Mandatory Access Control Multilevel Security MLS MLS needed





- Slides: 16

Mandatory Access Control

Multilevel Security (MLS) • MLS needed when subjects/objects at different levels access the same system • MLS is a form of Access Control • Military and Government interest in MLS for many decades – Lots of research into MLS – Strengths and weaknesses of MLS well understood (almost entirely theoretical) – Many possible uses of MLS outside military

MLS Applications • Classified Government/Military systems • Business example: info restricted to – Senior Management only, – All Management, – Everyone in company, or – General public • Network firewall • Confidential medical info, databases, etc. • Usually, MLS are not really a technical system – More like part of a legal structure

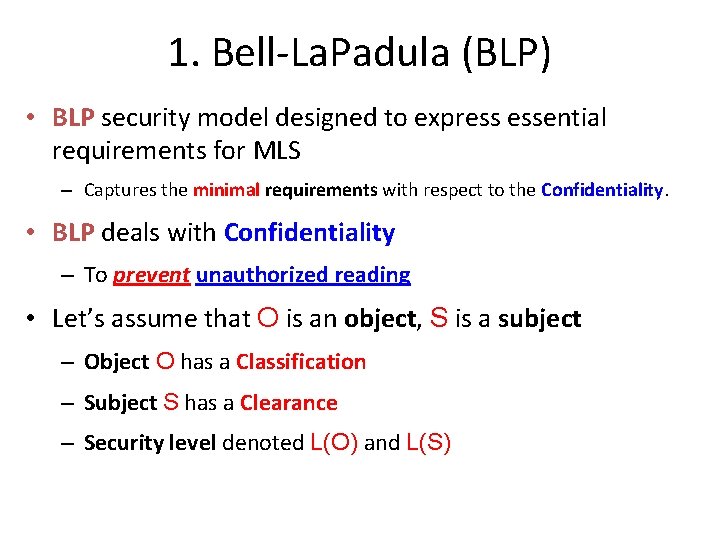
MLS Security Models • MLS models explain what needs to be done • Models do not tell you how to implement • Models are descriptive, not prescriptive – That is, high-level description, not an algorithm • There are many MLS models • We’ll discuss simplest MLS model – Other models are more complex, more difficult to enforce, harder to verify, etc.

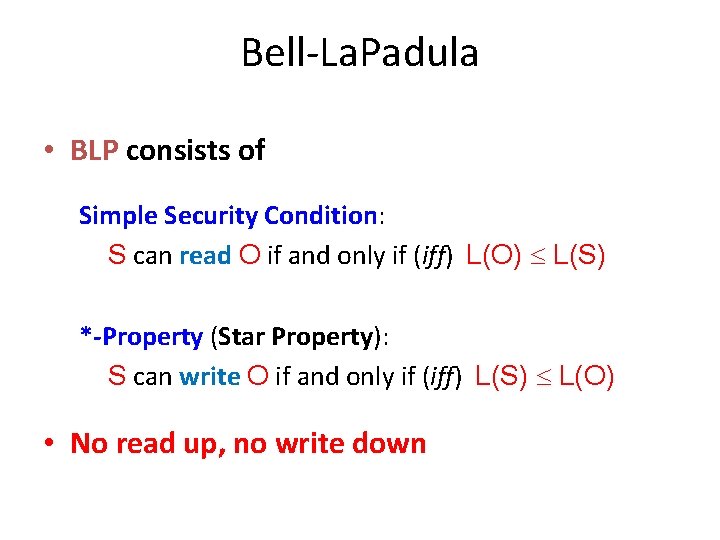
1. Bell-La. Padula (BLP) • BLP security model designed to express essential requirements for MLS – Captures the minimal requirements with respect to the Confidentiality. • BLP deals with Confidentiality – To prevent unauthorized reading • Let’s assume that O is an object, S is a subject – Object O has a Classification – Subject S has a Clearance – Security level denoted L(O) and L(S)

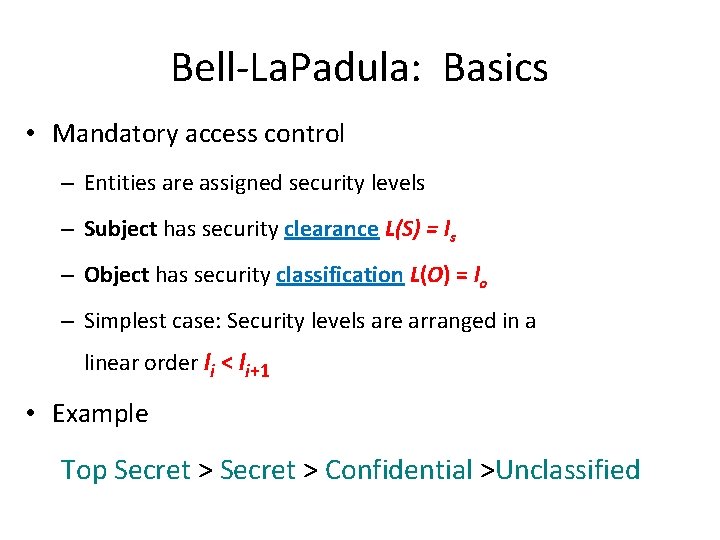
Bell-La. Padula • BLP consists of Simple Security Condition: S can read O if and only if (iff) L(O) L(S) *-Property (Star Property): S can write O if and only if (iff) L(S) L(O) • No read up, no write down

