Introduction to firewalls and IDSIPS 1 firewalls 2

















- Slides: 62

Introduction to firewalls and IDS/IPS 1

firewalls 2

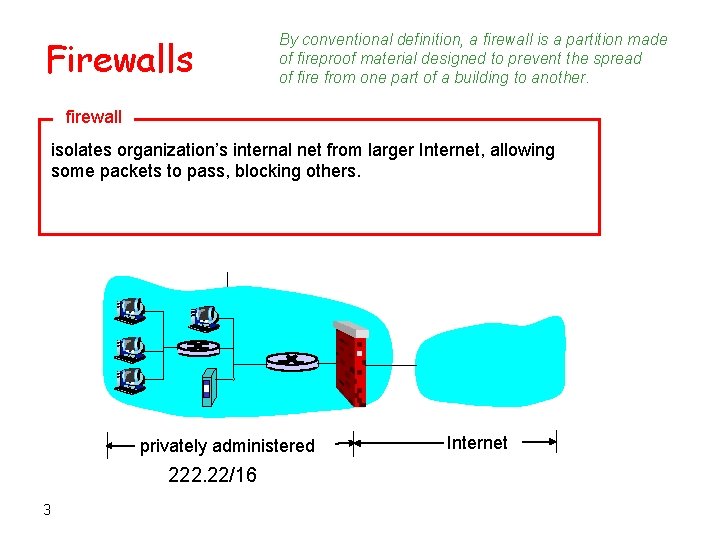
Firewalls By conventional definition, a firewall is a partition made of fireproof material designed to prevent the spread of fire from one part of a building to another. firewall isolates organization’s internal net from larger Internet, allowing some packets to pass, blocking others. privately administered 222. 22/16 3 Internet

Firewall goals: • All traffic from outside to inside and viceversa passes through the firewall. • Only authorized traffic, as defined by local security policy, will be allowed to pass. • The firewall itself is immune to penetration. 4

Firewalls: taxonomy 1. Traditional packet filters – filters often combined with router, creating a firewall 2. Stateful filters 3. Application gateways 5 Major firewall vendors: Checkpoint Cisco PIX

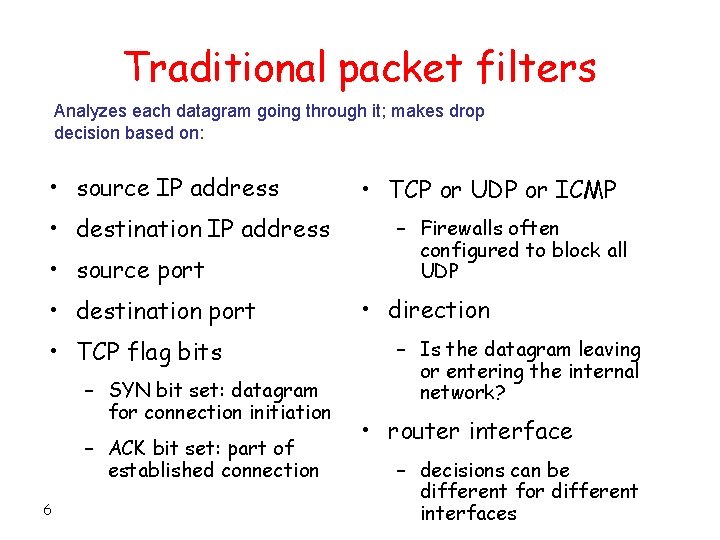
Traditional packet filters Analyzes each datagram going through it; makes drop decision based on: • source IP address • destination IP address • source port • destination port • TCP flag bits – SYN bit set: datagram for connection initiation – ACK bit set: part of established connection 6 • TCP or UDP or ICMP – Firewalls often configured to block all UDP • direction – Is the datagram leaving or entering the internal network? • router interface – decisions can be different for different interfaces

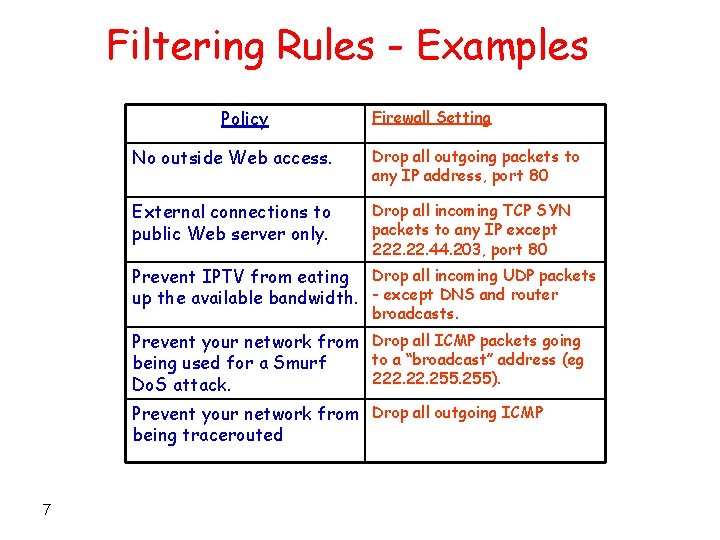
Filtering Rules - Examples Policy Firewall Setting No outside Web access. Drop all outgoing packets to any IP address, port 80 External connections to public Web server only. Drop all incoming TCP SYN packets to any IP except 222. 44. 203, port 80 Prevent IPTV from eating Drop all incoming UDP packets up the available bandwidth. - except DNS and router broadcasts. Prevent your network from Drop all ICMP packets going to a “broadcast” address (eg being used for a Smurf 222. 255). Do. S attack. Prevent your network from Drop all outgoing ICMP being tracerouted 7

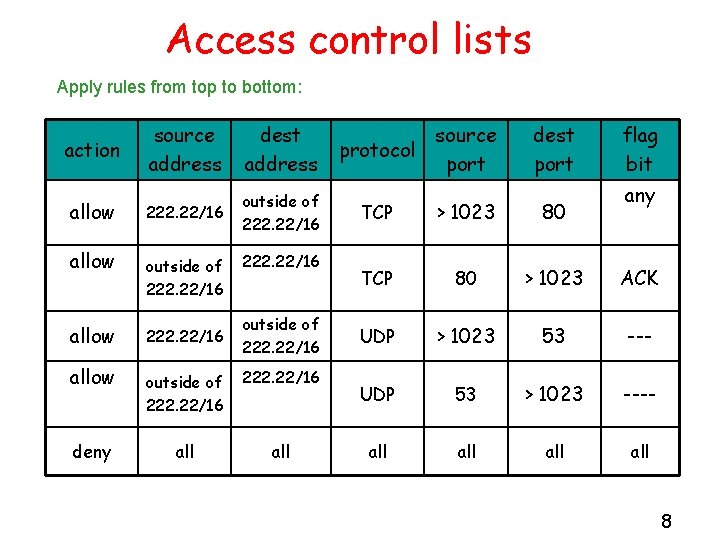
Access control lists Apply rules from top to bottom: action allow deny source address dest address 222. 22/16 outside of 222. 22/16 all source protocol port dest port flag bit any TCP > 1023 80 TCP 80 > 1023 ACK UDP > 1023 53 --- UDP 53 > 1023 ---- all all 8

