Network Security r Understand principles of network security



















- Slides: 38

Network Security r Understand principles of network security: m Cryptography and its many uses beyond “confidentiality”. m Authentication. m Message integrity m Non-repudiation m Key distribution. r Security in practice: m Firewalls m Security and protocols in application, transport, network, and link layers (NAT, IPSec, SSL, Kerberos, etc) 1

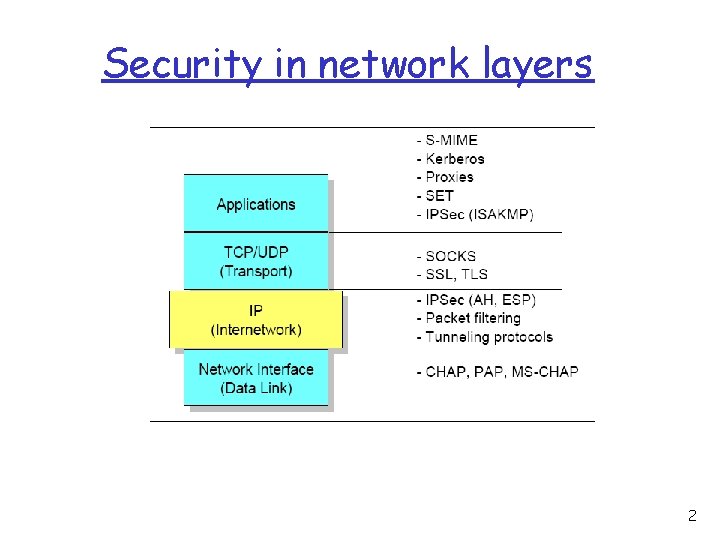
Security in network layers 2

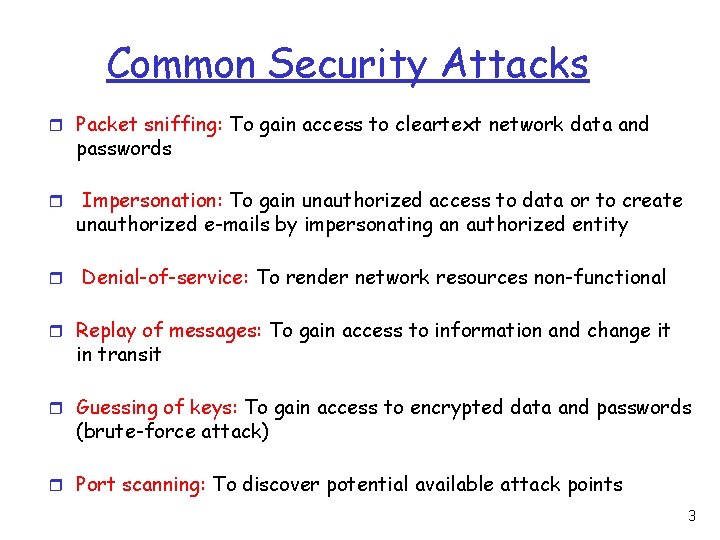
Common Security Attacks r Packet sniffing: To gain access to cleartext network data and passwords r Impersonation: To gain unauthorized access to data or to create unauthorized e-mails by impersonating an authorized entity r Denial-of-service: To render network resources non-functional r Replay of messages: To gain access to information and change it in transit r Guessing of keys: To gain access to encrypted data and passwords (brute-force attack) r Port scanning: To discover potential available attack points 3

What is Network Security? Confidentiality: only sender, intended receiver should “understand” message contents Authentication: sender, receiver want to confirm identity of each other Message Integrity: sender, receiver want to ensure message not altered without detection Non-Repudiation: being able to prove that the sender did send the message 4

