PointtoMultipoint in 802 1 Qay Nurit Sprecher Nokia





- Slides: 15

Point-to-Multipoint in 802. 1 Qay Nurit Sprecher, Nokia Siemens Networks Hayim Porat, Ethos Networks Slide 1 11 May 2008

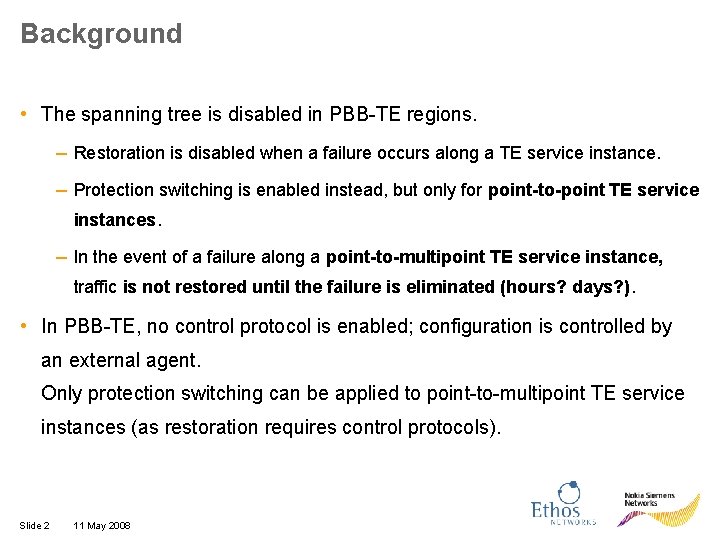
Background • The spanning tree is disabled in PBB-TE regions. – Restoration is disabled when a failure occurs along a TE service instance. – Protection switching is enabled instead, but only for point-to-point TE service instances. – In the event of a failure along a point-to-multipoint TE service instance, traffic is not restored until the failure is eliminated (hours? days? ). • In PBB-TE, no control protocol is enabled; configuration is controlled by an external agent. Only protection switching can be applied to point-to-multipoint TE service instances (as restoration requires control protocols). Slide 2 11 May 2008

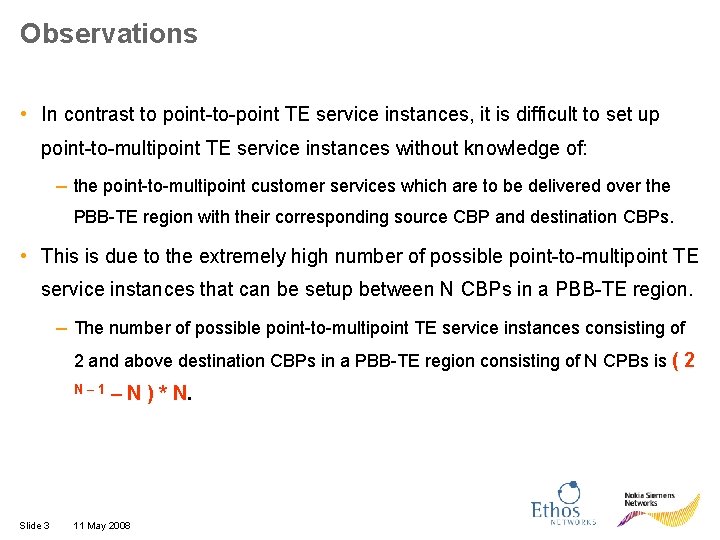
Observations • In contrast to point-to-point TE service instances, it is difficult to set up point-to-multipoint TE service instances without knowledge of: – the point-to-multipoint customer services which are to be delivered over the PBB-TE region with their corresponding source CBP and destination CBPs. • This is due to the extremely high number of possible point-to-multipoint TE service instances that can be setup between N CBPs in a PBB-TE region. – The number of possible point-to-multipoint TE service instances consisting of 2 and above destination CBPs in a PBB-TE region consisting of N CPBs is ( 2 N– 1 Slide 3 – N ) * N. 11 May 2008

