Network Control Sukiswo sukiswokyahoo com Manajemen Jaringan Sukiswo





- Slides: 13

Network Control Sukiswo sukiswok@yahoo. com Manajemen Jaringan, Sukiswo ST, MT 1

Table of Contents 4 Introduction 4 Configuration Control 4 Security Control Manajemen Jaringan, Sukiswo ST, MT 2

Introduction 4 Network control is concerned with modifying parameters in and causing actions to be taken by the end systems, intermediate systems, and subnetworks that make up the network to be managed 4 All five functional areas of NM involve monitoring and control but configuration and security are more concerned with control 4 Issues in network control – what to control? • define what is to be controlled – how to control? • how to cause actions to be performed Manajemen Jaringan, Sukiswo ST, MT 3

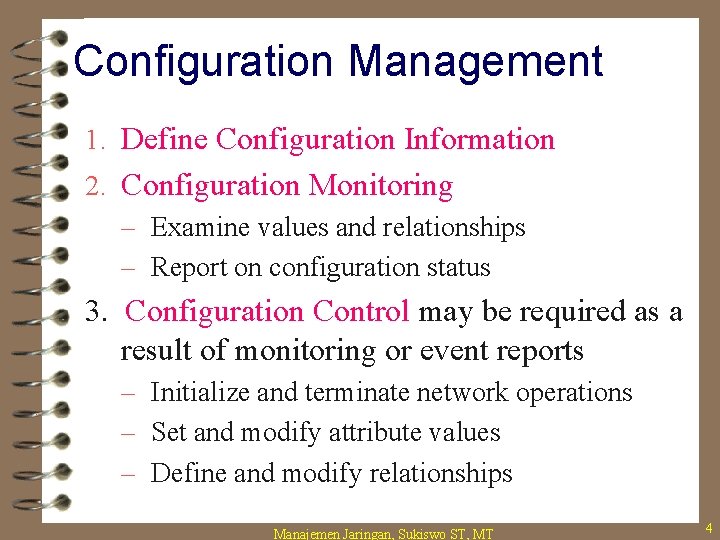
Configuration Management 1. Define Configuration Information 2. Configuration Monitoring – Examine values and relationships – Report on configuration status 3. Configuration Control may be required as a result of monitoring or event reports – Initialize and terminate network operations – Set and modify attribute values – Define and modify relationships Manajemen Jaringan, Sukiswo ST, MT 4

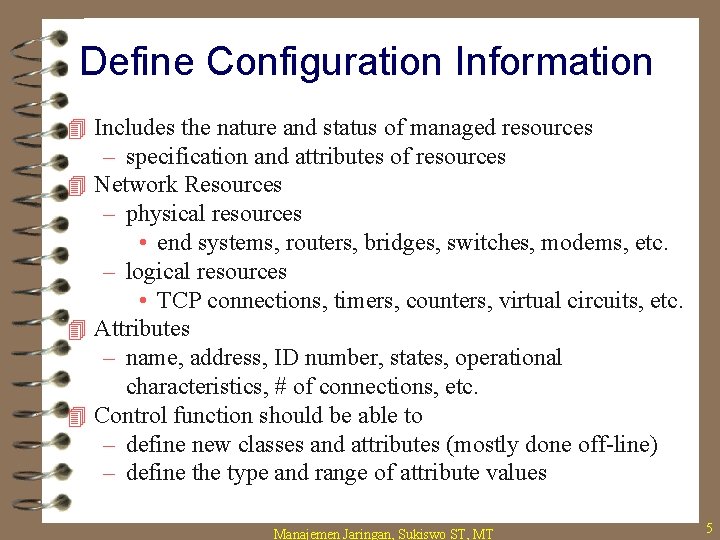
Define Configuration Information 4 Includes the nature and status of managed resources – specification and attributes of resources 4 Network Resources – physical resources • end systems, routers, bridges, switches, modems, etc. – logical resources • TCP connections, timers, counters, virtual circuits, etc. 4 Attributes – name, address, ID number, states, operational characteristics, # of connections, etc. 4 Control function should be able to – define new classes and attributes (mostly done off-line) – define the type and range of attribute values Manajemen Jaringan, Sukiswo ST, MT 5