Bell-La. Padula: Basics • Mandatory access control – Entities are assigned security levels – Subject has security clearance L(S) = ls – Object has security classification L(O) = lo – Simplest case: Security levels are arranged in a linear order li < li+1 • Example Top Secret > Confidential >Unclassified

“No Read Up” • Information is allowed to flow up, not down • Simple security property: – S can read O if and only if • lo ≤ ls and • S has discretionary (available for use) read access to O - Combines mandatory (security levels) and discretionary (permission required) - Prevents subjects from reading objects at higher levels (No Read Up Rule)

“No Write Down” • Information is allowed to flow up, not down • *property – S can write O if and only if • ls ≤ lo and • S has write access to O - Combines mandatory (security levels) and discretionary (permission required) - Prevents subjects from writing to objects at lower levels (No Write Down Rule)

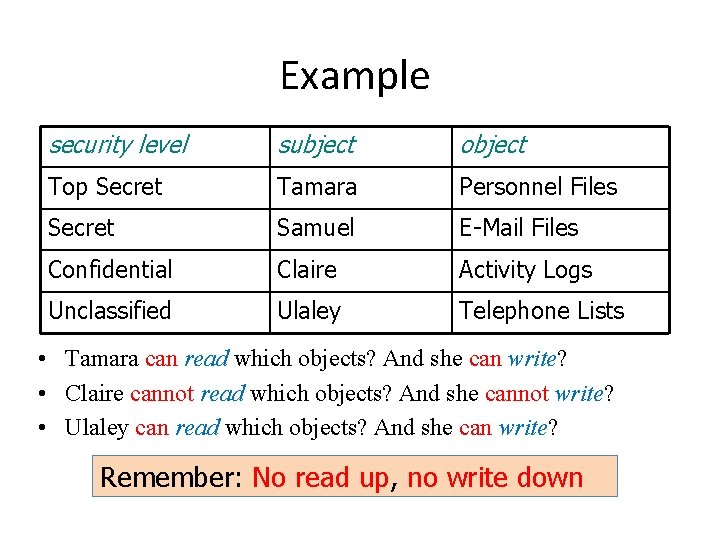
Example security level subject object Top Secret Tamara Personnel Files Secret Samuel E-Mail Files Confidential Claire Activity Logs Unclassified Ulaley Telephone Lists • Tamara can read which objects? And she can write? • Claire cannot read which objects? And she cannot write? • Ulaley can read which objects? And she can write? Remember: No read up, no write down

BLP: The Bottom Line • BLP is simple, probably too simple • BLP is one of the few security models that can be used to prove things about systems • BLP has inspired other security models – Most other models try to be more realistic – Other security models are more complex – Models difficult to analyze, apply in practice

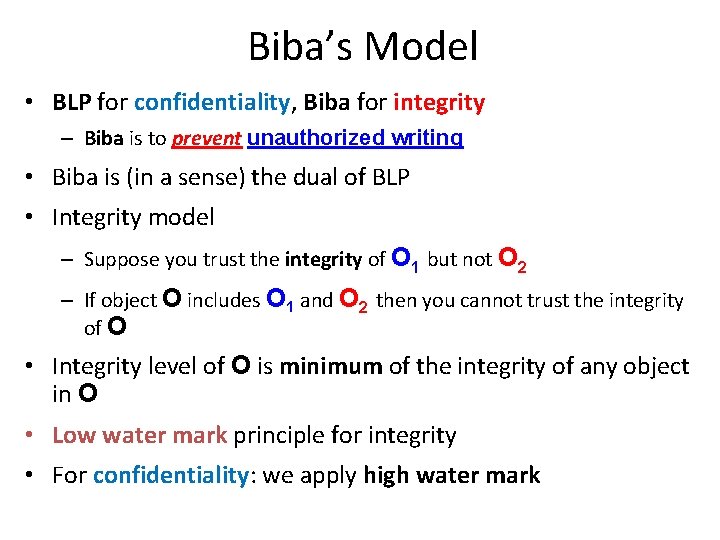
Biba’s Model • BLP for confidentiality, Biba for integrity – Biba is to prevent unauthorized writing • Biba is (in a sense) the dual of BLP • Integrity model – Suppose you trust the integrity of O 1 but not O 2 – If object O includes O 1 and O 2 then you cannot trust the integrity of O • Integrity level of O is minimum of the integrity of any object in O • Low water mark principle for integrity • For confidentiality: we apply high water mark

