Remote Name Mapping Linux NFSv 4 Andy Adamson





- Slides: 18

Remote Name Mapping Linux NFSv 4 Andy Adamson Center For Information Technology Integration University of Michigan

NFSv 4 Administrative Domain Multiple DNS domains Multiple Security Realms Kerberos, PKI Certificate Authorities (SPKM 3) NFSv 4 domain = unique UID/GID namespace Pick one DNS domain to be the NFSv 4 Domain Name <user@nfsv 4 domain> ACL 'who' and GETTATTR owner and owner_group

Local NFSv 4 Domain Name to ID One to one correspondence between UID and NFSv 4 domain name joe@arbitrary. domain. org GSS Principal name will differ from NFSv 4 domain name Kerberos V: joe@ARBITRARY. DOMAIN. ORG PKI: OU=US, OU=State, OU= Arbitrary Inc, CN = Joe User Email= joe@arbitrary. domain. org

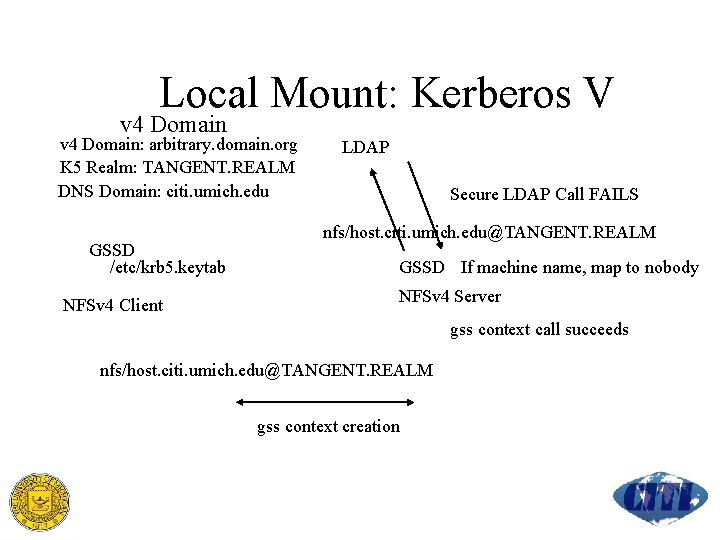
Local Mount: Kerberos V v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu GSSD /etc/krb 5. keytab NFSv 4 Client LDAP Secure LDAP Call FAILS nfs/host. citi. umich. edu@TANGENT. REALM GSSD If machine name, map to nobody NFSv 4 Server gss context call succeeds nfs/host. citi. umich. edu@TANGENT. REALM gss context creation

Local Mount: Kerberos V Issues Distribution of client keytabs Client service name UID/GID mapping for client machine principals? Related issue: Client root user Map to machine principal Map to root principal Map to nobody other

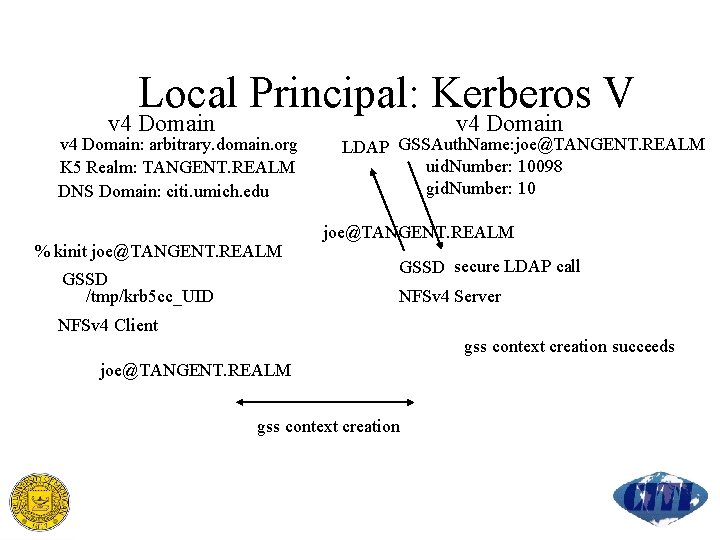
Local Principal: Kerberos V v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu % kinit joe@TANGENT. REALM GSSD /tmp/krb 5 cc_UID v 4 Domain LDAP GSSAuth. Name: joe@TANGENT. REALM uid. Number: 10098 gid. Number: 10 joe@TANGENT. REALM GSSD secure LDAP call NFSv 4 Server NFSv 4 Client gss context creation succeeds joe@TANGENT. REALM gss context creation