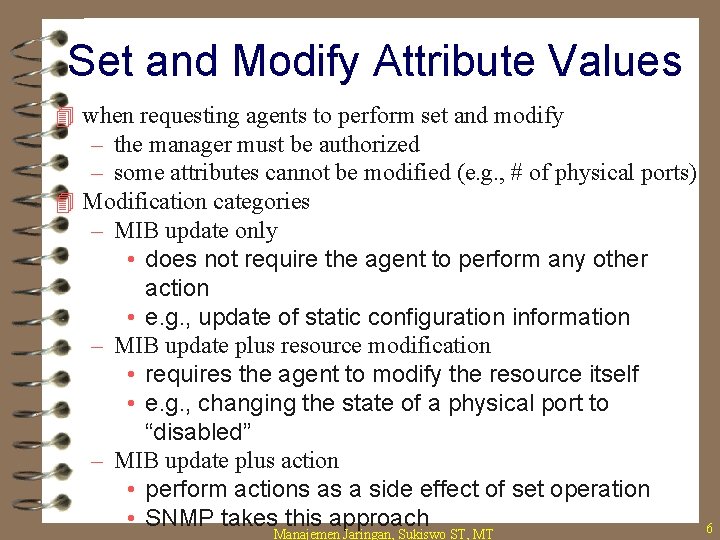
Set and Modify Attribute Values 4 when requesting agents to perform set and modify – the manager must be authorized – some attributes cannot be modified (e. g. , # of physical ports) 4 Modification categories – MIB update only • does not require the agent to perform any other action • e. g. , update of static configuration information – MIB update plus resource modification • requires the agent to modify the resource itself • e. g. , changing the state of a physical port to “disabled” – MIB update plus action • perform actions as a side effect of set operation • SNMP takes this approach Manajemen Jaringan, Sukiswo ST, MT 6

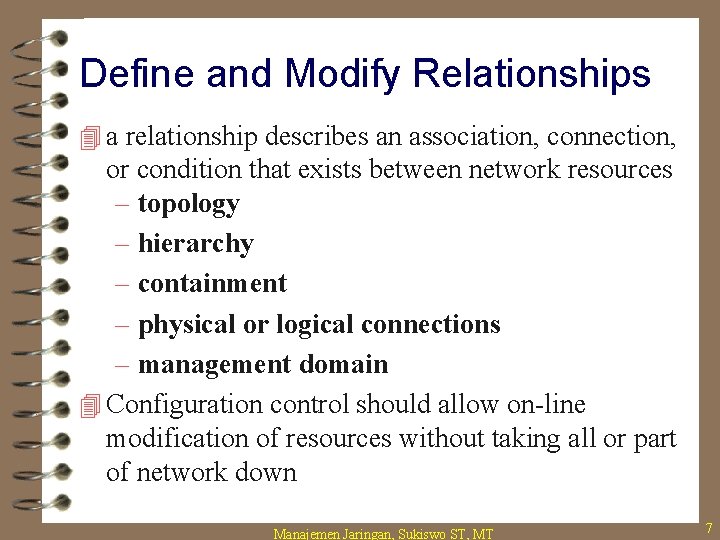
Define and Modify Relationships 4 a relationship describes an association, connection, or condition that exists between network resources – topology – hierarchy – containment – physical or logical connections – management domain 4 Configuration control should allow on-line modification of resources without taking all or part of network down Manajemen Jaringan, Sukiswo ST, MT 7

