Packet Classification George Varghese Original Motivation Firewalls Firewalls







- Slides: 24

Packet Classification George Varghese

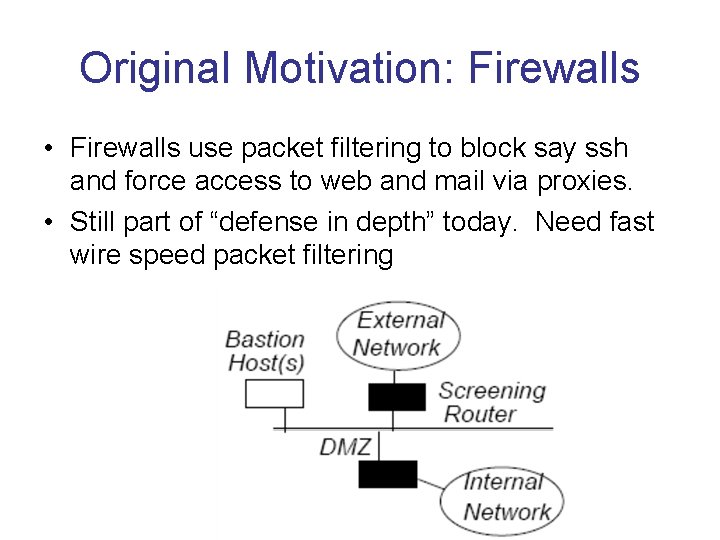
Original Motivation: Firewalls • Firewalls use packet filtering to block say ssh and force access to web and mail via proxies. • Still part of “defense in depth” today. Need fast wire speed packet filtering

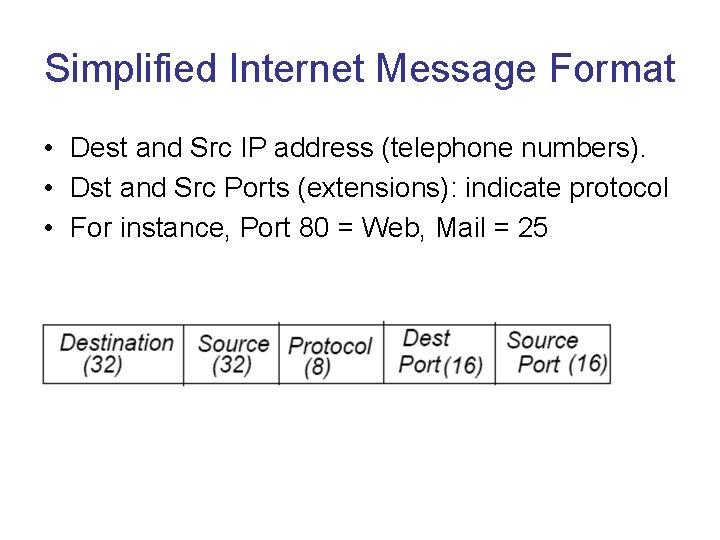
Simplified Internet Message Format • Dest and Src IP address (telephone numbers). • Dst and Src Ports (extensions): indicate protocol • For instance, Port 80 = Web, Mail = 25

