ReverseEngineering MAC A noncooperative game model JangWon Lee



- Slides: 15

Reverse-Engineering MAC: A non-cooperative game model Jang-Won Lee, Ao Tang, Jianwei Huang, Mung Chiang, A. Robert Calderbank IEEE JSAC, 2007

Reverse engineering �Reverse engineering is the process of discovering the technological principles of a device, object, or system through analysis of its structure, function, and operation. �In this paper, by studying the current MAC protocol, they discover that the users are actually implicitly participating a non-cooperative game, with the utility function of each selfish user - a mathematical model to study the selfish behaviors in the current MAC protocol - much insights on protocol performance

Reverse engineering �In protocol layers - Layer 4: TCP/AQM - Layer 3: BGP - Layer 2: MAC �MAC protocols - scheduling-based (contention free): FDMA, TDMA, CDMA - random access (contention-based): Ethernet, slotted Aloha, 802. 11 DCF function >> Exponential Backoff (EB) protocol

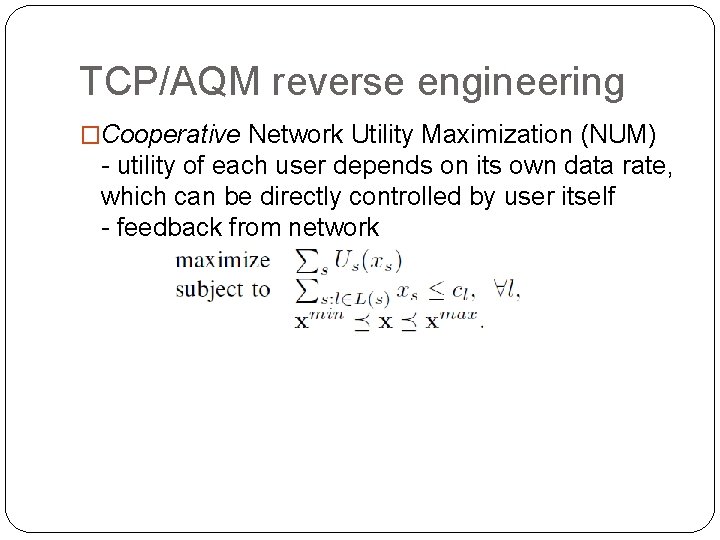
TCP/AQM reverse engineering �Cooperative Network Utility Maximization (NUM) - utility of each user depends on its own data rate, which can be directly controlled by user itself - feedback from network

EB protocol reverse engineering �The utility of each link in the EB protocol directly depends on not just its own transmission but also transmissions of other links due to collisions - cannot be controlled by the link itself �There is no explicit feedback from the network �Hence, in contrast to TCP reverse engineering, a non-cooperative game model is more appropriate for the EB protocol than a global optimization model

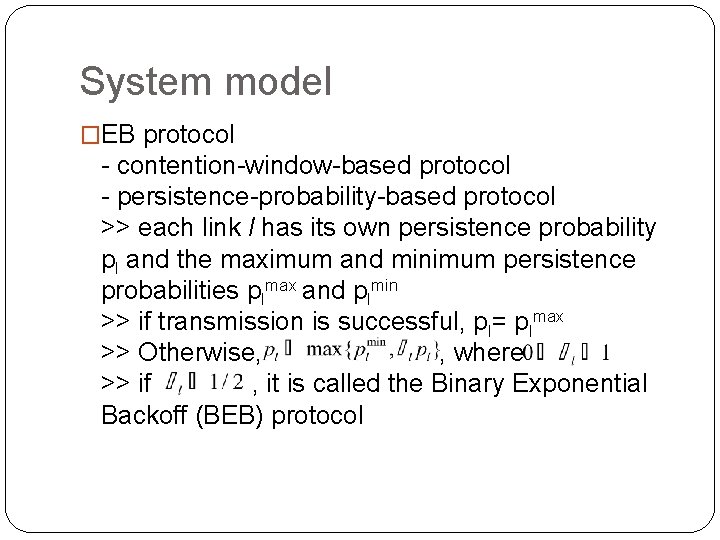
System model �EB protocol - contention-window-based protocol - persistence-probability-based protocol >> each link l has its own persistence probability pl and the maximum and minimum persistence probabilities plmax and plmin >> if transmission is successful, pl= plmax >> Otherwise, , where >> if , it is called the Binary Exponential Backoff (BEB) protocol