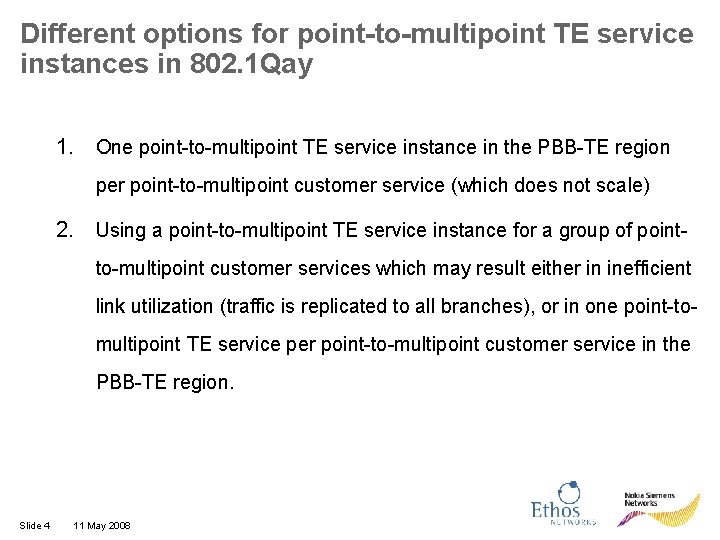
Different options for point-to-multipoint TE service instances in 802. 1 Qay 1. One point-to-multipoint TE service instance in the PBB-TE region per point-to-multipoint customer service (which does not scale) 2. Using a point-to-multipoint TE service instance for a group of pointto-multipoint customer services which may result either in inefficient link utilization (traffic is replicated to all branches), or in one point-tomultipoint TE service per point-to-multipoint customer service in the PBB-TE region. Slide 4 11 May 2008

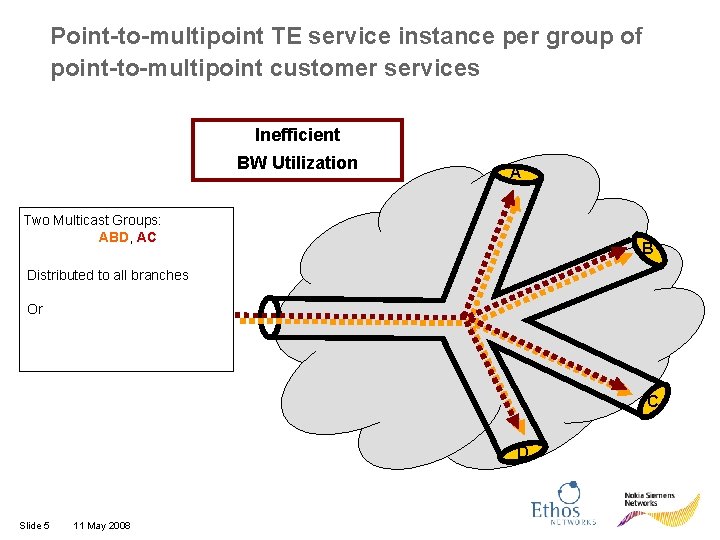
Point-to-multipoint TE service instance per group of point-to-multipoint customer services Inefficient BW Utilization A Two Multicast Groups: ABD, AC B Distributed to all branches Or C D Slide 5 11 May 2008

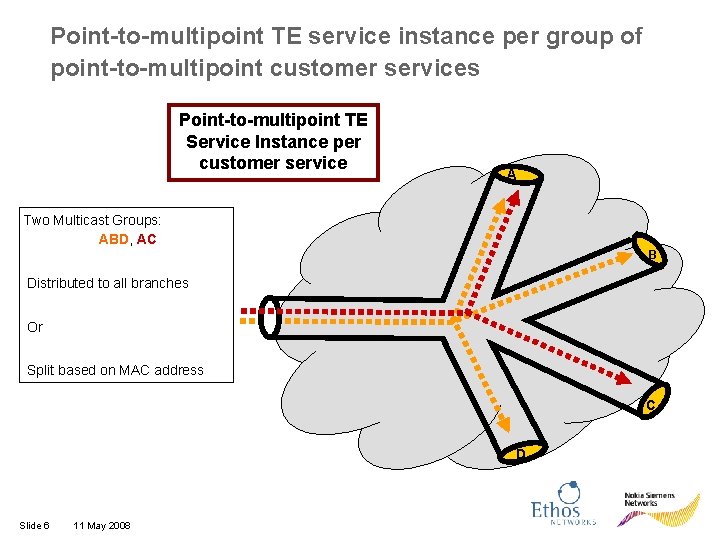
Point-to-multipoint TE service instance per group of point-to-multipoint customer services Point-to-multipoint TE Service Instance per customer service A Two Multicast Groups: ABD, AC B Distributed to all branches Or Split based on MAC address C D Slide 6 11 May 2008

