MIST An Efficient Randomized Exponentiation Algorithm for Resisting








- Slides: 18

MIST: An Efficient, Randomized Exponentiation Algorithm for Resisting Power Analysis Colin D. Walter formerly: www. co. umist. ac. uk (Manchester, UK) c. walter@umist. ac. uk now: www. comodo. net (Bradford, UK) colin@comodo. net RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Power Analysis Attacks • With no counter-measures and the binary expn algm, averaging power traces at the same instants during several expns enables one to differentiate squares and multiplies and hence deduce the exponent bits. • Averaging power traces over individual digit-by-digit products in a single expn enables one to differentiate mutliplicands in m-ary expn and hence deduce the exponent. • Smartcards have limited scope for including expensive, tamper-resistant, hardware measures. • Good software counter-measures are required: new algorithms as well as modifying arguments e. g. E to E+r (M). RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Requirements for Exponentiation • New algorithm, not new inputs, as single expn may be attacked. • Different pattern of Squares and Multiplies to frustrate averaging. • No re-use of multiplicands (same reason) • No fully determined tie between Square or Multiply and known process. • Good time and space efficiency RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

History • T. S. Messerges, E. A. Dabbish & R. H. Sloan Power Analysis Attacks of Modular Exponentiation in Smartcards CHES 99 , LNCS 1717 • E. Oswald & M. Aigner Randomized Addition-Subtraction Chains as a Countermeasure against Power Attacks CHES 2001, LNCS 2162 • C. D. Walter Exponentiation using Division Chains IEEE TC 47, 1998, pp 757– 765 RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

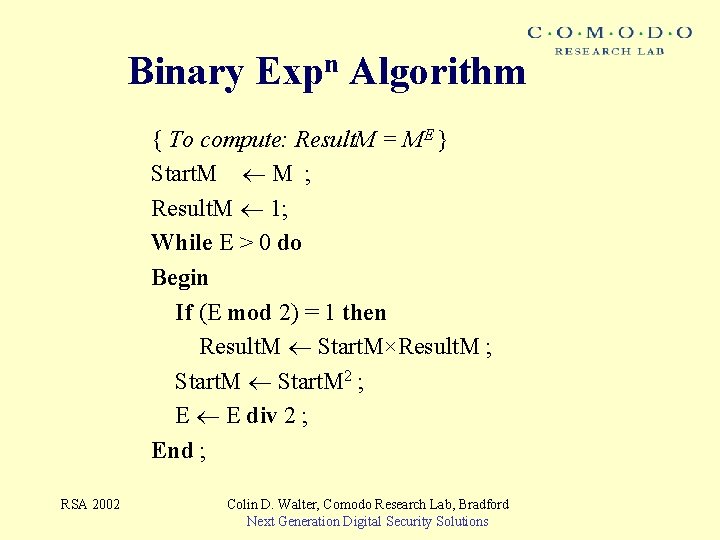
Binary Expn Algorithm { To compute: Result. M = ME } Start. M M ; Result. M 1; While E > 0 do Begin If (E mod 2) = 1 then Result. M Start. M×Result. M ; Start. M 2 ; E E div 2 ; End ; RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

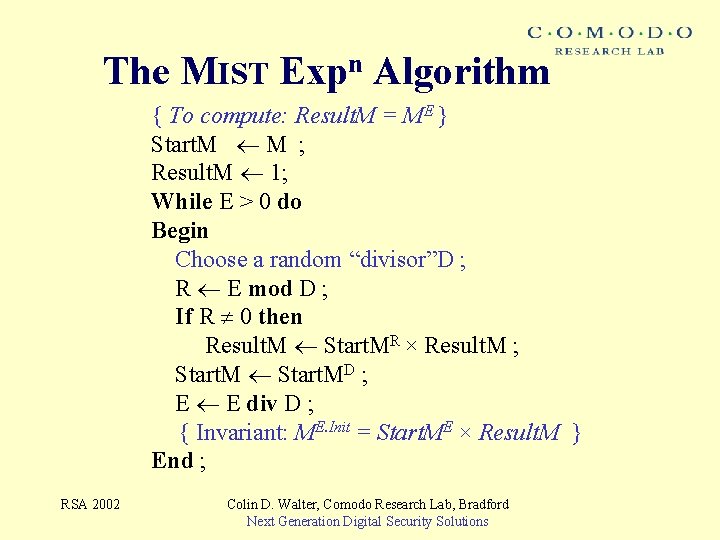
The MIST Expn Algorithm { To compute: Result. M = ME } Start. M M ; Result. M 1; While E > 0 do Begin Choose a random “divisor”D ; R E mod D ; If R 0 then Result. M Start. MR × Result. M ; Start. MD ; E E div D ; { Invariant: ME. Init = Start. ME × Result. M } End ; RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