Access control lists • Each router/firewall interface can have its own ACL • Most firewall vendors provide both commandline and graphical configuration interface 9 Introduction

Advantages and disadvantages of traditional packet filters • Advantages – One screening router can protect entire network – Can be efficient if filtering rules are kept simple – Widely available. Almost any router, even Linux boxes • Disadvantages – Can possibly be penetrated – Cannot enforce some policies. For example, permit certain users. – Rules can get complicated and difficult to test 10

Case Study: iptables

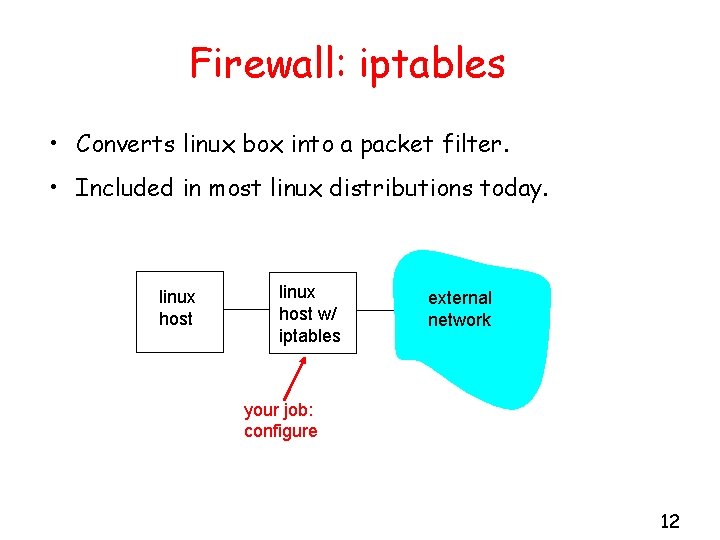
Firewall: iptables • Converts linux box into a packet filter. • Included in most linux distributions today. linux host w/ iptables external network your job: configure 12

Firewall: iptables • iptables – Provides firewall capability to a linux host – Comes installed with most linux distributions – Three types of tables: FILTER, NAT, MANGLE – Let’s only consider FILTER table for now 13

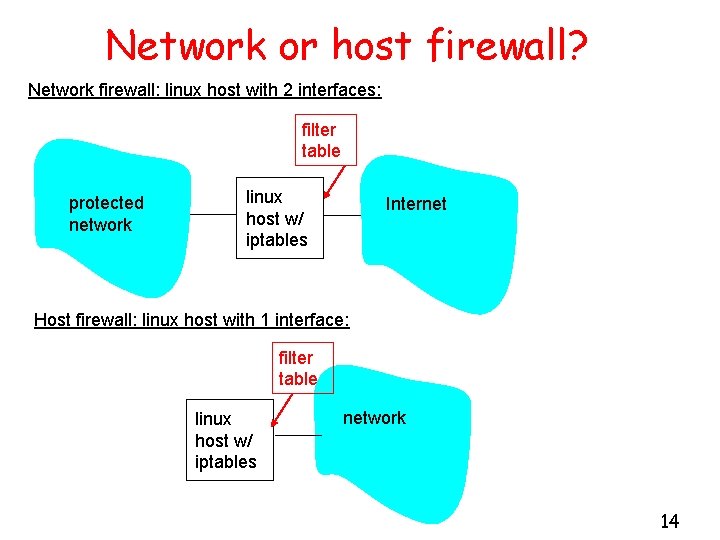
Network or host firewall? Network firewall: linux host with 2 interfaces: filter table protected network linux host w/ iptables Internet Host firewall: linux host with 1 interface: filter table linux host w/ iptables network 14

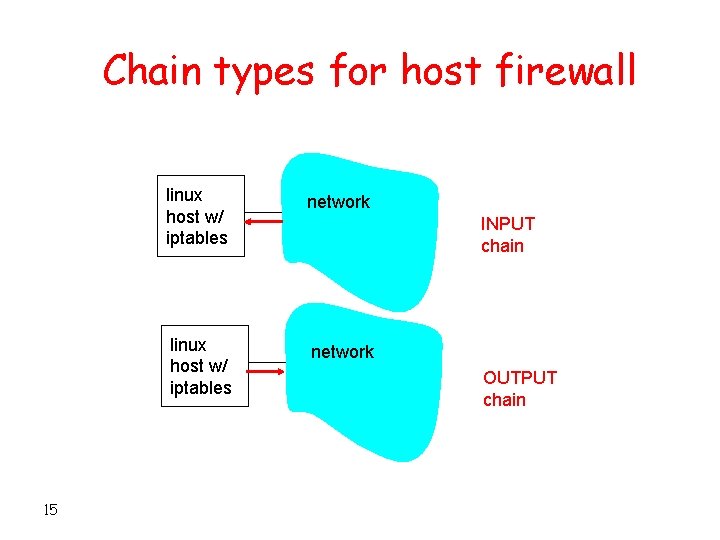
Chain types for host firewall 15 linux host w/ iptables network INPUT chain OUTPUT chain

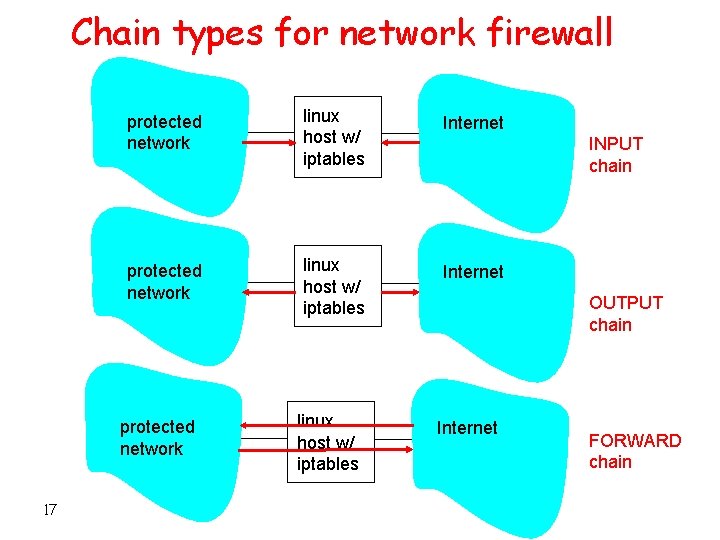
INPUT, OUTPUT, FORWARD CHAINS for network firewall • INPUT chain applies for all packets destined to firewall • OUTPUT chain applies for all packets originating from firewall • FORWARD chain applies for all packets passing through firewall. 16