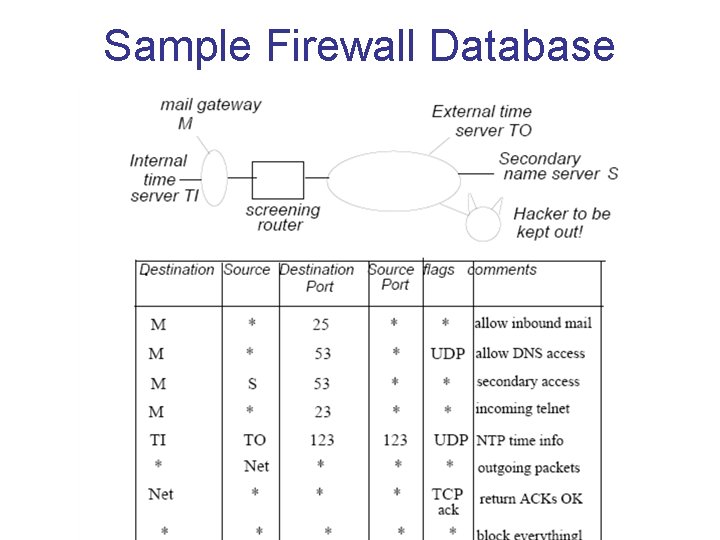
Sample Firewall Database

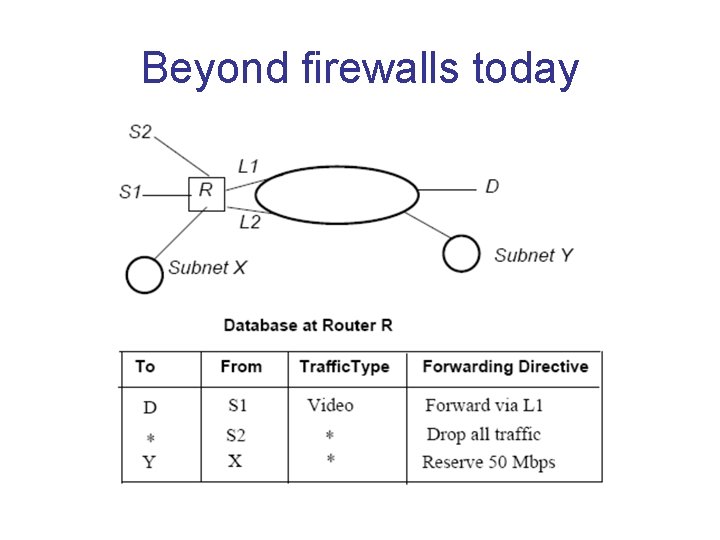
Beyond firewalls today

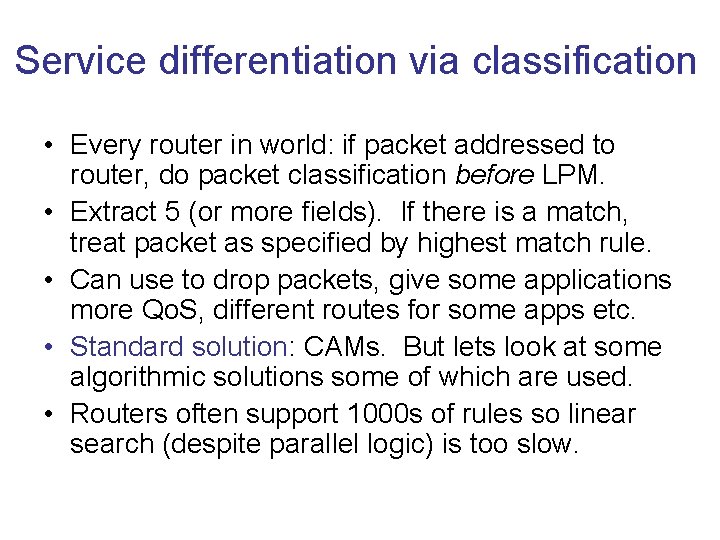
Service differentiation via classification • Every router in world: if packet addressed to router, do packet classification before LPM. • Extract 5 (or more fields). If there is a match, treat packet as specified by highest match rule. • Can use to drop packets, give some applications more Qo. S, different routes for some apps etc. • Standard solution: CAMs. But lets look at some algorithmic solutions some of which are used. • Routers often support 1000 s of rules so linear search (despite parallel logic) is too slow.

Plan of Attack • First, 2 -field (2 D) packet classification. Useful for measurement and multicast. • Then we introduce a nice geometric model and move on to general K-field classification.