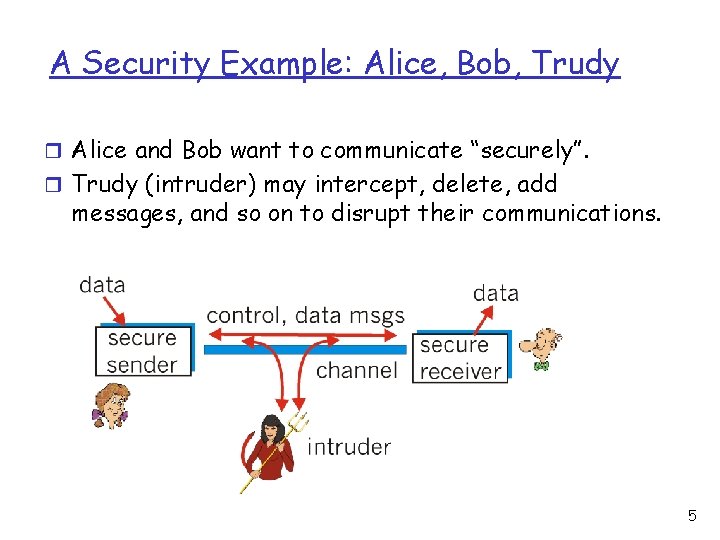
A Security Example: Alice, Bob, Trudy r Alice and Bob want to communicate “securely”. r Trudy (intruder) may intercept, delete, add messages, and so on to disrupt their communications. 5

Who Might Alice and Bob Be? r Users r Web browser/server for electronic transactions (e. g. , on-line purchases) r On-line banking client/server r DNS servers r Routers exchanging routing table updates 6

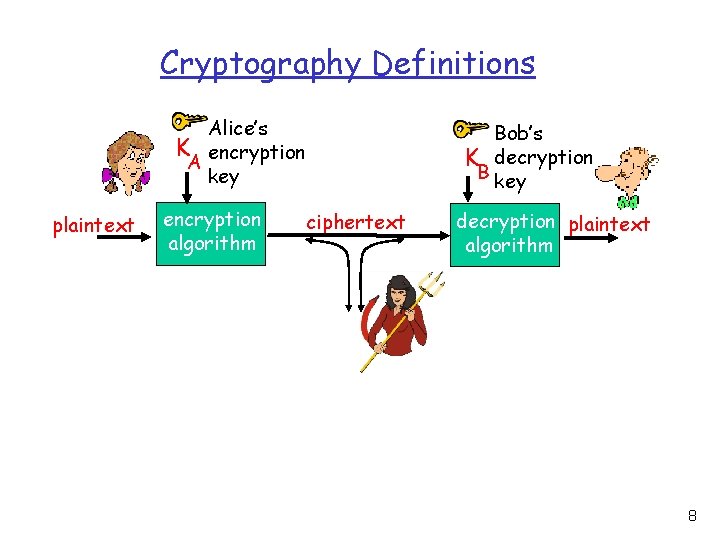
Cryptography Definitions r Encryption is a process by which a message (called plaintext) is transformed into another message (called ciphertext) using a mathematical function and a special encryption password (called a key). r Decryption is the reverse process 7

Cryptography Definitions Alice’s K encryption A key plaintext encryption algorithm Bob’s K decryption B key ciphertext decryption plaintext algorithm 8

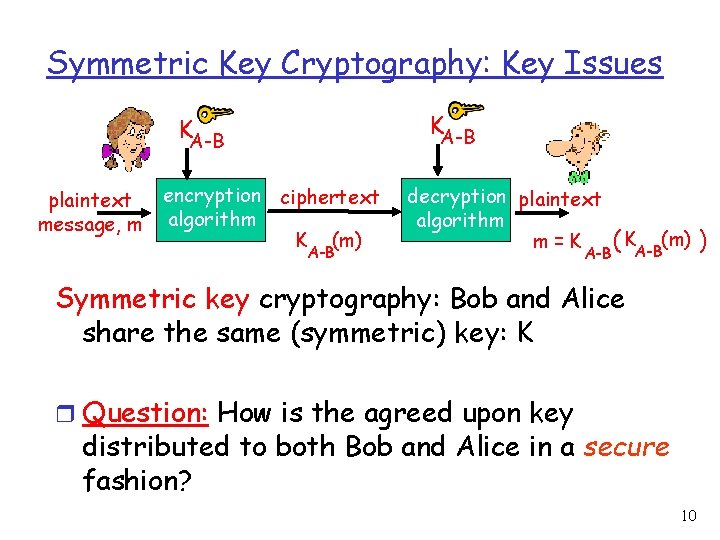
Symmetric (Secret) Key Cryptography r Same key decrypts and encrypts information. r The encryption functions used need not be secret, but the keys used must be secret r Sender and receiver must agree on the key before secured communication starts r The encryption and decryption functions used can be the same or different. 9