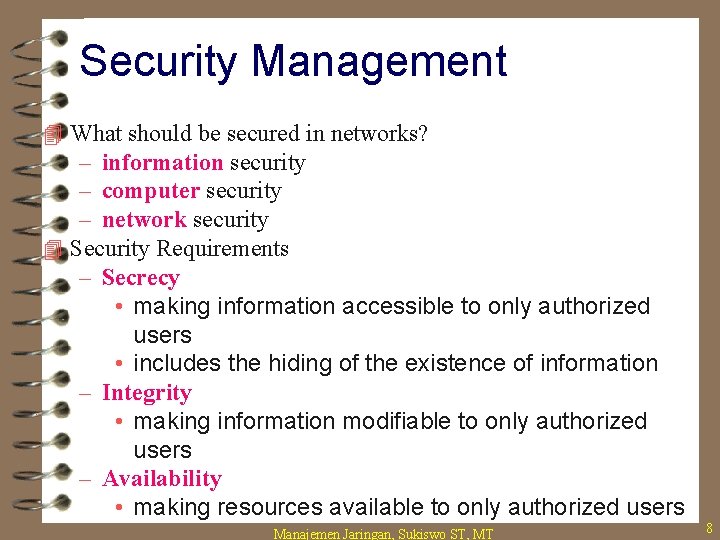
Security Management 4 What should be secured in networks? – information security – computer security – network security 4 Security Requirements – Secrecy • making information accessible to only authorized users • includes the hiding of the existence of information – Integrity • making information modifiable to only authorized users – Availability • making resources available to only authorized users Manajemen Jaringan, Sukiswo ST, MT 8

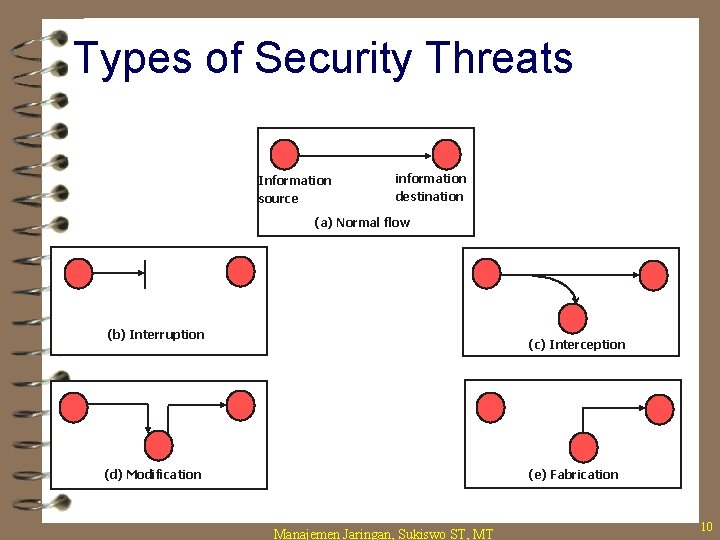
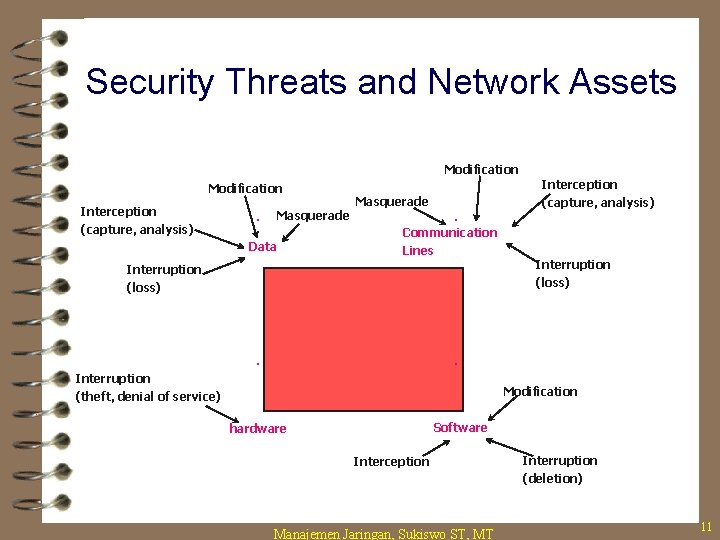
Security Threats 4 Interruption – destroyed or becomes unavailable or unusable – threat to “availability” 4 Interception – an unauthorized party gains access – threat to “secrecy” 4 Modification – an unauthorized party makes modification – threat to “integrity” 4 Fabrication – an unauthorized party inserts false information 4 Masquerade – an entity pretends to be a different entity Manajemen Jaringan, Sukiswo ST, MT 9