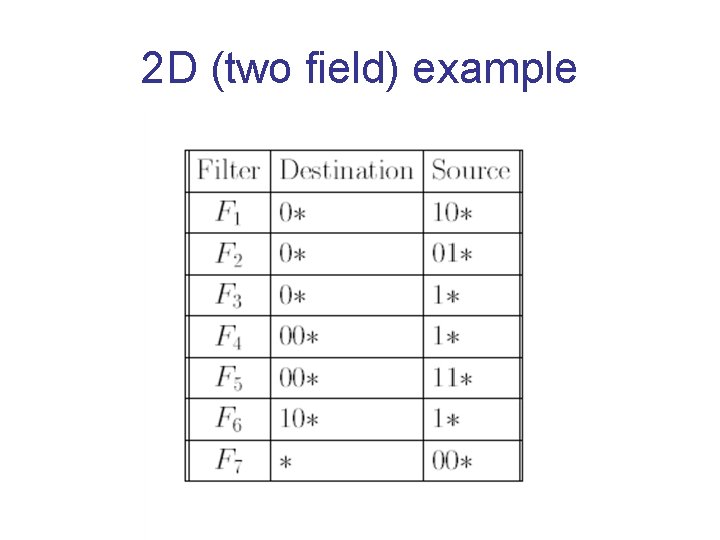
2 D (two field) example

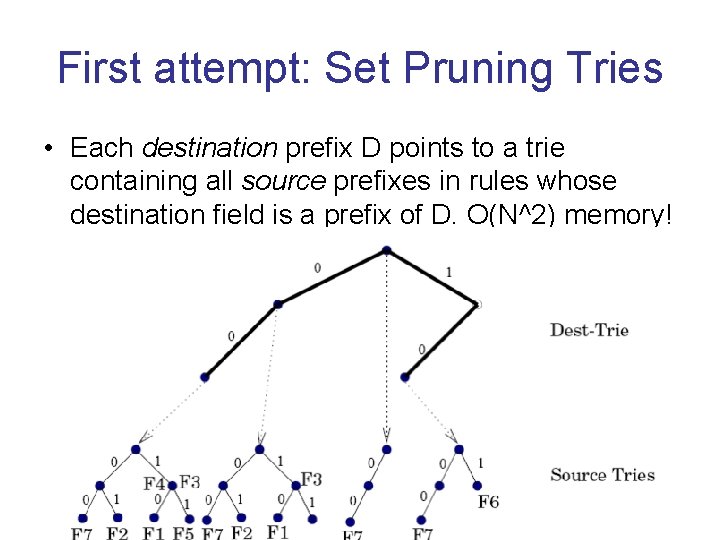
First attempt: Set Pruning Tries • Each destination prefix D points to a trie containing all source prefixes in rules whose destination field is a prefix of D. O(N^2) memory!

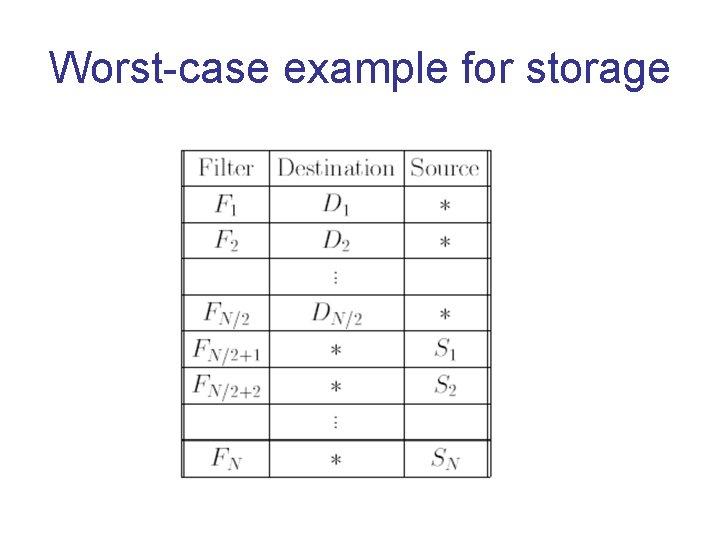
Worst-case example for storage

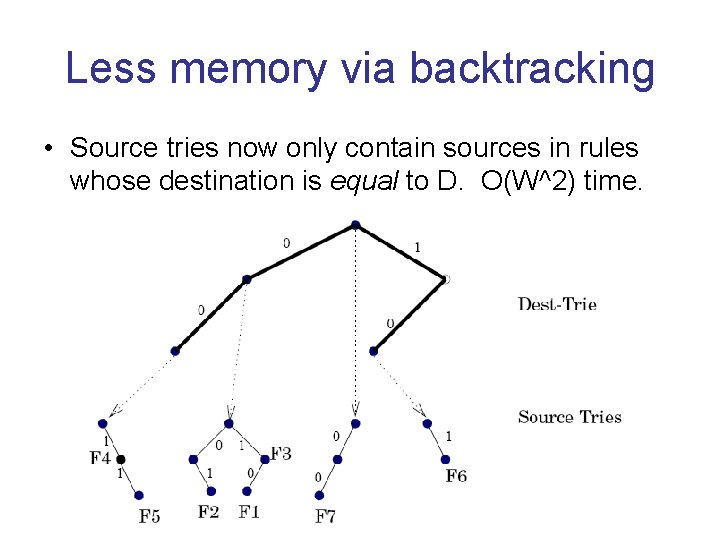
Less memory via backtracking • Source tries now only contain sources in rules whose destination is equal to D. O(W^2) time.