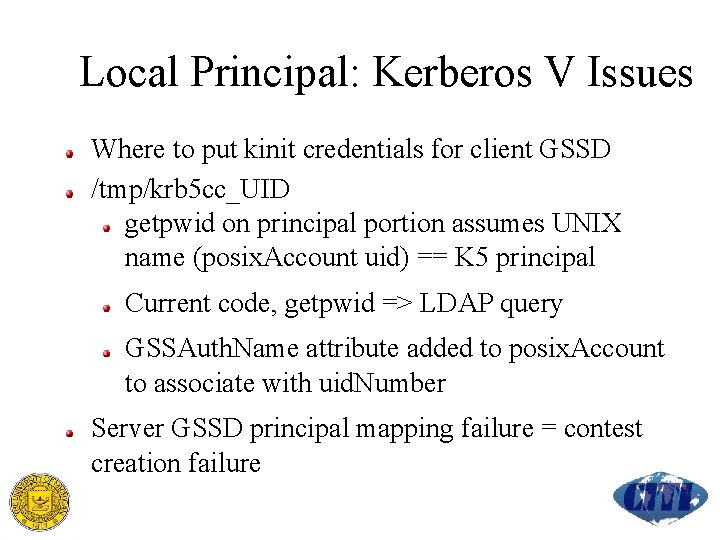
Local Principal: Kerberos V Issues Where to put kinit credentials for client GSSD /tmp/krb 5 cc_UID getpwid on principal portion assumes UNIX name (posix. Account uid) == K 5 principal Current code, getpwid => LDAP query GSSAuth. Name attribute added to posix. Account to associate with uid. Number Server GSSD principal mapping failure = contest creation failure

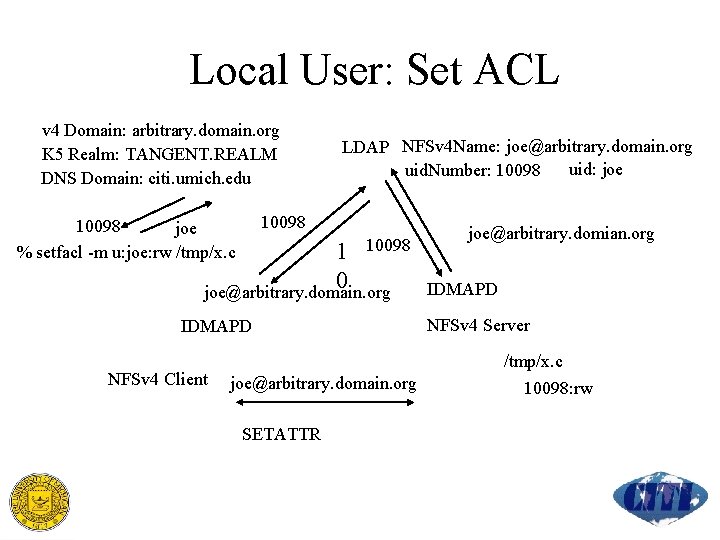
Local User: Set ACL v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu LDAP NFSv 4 Name: joe@arbitrary. domain. org uid: joe uid. Number: 10098 joe % setfacl -m u: joe: rw /tmp/x. c 10098 1 0 joe@arbitrary. domain. org IDMAPD NFSv 4 Client joe@arbitrary. domain. org SETATTR joe@arbitrary. domian. org IDMAPD NFSv 4 Server /tmp/x. c 10098: rw

Local User: Set ACL issues setfacl POSIX interface uses UID/GID across kernel boundary LDAP posix. Account: uid is mapped need a local name two name mapping calls LINUX nfs 4_setfacl interface passes string names across kernel boundary no local name needed

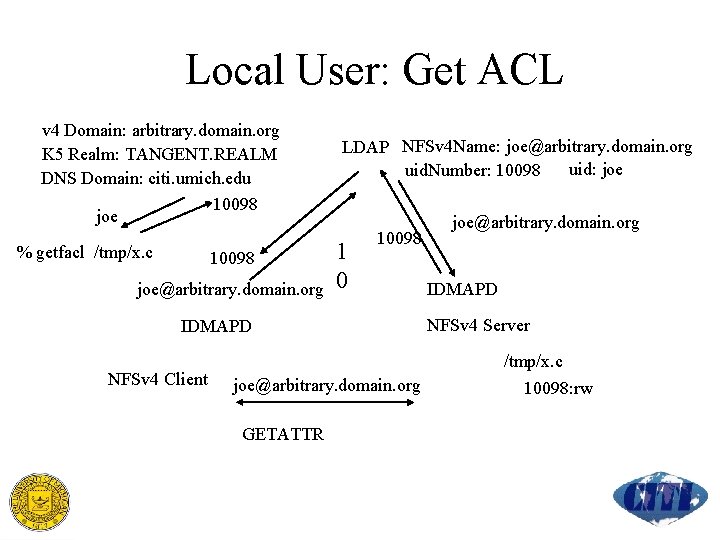
Local User: Get ACL v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu 10098 joe % getfacl /tmp/x. c 10098 joe@arbitrary. domain. org LDAP NFSv 4 Name: joe@arbitrary. domain. org uid: joe uid. Number: 10098 1 0 10098 IDMAPD NFSv 4 Client joe@arbitrary. domain. org GETATTR joe@arbitrary. domain. org IDMAPD NFSv 4 Server /tmp/x. c 10098: rw