Symmetric Key Cryptography: Key Issues KA-B plaintext message, m encryption ciphertext algorithm K (m) A-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) Symmetric key cryptography: Bob and Alice share the same (symmetric) key: K r Question: How is the agreed upon key distributed to both Bob and Alice in a secure fashion? 10

Symmetric Key Cryptography: DES: Data Encryption Standard r US encryption standard r 56 -bit symmetric key, 64 -bit plaintext input AES: Advanced Encryption Standard r Newer (November 2001) symmetric key replacing DES. r 128, 192, or 256 bit keys, 128 -bit plaintext input r Brute force decryption (trying each key) would take 1 second on DES, but would take 149 trillion years for AES. IDEA: International Data Encryption Algorithm q 64 -bit input, 128 -bit keys q Stronger, more efficient than DES. 11

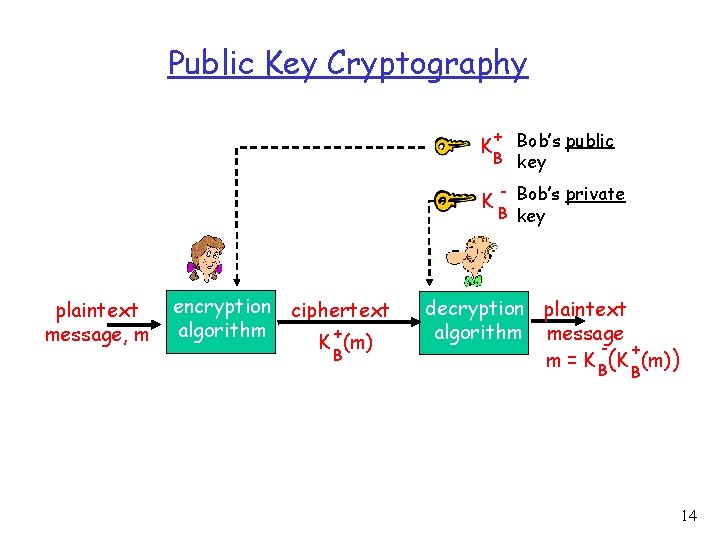
Public Key Cryptography Symmetric key cryptography r Requires both the sender and receiver to know the shared secret key. r Question: how do they agree on the key in the first place (particularly if they have never “met”)? Public key cryptography r Sender and receiver do not share secret key. r Public encryption key known to all. r Private decryption key known only by the owner. 12

Public (Assymetric) Key Cryptography r Keys are generated in pairs. m Public key is publicly registered so everyone knows it, and private one is kept secret by the owner. m Each key can decrypt what the other encrypts, but not what it encrypts itself. Important properties of key generation: m There is a one-to-one correspondence in the generated key pairs – if one key can decrypt a message, it must have been encrypted by the other. m It must be extremely difficult, if not impossible, to deduce the private key when given a public key. 13

Public Key Cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B 14

Public Key Encryption Algorithms r Diffie-Hellman: the first public key approach proposed. r RSA: the best known public key system, developed by Rivest, Shamir, and Adleman (hence RSA). r DSA: Digital Signature Algorithm, developed by the U. S. National Security Agency (NSA). 15

Symmetric vs. Public Key Cryptography Which method provides stronger security? Which method is more convenient? Which method performs better? r Ideally, we would like to combine the strengths of symmetric and public key cryptography, and avoid their weaknesses: We want the efficiency of symmetric cryptography combined with the ease of use and convenience of public key cryptography. 16

Hybrid Secret-Public Key Cryptography r When two parties want to communicate securely, public key cryptography is used to exchange a random symmetric session key. r To communicate, symmetric cryptography is used with the session key. r When done, both parties destroy the session key. 17

Hash functions/Message Digests r Message digest is a special kind of checksum produced using cryptographic means. r Typically produced from a one-way hash function that is difficult to reverse or predict. r This function takes the entire input and reduces it to a small value of fixed length, typically 128 to 512 bits in length. r Must be collision-resistant: must be difficult for 2 messages to produce the same digest r Encrypted hash (MAC) is used to ensure authentication and integrity 18

Message Digests: Hash Function Algorithms r MD 5 hash function widely used r SHA-1 is also used. r Issues in both MD 5 and SHA-1 have been found in recent years though m These algorithms are now being phased out more quickly in favour of other, newer approaches like SHA-2. 19