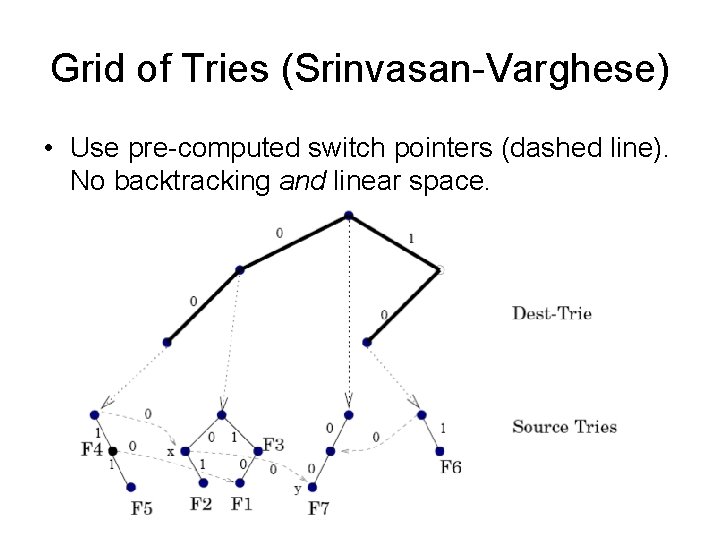
Grid of Tries (Srinvasan-Varghese) • Use pre-computed switch pointers (dashed line). No backtracking and linear space.

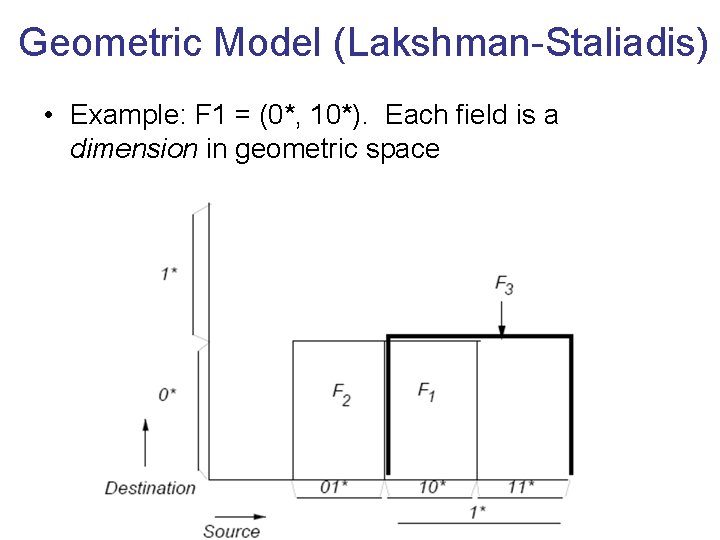
Geometric Model (Lakshman-Staliadis) • Example: F 1 = (0*, 10*). Each field is a dimension in geometric space

Beyond 2 D • Bad News: Lower bound (computational geometry): O((W^k)/k!) time for linear storage. • Good news: (Gupta-Mckeown): # of Disjoint classification regions in real databases is small. • For example: theoretically in 2 D we can have N^2 disjoint regions but practically we have O(N) • Can we exploit this observation for speed with small storage. Yes, but not provably. Heuristics.