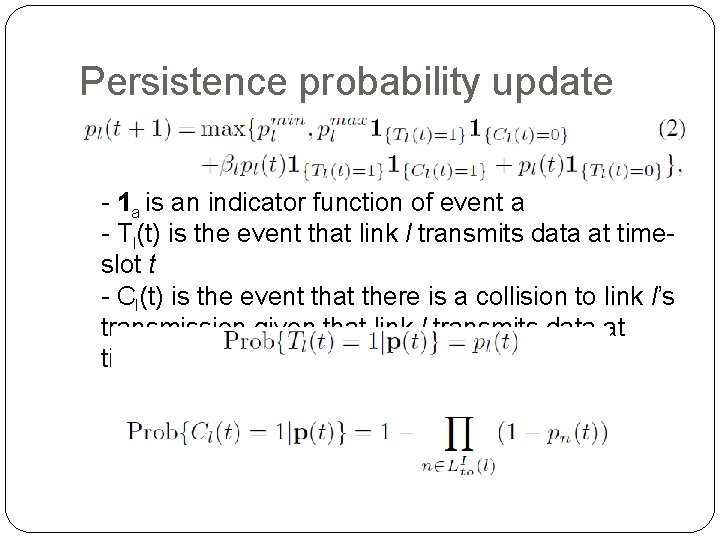
Persistence probability update � - 1 a is an indicator function of event a - Tl(t) is the event that link l transmits data at timeslot t - Cl(t) is the event that there is a collision to link l’s transmission given that link l transmits data at time-slot t

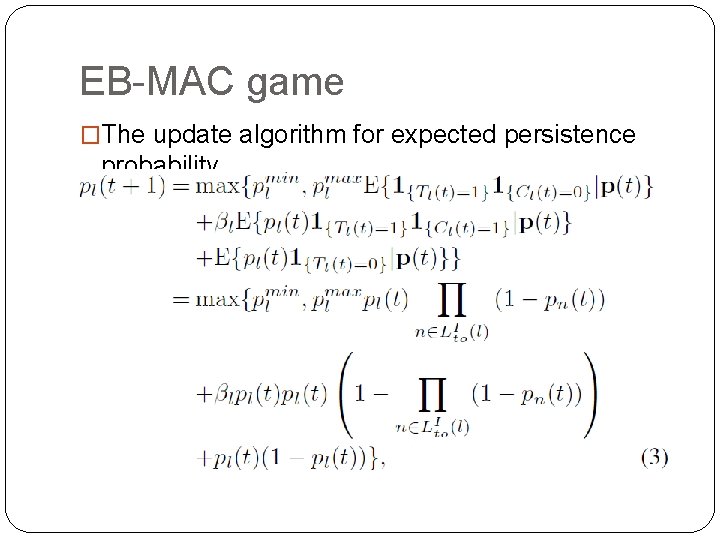
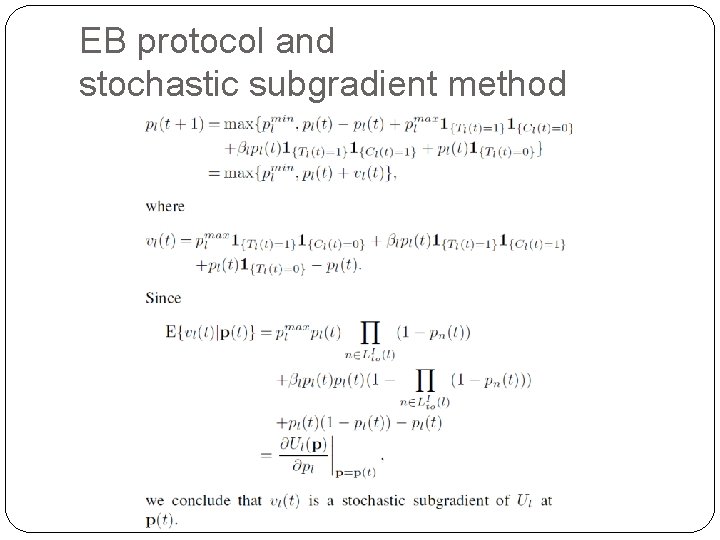
EB-MAC game �The update algorithm for expected persistence probability

