Review for Midterm Exam Accounting Information Systems Romney









- Slides: 15

Review for Midterm Exam Accounting Information Systems Romney and Steinbart Linda Batch February 2012

Learning Objectives – Course Outline • LO 1 - Demonstrate how an Accounting Information System satisfies key information needs and data quality requirements for each of the five core transactions processing cycles. Ch 1, Week 1 PP deck • LO – 2 Describe how ERP systems, e-business systems support business strategies for competitive advantage. Ch 2, Week 1 PP deck • LO – 3 Compare the Semantic Data Modeling approach to other file and database organization methodologies and use it to design a simple Access 2007 -2010 relational database. Ch 4, Ch 17, MS Access exercises for weeks 1 to week 5, Week 2 PP deck, Week 3 PP deck (REA) • LO – 4 Compose Data Flow diagrams. Ch 3 Week 2 PP deck,

Learning Objectives – Course Outline • LO – 5 Describe the circumstances and opportunities that give rise to computer fraud, common computer abuses and their classification, and, methods of detection and prevention. Ch 5, Ch 6, Week 4 and Week 5 PP decks • LO 6 - Outline the elements of an organization’s internal control system and risk management for IS. Ch 7 p. 182 – 195, Ch 4 p. 97 - 104, Week 6 PP deck

LO 1 & LO 2 • • Data vs Information Value of Information – cost vs. benefit Characteristics of Useful Information (table 1 -1 all) Business Processes – – Transaction processing – give get exchanges (p. 5) Five Major Business Processes (p. 7) Common cycle activities (table 1 -3) know 5 from each • Accounting Information Systems – – – Know the 6 components of an AIS (p. 10) Three important business functions of an AIS (p. 10) How does an AIS add value to an organization (p. 11) How does an AIS improve decision making (p. 12) AIS and corporate strategy (how does an AIS assist with corporate strategy) (p. 13) Role of the AIS in the value chain (p. 13 – 14) • Know your support activities vs primary activities

LO 1 & LO 2 • Transaction Processing (p. 26 and 27) – – – Data Input Data Processing Data Storage Information Output Common Business Activities and Source Documents (know a few) Source Data automation Turnaround documents Data storage (know what it is but do not go into the Ledgers and Chart of Accounts) Know what an audit trail is and why it matters (p. 31) Entity and Attributes (p. 31) Data processing (creating, reading, updating, deleting) (p. 33) Information output (documents, reports, queries) (p. 34) • ERP Systems (p. 36 and 37) – Typical modules (know at least 3) – Advantages (know at least 3) – Disadvantages (know at least 3)

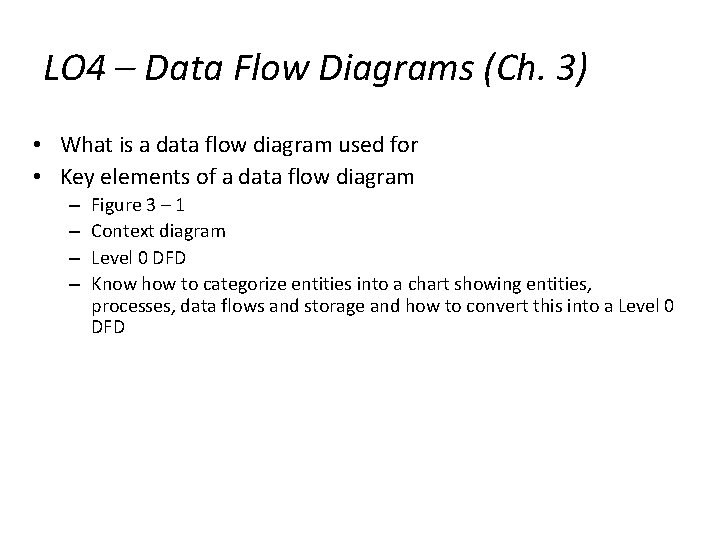
LO 4 – Data Flow Diagrams (Ch. 3) • What is a data flow diagram used for • Key elements of a data flow diagram – – Figure 3 – 1 Context diagram Level 0 DFD Know how to categorize entities into a chart showing entities, processes, data flows and storage and how to convert this into a Level 0 DFD