Local User: Get ACL issues getfacl POSIX interface uses UID/GID across kernel boundary LDAP posix. Account: uid is displayed two name mapping calls LINUX nfs 4_getfacl interface passes string names across kernel boundary

Kerberos V X-Realm and Linux NFSv 4 X-realm GSS context initialization just works Need to add GSSAuth. Name and UID/GID mapping for remote user NFSv 4 Remote. User schema can be used instead of posix. Account NFSv 4 remote access without local machine access mount from remote machine: mapping library needs to recognize service portion of name Secure LDAP communication required

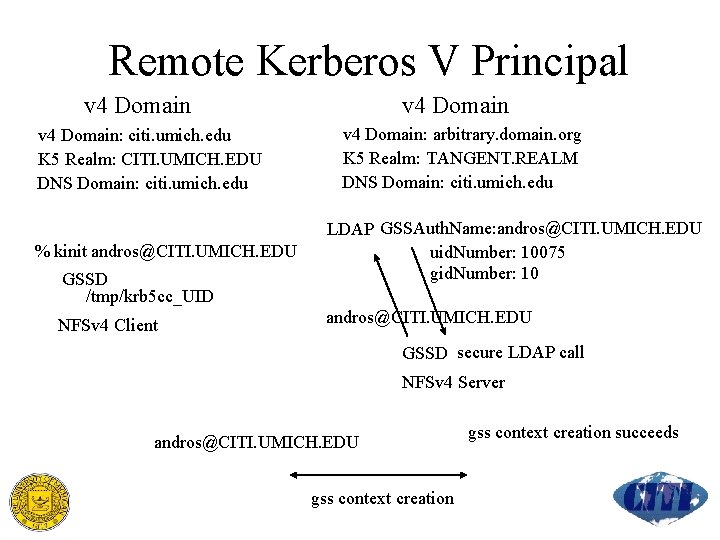
Remote Kerberos V Principal v 4 Domain: citi. umich. edu K 5 Realm: CITI. UMICH. EDU DNS Domain: citi. umich. edu % kinit andros@CITI. UMICH. EDU GSSD /tmp/krb 5 cc_UID NFSv 4 Client v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu LDAP GSSAuth. Name: andros@CITI. UMICH. EDU uid. Number: 10075 gid. Number: 10 andros@CITI. UMICH. EDU GSSD secure LDAP call NFSv 4 Server andros@CITI. UMICH. EDU gss context creation succeeds

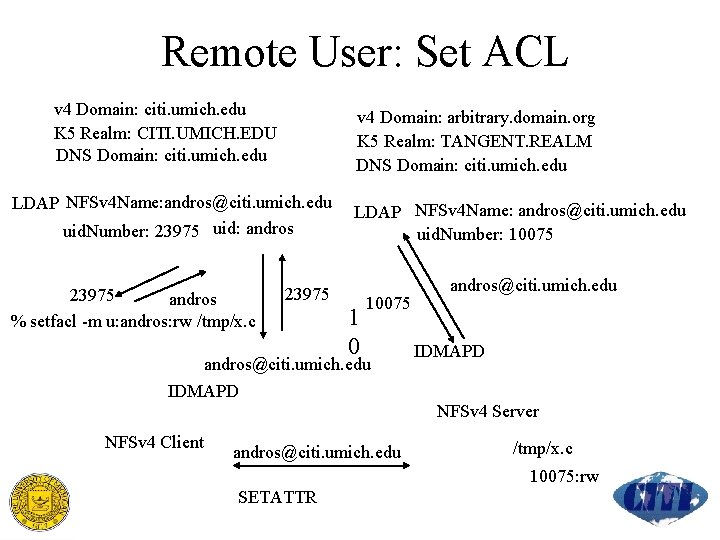
Remote User: Set ACL v 4 Domain: citi. umich. edu K 5 Realm: CITI. UMICH. EDU DNS Domain: citi. umich. edu v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu LDAP NFSv 4 Name: andros@citi. umich. edu uid. Number: 23975 uid: andros 23975 andros % setfacl -m u: andros: rw /tmp/x. c 23975 LDAP NFSv 4 Name: andros@citi. umich. edu uid. Number: 10075 1 0 10075 andros@citi. umich. edu IDMAPD NFSv 4 Server NFSv 4 Client andros@citi. umich. edu /tmp/x. c 10075: rw SETATTR