Authentication and Integrity r Authentication is the process of proving one’s identity to someone else. r There are three main ways of authenticating an individual: m Something you know m Something you own m Something you are r Message integrity: ensuring that a message not altered without detection. 20

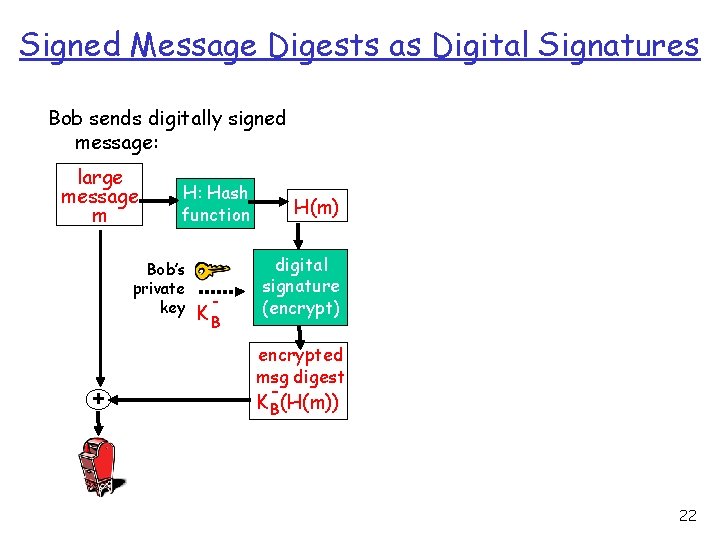
Digital Signatures We would like to have a cryptographic technique analogous to hand-written signatures. r This digital signature is verifiable and not forgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed the document. r Hash encrypted by a private key is a digital signature that is then attached to the original message r By signing only the digest, we have the same level of security, as the digest is tied to the message, with less encryption and decryption overhead. 21

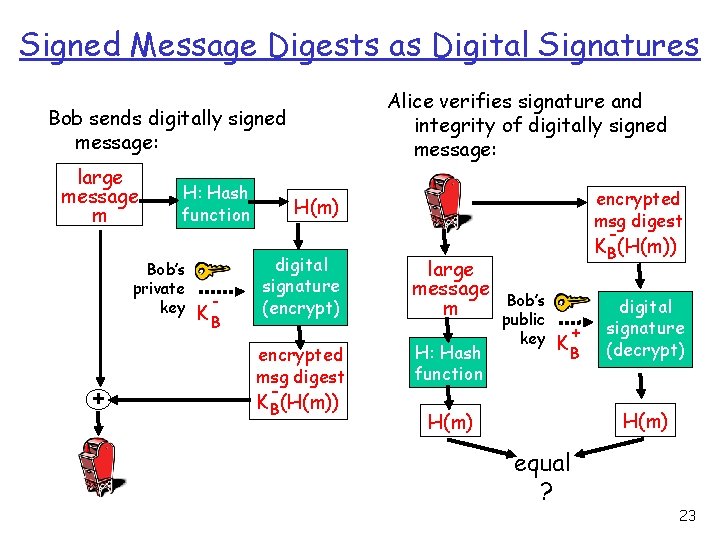
Signed Message Digests as Digital Signatures Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) 22

Signed Message Digests as Digital Signatures Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: Hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 23

Certification Authorities r With public key cryptography there’s a danger of a “man-in-the-middle attacks” r How do we make sure that a particular public key belongs to a certain entity? r How can we avoid impersonation? r The International Telecommunication Union (ITU) specifies an authentication service and specific syntax for certificates in X. 509. 24

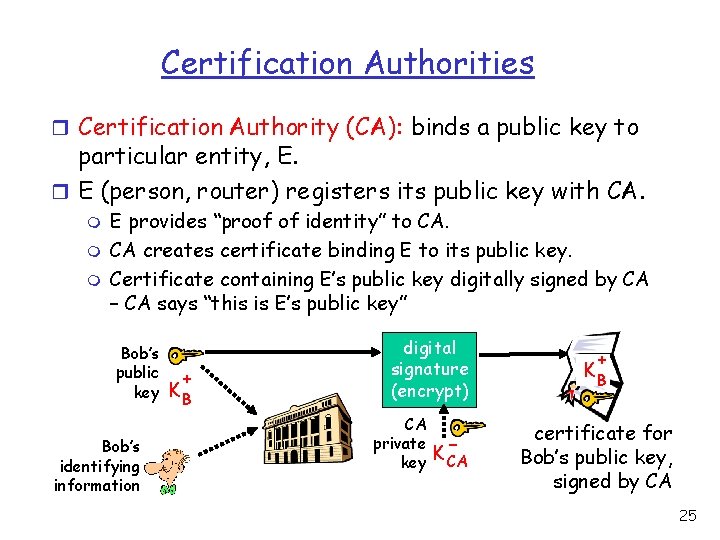
Certification Authorities r Certification Authority (CA): binds a public key to particular entity, E. r E (person, router) registers its public key with CA. m m m E provides “proof of identity” to CA. CA creates certificate binding E to its public key. Certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA 25

