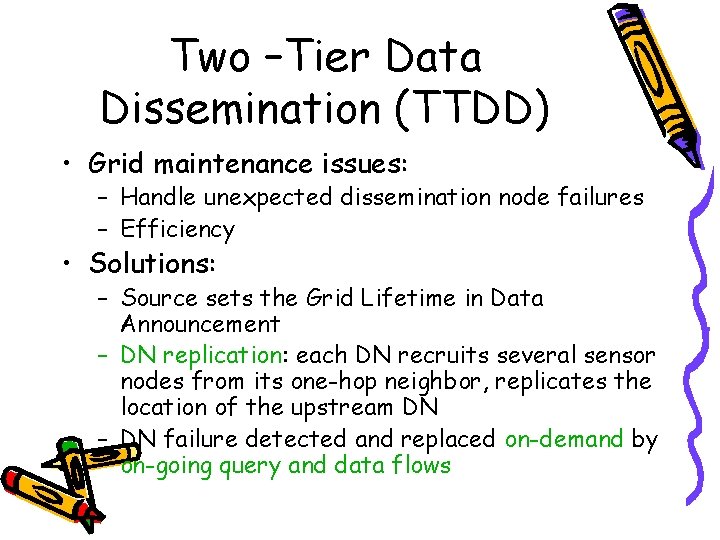
Two –Tier Data Dissemination (TTDD) • Grid maintenance issues: – Handle unexpected dissemination node failures – Efficiency • Solutions: – Source sets the Grid Lifetime in Data Announcement – DN replication: each DN recruits several sensor nodes from its one-hop neighbor, replicates the location of the upstream DN – DN failure detected and replaced on-demand by on-going query and data flows

Two –Tier Data Dissemination (TTDD) Dissemination Node Source X Data Immediate Dissemination Node

Two –Tier Data Dissemination (TTDD) Dissemination Node Source X Data Immediate Dissemination Node

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical vs. Flat Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

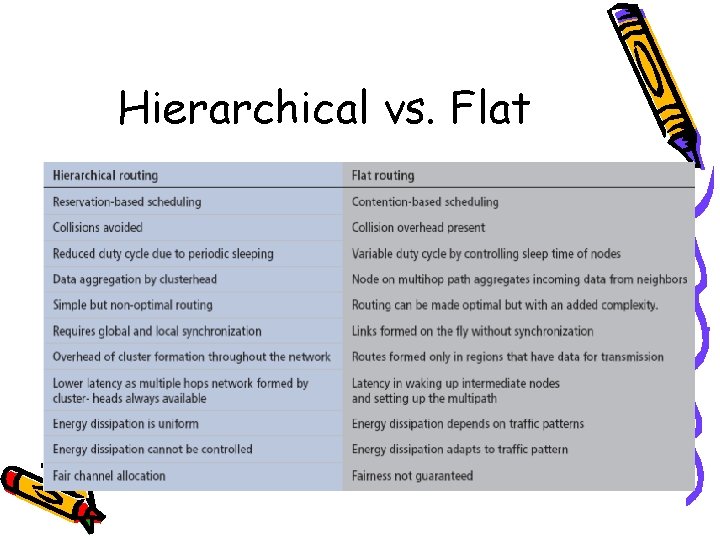
Hierarchical vs. Flat

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Location-Based Routing Protocols • Nodes’ positions are exploited to route data – Sensor nodes are addressed by means of their locations – Distance can be estimated on the basis of incoming signal strengths • Protocols: – – – Geographic Adaptive Fidelity Geographic and Energy Aware Routing MFR, DIR and GEDIR The Greedy Other Adaptive Face Routing SPAN

Geographic Adaptive Fidelity • Core idea – Turn off a node if it is equivalent from a routing perspective – Adaptively adjust routing fidelity use node deployment density • What’s fidelity – Uninterrupted connectivity between communicating nodes