Chain types for network firewall protected network linux host w/ iptables Internet protected network 17 linux host w/ iptables INPUT chain OUTPUT chain Internet FORWARD chain

iptables: Example command iptables –A INPUT –i eth 0 –s 232. 16. 4. 0/24 –j ACCEPT • Sets a rule – Accepts packets that enter from interface eth 0 and have source address in 232. 16. 4/24 • Kernel applies the rules in order. – The first rule that matches packet determines the action for that packet • Append: -A 18 – Adds rule to bottom of list of existing rules

iptables: Example command iptables –A INPUT –i eth 0 –j DENY • Sets a rule – Rejects all packets that enter from interface eth 0 (except for those accepted by previous rules) 19

iptables: More examples iptables –L – list current rules iptables –F – flush all rules iptables –D INPUT 2 – deletes 2 nd rule in INPUT chain iptables –I INPUT 1 –p tcp –tcp-flags SYN –s 232. 16. 4. 0/24 –d 0/0: 22 –j ACCEPT – -I INPUT 1: insert INPUT rule at top 20 – Accept TCP SYNs to from 232. 16. 4. 0/24 to firewall port 22 (ssh)

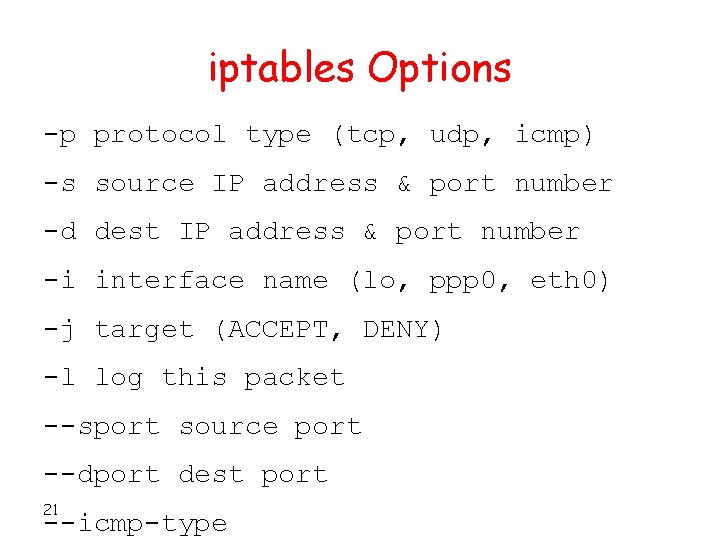
iptables Options -p protocol type (tcp, udp, icmp) -s source IP address & port number -d dest IP address & port number -i interface name (lo, ppp 0, eth 0) -j target (ACCEPT, DENY) -l log this packet --sport source port --dport dest port 21 --icmp-type

iptable Table types • FILTER: – What we have been talking about! – 3 chain types: INPUT, OUTPUT, and FORWARD • NAT: – Hide internal network hosts from outside world. Outside world only sees the gateway’s external IP address, and no other internal IP addresses – PREROUTING, POSTROUTING, and others • MANGLE 22 – Don’t worry about it.

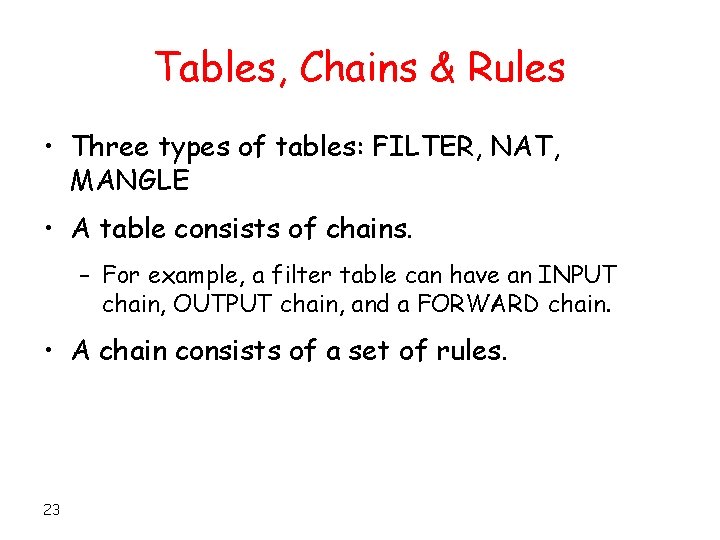
Tables, Chains & Rules • Three types of tables: FILTER, NAT, MANGLE • A table consists of chains. – For example, a filter table can have an INPUT chain, OUTPUT chain, and a FORWARD chain. • A chain consists of a set of rules. 23

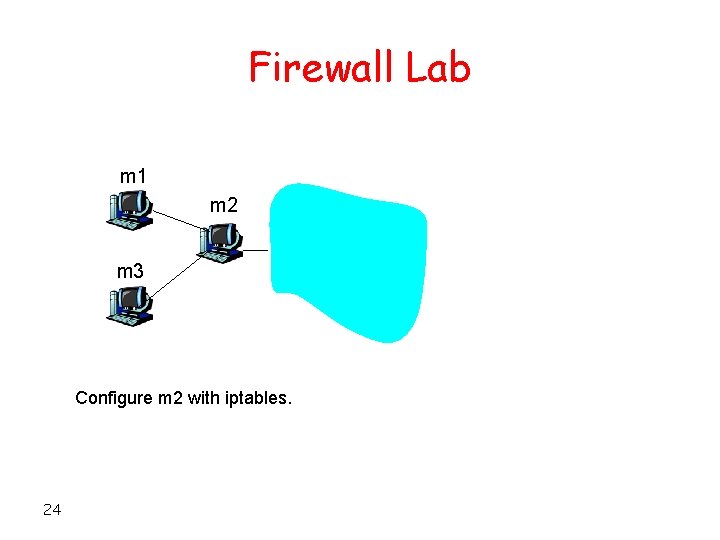
Firewall Lab m 1 m 2 m 3 Configure m 2 with iptables. 24

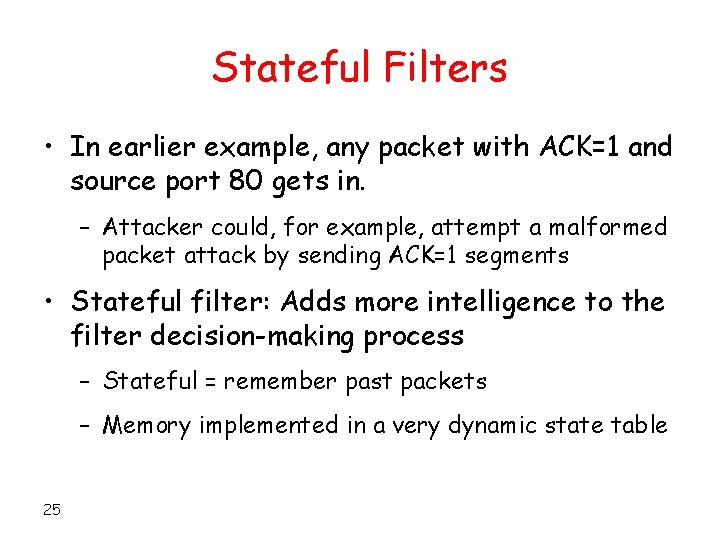
Stateful Filters • In earlier example, any packet with ACK=1 and source port 80 gets in. – Attacker could, for example, attempt a malformed packet attack by sending ACK=1 segments • Stateful filter: Adds more intelligence to the filter decision-making process – Stateful = remember past packets – Memory implemented in a very dynamic state table 25