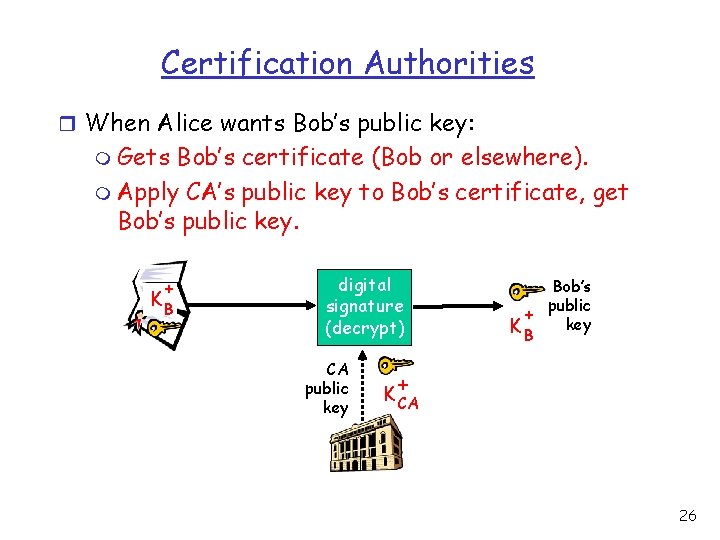
Certification Authorities r When Alice wants Bob’s public key: m Gets Bob’s certificate (Bob or elsewhere). m Apply CA’s public key to Bob’s certificate, get Bob’s public key. + KB digital signature (decrypt) CA public key Bob’s public + key KB + K CA 26

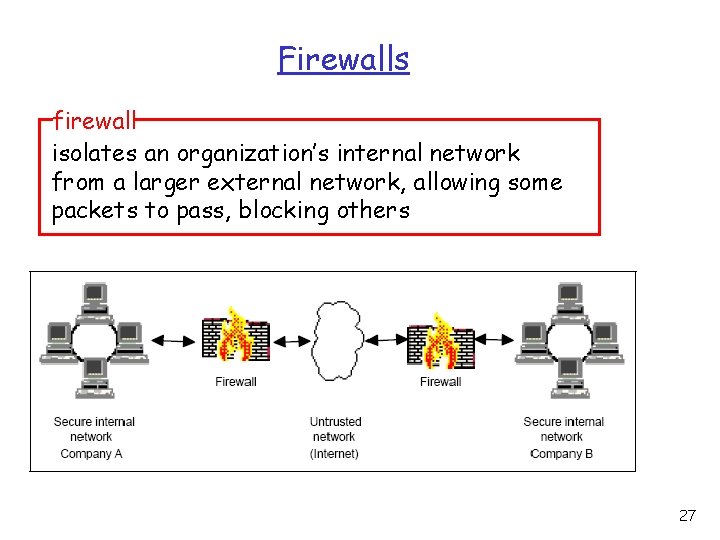
Firewalls firewall isolates an organization’s internal network from a larger external network, allowing some packets to pass, blocking others 27