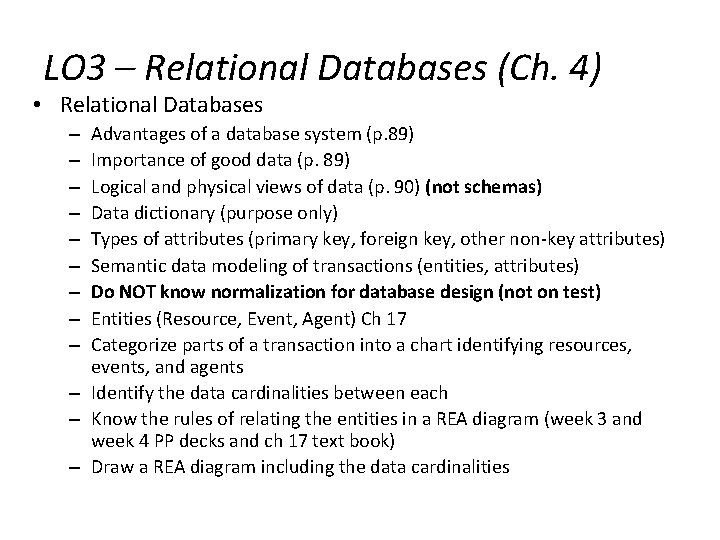
LO 3 – Relational Databases (Ch. 4) • Relational Databases Advantages of a database system (p. 89) Importance of good data (p. 89) Logical and physical views of data (p. 90) (not schemas) Data dictionary (purpose only) Types of attributes (primary key, foreign key, other non-key attributes) Semantic data modeling of transactions (entities, attributes) Do NOT know normalization for database design (not on test) Entities (Resource, Event, Agent) Ch 17 Categorize parts of a transaction into a chart identifying resources, events, and agents – Identify the data cardinalities between each – Know the rules of relating the entities in a REA diagram (week 3 and week 4 PP decks and ch 17 text book) – Draw a REA diagram including the data cardinalities – – – – –

LO 3 – Relational Databases (Ch. 4) • Relational Databases Continued – Based on the REA diagram, suggest tables to build in an access database • Week 5 in class exercise – Suggest attributes that should be in each table – Identify the data cardinalities and how the tables should be linked – Note: You will not be asked to build this, only design it

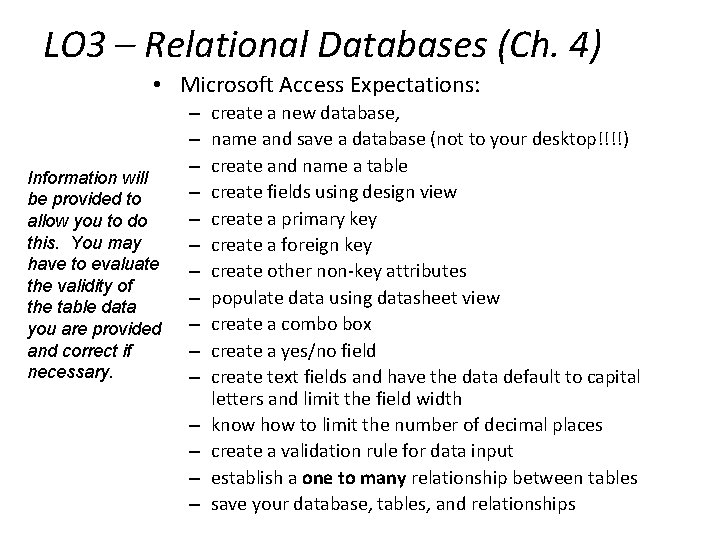
LO 3 – Relational Databases (Ch. 4) • Microsoft Access Expectations: Information will be provided to allow you to do this. You may have to evaluate the validity of the table data you are provided and correct if necessary. – – – – create a new database, name and save a database (not to your desktop!!!!) create and name a table create fields using design view create a primary key create a foreign key create other non-key attributes populate data using datasheet view create a combo box create a yes/no field create text fields and have the data default to capital letters and limit the field width know how to limit the number of decimal places create a validation rule for data input establish a one to many relationship between tables save your database, tables, and relationships

LO 5 – Computer Fraud and Abuse Techniques (ch 5 and 6) • Threats to accounting information systems (p. 122) • What is fraud and what are the five legal requirements for a fraud to have occurred (p. 123, 124) • Types of fraud – – – Misappropriation of assets Fraudulent financial reporting Which fraud is the biggest risk and why Who perpetuates fraud and why The fraud triangle – pressure, opportunity, rationalization • • Employee pressures Financial statement pressures Opportunities (commit, conceal, convert to personal gain) Rationalizations – What can be done to prevent fraud