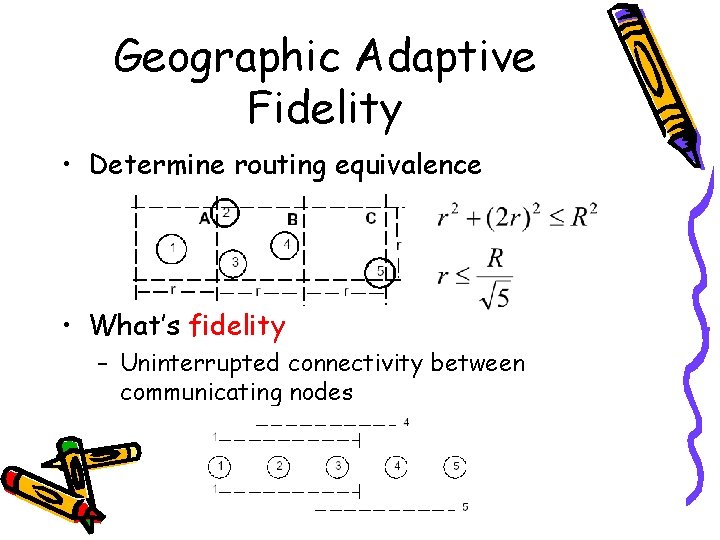
Geographic Adaptive Fidelity • Determine routing equivalence • What’s fidelity – Uninterrupted connectivity between communicating nodes

Geographic Adaptive Fidelity • Use GPS information to decide virtual grid ID • 3 -state transition – Discovery (Td) – Active (Ta) – Sleep (Ts) • Node ranking – Active node wins – High energy node wins • Adapting to mobility – With GPS information

Geographic and Energy Aware Routing • Motivation: – Reduce overhead of interest and low rate data flooding in directed diffusion • Basic ideas: – Leverage geographical information to restrict flooding, and recursively disseminate data inside the target region. – Extend overall network lifetime using local techniques to balance energy usage – Reuse routing information across multiple user queries.

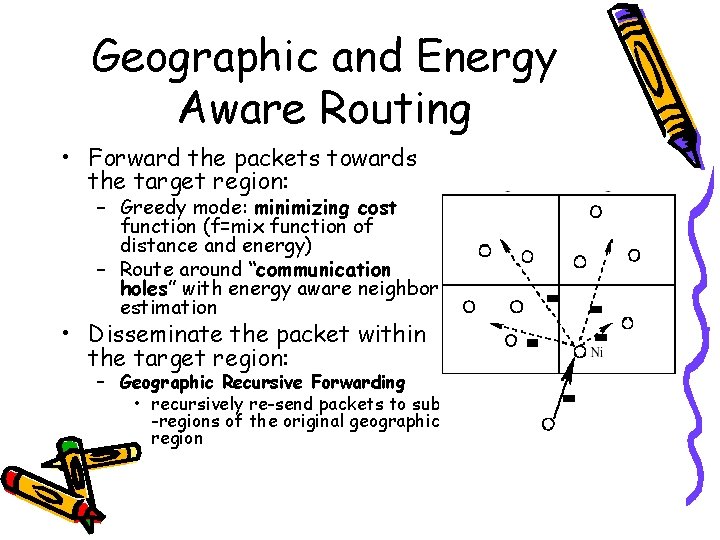
Geographic and Energy Aware Routing • Forward the packets towards the target region: – Greedy mode: minimizing cost function (f=mix function of distance and energy) – Route around “communication holes” with energy aware neighbor estimation • Disseminate the packet within the target region: – Geographic Recursive Forwarding • recursively re-send packets to sub -regions of the original geographic region

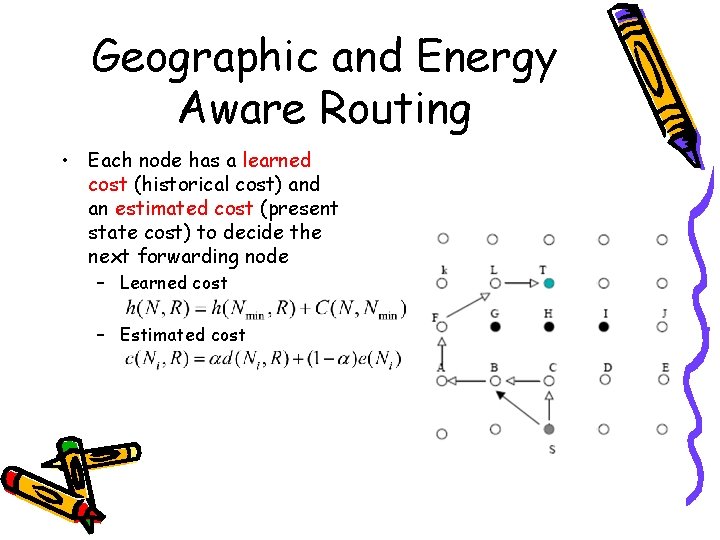
Geographic and Energy Aware Routing • Each node has a learned cost (historical cost) and an estimated cost (present state cost) to decide the next forwarding node – Learned cost – Estimated cost