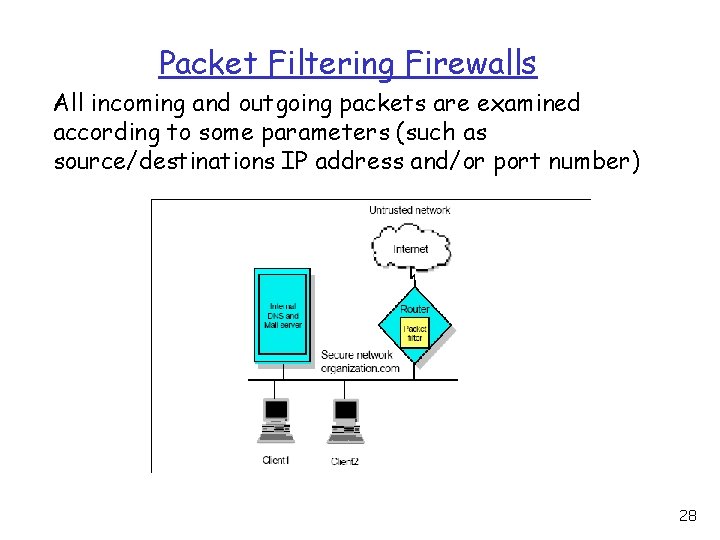
Packet Filtering Firewalls All incoming and outgoing packets are examined according to some parameters (such as source/destinations IP address and/or port number) 28

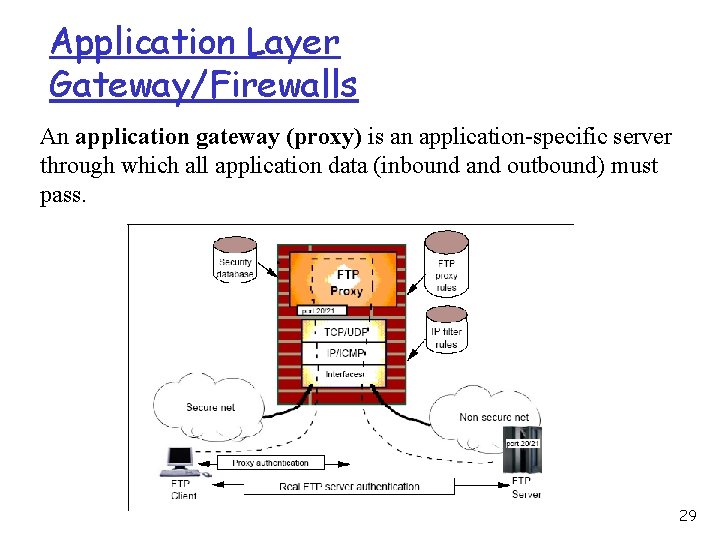
Application Layer Gateway/Firewalls An application gateway (proxy) is an application-specific server through which all application data (inbound and outbound) must pass. 29

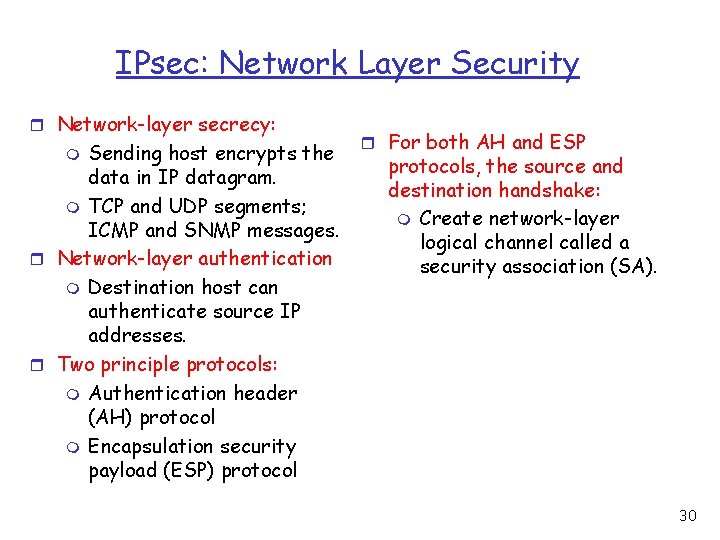
IPsec: Network Layer Security r Network-layer secrecy: Sending host encrypts the data in IP datagram. m TCP and UDP segments; ICMP and SNMP messages. r Network-layer authentication m Destination host can authenticate source IP addresses. r Two principle protocols: m Authentication header (AH) protocol m Encapsulation security payload (ESP) protocol m r For both AH and ESP protocols, the source and destination handshake: m Create network-layer logical channel called a security association (SA). 30

Authentication Header (AH) Protocol r Provides source authentication, data integrity, but not confidentiality. r AH header inserted between IP header, data field. IP header AH header data (e. g. , TCP, UDP segment) 31