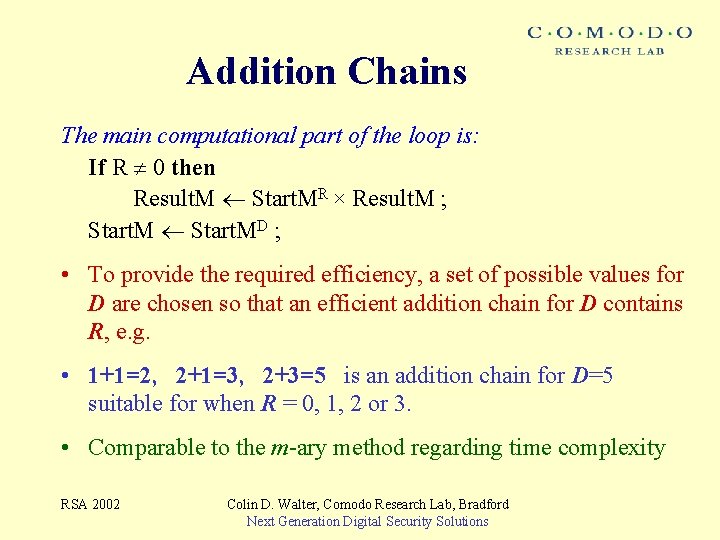
Addition Chains The main computational part of the loop is: If R 0 then Result. M Start. MR × Result. M ; Start. MD ; • To provide the required efficiency, a set of possible values for D are chosen so that an efficient addition chain for D contains R, e. g. • 1+1=2, 2+1=3, 2+3=5 is an addition chain for D=5 suitable for when R = 0, 1, 2 or 3. • Comparable to the m-ary method regarding time complexity RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

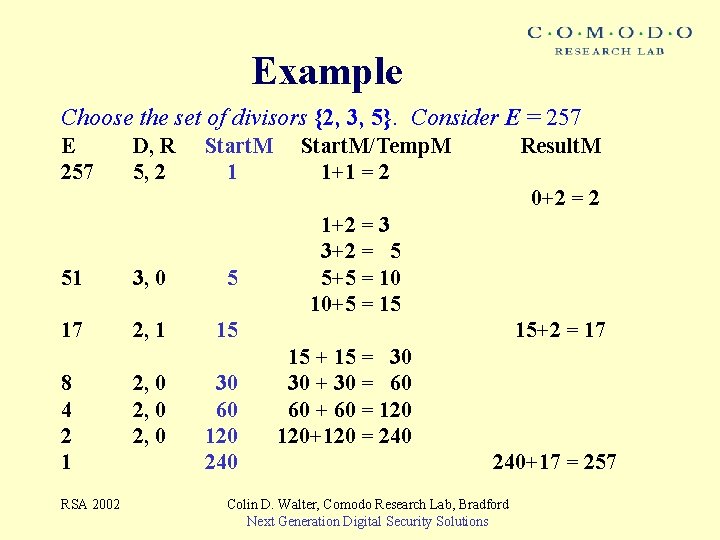
Example Choose the set of divisors {2, 3, 5}. Consider E = 257 E 257 D, R 5, 2 Start. M 1 Start. M/Temp. M 1+1 = 2 Result. M 0+2 = 2 51 3, 0 5 17 2, 1 15 8 4 2 1 RSA 2002 2, 0 30 60 120 240 1+2 = 3 3+2 = 5 5+5 = 10 10+5 = 15 15+2 = 17 15 + 15 = 30 30 + 30 = 60 60 + 60 = 120+120 = 240+17 = 257 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Choice of Divisor Set • Security: Divisors must be chosen so that sequences of squares and multiplies do not reveal D. • Efficiency: – Divisors must be chosen so that raising to the power D is (time) efficient enough. – Space is required to store addition chains. – As few registers as possible should be used for the exponentiation. • Solution: Take the set of divisors {2, 3, 5}. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