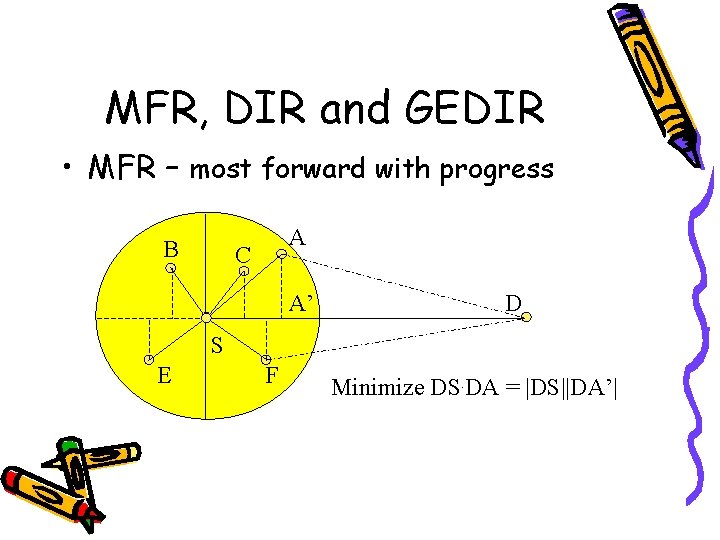
MFR, DIR and GEDIR • MFR – most forward with progress B A C A’ D S E F Minimize DS. DA = |DS||DA’|

MFR, DIR and GEDIR • DIR – best direction S A D Closest direction

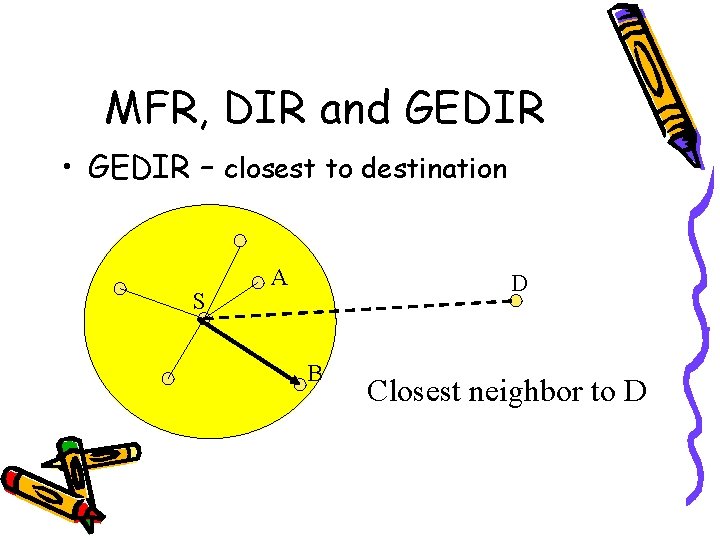
MFR, DIR and GEDIR • GEDIR – closest to destination S A D B Closest neighbor to D

MFR, DIR and GEDIR • MFR vs GEDIR B A S D A’ B’ may choose different node choice is same most of time! GEDIR wins in power efficiency AD<BD

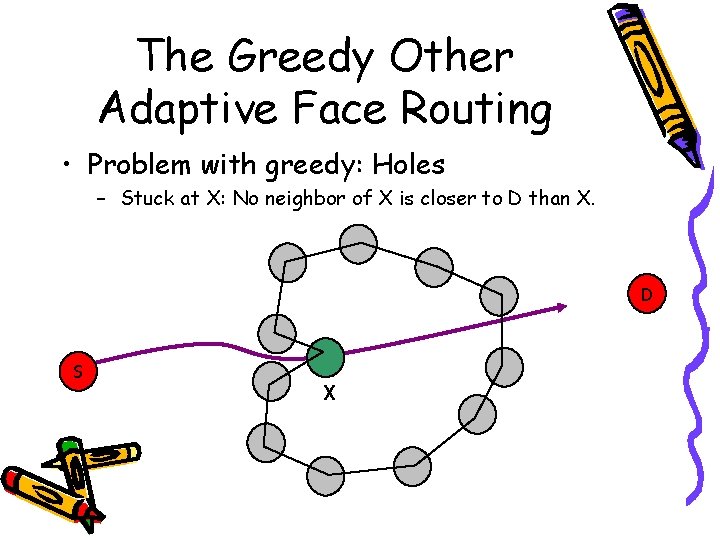
The Greedy Other Adaptive Face Routing • Problem with greedy: Holes – Stuck at X: No neighbor of X is closer to D than X. D S X