Types of Security Threats Information source information destination (a) Normal flow (b) Interruption (c) Interception (d) Modification (e) Fabrication Manajemen Jaringan, Sukiswo ST, MT 10

Security Threats and Network Assets Modification Interception (capture, analysis) . Masquerade Data Masquerade. Communication Lines Interception (capture, analysis) Interruption (loss) . . Interruption (theft, denial of service) Modification Software hardware Interception Manajemen Jaringan, Sukiswo ST, MT Interruption (deletion) 11

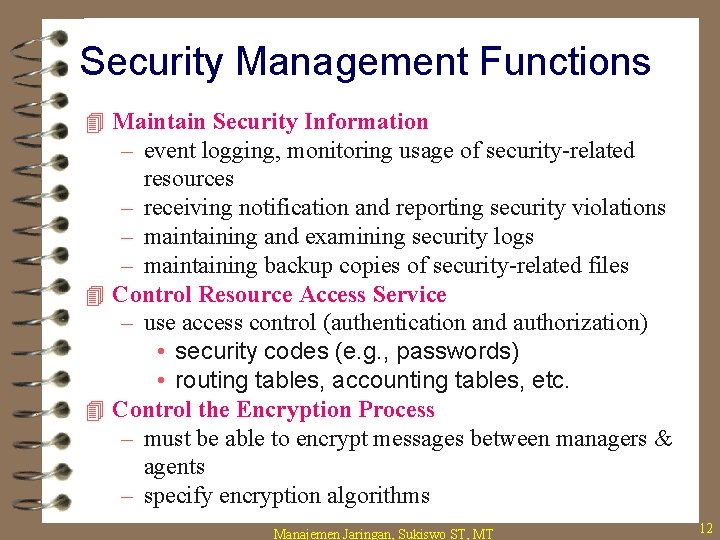
Security Management Functions 4 Maintain Security Information – event logging, monitoring usage of security-related resources – receiving notification and reporting security violations – maintaining and examining security logs – maintaining backup copies of security-related files 4 Control Resource Access Service – use access control (authentication and authorization) • security codes (e. g. , passwords) • routing tables, accounting tables, etc. 4 Control the Encryption Process – must be able to encrypt messages between managers & agents – specify encryption algorithms Manajemen Jaringan, Sukiswo ST, MT 12

Summary 4 Network control is concerned with setting and changing parameters of various parts of network resources as consequences of network monitoring and analysis 4 Configuration control and security control are two essential aspects of network control 4 READ Chapter 3 of Textbook Manajemen Jaringan, Sukiswo ST, MT 13
 Dậy thổi cơm mua thịt cá
Dậy thổi cơm mua thịt cá Cơm
Cơm Aoncas
Aoncas Alat perkembangbiakan pada bunga
Alat perkembangbiakan pada bunga Jaringan meristem
Jaringan meristem Meristem
Meristem Jaringan hopfield digunakan untuk tipe jaringan
Jaringan hopfield digunakan untuk tipe jaringan Fungsi dan cara kerja jaringan telekomunikasi
Fungsi dan cara kerja jaringan telekomunikasi Teori haberlandt
Teori haberlandt Apakah yang dimaksud manajemen jaringan persediaan
Apakah yang dimaksud manajemen jaringan persediaan Ruang lingkup manajemen data kesehatan
Ruang lingkup manajemen data kesehatan Hubungan manajemen persediaan dengan manajemen keuangan
Hubungan manajemen persediaan dengan manajemen keuangan Manajemen informasi dan manajemen internasional
Manajemen informasi dan manajemen internasional Manajemen usaha kecil dan manajemen organisasi nirlaba
Manajemen usaha kecil dan manajemen organisasi nirlaba