Biba’s Integrity Policy Model • Based on Bell-La. Padula – Subject, Objects have • Integrity Levels with dominance relation – Higher levels • More reliable/trustworthy • More accurate

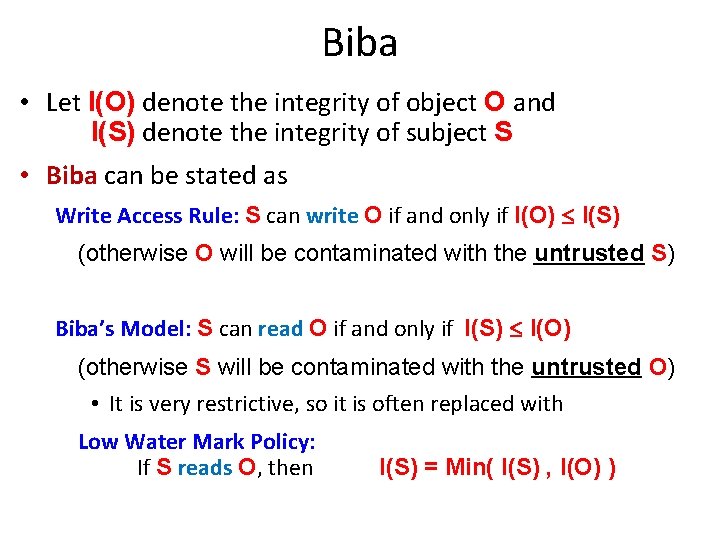
Biba • Let I(O) denote the integrity of object O and I(S) denote the integrity of subject S • Biba can be stated as Write Access Rule: S can write O if and only if I(O) I(S) (otherwise O will be contaminated with the untrusted S) Biba’s Model: S can read O if and only if I(S) I(O) (otherwise S will be contaminated with the untrusted O) • It is very restrictive, so it is often replaced with Low Water Mark Policy: If S reads O, then I(S) = Min( I(S) , I(O) )

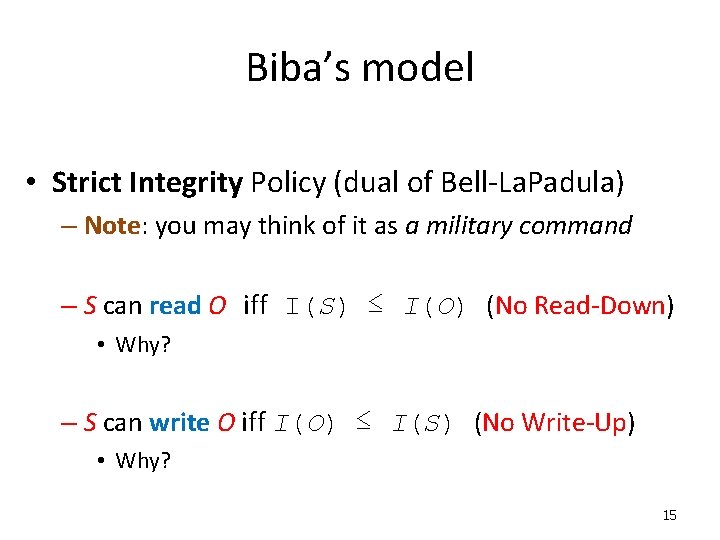
Biba’s model • Strict Integrity Policy (dual of Bell-La. Padula) – Note: you may think of it as a military command – S can read O iff I(S) ≤ I(O) (No Read-Down) • Why? – S can write O iff I(O) ≤ I(S) (No Write-Up) • Why? 15

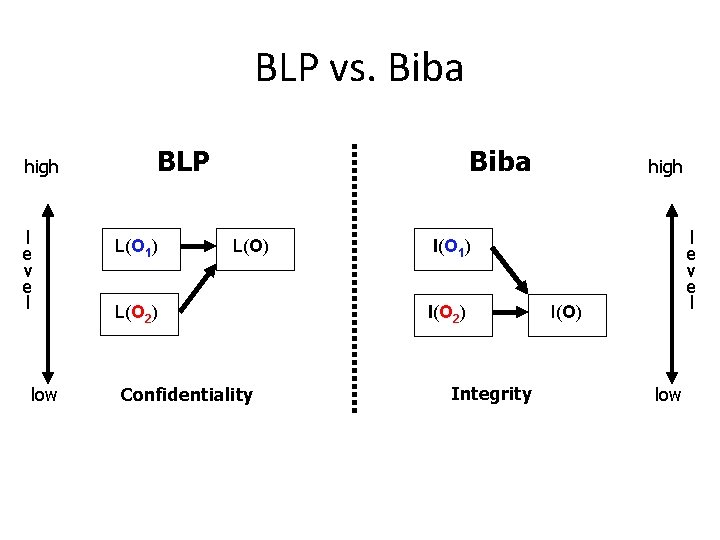
BLP vs. Biba high l e v e l low BLP L(O 1) Biba L(O) L(O 2) Confidentiality high l e v e l I(O 1) I(O 2) Integrity I(O) low