The Greedy Other Adaptive Face Routing a) b) Route through the sequence of faces that intersect the line segment [S, D]. Go around each face. Switch to the next face at a common edge. D S

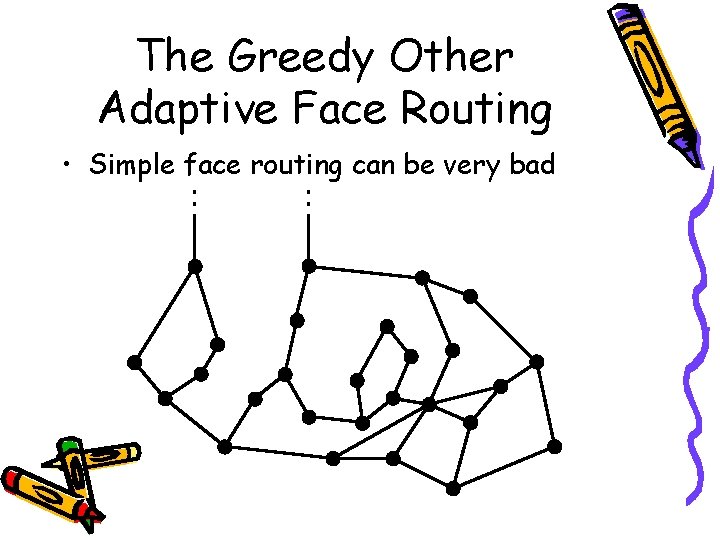
The Greedy Other Adaptive Face Routing • Simple face routing can be very bad

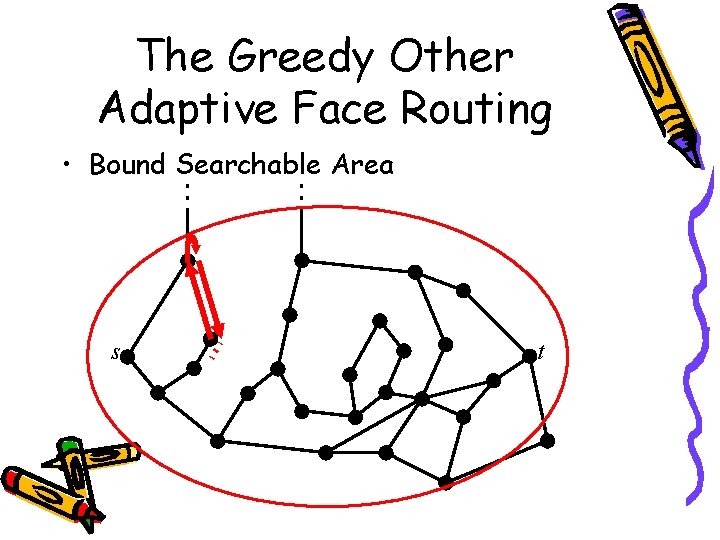
The Greedy Other Adaptive Face Routing • Bound Searchable Area s t

The Greedy Other Adaptive Face Routing • What is the correct size of the bounding area? – Start with a small searchable area – Grow area each time you cannot reach the destination – In other words, adapt area size whenever it is too small • → Adaptive Face Routing AFR

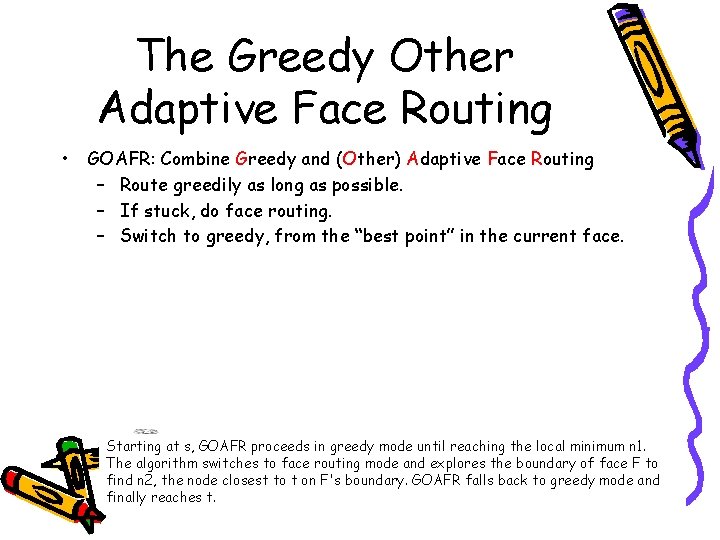
The Greedy Other Adaptive Face Routing • GOAFR: Combine Greedy and (Other) Adaptive Face Routing – Route greedily as long as possible. – If stuck, do face routing. – Switch to greedy, from the “best point” in the current face. Starting at s, GOAFR proceeds in greedy mode until reaching the local minimum n 1. The algorithm switches to face routing mode and explores the boundary of face F to find n 2, the node closest to t on F's boundary. GOAFR falls back to greedy mode and finally reaches t.