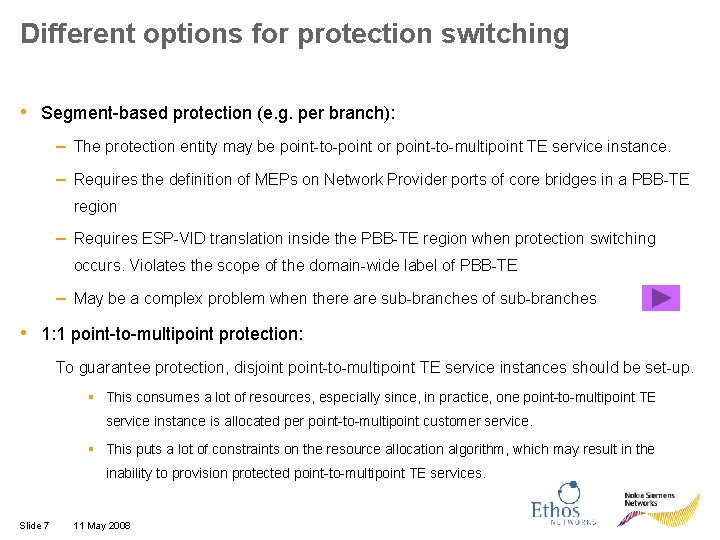
Different options for protection switching • Segment-based protection (e. g. per branch): – The protection entity may be point-to-point or point-to-multipoint TE service instance. – Requires the definition of MEPs on Network Provider ports of core bridges in a PBB-TE region – Requires ESP-VID translation inside the PBB-TE region when protection switching occurs. Violates the scope of the domain-wide label of PBB-TE – May be a complex problem when there are sub-branches of sub-branches • 1: 1 point-to-multipoint protection: To guarantee protection, disjoint point-to-multipoint TE service instances should be set-up. ▪ This consumes a lot of resources, especially since, in practice, one point-to-multipoint TE service instance is allocated per point-to-multipoint customer service. ▪ This puts a lot of constraints on the resource allocation algorithm, which may result in the inability to provision protected point-to-multipoint TE services. Slide 7 11 May 2008

Different options for protection switching (Contd. ) • 1: 1 point-to-point protection: 1. To guarantee protection, disjoint point-to-point TE service instance should be set-up for each destination CBP. ▪ When a failure occurs along a particular branch from the source CBP to a destination CBP, a switchover is performed from the failed branch to the relevant protection point-to-point TE service instance, without affecting the entire point-to-multipoint TE service insatnce. ▪ Although in practice one point-to-multipoint TE service instance is allocated per point-tomultipoint customer service, this result in a better resource utilization as the protection point-to -point TE service instances for the different destination CBPs do not need to disjoint. ▪ This does not put additional constraints on the resource allocation algorithm as compare to the 1: 1 point-to-point protection switching. 2. Point-to-multipoint customer services are delivered over full-mesh protected point-topoint TE service instances. ▪ This does not require any modification to the protection switching mechanism which is defined in 802. 1 Qay. Slide 8 11 May 2008