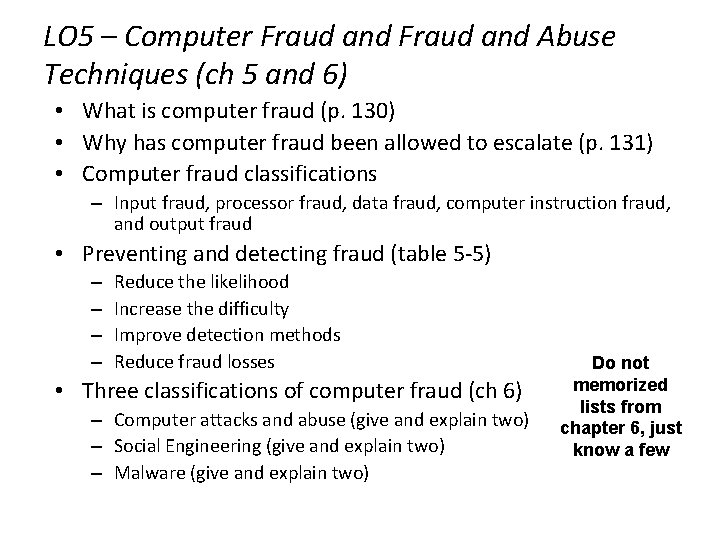
LO 5 – Computer Fraud and Abuse Techniques (ch 5 and 6) • What is computer fraud (p. 130) • Why has computer fraud been allowed to escalate (p. 131) • Computer fraud classifications – Input fraud, processor fraud, data fraud, computer instruction fraud, and output fraud • Preventing and detecting fraud (table 5 -5) – – Reduce the likelihood Increase the difficulty Improve detection methods Reduce fraud losses • Three classifications of computer fraud (ch 6) – Computer attacks and abuse (give and explain two) – Social Engineering (give and explain two) – Malware (give and explain two) Do not memorized lists from chapter 6, just know a few

LO 6 – Introduction to ERM and Internal Control (ch 7 and ch 4) • Criteria that is used when assessing whether controls are required – Threat or event, exposure or impact, likelihood or probability, • Overview of Control Concepts – Internal control – process implemented to provide reasonable assurance that control objectives are achieved (p. 184 and week 6 deck) • Know three control objectives – Internal control perform three functions – preventive controls, detective controls, corrective controls (p. 185) – General controls make an organizations control environment stable (relate to IT and infrastructure) (p. 185) – Applications Controls make sure transactions are processed properly (p. 185) • Sarbanes-Oxley Act (SOX) – Passed after large frauds caused the collapse of several large corporations (World. Com, Eron, Tyco, Xerox, and others) – Most important aspects of SOX (p. 186) • Know 3

LO 6 – Introduction to ERM and Internal Control (ch 7 and ch 4) • Three Major control frameworks – COBIT – Control Objectives for Information and Related Technology – COSO (IC) – Committee of Sponsoring Organizations Internal Control-Integrated framework is widely accepted as the authority on internal controls and there are five interrelated components of the framework • Control environment • Control activities • Risk assessment • Information and communication • Monitoring – Limitation of this framework is that it examines controls without looking at the purposes and risks of business processes and provides little context for evaluating the results, hard to know which controls are the most important, whether they adequately deal with risk, and whether important controls are missing

LO 6 – Introduction to ERM and Internal Control (ch 7 and ch 4) • Three Major control frameworks continued – COSO (ERM) Enterprise Risk Management Framework • Adds three more components to the COSO IC model • It is a risk based approach rather than a control based approach – Setting objectives – top and right side of cube – strategic, operating, reporting and compliance objectives are cascaded down through the organizational structure at all levels including entity level, division, business unit, and subsidiary levels. – Event identification – just know what this means – Risk assessment – probability of an event, impact of the event, inherent risk and residual risk – Risk response (reduce, accept, share, avoid) – Control activities (details are not on midterm) – Information and communication (details are not on midterm) – Monitoring (details are not on midterm) • Know about setting objectives (top and right side of cube p. 188) event identification (what is event identification) and risk assessment and response (p. 194 195)

Questions? • • • 3 hour exam Bring your computer Bring a ethernet cable Bring and pencils Give yourself the full 3 hours – – – Multiple Choice True False Select multiple correct answers Short Answer Microsoft Access • If anyone is entitled to an academic accomodation, please let me know so we can make arrangements.