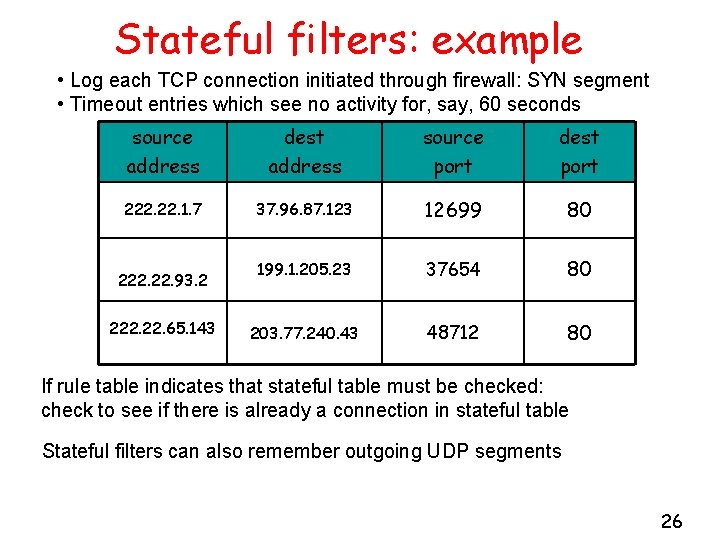
Stateful filters: example • Log each TCP connection initiated through firewall: SYN segment • Timeout entries which see no activity for, say, 60 seconds source address dest address source port dest port 222. 1. 7 37. 96. 87. 123 12699 80 199. 1. 205. 23 37654 80 203. 77. 240. 43 48712 80 222. 93. 2 222. 65. 143 If rule table indicates that stateful table must be checked: check to see if there is already a connection in stateful table Stateful filters can also remember outgoing UDP segments 26

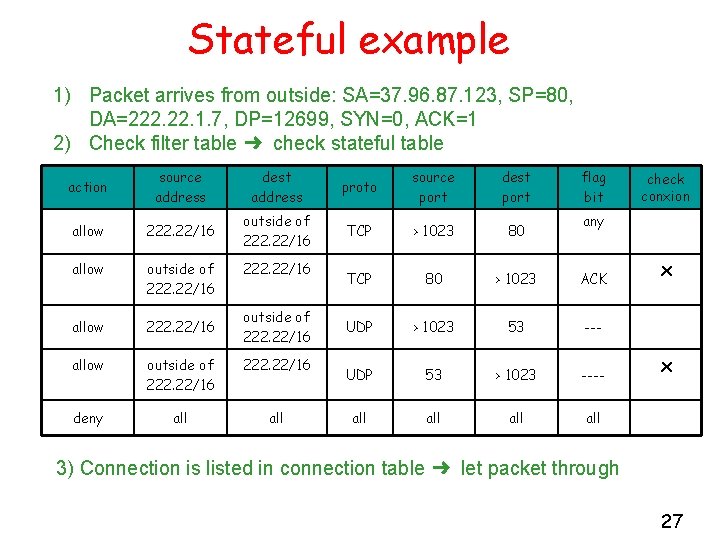
Stateful example 1) Packet arrives from outside: SA=37. 96. 87. 123, SP=80, DA=222. 1. 7, DP=12699, SYN=0, ACK=1 2) Check filter table ➜ check stateful table action source address dest address proto source port dest port allow 222. 22/16 outside of 222. 22/16 TCP > 1023 80 allow outside of 222. 22/16 TCP 80 > 1023 ACK allow 222. 22/16 UDP > 1023 53 --- allow outside of 222. 22/16 UDP 53 > 1023 ---- deny all all all 222. 22/16 outside of 222. 22/16 flag bit check conxion any x x 3) Connection is listed in connection table ➜ let packet through 27

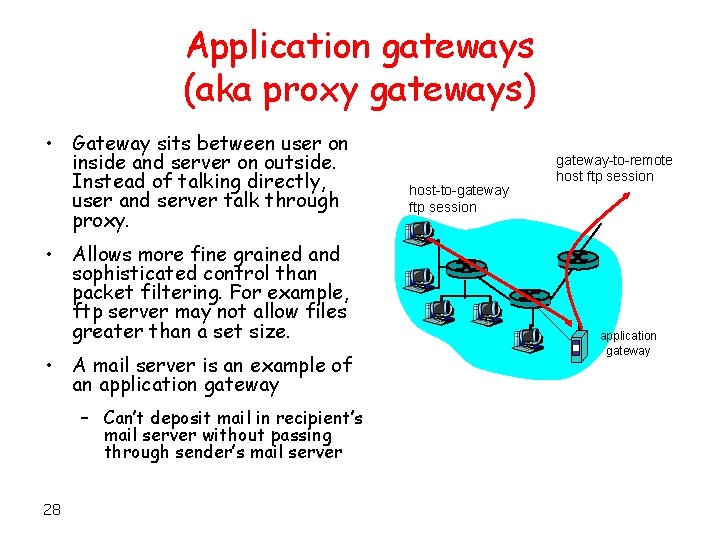
Application gateways (aka proxy gateways) • Gateway sits between user on inside and server on outside. Instead of talking directly, user and server talk through proxy. • Allows more fine grained and sophisticated control than packet filtering. For example, ftp server may not allow files greater than a set size. • A mail server is an example of an application gateway – Can’t deposit mail in recipient’s mail server without passing through sender’s mail server 28 host-to-gateway ftp session gateway-to-remote host ftp session application gateway

Configuring client Tools/options/connections/LAN settings/proxies: 29

Advantages and disadvantages of proxy gateways • Advantages – Proxy can log all connections, activity in connections – Proxy can provide caching – Proxy can do intelligent filtering based on content – Proxy can perform user-level authentication • Disadvantages – Not all services have proxied versions – May need different proxy server for each service – Requires modification of client 30 – Performance