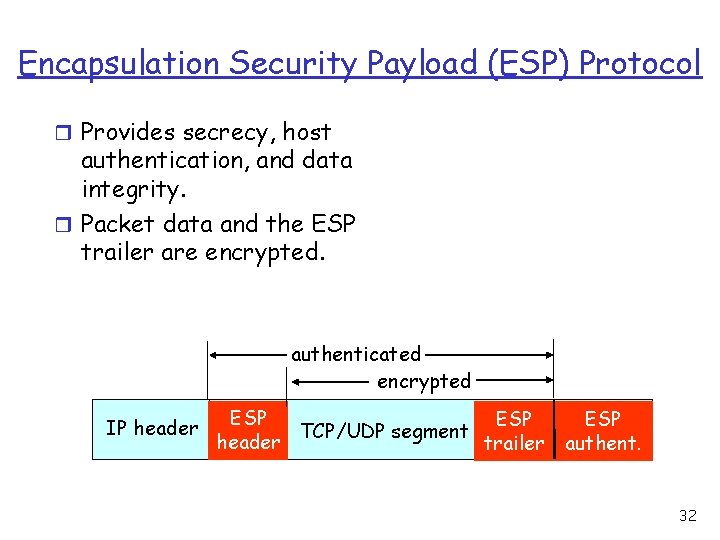
Encapsulation Security Payload (ESP) Protocol r Provides secrecy, host authentication, and data integrity. r Packet data and the ESP trailer are encrypted. authenticated encrypted IP header ESP TCP/UDP segment header trailer ESP authent. 32

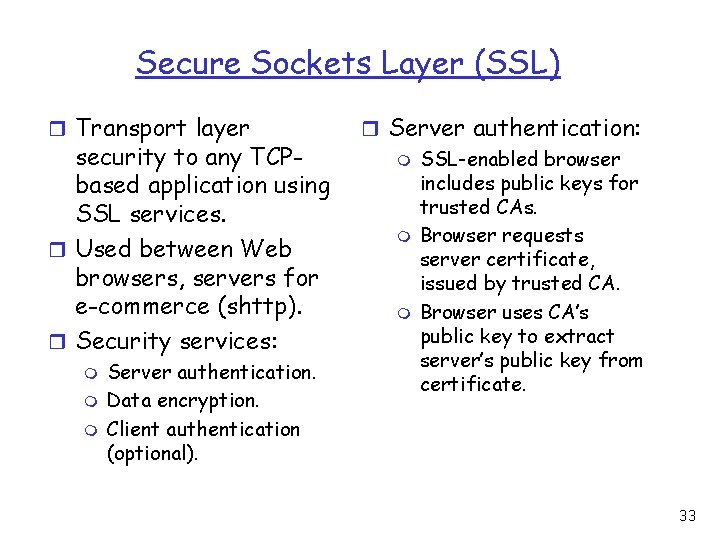
Secure Sockets Layer (SSL) r Transport layer security to any TCPbased application using SSL services. r Used between Web browsers, servers for e-commerce (shttp). r Security services: m m m Server authentication. Data encryption. Client authentication (optional). r Server authentication: m SSL-enabled browser includes public keys for trusted CAs. m Browser requests server certificate, issued by trusted CA. m Browser uses CA’s public key to extract server’s public key from certificate. 33

SSL (Continued) Encrypted SSL session: r Browser generates symmetric session key, encrypts it with server’s public key, sends encrypted key to server. r Using private key, server decrypts session key. r Only the browser and server know session key. m r SSL can be used for non-Web applications, e. g. , IMAP. r Client authentication can be done with client certificates which have also been issued by CAs. r SSL serves as a basis for TLS protocol All data sent into TCP socket (by client or server) encrypted with session key. 34

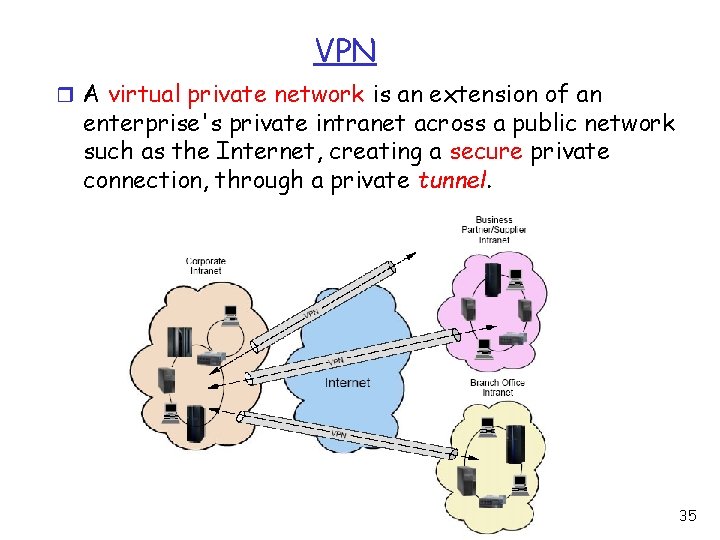
VPN r A virtual private network is an extension of an enterprise's private intranet across a public network such as the Internet, creating a secure private connection, through a private tunnel. 35