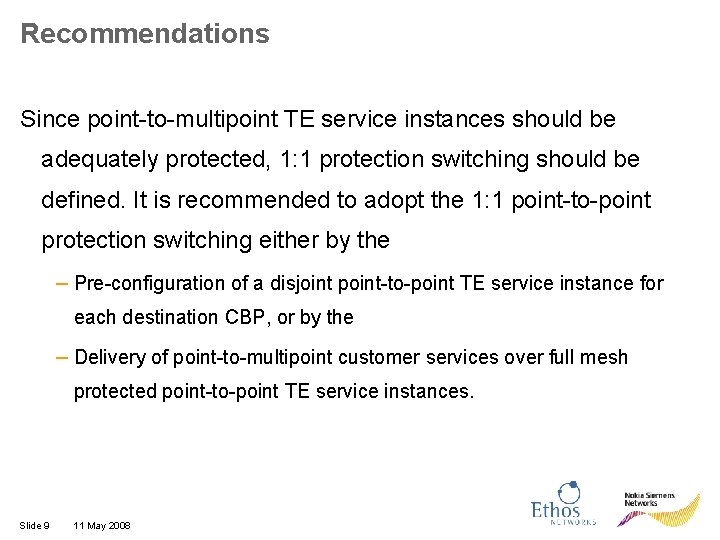
Recommendations Since point-to-multipoint TE service instances should be adequately protected, 1: 1 protection switching should be defined. It is recommended to adopt the 1: 1 point-to-point protection switching either by the – Pre-configuration of a disjoint point-to-point TE service instance for each destination CBP, or by the – Delivery of point-to-multipoint customer services over full mesh protected point-to-point TE service instances. Slide 9 11 May 2008

Thank You Slide 10 11 May 2008

Backup Slides Slide 11 11 May 2008

Protection vs. Restoration • Protection (data plane) – Utilizes the pre-assigned capacity between nodes. – 50 ms is the target time for protection switching. – In the event of failure, the protection mechanism does not involve rerouting or an additional connection setup. Only the source and destination connection controllers are involved. – Protection switching may be either unidirectional or bidirectional. – Protection at link, trunk or circuit layers – Optimization for specific topologies: Linear Protection, Ring Protection • Restoration (distributed control plane, management plane) – Utilizes any available capacity between nodes – The algorithms used for restoration involve rerouting. When restoration is used, a percentage of the transport network capacity is reserved for the rerouting of working traffic. – Any topology. Slide 12 11 May 2008

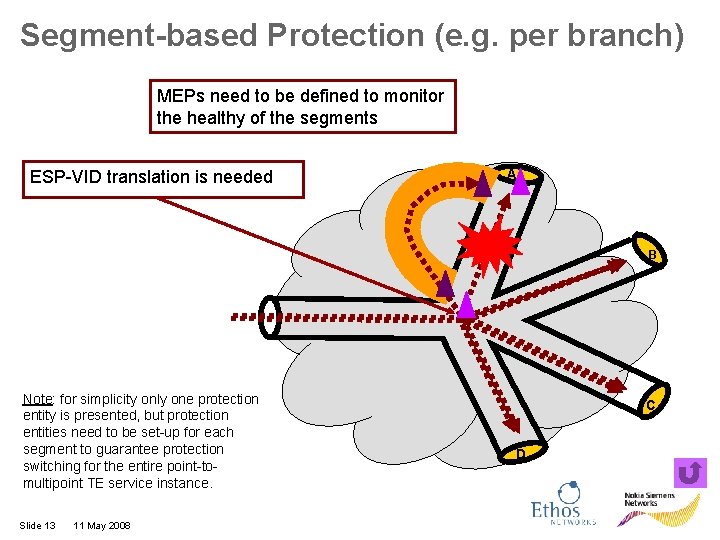
Segment-based Protection (e. g. per branch) MEPs need to be defined to monitor the healthy of the segments ESP-VID translation is needed A B Note: for simplicity only one protection entity is presented, but protection entities need to be set-up for each segment to guarantee protection switching for the entire point-tomultipoint TE service instance. Slide 13 11 May 2008 C D