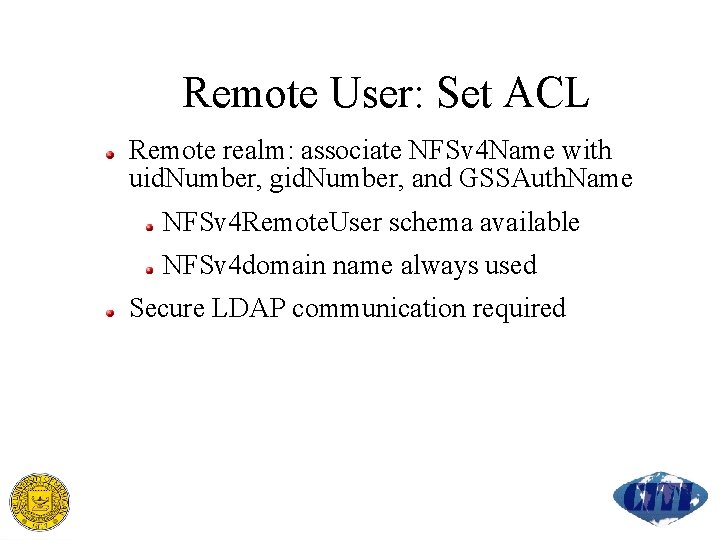
Remote User: Set ACL Remote realm: associate NFSv 4 Name with uid. Number, gid. Number, and GSSAuth. Name NFSv 4 Remote. User schema available NFSv 4 domain name always used Secure LDAP communication required

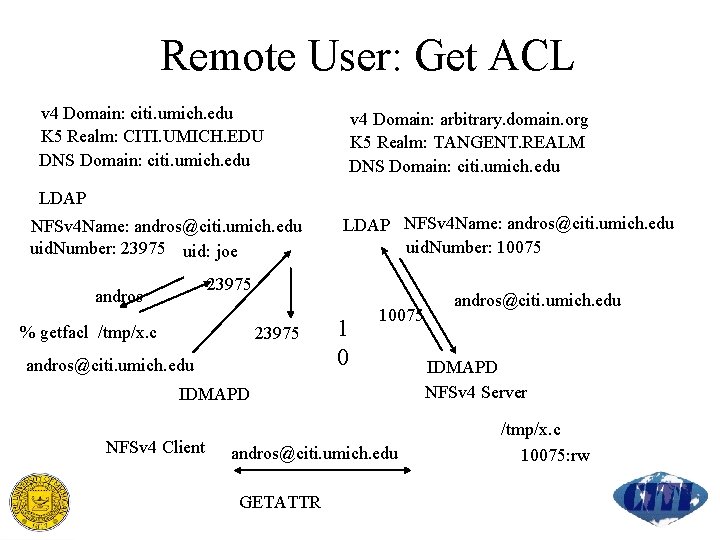
Remote User: Get ACL v 4 Domain: citi. umich. edu K 5 Realm: CITI. UMICH. EDU DNS Domain: citi. umich. edu v 4 Domain: arbitrary. domain. org K 5 Realm: TANGENT. REALM DNS Domain: citi. umich. edu LDAP NFSv 4 Name: andros@citi. umich. edu uid. Number: 23975 uid: joe LDAP NFSv 4 Name: andros@citi. umich. edu uid. Number: 10075 23975 andros % getfacl /tmp/x. c 23975 andros@citi. umich. edu 1 0 10075 IDMAPD NFSv 4 Client andros@citi. umich. edu GETATTR andros@citi. umich. edu IDMAPD NFSv 4 Server /tmp/x. c 10075: rw

Remote User: Get ACL LDAP mappings required only for POSIX getfacl NFSv 4 Name and uid. Number for remote user uid (local user name) for remote user nfsv 4_getfacl simply displays the on-the-wire ACL name Secure LDAP not required

Any Questions? http: //www. citi. umich. edu/projects