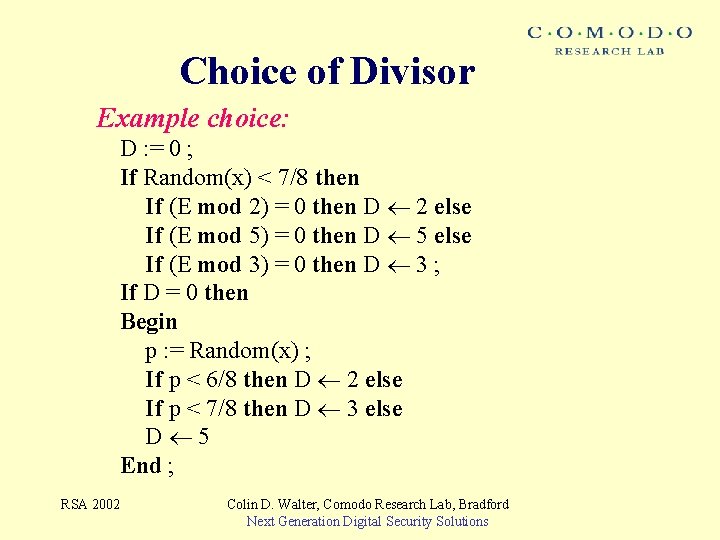
Choice of Divisor Example choice: D : = 0 ; If Random(x) < 7/8 then If (E mod 2) = 0 then D 2 else If (E mod 5) = 0 then D 5 else If (E mod 3) = 0 then D 3 ; If D = 0 then Begin p : = Random(x) ; If p < 6/8 then D 2 else If p < 7/8 then D 3 else D 5 End ; RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Choice of Divisor – Choosing D when E 0 mod D is efficient because it avoids a multiplication by Start. MR. – Choosing such D deterministically is unsafe, so they should not be chosen always. – Some pairs (D, R) require fewer multiplications per than others per bit of reduction in the size of E. We should choose the more efficient ones more frequently. – The published paper gives some details on ordering them. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

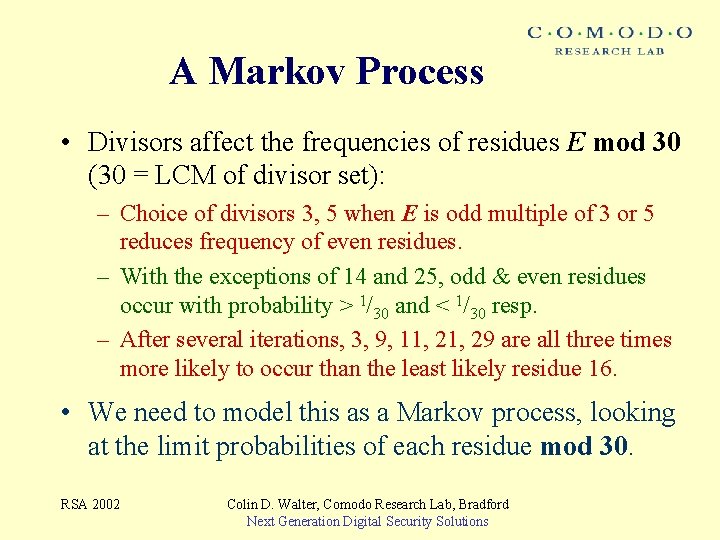
A Markov Process • Divisors affect the frequencies of residues E mod 30 (30 = LCM of divisor set): – Choice of divisors 3, 5 when E is odd multiple of 3 or 5 reduces frequency of even residues. – With the exceptions of 14 and 25, odd & even residues occur with probability > 1/30 and < 1/30 resp. – After several iterations, 3, 9, 11, 29 are all three times more likely to occur than the least likely residue 16. • We need to model this as a Markov process, looking at the limit probabilities of each residue mod 30. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