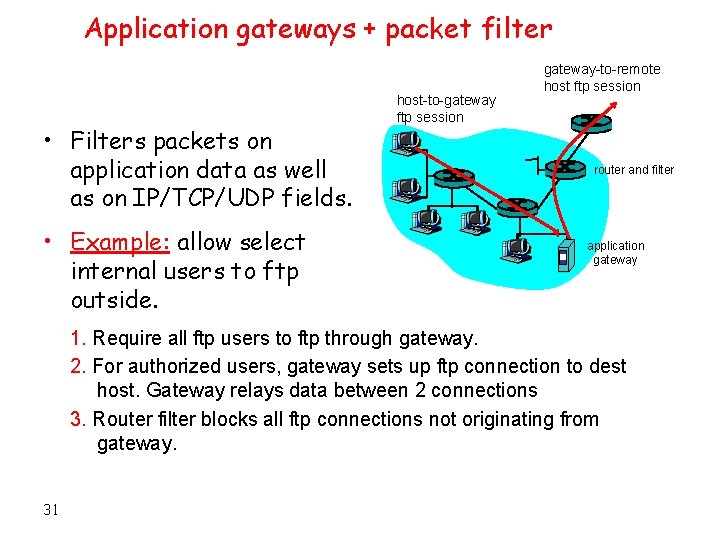
Application gateways + packet filter • Filters packets on application data as well as on IP/TCP/UDP fields. • Example: allow select internal users to ftp outside. host-to-gateway ftp session gateway-to-remote host ftp session router and filter application gateway 1. Require all ftp users to ftp through gateway. 2. For authorized users, gateway sets up ftp connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all ftp connections not originating from gateway. 31

Chaining Proxies proxy 2 proxy 1 32

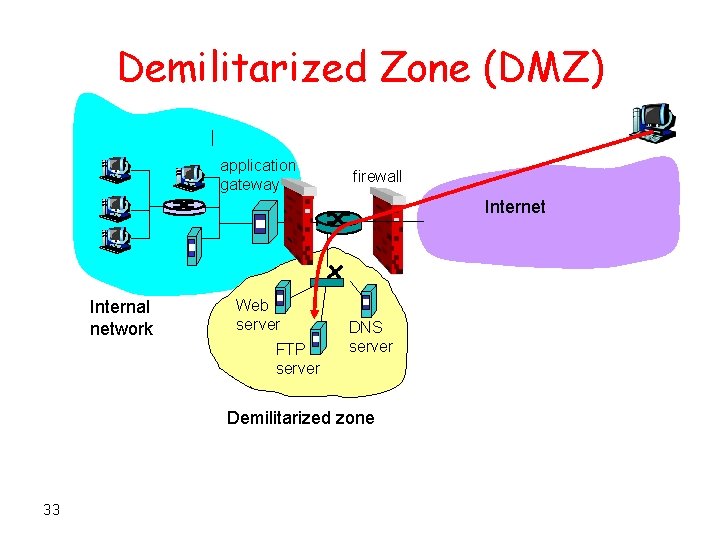
Demilitarized Zone (DMZ) application gateway firewall Internet Internal network Web server FTP server DNS server Demilitarized zone 33

Firewalls: Summary • Filters – Widely available in routers, linux • Stateful filters – Maintains connection state • Application gateways – Often implemented with SOCKS today 34

Intrusion Detection/Prevention Systems

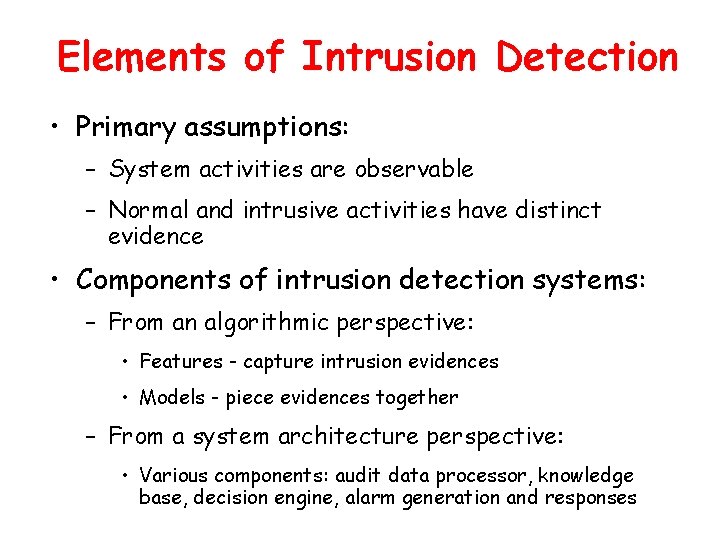
Elements of Intrusion Detection • Primary assumptions: – System activities are observable – Normal and intrusive activities have distinct evidence • Components of intrusion detection systems: – From an algorithmic perspective: • Features - capture intrusion evidences • Models - piece evidences together – From a system architecture perspective: • Various components: audit data processor, knowledge base, decision engine, alarm generation and responses

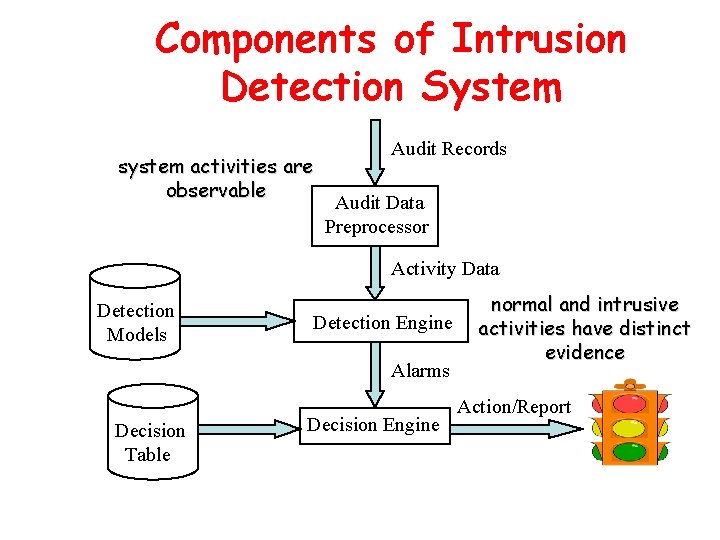
Components of Intrusion Detection System system activities are observable Audit Records Audit Data Preprocessor Activity Data Detection Models Detection Engine Alarms Decision Table Decision Engine normal and intrusive activities have distinct evidence Action/Report