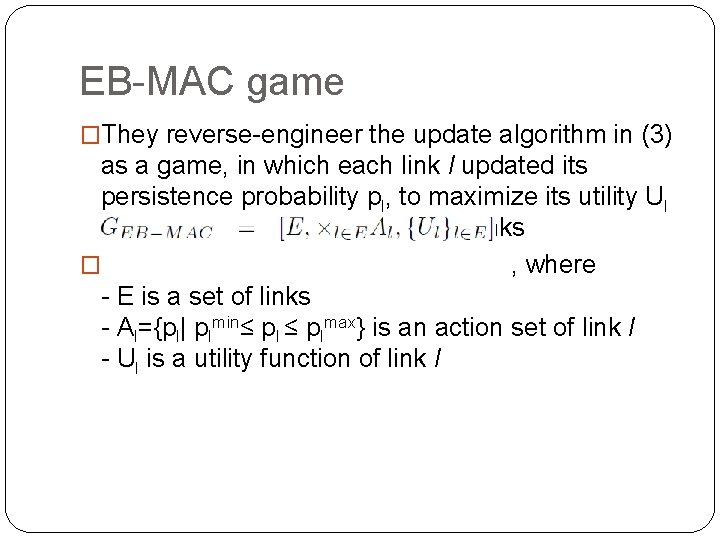
EB-MAC game �They reverse-engineer the update algorithm in (3) as a game, in which each link l updated its persistence probability pl, to maximize its utility Ul based on strategies of the other links � , where - E is a set of links - Al={pl| plmin≤ plmax} is an action set of link l - Ul is a utility function of link l