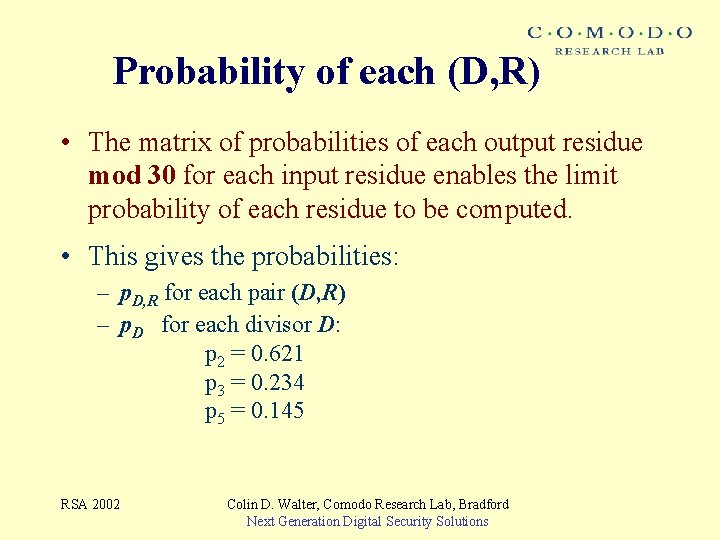
Probability of each (D, R) • The matrix of probabilities of each output residue mod 30 for each input residue enables the limit probability of each residue to be computed. • This gives the probabilities: – p. D, R for each pair (D, R) – p. D for each divisor D: p 2 = 0. 621 p 3 = 0. 234 p 5 = 0. 145 RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Avage Addn Chain Properties • The probabilities of addition sub-chain lengths are: – – • • length 1 is p 2, 0 = 0. 350 length 2 is p 3, 0 + p 2, 1 = 0. 460 length 3 is p 5, 0 + p 3, 1 + p 3, 2 = 0. 143 length 4 is p 5, 1 + p 5, 2 + p 5, 3 + p 5, 4 = 0. 047 So average divisor sub-chain has length 1. 887 mults Av decrease in E is 2 p 23 p 35 p 5 = 2. 512 per subchain So 0. 75 log 2 E subchains & 1. 42 log 2 E mults This is faster than the binary expn algorithm and marginally slower than 4 -ary expn RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

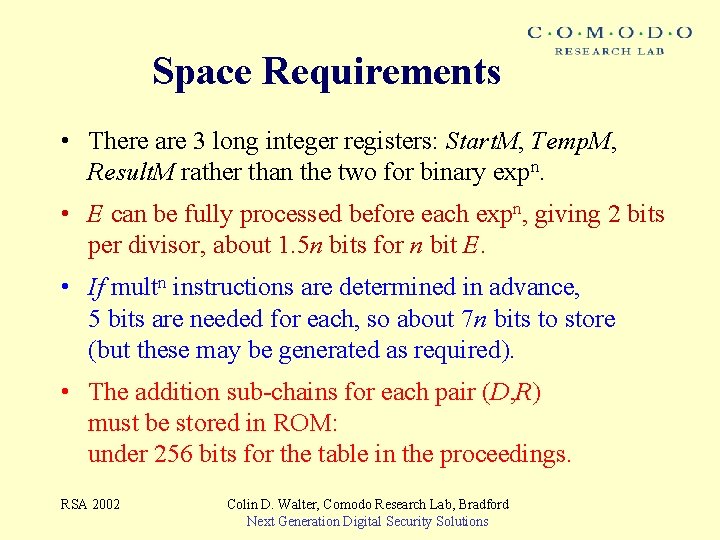
Space Requirements • There are 3 long integer registers: Start. M, Temp. M, Result. M rather than the two for binary expn. • E can be fully processed before each expn, giving 2 bits per divisor, about 1. 5 n bits for n bit E. • If multn instructions are determined in advance, 5 bits are needed for each, so about 7 n bits to store (but these may be generated as required). • The addition sub-chains for each pair (D, R) must be stored in ROM: under 256 bits for the table in the proceedings. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Other Processing Apart from the long integer multiplicative operations, processing includes: • Generation of random numbers: 33/5 bits per divisor, or 3 n bits for exponents of n bits. • Divisions of E by D: equivalent to a few long integer multiplications overall. • With three registers rather than the two for the binary algm, data movement is greater but still insignificant overall: at most one new value needs to be fetched from/ written to memory for each multiplication. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Data Leakage • MIST prevents the usual power trace averaging associated with power analysis attacks, but: • The sequence of Squares and Mults parses in too many ways to enable pairs (D, R) to be recovered: (2, 1) & (3, 0) are the same. • Making deterministic choices for D is poor practice: they may provide a handle to distinguish between correct and incorrect keys. • Processing of E and choosing of divisors must be well hidden: computing E div D may leak. It is much shorter than a long integer multiplication, so should leak much less. Don’t do it after processing the long integer mults of the previous divisor. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions

Conclusion • A novel exponentiation algorithm has been presented for which random choices make averaging for DPA impossible. • The speed is comparable to 4 -ary expn. • The space requirements comparable. • Areas of security concern have been narrowed. RSA 2002 Colin D. Walter, Comodo Research Lab, Bradford Next Generation Digital Security Solutions