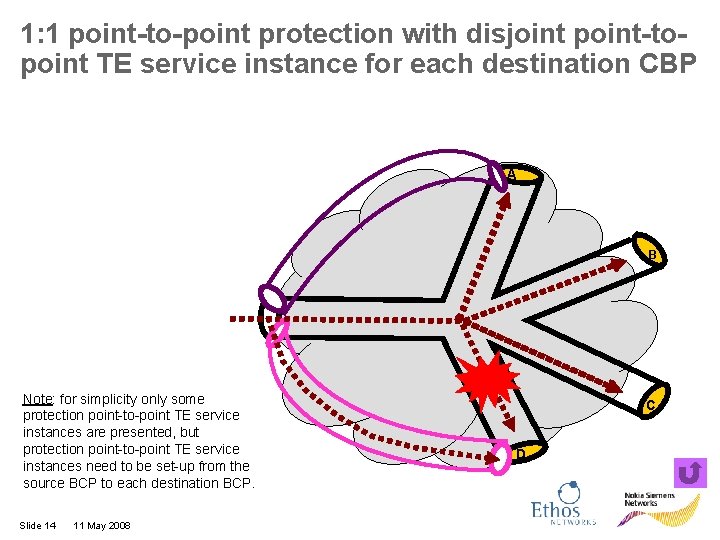
1: 1 point-to-point protection with disjoint point-topoint TE service instance for each destination CBP A B Note: for simplicity only some protection point-to-point TE service instances are presented, but protection point-to-point TE service instances need to be set-up from the source BCP to each destination BCP. Slide 14 11 May 2008 C D

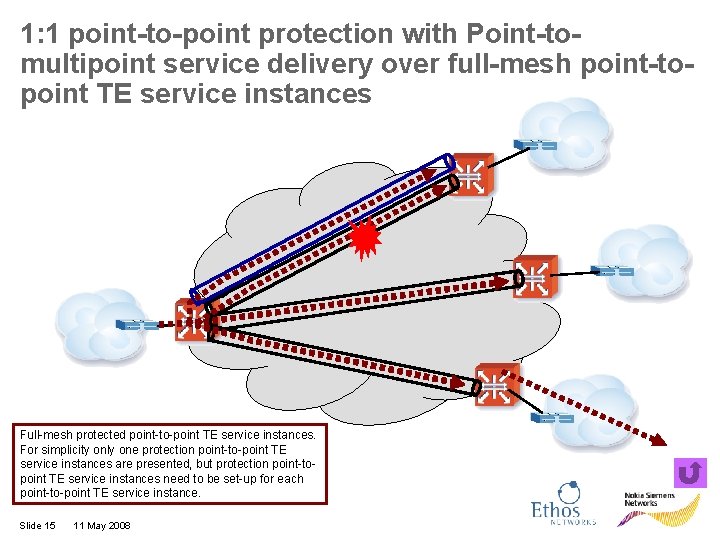
1: 1 point-to-point protection with Point-tomultipoint service delivery over full-mesh point-topoint TE service instances Full-mesh protected point-to-point TE service instances. For simplicity only one protection point-to-point TE service instances are presented, but protection point-topoint TE service instances need to be set-up for each point-to-point TE service instance. Slide 15 11 May 2008
 Bridges from 802.x to 802.y
Bridges from 802.x to 802.y Bridges from 802.x to 802.y
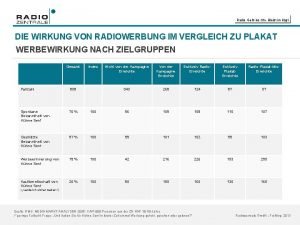
Bridges from 802.x to 802.y Radiowerbung bleibt im kopf
Radiowerbung bleibt im kopf Nokia research center
Nokia research center Nokia bts alarm list
Nokia bts alarm list Nokia keilaniemi
Nokia keilaniemi Sca nokia
Sca nokia Variable pay in nokia
Variable pay in nokia Nokia enterprise solutions
Nokia enterprise solutions Scamper business model
Scamper business model Nokia pen
Nokia pen Nokia 1998
Nokia 1998 Swot nokia
Swot nokia Case study segmentation targeting positioning
Case study segmentation targeting positioning Nokia balaca telefon
Nokia balaca telefon Nokia nesc
Nokia nesc