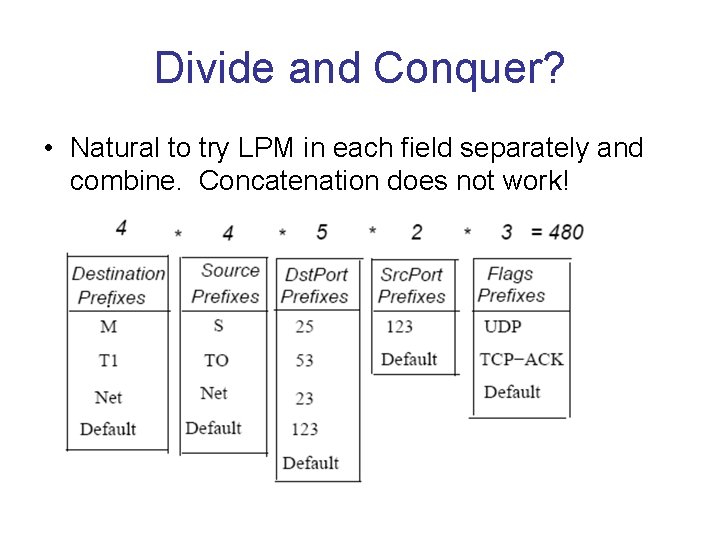
Divide and Conquer? • Natural to try LPM in each field separately and combine. Concatenation does not work!

Aside: Range to Prefix Matches • Real classifiers use ranges (e. g. , < 1024 for well known ports). • Theorem: Can write any range as the union of a logaritmic number of prefix ranges. • Example: [8, 12] in 5 bits. 01* does not work but 0100* and 0101* and 011000 does! • Useful theorem for CAM vendors as well as they only support prefix ranges. Recall hardware!

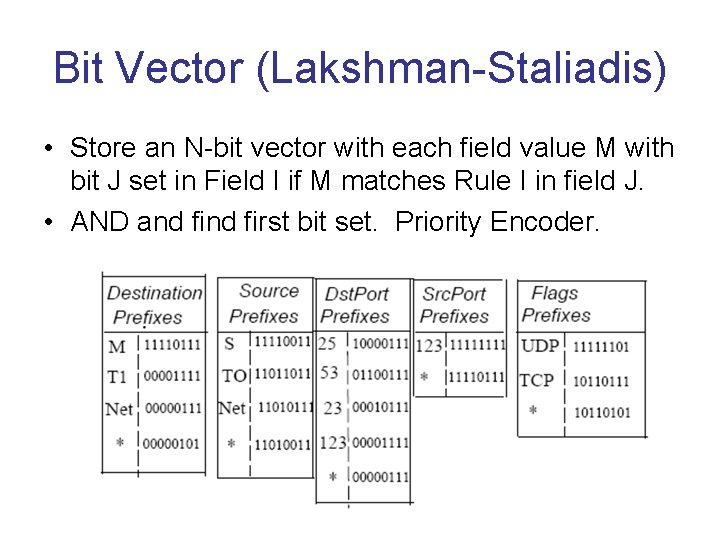
Bit Vector (Lakshman-Staliadis) • Store an N-bit vector with each field value M with bit J set in Field I if M matches Rule I in field J. • AND and first bit set. Priority Encoder.

Why is Lucent Fast? • Since the bit vectors are O(N), from a CS perspective it is O(N), as bad as linear search. • Really reduces constants uses wide memories. • Nk/W memory accesses where W is width. • Recall W = 1000 is feasible 1000 rule tables in a few accesses, many of which are parallel. • Moral: Know hardware complexity measures!

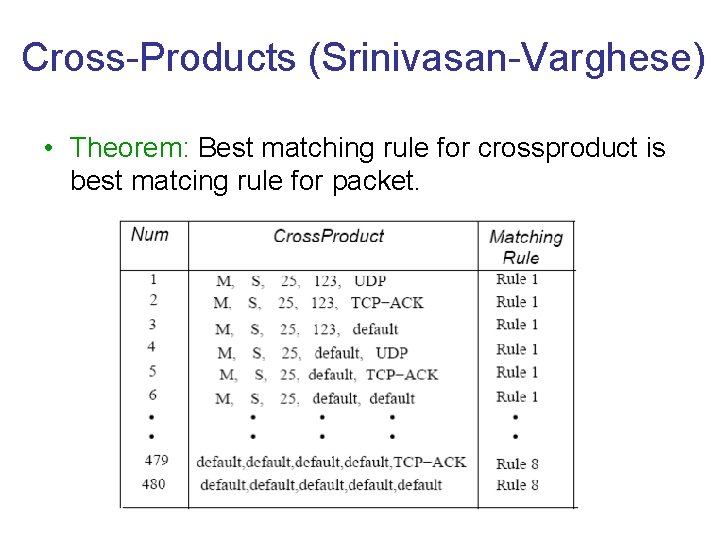
Cross-Products (Srinivasan-Varghese) • Theorem: Best matching rule for crossproduct is best matcing rule for packet.