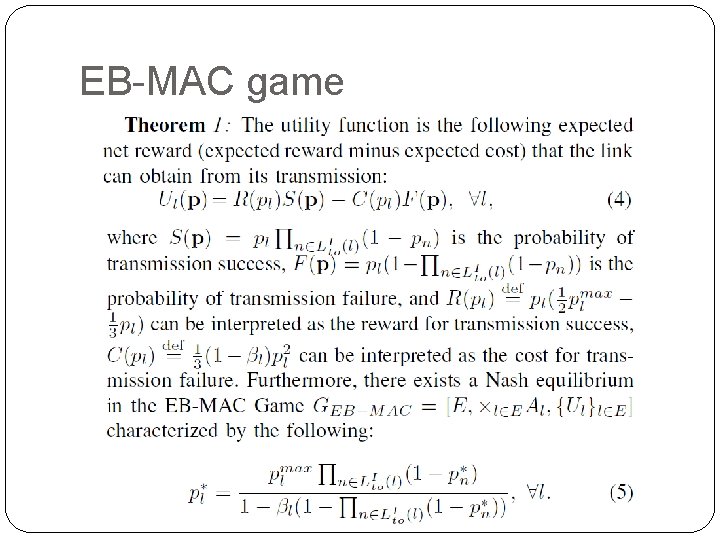
EB-MAC game

EB protocol and stochastic subgradient method

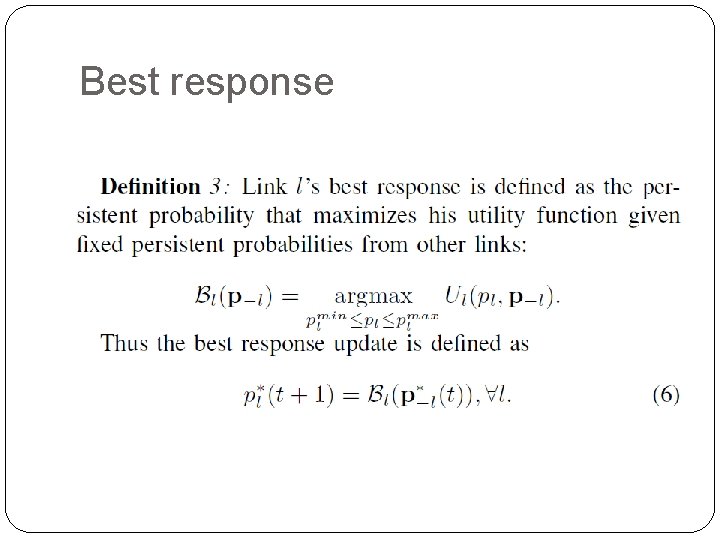
Best response

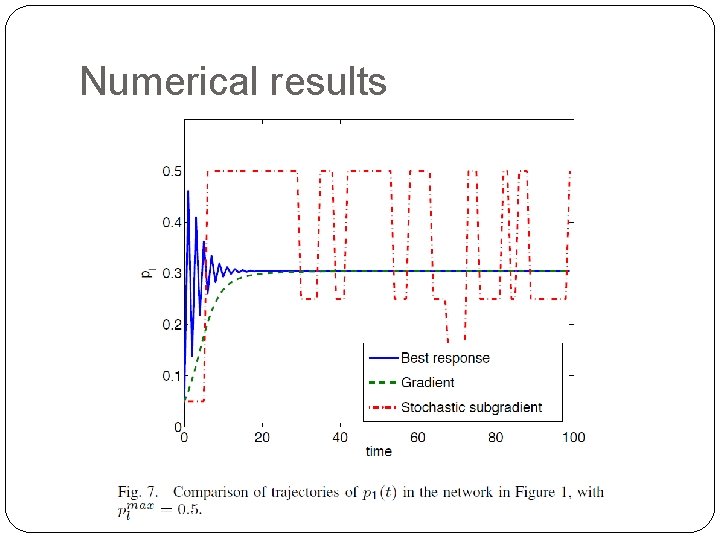
Numerical results

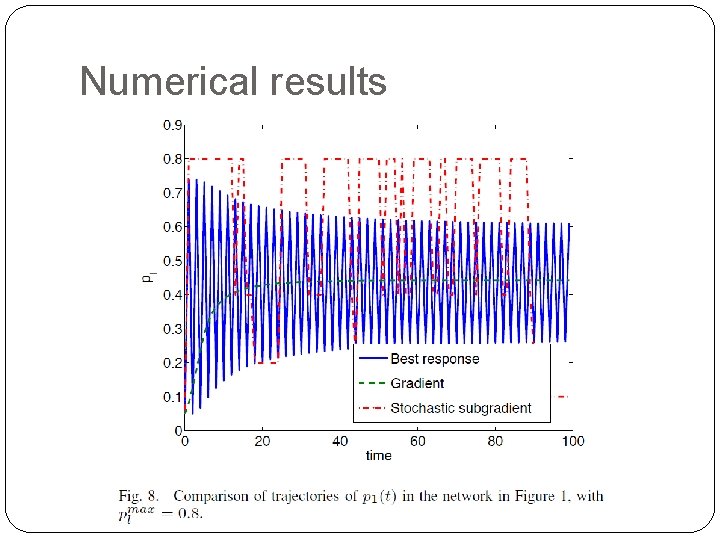
Numerical results

Conclusion �Reverse-engineered exponential-backoff random access protocols as a non-cooperative game model �Each link is implicitly maximizing a utility function in the form of net reward for successful transmission �Due to the lack of proper feedback mechanisms in the current EB protocols, such selfish, local actions are not aligned to maximize the networkwide total utility, nor are they guaranteed to converge, even though a Nash equilibrium for the MAC game always exists