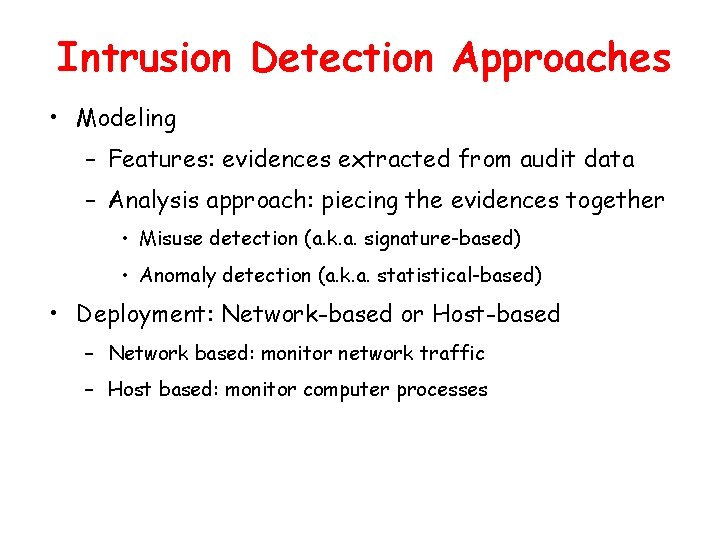
Intrusion Detection Approaches • Modeling – Features: evidences extracted from audit data – Analysis approach: piecing the evidences together • Misuse detection (a. k. a. signature-based) • Anomaly detection (a. k. a. statistical-based) • Deployment: Network-based or Host-based – Network based: monitor network traffic – Host based: monitor computer processes

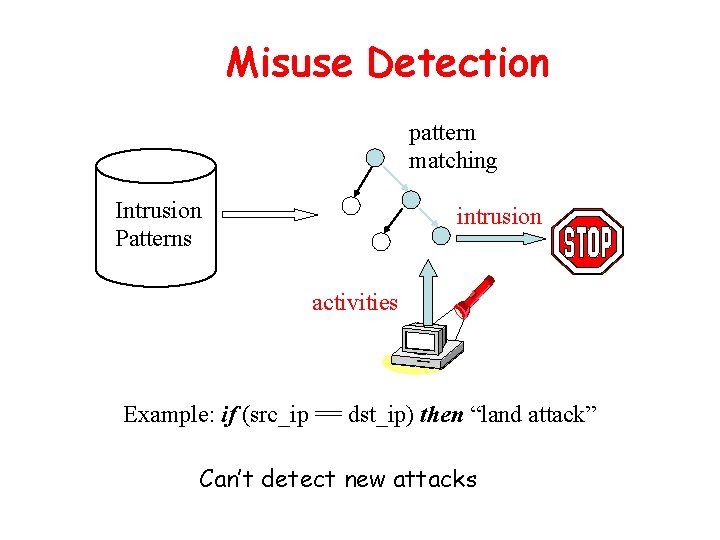
Misuse Detection pattern matching Intrusion Patterns intrusion activities Example: if (src_ip == dst_ip) then “land attack” Can’t detect new attacks

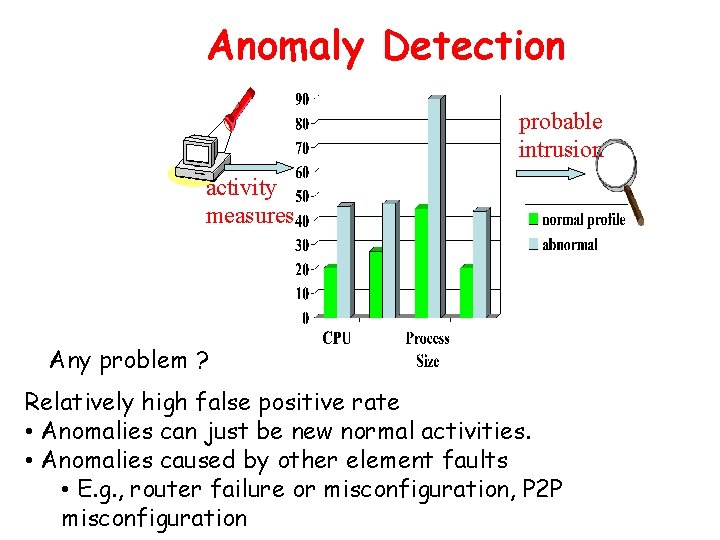
Anomaly Detection probable intrusion activity measures Any problem ? Relatively high false positive rate • Anomalies can just be new normal activities. • Anomalies caused by other element faults • E. g. , router failure or misconfiguration, P 2 P misconfiguration

Host-Based IDSs • Using OS auditing mechanisms – E. G. , BSM on Solaris: logs all direct or indirect events generated by a user – strace for system calls made by a program (Linux) • Monitoring user activities – E. G. , analyze shell commands • Problems: user dependent – Have to install IDS on all user machines ! – Ineffective for large scale attacks

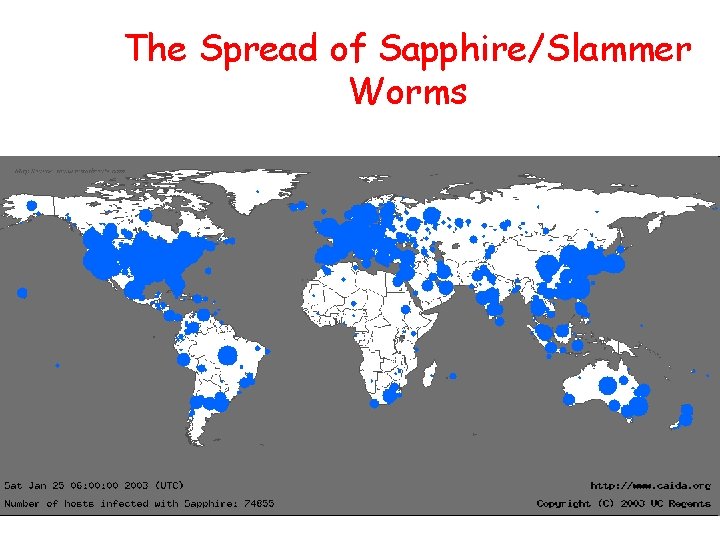
The Spread of Sapphire/Slammer Worms

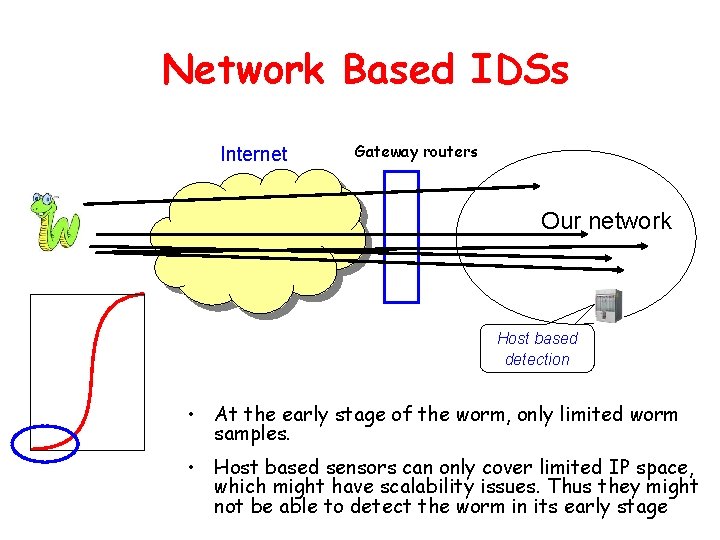
Network Based IDSs Internet Gateway routers Our network Host based detection • At the early stage of the worm, only limited worm samples. • Host based sensors can only cover limited IP space, which might have scalability issues. Thus they might not be able to detect the worm in its early stage