Equivalenced Crossproducts (Gupta-Mckeown): aka RFC • Idea: Instead of “multiplying” in 1 fell swoop, do 2 at a time and equivalence at each step. GSR 16 crossproducts but only 8 classes!

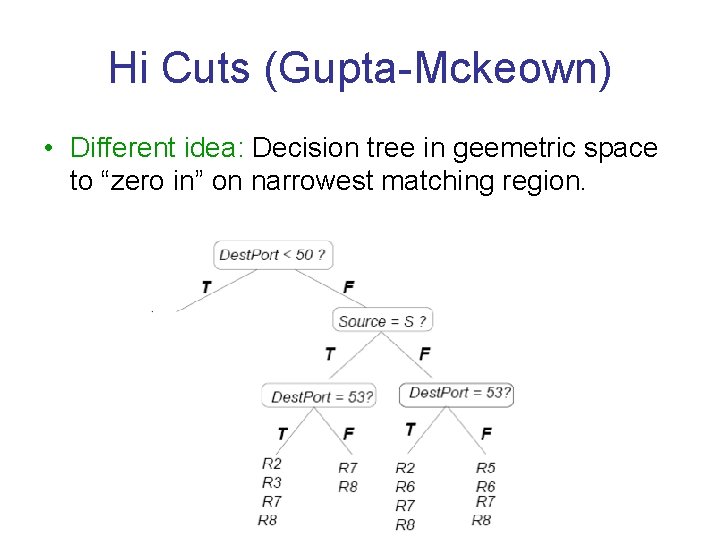
Hi Cuts (Gupta-Mckeown) • Different idea: Decision tree in geemetric space to “zero in” on narrowest matching region.

State of Art • Woo algorithm: Like Hi. Cuts but uses bit testing and not range testing. • Hypercuts (Singh): beyond Woo to test multiple bits at a time using arrays. Cisco CRS • Space usage of Hypercuts/Hi. Cuts can be employed using 2 parallel trees (Brian Alleyne) • Efficuts (Purdue, SIGCOMM 2010) is a publicly available implementation of best ideas so far. • CAMs still easier though need algorithmic tricks to reduce power.

Principles Used • • P 1: Relax Specification (heuristics beyond 2 D) P 2: Degrees of freedom (Hi. Cuts Hypercuts) P 3: Shift Computation in Time (grid-of-tries) P 4: Avoid Waste seen (Crossproducts RFC) P 5: Add State for efficiency (switch pointers) P 6: Hardware parallelism (Bit vector) P 8: Finite universe methods (Bit vector) P 9: Use algorithmic thinking (decision trees)

Students like you. . . • PANKAJ Stanford Sahasra Netlogic Twitter CHEENU UCSD Sahasra Netlogic Google SUMEET UCSD Net. Sift Cisco SO DO A GREAT PROJECT! SOME MORE PAPERS UP
 Julian varghese
Julian varghese Developer.apple.com
Developer.apple.com George washington vs king george iii venn diagram
George washington vs king george iii venn diagram Venn diagram ghent
Venn diagram ghent Linux kernel history
Linux kernel history Introduction to firewalls
Introduction to firewalls What are the two main types of firewall
What are the two main types of firewall Characteristics of a firewall
Characteristics of a firewall Iptables stateful or stateless
Iptables stateful or stateless Ids sensors
Ids sensors Firewalls are used for what security principle
Firewalls are used for what security principle Carp vs vrrp
Carp vs vrrp Types of firewalls ppt
Types of firewalls ppt Dynamic firewalls
Dynamic firewalls Perimeter firewalls are the simplest type of firewall
Perimeter firewalls are the simplest type of firewall Firewall security audit
Firewall security audit Utulsa computer science
Utulsa computer science Ssh works
Ssh works Neurocuts
Neurocuts Three fold classification of motivation security
Three fold classification of motivation security Eager learning vs lazy learning
Eager learning vs lazy learning Manifold table in statistics
Manifold table in statistics Traditional classification vs modern classification
Traditional classification vs modern classification Original gospel manuscripts
Original gospel manuscripts An operation that maps an original figure called the
An operation that maps an original figure called the