SPAN • Goal – Turn off nodes without significantly diminishing the capacity or connectivity of the network • Core concept – Coordinator – Forwarding backbone – Non-coordinator

SPAN • Rule 1: periodically broadcasts HELLO message – Current Status (coordinator or not) – Current coordinator – Current neighbors • Rule 2: coordinator announcement – A node decides to volunteer to be a coordinator if it discovers that two of its neighbors cannot communicate with each other directly or via one or two coordinators – Avoid coordinator contention: delayed announcement • Rule 3: coordinator withdrawal – If every pair of its neighbors can reach other either directly or via some other coordinators – To archive fairness, if one node has been a coordinator for some period of time and every pair of neighbor nodes can reach other via some other neighbors (even if they are not coordinators yet)

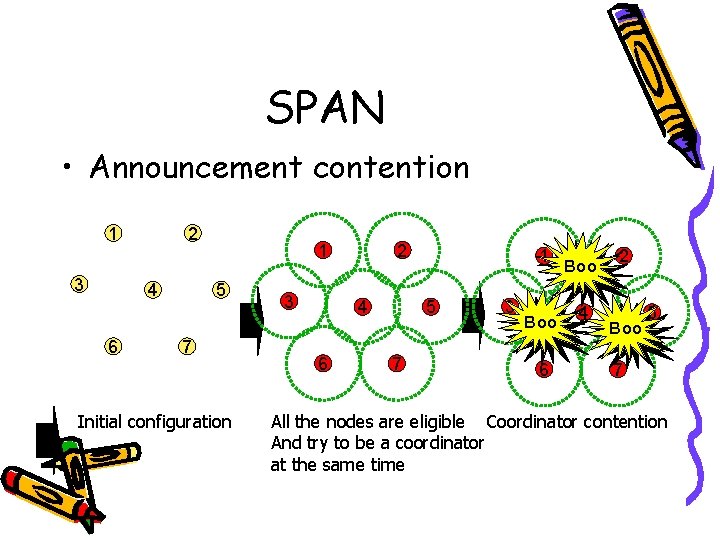
SPAN • Announcement contention 1 3 2 4 6 1 5 7 Initial configuration 3 2 4 6 1 5 7 3 Boo 6 Boo 4 2 Boo 5 7 All the nodes are eligible Coordinator contention And try to be a coordinator at the same time

SPAN • Resolving announcement contention using backoff utility 0<R<1

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Routing Protocols Based on Protocol Operation • • • Multipath Routing Protocols Query-Based Routing Negotiation-Based Routing Protocols Qo. S-based Routing Coherent and Noncoherent Processing

Multipath Routing Protocols • Use multiple paths in order to enhance network performance – – Fault tolerance Balance energy consumption Energy-efficient Reliability

Query-Based Routing • Destination nodes propagate a query for data • Usually theses queries are described in natural language or high-level query language • E. g. – Directed diffusion – Rumor routing protocol

Negotiation-Based Routing Protocols • Use high-level data descriptors in order to eliminate redundant data transmissions through negotiation • Communication decisions are also made based on the resources available to them • E. g. – SPIN

Qo. S-based Routing • Has to balance between energy consumption and data quality • E. g. – SPEED (congestion avoidance)

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Future Directions • • • (1/2) Qo. S Nodes mobility Exploit redundancy Tiered architectures Exploit spatial diversity and density of sensor nodes • Achieve desired global behavior with adaptive localized algorithms

Future Directions (2/2) • Leverage data processing inside the network and exploit computation near data sources to reduce communication • Time and location synchronization • Localization • Self-configuration and reconfiguration • Secure routing • Integration of sensor networks with wired networks

Outline • • • Introduction Challenges Design Issues Flat Routing Hierarchical Routing Flat vs. Hierarchical Location-based Routing Protocols Based on Protocol Operation Future Directions Conclusions

Conclusions • They have the common objective of trying to extend the lifetime of network • Trade-off energy and communication overhead • There are still many challenges that need to be solved

The End Thanks for Listening…