Network IDSs • Deploying sensors at strategic locations – E. G. , Packet sniffing via tcpdump at routers • Inspecting network traffic – Watch for violations of protocols and unusual connection patterns • Monitoring user activities – Look into the data portions of the packets for malicious code • May be easily defeated by encryption – Data portions and some header information can be encrypted – The decryption engine may still be there, especially for exploit

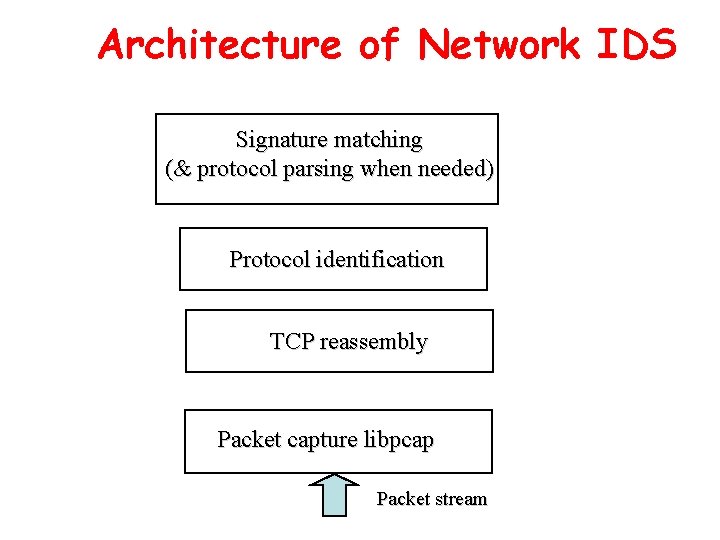
Architecture of Network IDS Signature matching (& protocol parsing when needed) Protocol identification TCP reassembly Packet capture libpcap Packet stream

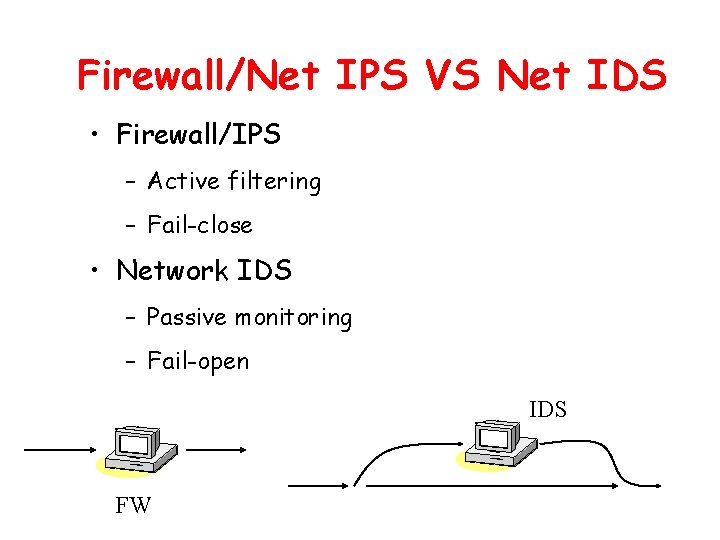
Firewall/Net IPS VS Net IDS • Firewall/IPS – Active filtering – Fail-close • Network IDS – Passive monitoring – Fail-open IDS FW

Related Tools for Network IDS (I) • While not an element of Snort, Ethereal is the best open source GUI-based packet viewer • www. ethereal. com offers: – Windows – UNIX, e. g. , www. ethereal. com/download. html – Red Hat Linux RPMs: ftp. ethereal. com/pub/ethereal/rpms/


Related Tools for Network IDS (II) • Also not an element of Snort, tcpdump is a well-established CLI packet capture tool – www. tcpdump. org offers UNIX source – http: //www. winpcap. org/windump/ offers windump, a Windows port of tcpdump • windump is helpful because it will help you see the different interfaces available on your sensor

Case Study: Snort IDS

Snort 1. A packet sniffer: capture and display packets from the network with different levels of detail on the console 2. Packet logger: log data in text file 3. Honeypot monitor: deceiving hostile parties 4. NIDS: network intrusion detection system

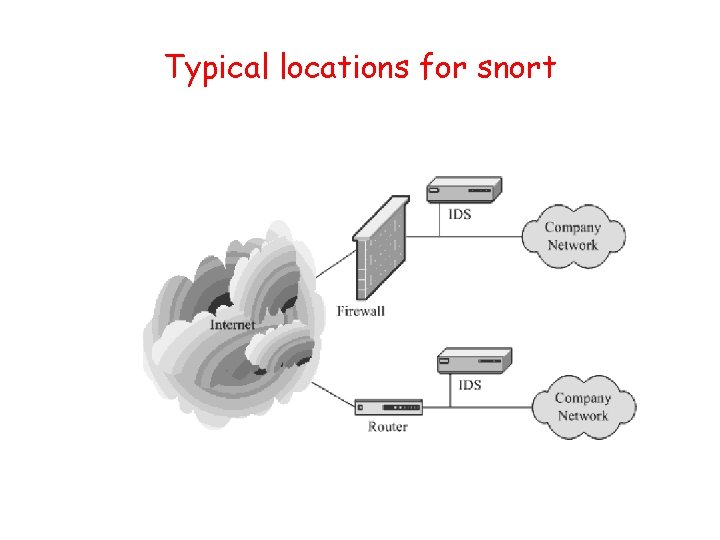
Typical locations for snort

Requirement of snort • lightweight NIDS • small, flexible • highly capable system

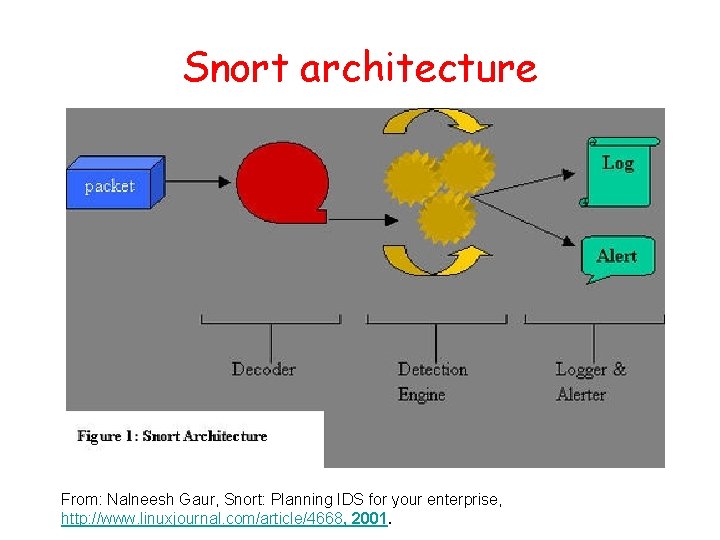
Snort architecture From: Nalneesh Gaur, Snort: Planning IDS for your enterprise, http: //www. linuxjournal. com/article/4668, 2001.