Kerberos r an encryption-based security system that provides mutual authentication between the users and the servers in a network environment. r Authorization can be implemented independently from the authentication r a ticket-granting server (key distribution center) acts as a mutually trusted third party 36

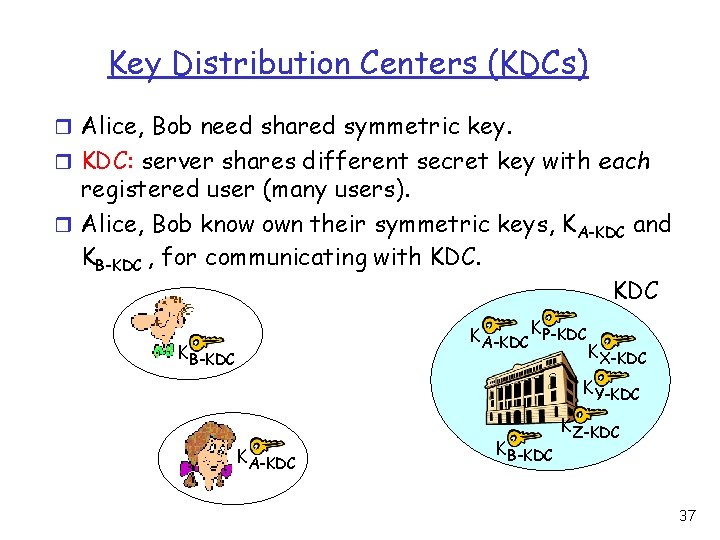
Key Distribution Centers (KDCs) r Alice, Bob need shared symmetric key. r KDC: server shares different secret key with each registered user (many users). r Alice, Bob know own their symmetric keys, KA-KDC and KB-KDC , for communicating with KDC KA-KDC KP-KDC KB-KDC KX-KDC KY-KDC KA-KDC KB-KDC KZ-KDC 37

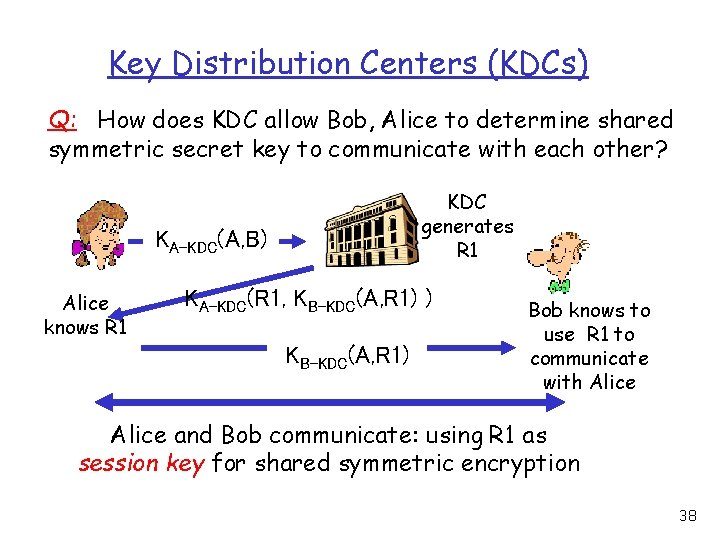
Key Distribution Centers (KDCs) Q: How does KDC allow Bob, Alice to determine shared symmetric secret key to communicate with each other? KDC generates R 1 KA-KDC(A, B) Alice knows R 1 KA-KDC(R 1, KB-KDC(A, R 1) ) KB-KDC(A, R 1) Bob knows to use R 1 to communicate with Alice and Bob communicate: using R 1 as session key for shared symmetric encryption 38