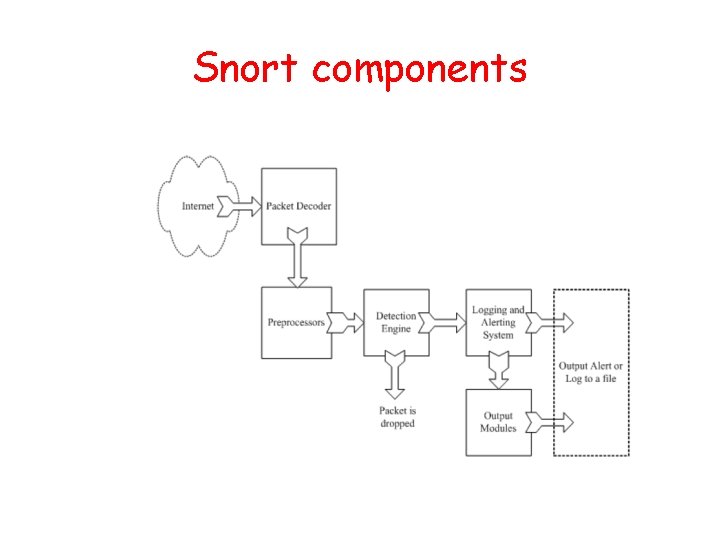
Snort components

Logical components of snort • Packet Decoder: takes packets from different types of network interfaces (Ethernet, SLIP, PPP…), prepare packets for processing • Preprocessor: (1) prepare data for detection engine; (2) detect anomalies in packet headers; (3) packet defragmentation; (4) decode HTTP URI; (5) reassemble TCP streams. • Detection Engine: the most important part, applies rules to packets • Logging and Alerting System • Output Modules: process alerts and logs and generate final output.

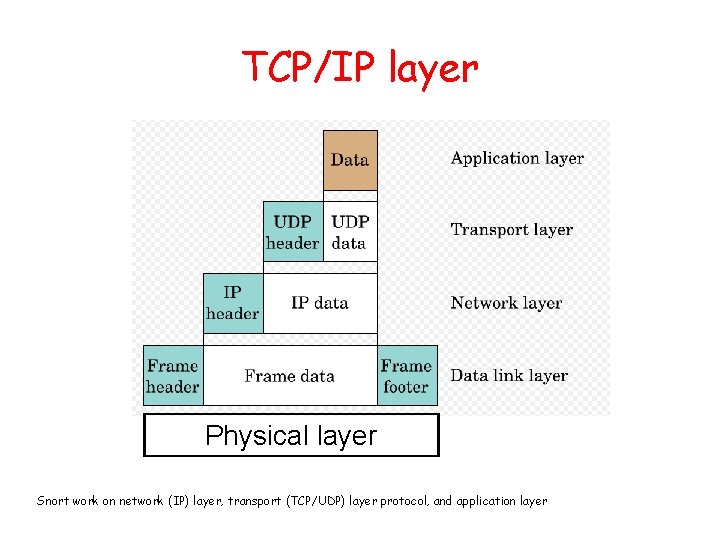
TCP/IP layer Physical layer Snort work on network (IP) layer, transport (TCP/UDP) layer protocol, and application layer

Detection Engine ※Things need to be done for detection engine: • The IP header of the packet • The transport layer header. TCP, UDP, ICMP etc. • The application layer level header. Header of DNS, FTP, SNMP, SMTP • Packet payload ※ How to do these? Apply rules to the packets using a Boyer-Moore string matching algorithm ※ Requirement 1. Time critical 2. Fast

Detection engine • Number of rules • Traffic load on the network • Speed of network and machine • Efficiency of detection algorithm

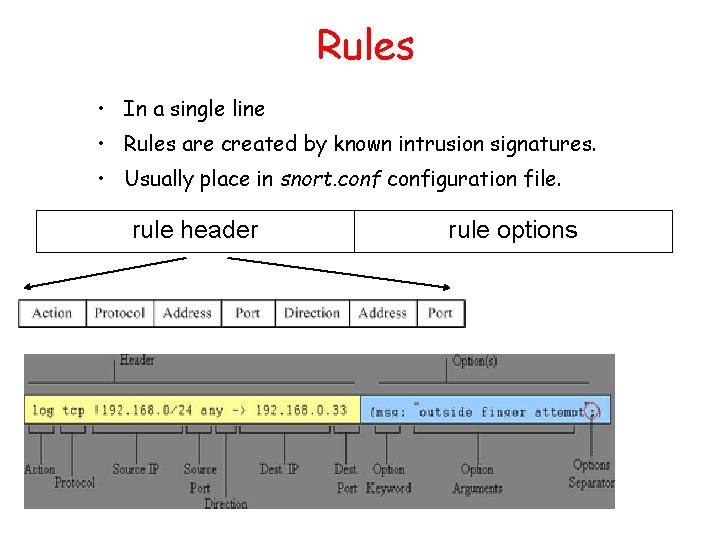
Rules • In a single line • Rules are created by known intrusion signatures. • Usually place in snort. configuration file. rule header rule options

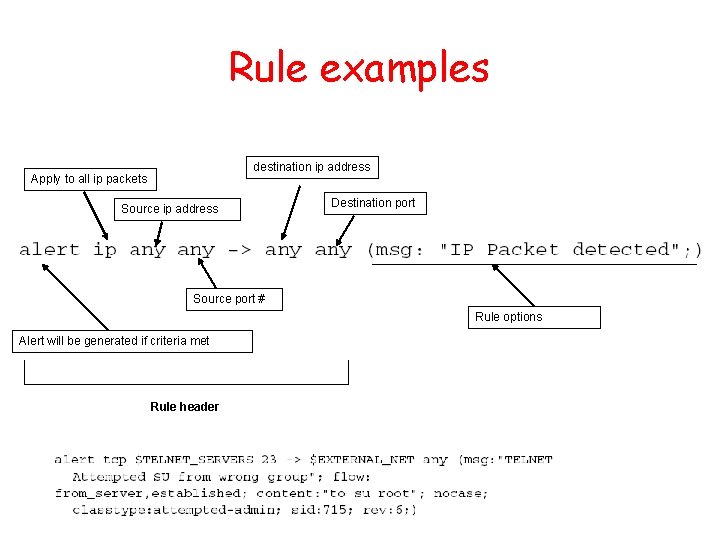
Rule examples destination ip address Apply to all ip packets Source ip address Destination port Source port # Rule options Alert will be generated if criteria met Rule header
Thank you !